When mobile device management is being used there are often concerns by end users about what the company can see on their mobile devices. For most people the concerns are around private information such as text messages and photos, while others are concerned about the level of control that the company gets over their device. For the purposes of this blog post I’m going to be looking at Microsoft Intune, but other MDM solutions will have similar capabilities and if you want to know about those then you should investigate that further with your MDM vendor of choice.
Those two types of concerns can be addressed separately, but before I go into that in more detail I just want to point out that this is not a purely technical problem to solve. Mobile device management requires a level of trust between the end users in your organization and the people responsible for managing the MDM platform. There needs to be clear communication between the parties to ensure that expectations are properly set. There also needs to be reasonable policies in place to reduce the risk of administrative error (or malicious action) causing a data loss or breach of privacy for the user of a managed device. This means that you should have, at a minimum:
- An acceptance policy for end users who are enrolling devices in your MDM solution. A real one, written by humans and only partially mangled by lawyers. The goal is to have a document that your users will actually read, understand, and willingly sign (or reject), and not just a formality that gets signed and filed away somewhere to cover your butt in the event of a problem later.
- A limited number of trusted and trained administrators who can manage the sensitive and impactful elements of the MDM solution (e.g. able to configure policies, access inventory data, etc). Limited access can be provided for support staff to deliver end user support, but like all administrative rights should be provided on a least privilege basis.
- Privacy advocates from the user population who can review and understand the level of control and access that the MDM solution provides over managed devices.
So with all that in mind, let’s look at an example of what Microsoft Intune knows about a iOS device that has been enrolled.
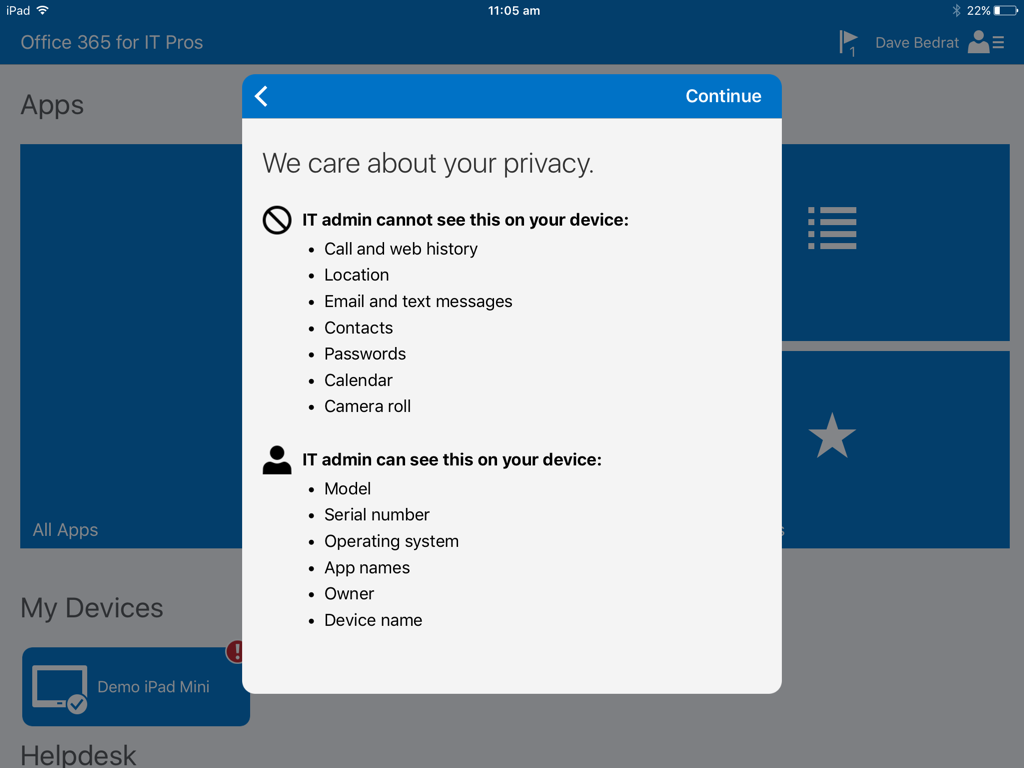
As you can see the privacy notice is fairly clear about what the Intune administrators can see – model, serial number, OS, app names, owner, device name. Intune admins can’t see phone call history, web surfing history, location information (except for iOS 9.3 and later devices when the device is in Lost Mode), email and text messages, contacts, passwords, calendar, and cameral roll.
