Get the Basics Right and Good Things Follow
Occasionally, I receive an email to ask what’s the best way to secure the deployment of Microsoft Teams. Such an important question deserves a measured answer, but in most cases, people want a simple formula that they can implement in an afternoon. After all, other tasks compete for valuable time, and there’s other work to do.
After many debates with tenant administrators, I’ve boiled my answer down to three points:
- Secure Users.
- Secure External Access.
- Secure Teams.
Because Teams is such a convoluted application, complexity hides beneath the serenity of such a simple framework. However, I’m pretty sure that you can put any of the challenges involved in securing Microsoft Teams to meet the needs of your organization in one of the three buckets, and I prefer to get the basics right before plunging into the minutiae of policy settings and other controls.
Let me explain what I mean.
Securing Microsoft Teams Users
If user accounts are insecure, your tenant is insecure, and all applications are at risk. Microsoft is doing its best to move organizations away from insecure protocols through efforts like the deprecation of older versions of TLS (now over 90% complete, or so I hear), and removing basic authentication for seven email connectivity protocols. These projects help because they reduce the attack surface for account penetration and compromise. However, the single most important thing you can do to achieve secure users is to force the adoption of multi-factor authentication (MFA).
Alex Weinert, Director of Identity Security at Microsoft, has long banged the drum for MFA, but the evidence suggests that four out of five Microsoft 365 accounts remain unprotected. In 2020, he said that more than 99.9% of Microsoft enterprise accounts that end up being compromised didn’t use MFA.
If an attacker compromises an account and can get into Teams, they have access to everything the account’s owner works with through Teams. And given the widespread adoption of Teams as a hub for collaboration and integration, that could be a rich harvest of valuable information.
Some protest about MFA because they don’t like the additional challenges. But even the weaker forms of MFA, like SMS, work so much better at deterring attackers. Paul Robichaux wrote a good piece on this topic last year. You should take his advice and make sure that Teams has a solid foundation for secure access. I recommend Microsoft’s Authenticator app as the additional authentication (it comes with some nice features), but it doesn’t matter what you use once it’s not single-factor authentication. And if you have the necessary Azure AD Premium licenses, you can combine MFA with conditional access policies to ensure that everyone does the right thing.
Engage with Microsoft 365 experts like Alex Weinert and Tony Redmond at The Experts Conference 2022 in Atlanta, GA September 20-21. Ask your questions 1:1, get hands-on in our M365 Managements Shortcuts Village, and network with peers!
Secure Microsoft Teams External Access
After making sure that tenant users are secure, the focus moves to people whose identities exist outside your organization in other Microsoft 365 tenants or other directories like Google. These people can access Teams using:
- Azure AD B2B Collaboration: Used to allow external people to become guest members of teams with access to regular and private channels and the SharePoint Online sites for the team and private channels.
- Azure AD B2B Direct Connect: Used to allow external people to become members of shared channels with access to the SharePoint Online sites for those channels.
The first thing to decide is whether to allow external access. Most organizations do because it’s hard to collaborate on an exclusively internal basis. Some people outside your company have unique experience, knowledge, and expertise that bring value, and external access is how you let them in.
Assuming that external people are welcome, the focus shifts to Azure AD because it manages inbound connections. After deciding who can add guest members (anyone or users with specific admin roles like Teams administrator), I recommend that every organization pays attention to two groups of settings in the External Identities section of the Azure AD admin center.
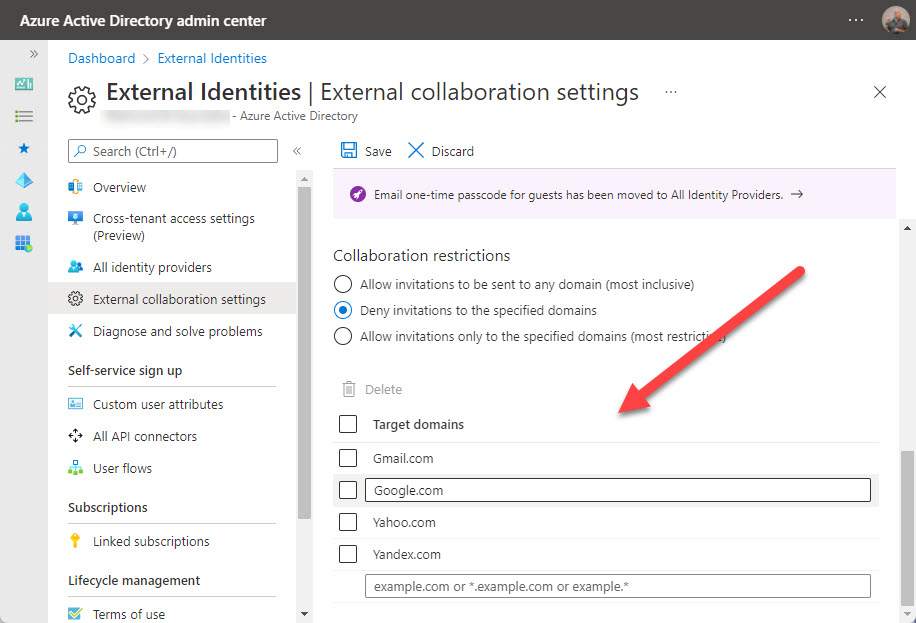
Collaboration restrictions under External collaboration settings. These control what external domains guest accounts can come from. You can have a single allow list (guests can only come from these domains) or deny list (guests can’t come from these domains). I usually go with a small deny list (Figure 1). Most organizations block competitor domains, and many don’t allow guests from consumer domains like Outlook.com. The downside of blocking guests from consumer domains is that smaller businesses often use these email services.
