Just a few years ago, there was a widespread belief that Active Directory (AD) was on the brink of obsolescence, destined to vanish from the IT landscape. Yet, as we mark the 25th anniversary of its 1999 preview release, it’s clear that such predictions couldn’t have been further from the truth.
Despite the rise of cloud-based identity services, which have led to Active Directory assuming a role as a secondary identity broker and the reallocation of many of its duties to other systems, Active Directory has not only persisted but continues to reign as the preeminent directory service for on-premises identity infrastructure with around 90% of Global Fortune 1000 companies depending on it for their identity management needs. Moreover, Microsoft’s strategic investments in enhancing AD’s scalability, performance, and security underscores a continued commitment to its future.
As we commemorate this significant milestone, it’s an ideal opportunity to revisit the origins, evolution, and the pivotal role AD continues to play in shaping IT infrastructures across the globe. In this blog, we’ll embark on a journey through the history and enduring significance of AD.
The Intriguing Pre-History of Active Directory
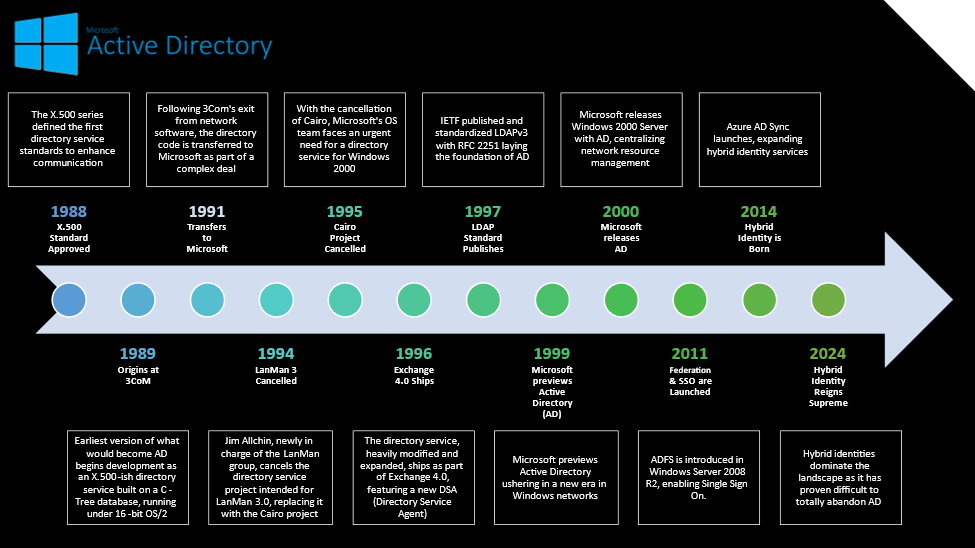
The journey of AD into the realm of technology is a tale of innovation, transformation, and strategic redirection. Originally born within the confines of 3Com in the late 1980s, what would become the foundational elements of AD started as an ambitious yet incomplete X.500-like directory service, operating on a C-Tree database under the then-popular 16-bit OS/2. This early venture into directory services by 3Com was short-lived, as the company decided to withdraw from network software endeavors by 1990. This led to the transfer of the directory code to Microsoft in 1991 through a complex arrangement, marking the beginning of AD’s journey under Microsoft’s stewardship.
Upon acquisition, Microsoft’s LAN Manager group intended to incorporate this directory service into LAN Manager 3.0, embarking on an endeavor to port it to the JET Blue (Microsoft’s Extensible Storage Engine) ISAM (Indexed Sequential Access Method) database and construct an RPC front end that complied with the X/Open XDS API (XDS, which stands for Directory Services, is a technical standard used for interaction with these services.) However, the project faced a significant turn when Jim Allchin, newly in charge of the LAN Manager group, decided to cancel LAN Manager 3.0 and its directory service project in favor of the Cairo project, which envisioned a directory service completely divergent from the X.500 standards, integrated within the Cairo file system.
Despite the Cairo project’s ambition, it was ultimately shelved in 1995, leaving a gap in Microsoft’s strategy for a directory service in its upcoming Windows 2000. In a swift pivot, developers from the Exchange Directory Service (DS) team, just after releasing Exchange 4.0 in 1996, copied the DS sources to the Windows group, thereby leading to the conception of what we now know as AD. This version of DS had evolved significantly from its initial form, with extensive modifications and additions, such as a MAPI RPC interface, a query engine, and a modifiable schema, rendering the original code almost unrecognizable.
A fascinating aspect of AD’s development was its clear delineation from other directory services and projects. Contrary to what some may assume, AD did not stem from Novell NDS/eDirectory, Banyan StreetTalk, or even Microsoft’s own Cairo project. Instead, it emerged from the ashes of previous endeavors, informed by other Microsoft internal projects and competitive insights. Additionally, while LDAP (Lightweight Directory Access Protocol) support was later added to both Exchange and Windows 2000’s directory services, AD’s development was notably distinct and separate from Exchange’s LDAP efforts, with only minimal crossover in personnel rather than direct code sharing.