So, is it as simple as that? Not really. There’s some extra considerations to apply here that I think are pretty important. Let’s start with device information.
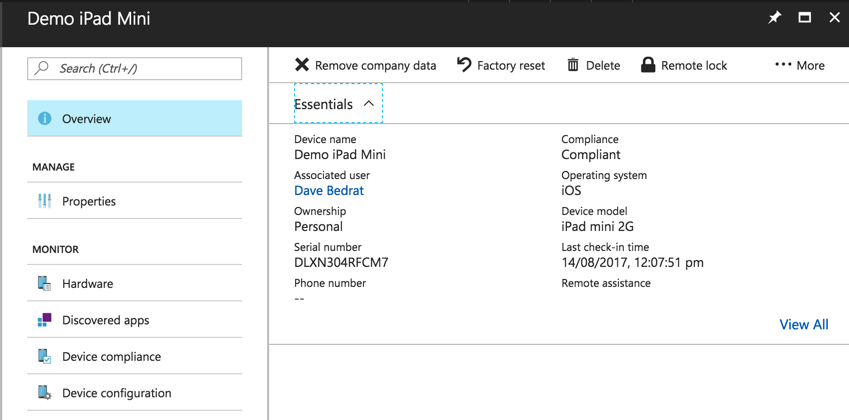
In the screenshot above the most important detail to be aware of is the phone number. My demo device is an iPad with no SIM card inserted, so there is no phone number reported. If a SIM was present, the last four digits of the phone number would be visible. That is the case for any personal device, which is what a newly enrolled device is classified as by default. If you change the device ownership to corporate (more on this shortly), the full number becomes visible.
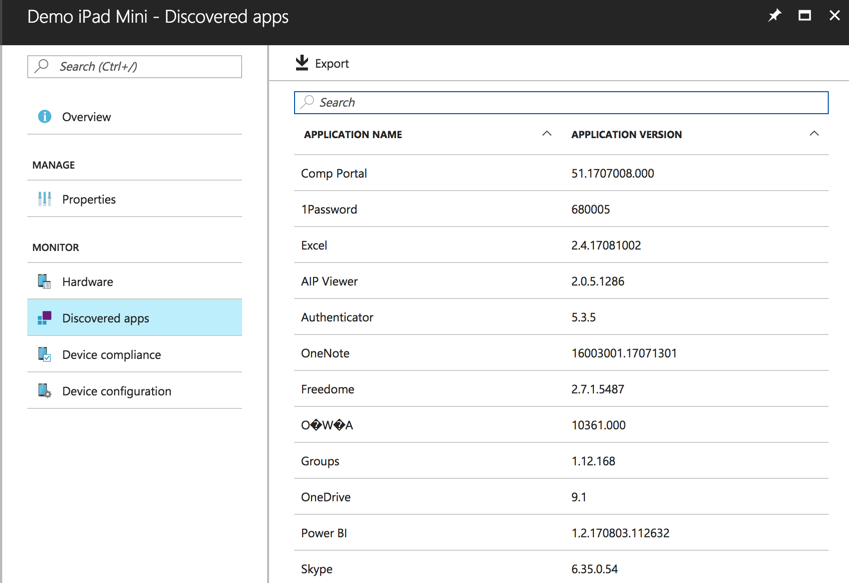
Another implication of personal vs corporate devices is the discovered apps. For personal devices there is no app inventory collected, except for the Company Portal app that is used to manage enrolment on the device.

An Intune administrator can change the device ownership from personal to corporate in the Intune admin portal.
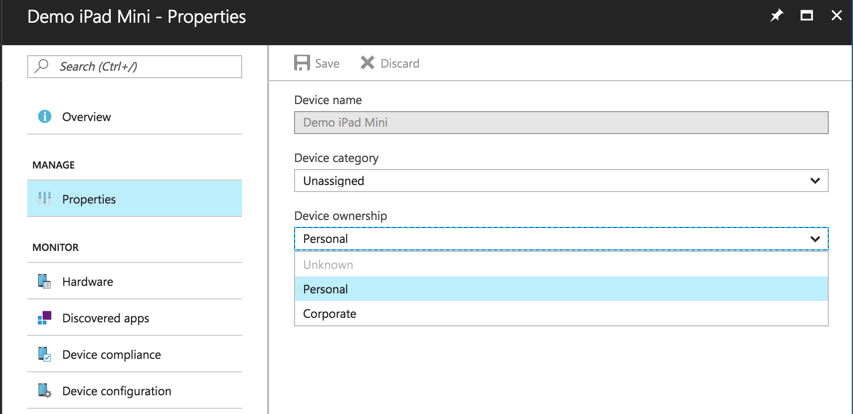
When doing so they are shown a very clear warning about the impact of this change.
