A certificate installed on an Exchange Server 2010 server may display the following error message.
The certificate is invalid for exchange server usage
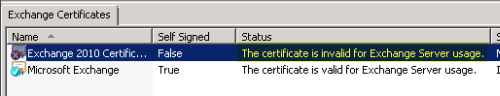
This can occur when the certificate cannot be verified to a trusted certificate authority. This may occur when the certificate has been issued by a private certificate authority.
To correct the problem you must install the root certificate for the certificate authority. For a private certificate authority this can be obtained from the web enrollment page (eg http://ca-server/certsrv).
Browse to the web page and click on Download a CA Certificate, Certificate Chain, or CRL.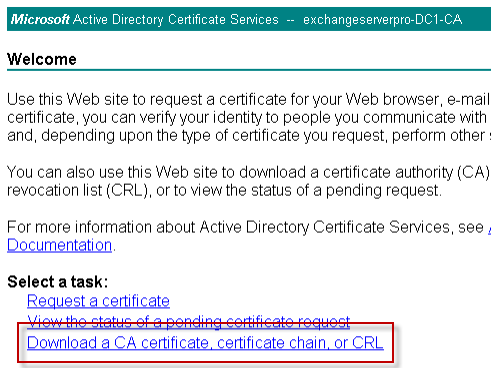
Click to download either the CA Certificate (if the certificate was issued by a root CA) or the Certificate Chain (if the certificate was issued by an intermediary CA).
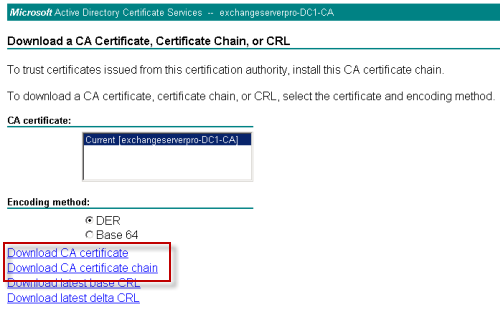
Launch a new Microsoft Management Console (Start -> Run, mmc.exe) and add the Certificates snap-in to it, connecting to the Computer Account for the Local Computer.
Navigate to Trusted Root Certification Authorities. Right-click on Certificates and choose All Tasks and then Import.
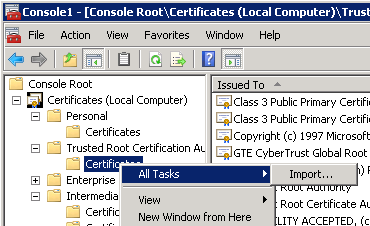
Browse and choose the CA Certificate or Certificate Chain that you downloaded earlier.
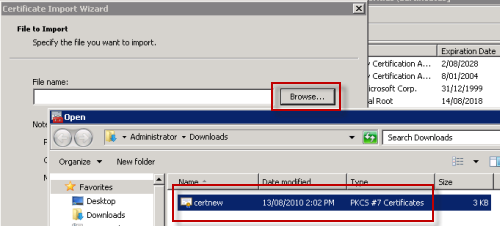
Place the certificate in the Trusted Root Certification Authorities store.

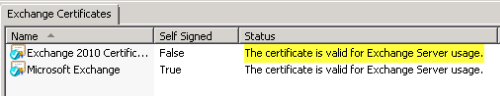
Complete the import wizard and then refresh the Exchange Management Console, and the certificate should now be valid.



Thank you. It works like a charm.
Thanks Paul! Your tutorials are invaluable.
thanks for this – helped me
We have an issue with clients not being able to connect with outlook anywhere. OWA works and so do our mobile devices. The only thing that has changed recently was our CAS certificate which is now SHA2(Entrust).
THX ! 🙂
Hi Paul
My cert is from GoDaddy. How I do about getting rid of the error for a cert that was issued from a public CA.
I would contact the CA for assistance. There may be a root or intermediate cert you need to download and install on the server as well.
Paul, i need a litle help, 🙂
my cenario.
one server for all services.
i buy a digicert san certificate,
I configured :
CN=autodiscover.mydomain.com.br
SAN=webmail.mydomain.com.br
i need add FQDN from my server spoex1.mydomain.com.br ? to my SAN certificate?
Thanks
You don’t need to add your server FQDN if you configure your various Exchange namespaces to use aliases.
