Access reviews in Azure AD/Office 365 were introduced a year ago, aiming to offer a solution to some of the problems arising from the use of the self-service capabilities across few features. In their initial release, access reviews allowed organizations to trigger periodic re-evaluation and re-attestation of employee access to applications and group membership, for all relevant users or ‘Guest users only’. The feature has been expanded to cover Azure AD admin role assignments and has received several other improvements, so now it’s time to take another look at it.
Quick refresher on how Access Reviews work
As Access Reviews aren’t that new and there is extensive documentation available online, I won’t go into much detail on how they work. To cover the basics though – a global admin or user management admin can navigate to the access reviews page in the Azure AD blade and create one or more Controls to trigger a review. Controls are grouped in Programs, which for all intents and purposes we can consider as containers for controls.
After pressing the New Access Review button to create a new control, one can specify the Review name, Description and Start date. Next, you can select the Frequency of the review, or its recurrence. This is a new element which was not available back when the feature was first released. Possible values include One time, Weekly, Monthly, Quarterly or Annually. Depending on the selection you make for the frequency of the review, some additional settings might have to be configured under the End group, including the Duration, Number of Times for the review to execute or an End Date. You can leave the Access review running indefinitely, specify a number of occurrences, or specify an End Date to complete it after.
The next step of configuring an access review is to specify the review target via the Users to review control, which can be either members of a group or users assigned to specific application. You can also limit the Scope of the review to ‘Guest users only’ or include ‘Everyone’ covered by the previous selection. Depending on the selection made, you will next have to specify the group (Security group, Mail-enabled Security group, Distribution group, or Office 365 group) or application (only “third-party” applications, excluding any of the Office 365 applications) for which to review access. Lastly, you need to specify the Reviewers, as in the users who will be responsible for approving or denying the request. The choice here can either be ‘Selected users’, ‘Group owners’ or the ‘Members’ themselves.
Finally, you can configure some additional settings, such as specify which Program to link the review to, whether Mail notifications should be sent to reviewers and admins, whether Reminders should be sent to reviewers who have not yet submitted their vote, and whether to Require reason on approval. A new setting to Show recommendations is also available, which does some magic under the covers to give you suggestions based on the user’s access patterns. Lastly, you have the option to Auto apply results to resource after the review has ended, as well as to specify which action will be performed Should the reviewer not respond. This is another new element and a welcome addition to the Access Reviews feature.
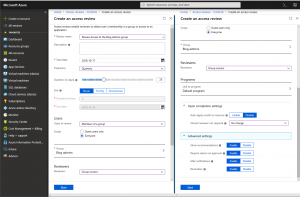
After configuring all the settings, you can Start the access review, at which point the reviewers will be notified via email if the corresponding option was selected, or you can inform them via any other means. As a reviewer, the user can navigate to the access reviews app in the Azure AD self-service portal or can open it directly by clicking this link. Then, for each Access Review currently assigned to him, the user can choose whether to Approve or Deny the request. A similar process used to review your own access to groups or applications. The decision made at this step will be applied after the Access review has been completed, either by reaching the end date or manually stopped by administrator.
Configuring access reviews for Azure AD admin roles
As mentioned above, the initial release of the access reviews feature covered only group membership and application access. Given that fact, it was very strange that Microsoft decided to put an Azure AD Premium P2 license requirement for every user involved in any part of the access reviews feature, while at the same time the feature didn’t offer any integration with either the Azure AD Privileged Identity Management or Identity Protection features, which are the core differentiators between the P1 and P2 tiers.
Fast forward a year, and access reviews can also be performed against any Azure AD administrative roles. Interestingly, you cannot start such a review from the “regular” access reviews blade in the portal, but instead you have to navigate to the Azure AD Privileged Identity Management page first, then click Azure AD Directory role’s under the Manage section, and lastly click on access reviews. Alternatively, you can just use this direct link. As this functionality is hosted on the PIM management page, users with the Privileged Role Administrator role assigned can also configure Access Reviews.
The steps to configure a New access review for a given admin role are practically the same as described in the previous section, with the only difference being that the Scope is preset to ‘Everyone’ and cannot be changed. All the other settings can be toggled as needed. For the purposes of this article, we’ve chosen to configure an access review for the Compliance administrator role that will run Quarterly’for the next 5 quarters, and each Member of the role should clarify whether they still need access. Should the user choose to ignore the review, the Remove access action will be auto-applied.
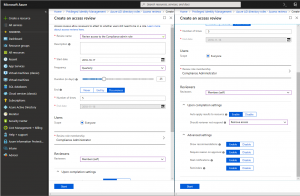
The screenshot above illustrates the settings configured for the access review and in the next section we will see how the actual review process is performed.
Responding to an Azure AD role Access Review request
After starting thea review process, email notifications will be delivered for each user that currently has the Compliance administrator role assigned, in accordance with the selection we made in the previous section. Compared to the initial feature release, notification emails have received a facelift and now look similar to the below:

Clicking the Start review button will take the user to the Azure portal instead of the My apps portal used for “regular” access reviews. Even if the user navigates manually to the access reviews app in the My apps portal, the request will not be visible there as this portal only lists group and application related reviews. Instead, if the user wants to get an overview of all Azure AD Role Access Reviews he is currently involved with, the can navigate to the Azure AD Privileged Identity Management page, then select Review access or use the direct link.