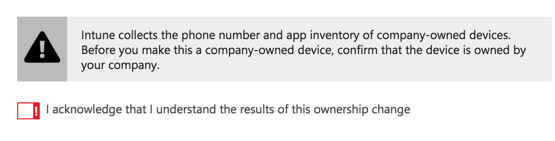
However there’s no additional warning provided to the user of the device, so they would not know when a device has been changed from personal to corporate owned by an administrator. There are two potential issues here that you need to be aware of. The first is the implications for device phone numbers being exposed to Intune administrators. Just because a user consents to having their device managed, doesn’t mean they want their phone number disclosed, and it’s not clear from the privacy notice during enrolment that this will actually occur. It’s something that you should make your users aware of in the documentation they sign when agreeing to enrol devices in Intune.
The second issue is the app inventory. The fact that corporate devices get a complete app inventory (for Windows 10 this only applies to Windows Store apps, not Win32 apps) is addressed in the privacy warning shown to users. The actual consequences of this may not entirely be clear. App inventory can reveal a lot about a person, even if the actual data within the apps is not exposed (which it isn’t). You could try to argue that a user shouldn’t be using apps that might reveal such private matters on a corporate device, which is a fair point. But remember, a personal device that is enrolled in Intune can be changed to a corporate device without the knowledge of the device owner.
Again, these issues are not able to be fully dealt with using technical solutions. The trust between your users and Intune administrators is key, and you should ensure that only the appropriate people in your IT support teams have access to this potentially sensitive data in Intune.
There’s a few more things to be aware of when devices are enrolled in Intune. In an earlier screenshot you can see controls for Intune administrators to:
- Remove company data – this will remove corporate data from managed apps such as Outlook and OneDrive, but leave personal data such as photos and text messages alone.
- Factory reset – this will wipe the device entirely, restoring it to a default state. If the user does not have backups of their personal data then it will be permanently lost.
- Delete – this will remove the device from Intune, but not remove data from the device.
- Remote lock – this will lock a device remotely, assuming it can be contacted. It takes just a few moments for the device to lock, but anyone with the device PIN/passcode can unlock it again.
Hidden in a “More” menu are some additional actions that Intune administrators can take.
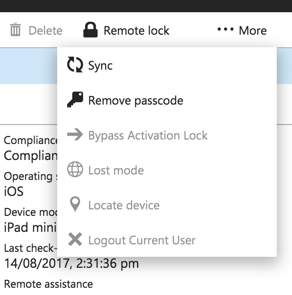
- Remove passcode – removes the device passcode, allowing anyone who has physical access to the device to access the apps and data on the device.
- Bypass activation lock – used to recover devices where the previous owner has not relinquished control of iOS before they handed back the device (e.g. a corporate owned device that will be re-issued to another staff member may require the activation lock to be bypassed).
- Lost mode/Locate device – when a iOS 9.3 or later device is in lost mode an administrator can access a limited amount of location data to try and find it.
Of all those administrative actions the ones of concern to end users are factory reset, which could result in permanent data loss, and remove passcode. You might be wondering why removing the passcode is a risk, given that it only benefits someone who has physical access to the device. Well… let’s just say that a previous case I investigated involved a… complicated relationship…er, triangle… of sorts… anyway, an admin helped another person gain access to a device belonging to a third person they were trying to snoop on for some rather unhinged reason. Moving on.
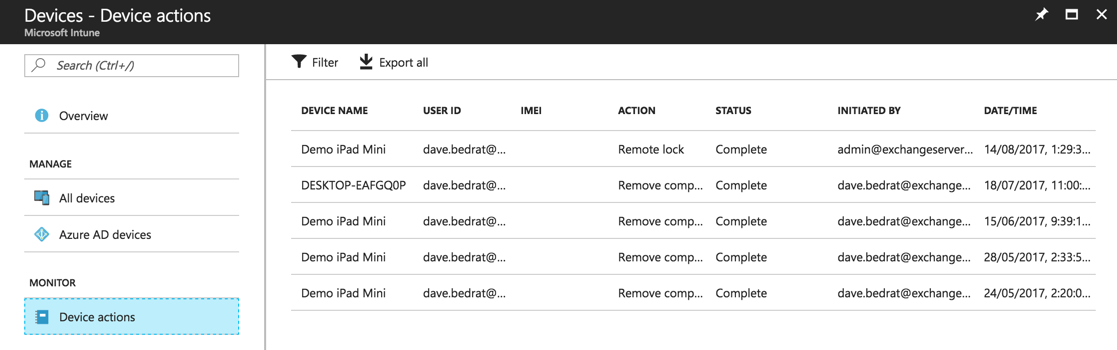
For any of those device actions you can see a list of who did what in the Intune monitoring section. This is not quite full-blown auditing for Intune, which is something Microsoft says they’re working on, but at least you should be able to identity any administrators who are doing the wrong thing (intentionally or otherwise).