Example (written for Exchange 2013 but applies to Exchange 2010 as well):
https://www.practical365.com/avoiding-exchange-2013-server-names-ssl-certificates/
Nice Write Up.. helped lot..
Thanks Mr.Paul.
Hi all,
I’ve read some articles relating to SAN, but still confuse about it and I appreciate your help.
Here are my lab:
——————————————————————————————————————————–
Exchange (ex.test.com)(103.20.74.52) Linux mail server (linux.mail.com) (103.20.76.3)
||
||
Outlook clients (internal users, non-domain): group1 (network: 103.20.74.x), group2 (network: 103.20.76.x)
———————————————————————————————————————————
I’d like to plan to :
– Users of group_1 use host: mail1.test.com, to create Exchange profile and get mail
– Users of group_2 use host: mail2.local.com, to create Exchange profile and get mail
– Linux mail server: use host : mail2.local.com, auto.local.com, to connect to Exchange server and use option Autosicover
(To add Exchange to Linux mail, we only put the name/IP of Exchange server and Administrator account into it. Besides, Linux mail server also support Autodiscover option to lookup Exchange e-mail. To create a mailbox connecting to Exchange email, we only create name and give a exchange email)
And some guys tell me to use multiple hosts, you will create SAN certificate. So, from Exchange server, I create a SAN with all information:
CN (Common) name = ex.test.com
Other domain names = mail1.test.com, mail2.local.com, auto.local.com, owa.local.com
All steps to create certificate/import are followed as in
https://www.practical365.com/exchange-server-2010-certificate-invalid-for-exchange-server-usage-error/
But I still confuse about this. Here are my questions:
1. To do my plan, create SAN is right way ?
2. We’ve to add the names in SAN to DNS server. (please review the table as below) ? IF not, is it possible ?
FQDN ————- DNS type ——— Value
ex.test.com———-A—————-103.20.74.52
mail1.test.com —– A —————103.20.74.52
mail2.local.com—-CNAME————–mail1.test.com
auto.local.com—–CNAME————–mail1.test.com
owa.local.com —–CNAME————–mail1.test.com
3. When requesting a certificate from CA authority server (also Active Directory of Exchange server), I’ve 2 options : Download a “ROOT CA” or “Certificate Chain”. what kind of certificate to download ? In my case, is Certificate Chain ?
4. if a user of group1 or group 2 or Linux connects to Exchange server, do we have the log in Exchange to know that ? and in log, whether all trace information point to primary host name or suitable name as in plan ? – I meant that:
group 1 connects to Exchange ny host: mail1.test.com. In Exchange logs, this show that users of group 1 connect to host mail1.test.com, or always point to ex.local.com ?
5.
5.1. After installing SAN, all connection to Exchange are verified by SAN no matter what the end-user is Outlook or other servers ?
5.2. From Linux server, I’ll send email to a Linux_user configured Exchange email. On Linux server command I typed:
openssl s_client -showcerts -connect mail2.local.com:443
or
openssl s_client -showcerts -connect ex.local.com:443
Output: verify error:num=20:unable to get local issuer certificate
Although having errors, I can get right Issuer (AD name and encrypt key between “Begin/ End”). So, does my SAN have problem ? do you know about this issue and how to fix it ?
Thanks in advance.
Tony
Yet again my bacon saved by Exchange Server Pro
Thank you Paul, I got it fix.
Had this issue today when my root CA cert expired. Resolved this on the Exchange servers by doing a gpupdate /force, as the root CA is automatically pushed out and updated in GP.
This helped me, thanks!
Hi Paul,
I get exactly the same error message. I bought SSL certificate from godaddy.com. Can you please tell me where can I get the root certificate for godaddy? I don’t know what is this web enrollment page? what I understand is that there must be a web enrollment page for godaddy and I need to download Root cert for godaddy from there and install it on my servers somewhere?
Please help,
Many thanks,
The web enrollment page you see there only relates to a private CA. For a commercial CA such as Godaddy you’ll need to check their support pages or contact them to ask about any other required certificates you need to install to get your SSL certificate working.
Thanks Paul. I got it working, I had to install the intermidiate certificates from go daddy to get it working, Cheers! 🙂
Addition:
Can also happen to certificates with an official root CA.
Then the Exchange server is not able to check the revocation of the cert.
