As our business workforce becomes more mobile every year, and security risks for corporate data increase, it’s important to consider how you will manage mobility for your organization. Office 365 customers have a choice of solutions that can be used for mobile device management (MDM) and mobile application management (MAM). Each has different features available, with different strengths and weaknesses.
Some of the considerations that come into play include which devices and operating systems will need to be managed, and who will own those devices (BYOD vs corporate). We also need to consider whether non-Microsoft applications such as SaaS apps or custom business apps need to be managed. Diversity in the user population is also an important consideration. For some organizations a single approach to mobility is required, whereas other needs to apply different policies and configurations to different groups of uses. Specific compliance requirements are also important, as some organizations fall under strict government or industry regulations.
The solutions that we can choose from are:
- Exchange ActiveSync
- Office 365 MDM
- Microsoft Intune
In addition to those Microsoft solutions there’s an extensive range of third party mobility solutions provided by other vendors. For this article I’m going to focus solely on the Microsoft solutions, but as part of your own assessment you should certainly evaluate third party options as well.
Exchange ActiveSync
Exchange ActiveSync has been available for mobile device management since the very early days of on-premises Exchange Server, and it is also available in Exchange Online. ActiveSync provides a basic MDM solution that allows you to configure policies that devices should comply with before they allowed to connect to Exchange mailboxes. The policies cover basic device security options such as PIN/passcode strength, encrypted storage, and some features such as cameras. However, ActiveSync relies on the device honestly reporting its own compliance with the policy, so it’s not a guarantee that the policy requirements will actually be met.
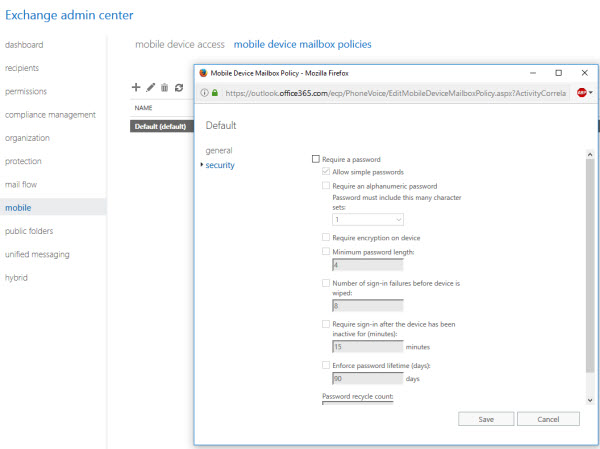
There are also ActiveSync controls for either allowing, blocking, or quarantining (ABQ) a device or application based on characteristics such as the device family, operating system, or specific device IDs. You can read more about the ABQ process here.
For Office 365 customers ActiveSync is a quick and easy way to access email on mobile devices. As long as you have configured the Autodiscover records in DNS when you set up your Office 365 tenant (Microsoft provides the exact DNS records to use), mobile devices will be able to connect to Exchange Online mailboxes.
In fact, even devices that are not secured with a PIN or passcode will be able to connect, because the default mobile device policy in Office 365 is quite weak. If you plan to use ActiveSync for mobility you should review those policy settings and consider strengthening the policy requirements for devices.
One of the long-standing weaknesses of ActiveSync has been the inability to perform selective wipes. If a remote wipe was issued to an ActiveSync device, the entire device would be wiped and the user could potentially lose personal data. This became less of a problem once applications such as Touchdown or Outlook for iOS and Android became available, because the application itself became the “device” as far as Exchange Online is concerned. Any remote wipe issued to the application would only erase application data, not the entire mobile device. Microsoft made further investments in the development of the ActiveSync protocol and released EAS 16.1 which includes the ability to perform selective wipes (or “account-only wipes“) for compatible devices. Apple added support for EAS 16.1 in iOS 10.
ActiveSync works for connectivity to Exchange Online mailboxes for email, calendar, contacts, notes and tasks. ActiveSync is not used for other Office 365 workloads such as SharePoint, OneDrive, Planner, Teams, and so on. If your users are licensed only for an Exchange Online mailbox then you might consider ActiveSync to be a suitable solution. If you are using more features of Office 365 than just Exchange Online, then you should consider securing mobile access using Office 365 MDM or Microsoft Intune.
Office 365 MDM
Office 365 includes a mobile device management capability that extends beyond what ActiveSync can provide. Office 365 MDM is included free with Office 365 business and enterprise subscriptions. While ActiveSync takes a device-centric approach to mobile device management, and only works for Exchange Online, Office 365 MDM is able to enforce management and security policies on devices and applications that are access other Office 365 workloads as well, for example OneDrive for Business. MDM policies can also be targeted at groups for ease of management.
The security settings that can be applied include the same PIN/passcode and device encryption options as ActiveSync provides, with additional detection of “jail broken” or “rooted” mobile devices. Office 365 MDM is also capable of managing the email profile on iOS devices and block users from creating their own profiles.