That was a rather long walk to answer a simple question – what can Microsoft Intune see on your managed mobile devices?
The short answer is, not much. At least not directly. But there’s a lot of control given to Intune administrators that could lead to more invasive snooping, or even more destructive actions. Which brings us back to my earlier point that most of this stuff is not a technical problem to be solved, rather it is a trust issue between the device user and the organization’s (and their IT support staff). Frankly I think it’s a reasonable trade-off. Companies trust their staff not to act in way that is harmful, and staff need to be able to trust the organization to manage their mobile devices appropriately. If that trust doesn’t exist, I suspect there’s deeper problems that Intune can’t solve.



I find it amusing that most companies are advised (and probably considering) the Zero Trust security model. Yet, that Zero Trust does not go both ways. Employees are expected to trust the company but companies definitely don’t trust employees. Allowing someone to reset my password or factory reset my device requires a lot of trust.
Hi, I’m not sure if this thread is still active or not- but I just found out that the personal cell phone my (recently deceased) father owned is under MDM through Azure. I believe his Gf is the one who installed it before she (reluctantly) turned over his assets to the estate. It took me months to figure out why his phone and all his accounts were wonky, and why it felt like I was getting re-locked out of his accounts and prevented from seeing things I KNOW he has….financial and otherwise!
I feel like this is a crime, but where do I begin? As a layperson trying to explain this situation to anyone, I get very weird conspiracy-phobic looks. Obviously, I can’t log into Azure Directory and remove his device. And no worries on my authority – I am the court appointed executor of dad’s estate, so I am well within my powers to gather and preserve his assets. Thank you in advance, I’m so overwhelmed.
we have a strange effect of a user who installed intunes on his private fon and then got one from the company.
After uninstalling Intunes and Authenticator, alll those office apps are still there and cannot be removed.
Any advice how to do this?
Device was likely converted to a “company owned” device in the portal. I had this happen with mine the 1st time I installed it. Needless to say, not a fan of my employer being able to lock me out of my 2000$ phone that I paid for, being able to manage apps etc, remotely wife… Problem was an inexperienced admin converted it by accident. Once it was reverted, I was able to remove the office apps etc.
Sure left a lot of privacy items out of their lists like locations, contact lists, browsing history, etc…
I would setup a second user profile on my android 12 device but its not even clear at that point.
This is for BYOD phones only.I have no issues with my Android enrolment due to separate work and personal profiles with clarity.I have outlook and Teams installed in my iPhone and configured with my corporate email address to access and emails and Teams .I am rolling out Outlook and Teams via Intune for users and in the end of test phase.The apps Outlook and teams do not have any issues for new users enrolling in Intune as it gets deployed through Intune and users can configure them in cases where they do not have them already installed. Here its get managed by Intune as it gets deployed through Intune. I have 2 questions
1.If outlook and Teams are already installed and if the iPhone is enrolled with Intune, would Intune not take care of managing both the apps which are already configured?
2.How do I know identify if Intune is managing the apps Outlook and Teams if they are already installed and if the phone is enrolled in Intune.I am asking this to ensure company data is protected.I am not configuring app protection policy here and believe it could be done without that and still protected in this case.
Is it at the discretion of the employer to require enrollment of Intune in order to access email on personal devices (and to what level of involvement they use it for)? We are currently locked out of email access unless we agree to enroll. We are in the process of transitioning out of the company (sold it) and migrating email used for both business and personal (currently on their Microsoft account over to a personal Microsoft account) but we cannot do so without access obviously. They are being cooperative so long as we agree to Intune. Which seems risky and invasive under the circumstances. So from what I just read in comments above, does this mean they can prevent this transfer and/or remove the email/data like Outlook entirely?
I have just discovered that my devices were added to intune without my permission. How do I get them taken off?
Thank you ! Very helpful.