As shown from the above screenshot, the reviewer will be presented with all the essential information about the selected access review and a list of users whose access he needs to review. Since we selected the self-evaluation option in the access review settings above, only the user’s own account is listed here. If the user was selected as a reviewer instead of using the self-valuation option, a list of all users under the scope of the review will be presented instead. For each entry, a recommendation is also surfaced, based on the information stored in the Azure AD Audit logs for any relevant actions performed by the user. In this case, since the user has recently logged in, the recommendation is to keep its access.
Selecting the user entry and performing the corresponding action via the ‘Approve’ or ‘Deny’ buttons is all that is needed in order to complete thea review request. In our scenario, the user decided that he doesn’t need access to this admin role anymore and pressed the ‘Deny’ button. The option ‘Reason’ might be required depending on the settings we configured earlier.
Reviewing and applying the results of an Access Review
After all users have given their input or the end time for the review has been reached, an admin can go back to the PIM blade and the Access Reviews section to check the Results. Well, technically this action can be performed at any time, and if the review is still active the admin can also manage its Settings, add additional Reviewers or remove existing ones, as well as Remind any users that haven’t provided their input yet.
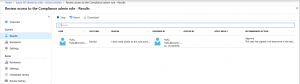
On the above screenshot, the current set of results for the access review are shown. We see that one user has already reviewed his access, the outcome of the review, the reason given, the date it was performed on as well as the recommendation generated by the system. For Access Reviews with a large number of users, it might be easier to use the Download button to get a file with all the results and review them in Excel.
At this point in time, the results have not yet been applied and the review is still underway, even though in this specific scenario all the users in the scope of the review have already provided their input. If the admin doesn’t want to wait for the review period to end before the results are auto-applied, he can Stop the review and choose to apply the results manually. Alternatively, he can Reset the status and require users to re-review their access.
Whichever method was used to reach the end of the access review period, upon completion an email notification will be sent to the admin(s) and the relevant actions can now be applied. Depending on the outcome applied, any affected users will also receive notifications from the PIM service about changes in their role assignments:
Additional comments and summary
As mentioned in the beginning of this blog, new controls are available for configuring recurrence for access reviews. If we go back to the first picture in the previous section, we can notice the clear differentiation between the Current instance and the Series. An admin can use the relevant controls to make changes for the Reviewers or Settings for either the current instance or the whole series, as necessary. You can continue making changes to the series settings until the last occurrence has completed. In addition, you can get the next date on which the review will run by clicking the Scheduled review entry under the Series group. You can also Review history for any instances of the selected Access Review. For example, this is how the Overview of the access review occurrence we just ended looks like:

On the Results page for each instance, you can get a detailed view of the outcome for each individual user under the scope of the review, similar to what was shown in the previous section. In addition, details about any actions that were applied will be included. Alternatively, information about every steps of the Access Review process can be found in the Audit logs.
One other thing worth mentioning is that access reviews are now available for Azure resource roles as well. The process is identical to the steps described above, so we will not go into more details. For additional information, you can always consult the official documentation. Lastly, the all types of Access Reviews can now be managed also via the Graph API /beta endpoint.
In summary, the access reviews feature has received some exciting updates. Not only we get expanded scheduling controls, but we can also configure default actions and auto-apply results. In addition, access reviews can now be configured for Azure AD Administrative roles as well as Azure Resource roles, providing yet another way to take control over the “sprawl” of role assignments in your tenant. In case you are already paying using Azure AD PIM or Azure Identity Protection, access reviews are given to you for free so start using them today. If you aren’t paying for Azure AD P2 licenses though, the $9 per user per month price tag might be off-putting.



what can we do when reviewers and users in privileged roles are admin accounts without email address?
Can we have an Access review set up in azure that looks for inactive users for 90 days instead of the default 30?
Hello Sir,
Can we use Shared Mailbox as an access review reviewer??
Great post.
How does this work for reviewing security groups from on prem AD synced to Azure. I can’t get the results to apply?
You cannot apply the result to on-premises groups, the only action you can take there is export the result, then make the changes directly in AD.
I conceive you have mentioned some very interesting
points, thank you for the post.