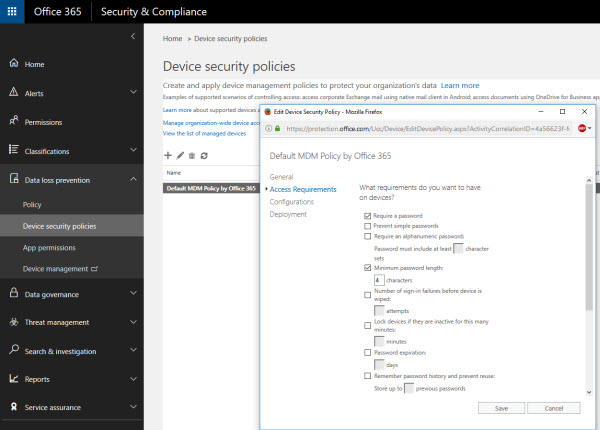
Selective wipes are also available in Office 365 MDM. Even though ActiveSync can perform account-only wipes for devices that are compatible with EAS 16.1, that still leaves a large number of older devices and applications among the user population that are not compatible. Office 365 MDM can perform selective wipes without the requirement of EAS 16.1 compatibility. However, very old devices are not compatible with Office 365 MDM at all. The current supported devices include:
- iOS 7.1 or later
- Android 4 or later
- Windows Phone 8.1 or later
- Windows 8.1 and 8.1 RT (limited to ActiveSync connections only)
- Windows 10 and 10 Mobile (for Azure AD joined devices that have enrolled in Office 365 MDM)
Compared to ActiveSync, Office 365 MDM requires more initial setup and configuration. MDM is not activated by default, and an APNs certificate needs to be acquired from Apple for supporting iOS devices. The APNs certificate must also be renewed each year to prevent MDM-enrolled devices from losing access. I’ve written about the Office 365 MDM process in this series of articles:
- Activate MDM for Office 365
- Create MDM policies
- Enroll Apple and Android devices
Microsoft Intune
Microsoft Intune is paid product that provides cloud-based mobile device and application management. Intune is available as a standalone license, and is also included in the Enterprise Mobility + Security (EMS) license. Intune has all of the capabilities of ActiveSync or Office 365 MDM but also offers a range of other features. Intune can be used to deploy business applications and application store apps to devices, as well as deploy configuration items such as certificates, VPN profiles and wifi network details. Web browsing from mobile devices can also be secured using the Intune Managed Browser app.

Intune also offers mobile application management (MAM) capabilities for preventing data being copied or saved from applications such as Word or OneDrive for business into other apps on managed devices. For example, you can allow users to download business documents using OneDrive, and edit them in the Word app on their device, but still prevent them from saving the file to their personal Dropbox app on the device. MAM policies can be applied to unmanaged devices by requiring users to access Office 365 services only from applications such as Outlook and OneDrive that are Intune-aware, and is often referred to as MAMWE (Mobile Application Management Without Enrolment).
Intune is not just for mobile devices, it can also be used to manage Windows PCs and macOS computers. Intune is also capable of operating in a hybrid mode with System Center Configuration Manager (SCCM) to unify the management of corporate on-premises and mobile/BYOD devices.
The capabilities of Intune can also be combined with Azure Active Directory Conditional Access policies to control access to Azure AD and Office 365 applications by requiring users to connect from devices that meet the organization’s compliance policies.
In an upcoming series of articles we’ll look closer at the capabilities of Intune and how to use it for specific scenarios.



Pingback: Embrace Outlook Mobile or Stay with Exchange ActiveSync?
Thanks Paul for the wonderful write up. I was also wondering when time permits if you could write some thing on ADAL aslo? Generic would be about step by step activation for all O365 Workloads and benefits of ADAL. how can it prevent hackers trying to authenticate using your UPN/Email address and access your mailbox or workload etc.
Mixed messages about support of InTune for OSX devices. What’s the real position?
Skip it… Intune is not a true Enterprise Mobility Management system, it’s a Enterprise Microsoft Management system. If you want something to manage iOS, Windows 10, Office365, Android and OSX look at MobileIron which is what we use or AirWatch.
For IOS/Android you have to confirm each app installation. Enrollment needs to be done via Company Portal app. For Win10 only msi can be deployed, no exe. Imo not many settings/policies are available (luckily with admx-backed policies there are some more added in 1703).
We’ve deployed intune to all our mobile devices with a policy similar to what we did in on premise exchange 2010. Unfortunately we’ve had some quirky behaviors with select devices. For example, our policy is for a simple (at least) 4 digit pin , but on some of our Android devices, if the want to change their initial pin, it requires a complex desktop style password. Only way to resolve it, I’ve found is remove the device administration, change the password, then re enable intune.