I try to find the answer for hours to this question. For a company device where my employer push WhatsApp through the comp portal application, can my employer access and read my messages on WhatsApp ?
Thank you !
Here it is : 1234567890
Ure belcome!
Thanks Paul for the wonderful article.
Is there any option to customize the Company portal IOS MDM Privacy Message (What my company can see)?
Hi Team,
Is it possible to get notifications once sim cards are removed on intune managed company devices
I work as an Executive Assistant to a company that just rolled out InTune (where we previously used MobileIron).
Installing InTune was considered optional to the entire company, however it was REQUIRED if you wanted to access your email from your phones native mail app or Microsoft Outlook.
You didn’t have to install it if you wanted to check your work email from using a web browser (Chrome, Safari, Firefox, etc.).
Reading this article made me a bit more comfortable with what administrators can see, because I don’t really have the option opt-ing out of downloading the app because checking my email via web browser eliminates the ability to receive notifications of email – which I need due to the nature of the support I provide in my role.
Two things that did suck though – was that the app made me change my passcode to my phone. Which I found super annoying because the SIX-digit number had no repeating adjacent numbers nor did it have ascending or descending adjacent numbers. In addition, I didn’t have a passcode on my Apple Watch and InTune also forced me to create one for my watch.
The comment “However there’s no additional warning provided to the user of the device, so they would not know when a device has been changed from personal to corporate owned by an administrator.” is incorrect. This may have been the case at the time of writing but is no longer true. If the ownership of a device is changed from Personal to Corporate the end user is notified.
If it is your personal phone, is there any way to preclude this from happening
The end user is not notified. Source—me. My personal phone I use just for work was switched to corporate without my knowledge some time in 2021. I only noticed because I had acquired a newer phone to use for work and was just starting the transfer. The end user is not notified unless that user opens InTune and checks the status.
The comment that “However there’s no additional warning provided to the user of the device, so they would not know when a device has been changed from personal to corporate owned by an administrator” is incorrect. Perhaps it was at the time of the writing of the article, but if the ownership type is changed from Personal to Corporate the end user of the device is notified.
1) can they look at my personnel photographs on my personnel device?
2) can they look at my personnel emails (ie, my outlook may be configured to multiple business and personnel emails)?
3) can i still use my fingerprint, face, iris, etc.. to unlock my device or they disable this feature?
1: no
2: no
3: this depends on the way your company has configured Intune. By default fingerprint is not disabled, but I’m not sure about Face ID as I have never tested it myself.
What about when Outlook requires installing Intune CP to bring in your company email account, but… you’re not required to enroll, just simply have it installed? What access does the company have on my device?
That way your device remains a ‘personal’ device and the only thing that the company can manage is the company apps (Outlook, OneDrive etc.). They can not in any case look into photo’s, texts or emails, neither with fully managed devices, nor with app-managed devices.
They can however remove the company data from your device by simply removing the company apps, which requires the user to have to redownload the apps and re-authenticate (login using company credentials).
Paul,
I read the following on the apple website: “The only time your administrator can view the location of your phone is if they put your device into Managed Lost Mode.
When this mode is turned on, it reveals the location of the device to the administrator. If your administrator puts your device into Managed Lost Mode, your device locks and you will see a message on the lock screen. Your organization can’t track the location of the device without locking it and showing a notification.” (https://support.apple.com/en-us/HT202837)
This seems to imply that when the company tries to see my location, I receive a warning and that it cannot silently change my device from personal to company owned and seek on my location without me knowing?
So I’m a little confused on what you wrote, can you clarify or has this changed since your article?
I’m probably too late to this, but for people with the same question;
The user can see if a device has been locked by the Lost Mode. Also when Lost Mode has been deactivated, the user will see a message saying that the device was tracked and when.
As far as I know, your company can no longer change your device from personal to company owned without letting the user know.
My question is following. When you browse to some of your sites from your personal phone that is registered with company’s intune software, does traffic goes thru corporate site or no. I do not see any VPN icon on the phone while using however was just wondering how does the URL’s to corporate sites get resolved.
ex.
http://www.amazon.com – and perform some activity from your personal phone.
http://www.corporatesite.com – and perform some activity from your personal phone.
In the above two scenarios where does the traffic goes thru (is it thru your cell phone provider or corporate computers) and how does the corporate sites URL’s gets resolved and the pages are served.
Very informative article. Frankly speaking, after reading this article I’d prefer not to login to corporate emails through my personal devices. If they need to be responsive out of the office, they need to provide me a corporate device and I will use it only for work purposes/apps.