Workaround:
Open cmd with elevated permissions (right click -> Run as Administrator)
netsh winhttp set proxy “;exeption;exeption”
Refresh EMC
Maybe need to restart Exchange Services
DING! All green!
Cheers,
Alex
Thank you paul this helped me as well – funny the smallest things you can rip your hair out
Perfect. Thank you Paul .
How to solve it but with Third party certificate from DigiCert
Thank you!! This fixed my problem!
Thx you
thanks heaps Paul, worked a treat!
Thanks for quick response!
I have assigned with Exchange Management Shell:
—
CertificateDomains : {mobile.code.com}
HasPrivateKey : True
IsSelfSigned : False
Issuer : E=Root_CA@mobile.code.com, CN=Mobile code, OU=PRS, O=code, L=Berlin, S=Berlin, C=DE
NotAfter : 09.10.2017 11:24:01
NotBefore : 11.10.2011 11:24:01
PublicKeySize : 2048
RootCAType : Unknown
SerialNumber : 0A
Services : IMAP, POP, IIS, SMTP
Status : Invalid
Subject : C=DE, S=Berlin, L=DE, O=code, OU=PRS, CN=mobile.code.com
Thumbprint : FCAA09B80451FB44AADBBF738ACBD5A42D6AE36
—
The root CA is also trusted but I still get the error message.
Hello,
I try this, but certificate is always invalid.
I created with the “New Certificate” a certificate request, let it sign by a private root CA
and (Root CA certificate & Exchange), both imported certificates
any idea?
Thanks!
You can try using the Exchange Management Shell to assign it instead. See here:
http://blogs.technet.com/b/exchange/archive/2010/07/26/3410505.aspx
Thanks for quick response!
I have assigned with Exchange Management Shell:
—
CertificateDomains : {mobile.code.com}
HasPrivateKey : True
IsSelfSigned : False
Issuer : E=Root_CA@mobile.code.com, CN=Mobile code, OU=PRS, O=code, L=Berlin, S=Berlin, C=DE
NotAfter : 09.10.2017 11:24:01
NotBefore : 11.10.2011 11:24:01
PublicKeySize : 2048
RootCAType : Unknown
SerialNumber : 0A
Services : IMAP, POP, IIS, SMTP
Status : Invalid
Subject : C=DE, S=Berlin, L=DE, O=code, OU=PRS, CN=mobile.code.com
Thumbprint : FCAA09B80451FB44AADBBF738ACBD5A42D6AE36
—
The root CA is also trusted but I still get the error message.
I try this, but certificate is always invalid.
Exist any different reasons for this error?
Hi Tomm, what kind of certificate have you installed? Is it from a private CA, or a commercial CA?
Paul,
I am having the same issues as outlined from several of the users. I have managed to resolve all but one. I am using the CLI for this portion of my lab. The cli commands are gleaned from your website tutorials.
Using a lab: Private Commercial CA
I was able to create, install and test my new SAN certificate on 1 CAS ARRAY server.
Problem: Unable to Import the SAN Cert to my 2nd CAS ARRAY server.
Command:
$file = Get-ExchangeCertificate | Export-ExchangeCertificate -BinaryEncoded:$true -Password (Get-Credential).password
Error:
Export-ExchangeCertificate : The private key couldn’t be exported as PKCS-12. It either couldn’t be accessed or isn’t exportable.
Please advise the solution to how to import the SAN Certificate I used for the initial Exchange Certificate request.
Get-ExchangeCertificate will return more than one certificate. I suggest you specify the thumbprint of the certificate you’re trying to export.
Hi,
I’ve just had EMC showing the certificate being invalid. I used Enable-ExchangeCertificate to force the certificate to be used for IIS, and this allowed me to see the real issue. The certificate had been revoked due to a mis-communication with our certificate supplier.
New certificate being ordered!
Worked perfect.
Hello Paul.
Thank you very much! You are really helped me! Cool!
you are my hero.
I was having this problem in my lab for exchange 2010 and of course MS Book didn’t mention anything regarding having this problem, so I got it fixed using your instruction.
Thanks a bunch.
Pingback: Exchange 2010 SSL Certificates - Exchange Server Pro
Thank you.
Pingback: How to Issue a SAN Certificate to Exchange Server 2010 from a Private Certificate Authority | Exchange Server Pro