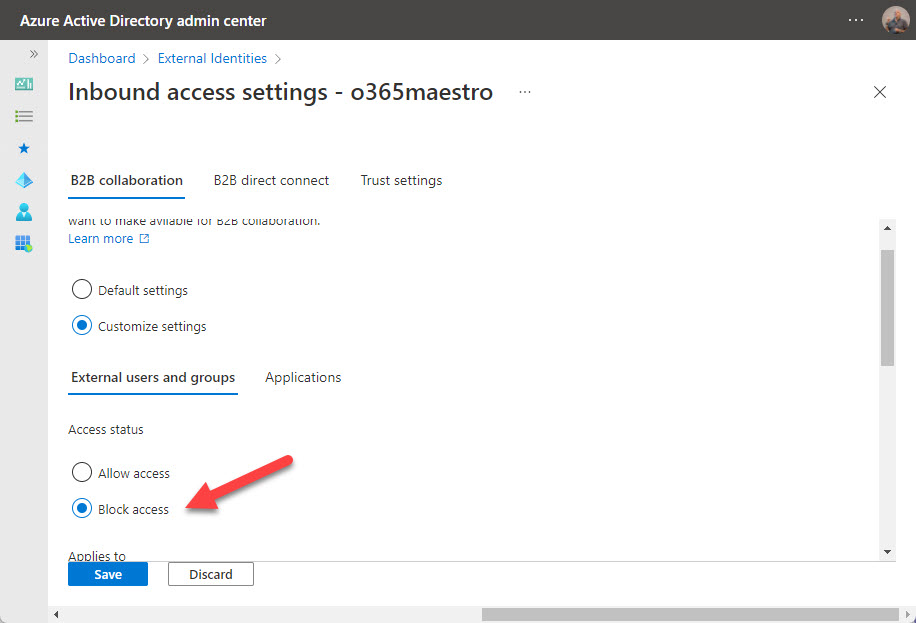
Cross-tenant access settings. The first application to consume this method of controlling external access is Teams shared channels. External members of shared channels don’t have guest accounts because Azure AD accepts the credentials granted by their home tenant (shared channels don’t currently support members with consumer accounts). You can get very granular with these settings. My suggestion is to decide on default settings that work well for all tenants and create tenant-specific settings only when absolutely necessary, such as when you need to restrict access to a specific group of users from another tenant.
The nice thing about cross-tenant access settings is that you can configure them to control Azure B2B Collaboration too. If you don’t want your users to become guests in another Microsoft 365 tenant, simply create a cross-tenant policy that blocks outbound access to that tenant (Figure 2).
Securing Microsoft Teams
With tenant users protected by MFA and external access under control, the next topic is how to secure teams (not the application, which is Teams, but rather the collaboration spaces managed by the Teams service).
A ton of individual controls exist (Teams is very fond of policy-driven management) over what individual tenant and guest users can do in private chat, group chat, channel conversations, and meetings. Microsoft 365 Data Loss Prevention policies can monitor chat and channel messages if you have Office 365 E5 or Microsoft 365 Compliance licenses. You could also implement Information Barriers for Teams. Again, this is a high-end feature, but if you need to stop different groups of users (organization segments) from communicating with each other in chat, channels, and meetings, it’s an effective mechanism.
On a more fundamental level, I consider four topics to secure teams:
- Container management.
- Apps.
- Control Sprawl.
- Auditing.
Container Management and Sensitivity Labels
Container management means that you use sensitivity labels (available in Office 365 E3 and above) to control team settings. For instance, I have a sensitivity label called Guest Access that’s applied to all teams allowed to have guest members. When a team receives the label, it inherits privacy and guest access settings from the label along with several settings for the team’s SharePoint Online site (Figure 3).