One question remains though. Imagine I register my device but after a while, I change my mind. How can I unregister my device such that I make sure MDM has ZERO access and control over my device afterward? I assume just a simple log out from email/OneDrive/etc would not unregister my device from MDM, does it?
The privacy message shown at the top of the article is criminally misleading. It does not mention that the company will be able to:
– reset the device to factory defaults
– remove the passcode
– bypass activation lock
– access location information
I understand why a company may need to perform these actions, especially on a company issued device. However, the level of control that can be exerted over a user’s personal device is far too broad. Users should not be required to relinquish control of their privacy just so they can use a corporate email account.
What is the difference between Office 365 MDM and Intune MDM and how are they linked / share information?
Hi! A Customer wants to have full administrative control over every mobile device of their personnel. The devices are corporate units, I’ saying they are given by the company and that is why they want to have full control. When they say full control they are talking about, for example, to have Audit or logging of the phone calls the user makes or receives.
Is that technically possible just with Intune?
Good article. Thank you!
Good article,
but i have now one problem.
I need to change the owner from personal to company device on a large part of all mobile devices.
Unfortunately I have not found a PowerShell string that can help more.
Do I have to manually readjust all devices?
Try Microsoft’s sample code that you can find here: https://github.com/microsoftgraph/powershell-intune-samples/tree/master/ManagedDevices
Perfect article, thanks Paul.
Once I configure in-tune and lets say after a while I decide not to use my personnel device for company’s work, can I remove it with out impacting my device and personal data?
That’s the idea, yeah.
Well, not so fast. I tried to do exactly that. Even though I deleted the app by the usual method of holding down the icon until it jiggled and the small “x” appeared in the corner, then proceeded to delete it, every day since I get a message from Apple App Store telling me Microsoft Intune wants permission to be installed on my device. And each time I hit “cancel”. I then checked all of my purchased apps on the App Store site, and sure enough it still shows I purchased Intunes. Is there some way to permanently delete that purchase from the App Store so I can stop the daily installation efforts?
You deleted the app, but you didn’t delete the management. Go to Settings – General – Device management and delete management. Regards!
Why should users trust theri company to not do “bad” with MDM/MAM while the company shows deep distrust to their employee by forcing an MDM/MAM application on their devices (especially if employee owned)? Did I miss something here?
If you don’t trust the company then don’t enrol your device in their MDM.
thats a double edged sword. They expect you to respond and answer email outside of the office, but give you no facility do to so. And when you ask for the facility, they tell you to use your own phone. Dont think that happens? I know Chase Bank did it to my (Vice President) brother.
ask them to provide you a phone
The company has a responsibility to protect corporate data and is tasked by it’s management and auditors with demonstrating due diligence in this area. It also has a responsibility to protect the privacy of it’s employees by properly protecting any personal data it holds. The only way it can meet these responsibilities while providing access via personal devices (which could include access to annual Leave Records, Work Rosters etc. in addition to sensitive company data) is through use of an MDM to ensure minimum protection levels are applied on the device. The general motivation for companies to provide access for employees is to improve ease of use for them for information access and carrying out certain functions. The company will also obviously also expect to see benefits in terms of employee satisfaction and retention and possibly also productivity. As outlined above it is the employee’s choice to enrol the device for these benefits and requires a degree of trust that the company will not abuse any privileges it has. Provided the company has documented the appropriate Policy and Privacy statements (which should be accessible to employees) it would expose itself to very significant litigation and costs for any breach of trust.
EXCELLENT comment.
Good article, thanks.
So there’s one question I can’t seem to get a straight answer to, maybe you can help.
On my corporate-owned device, I have my company email (O365) data as well as my personal email, also from O365 but my own tenancy.
How can (or does) Intune differentiate between my [O365] data and corporate data?
Cheers,
S
It’s app and data source awareness.
So let’s say you configure Intune to deploy the mail profile for your company email to your users. Intune is aware that is the “managed” corporate profile, and that the other ones are “unmanaged”, and will only delete the one it manages.
Similar awareness with other apps like OneDrive, it knows that the data syncing to/from the corporate OneDrive for Business account is corporate, but your personal OneDrive is personal.
The same awareness is how it prevents you copying data from OneDrive to Dropbox, if you’ve got policies preventing that.
It can’t magically tell the difference between two different photos in your camera roll, that sort of thing.
I don’t know if that’s the best explanation but hopefully that helps.
I have forgot my passcode, How can I reset without my personal data loss. Is their any solution???