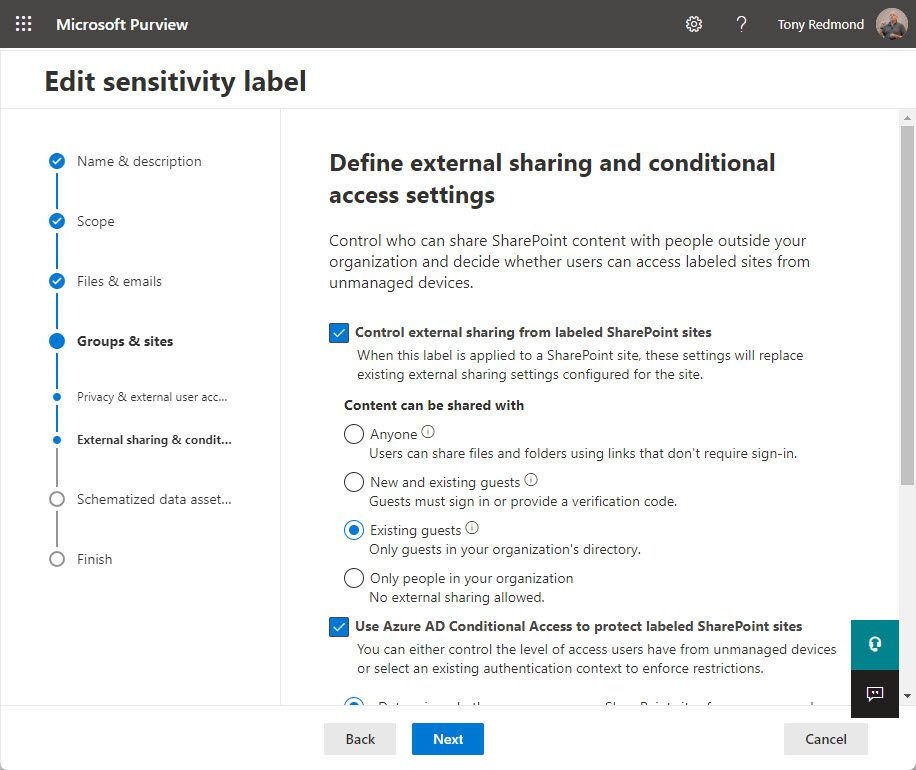
Microsoft is building out the set of container controls in sensitivity labels (the latest addition is site sharing permissions), and the biggest advantage of using sensitivity labels for container management is that the organization exerts consistent settings across all labeled teams. It means, for example, that organizations can lock down important and confidential teams through the application of an appropriate sensitivity label in the knowledge that the team will inherit all the necessary settings from the label.
Teams with guests and shared channels often have confidential information that external people should not be able to access. Private channels are one way to achieve this goal, but you can also protect confidential documents with sensitivity labels and encryption. This form of sensitivity label contains rights assigned to different users and groups. If the label restricts access to tenant accounts, guests can see the existence of confidential information in the SharePoint Online site belonging to the team, but they won’t be able to open protected documents.
Apps
The last time I checked, the Teams app store has 1,526 apps (first- and third-party). With an eye on security, it’s a bad thing to allow people to use apps without supervision. You can block apps on an individual or organization-wide basis and you use setup policies to install apps for users. Before making any decision about deploying an app, check out its Microsoft 365 app certification status to understand what access to user data the app needs. Read this article to dive further into Microsoft Teams security for apps.
Engage with Microsoft 365 experts like Alex Weinert and Tony Redmond at The Experts Conference 2022 in Atlanta, GA September 20-21. Ask your questions 1:1, get hands-on in our M365 Managements Shortcuts Village, and network with peers!
Control Sprawl
In early 2021, Microsoft acknowledged that tenants need some help to cope with group sprawl. Simply put, sprawl means that too many groups (and teams) are in use. Or rather, created and might be in use. The reason why group sprawl matters is that when an organization ends up with thousands of teams, the time necessary to manage teams grows and takes away time that administrators might better use elsewhere, like checking Azure AD sign-in logs, or learning how to use tools like Microsoft Sentinel to identify problems.
Tools like the group expiration policy help to remove obsolete and unwanted teams, but they need management too. The best approach is to control the creation of new teams and not allow sprawl to occur.
Auditing
Microsoft 365 tenants with Office 365 E3 and above licenses can capture over 1,500 different events for workload actions in a unified audit log, which is searchable using the Microsoft Purview Compliance portal or PowerShell. I can’t emphasize the usefulness of the audit log in answering what happened when questions.
To be secure, tenant administrators need to know what’s going on. If they do, they’ll pick up signs of anomalous behavior that might be early indicators of attack or compromise. Time spent becoming acquainted with the way the Search-UnifiedAuditLog cmdlet works and the results it delivers is a good investment. Microsoft adds new events to the audit log regularly, and it’s worthwhile browsing through the audit log to see what events turn up for activity in Teams, Exchange Online, Azure AD, and other workloads.
Keep it Simple
Each of the topics listed above deserves in-depth discussion. The nature of Teams and its web of interconnections with other parts of Microsoft 365 can make detailed configuration challenging. However, focusing on the basics to secure user accounts, control external access, and perform the essential management of teams is a great starting point. Keep it simple and get it right.