This backdrop of AD’s emergence was set against a competitive technological landscape. At the time, various players were offering alternative solutions to identity management challenges. Novell’s NetWare and NDS were notable for their mature, multi-platform directory services. LDAP-based directories, such as OpenLDAP and Sun Microsystems’ solutions, offered standards-based alternatives appealing for cross-platform interoperability. IBM’s Tivoli Directory Server and Oracle Internet Directory also provided enterprise-grade directory services, emphasizing large-scale performance and robustness.
We asked Derek Melber, veteran author, speaker, and 19-time Microsoft MVP for Identity & Access, how would you characterize Active Directory’s impact on the market compared to its competitors at the time of its inception?
“Active Directory was a massive game-changer for organizations. At that time, only Novell offered anything like what Microsoft AD provided. Security was not the major concern then; rather, management was. Group Policy was a radical new upgrade from Windows NT’s System Policy. I worked on many migrations from Windows NT to Windows Active Directory. There was a period when the competition tried to stay relevant by integrating with AD, but all the competitors, like Novell Netware, IBM SNA servers, and Banyan, could not keep up with the rapid deployments of Microsoft AD and were soon pushed out of the market.”
Derek Melber, 2024
Despite these competitors, AD carved out its niche by providing a tightly integrated solution for Windows environments, leveraging the widespread adoption of Windows server systems. It offered centralized management, scalability, and policy management tailored to the needs of Microsoft-centric IT infrastructures. The successful integration of various technological components and strategic redirections Reinforced AD’s evolution from its initial conception at 3Com to its indispensable role in Microsoft’s product lineup.
The Journey from On-Premises to Hybrid Cloud
In the emerging stages of its existence, AD brought about a paradigm shift in the way organizations orchestrated their IT ecosystems. It supplanted the disjointed and intricate management tasks with a consolidated and user-friendly methodology. As Bill Gates envisioned and conveyed about Windows during his 1994 Comdex keynote, “information at your fingertips”. The advent of domain controllers, organizational units, and Group Policy objects presented IT administrators with unparalleled authority over their networks and resources.
AD was first previewed by Microsoft in 1999 and officially released with Windows Server 2000 edition. AD represented a significant upgrade from traditional domain services, offering a multi-master model that allowed for the management of directory functionalities, including updates and changes, across any domain controller within a domain. This capability was one of the key features distinguishing AD.
The concept of LDAP was developed after the founding of Microsoft, drawing on the ITU-T‘s X.500 standards first published in 1988. LDAP itself was introduced in the early 1990s as a more accessible alternative to the X.500 Directory Access Protocol (DAP). This shows the deep roots and long-standing evolution of the technologies that eventually culminated in the creation of AD.
Over the years, AD has continuously evolved, enhancing its features, and simplifying administration with each new release of Windows Server. Although there was a period where active development shifted towards cloud initiatives, Microsoft has recently reaffirmed its near-term commitment to AD. Recognizing AD’s critical role in today’s identity management landscape, Microsoft has issued updates aimed at bolstering security, stability, and performance, addressing the needs of major customers, and resolving longstanding issues. Despite the proliferation of cloud-based solutions, the on-premises version of AD still commands a significant presence, being utilized in approximately 90% of global Fortune 1000 environments. This enduring dominance underscores both its robust design and pivotal contribution to the evolution of IT infrastructure management.
Challenges and Criticisms
AD has also faced its share of controversies and criticisms over the past 25 years, both from competitors and customers. Some of the common issues that have been raised are:
Security Vulnerabilities: AD remains a prime target for cyberattacks, with vulnerabilities leading to significant organizational breaches. Notably, global ransomware damages alone are predicted to exceed $265 Billion By 2031 according to Cybersecurity Ventures. The WannaCry and NotPetya ransomware attacks in 2017 exploited the EternalBlue vulnerability and Mimikatz to propagate through networks, encrypting data. Similarly, starting in 2015, the SamSam ransomware leveraged vulnerabilities in public-facing systems to infiltrate networks and escalate privileges within AD. The SolarWinds Supply Chain Attack in 2020 demonstrated another attack vector, with compromised software updates enabling network infiltration and AD targeting for elevated access. Additionally, vulnerabilities like PrintNightmare in July 2021 and ZeroLogon in 2020, which allow attackers to impersonate any computer including domain controllers, further reinforce the urgency for robust AD security protocols. These incidents highlight the necessity for vigilant patch management and continuous monitoring to safeguard sensitive data and ensure organizational integrity.
Complexity and Cost: Windows and AD have long faced criticism for their complexity and the associated costs of deployment, maintenance, and troubleshooting. These systems require specialized skills, hardware, and software for effective operation, often presenting challenges in staying updated with frequent patches and updates. Moreover, the aging workforce of skilled AD professionals, coupled with the prioritization of cloud technologies by newer generations, has further compounded these challenges.
Additionally, over the past 25 years, best practices for AD forest models have undergone significant evolution to meet changing organizational needs and security landscapes. Traditional models, such as the Single Forest Model, have given way to more nuanced approaches like the Restricted Access Forest Model (ESAE/Red Forest). Although ESAE itself has been retired, newer models have emerged, such as the ‘Pristine AD DS Forest,’ which assumes compromise and recommends a non-migration strategy to move critical assets to a ‘Life Boat’ or ‘Secure Cell’ .
Moreover, Microsoft recommends that organizations with ESAE / hardened forests should adopt the modern privileged access strategy using the security rapid modernization plan (RAMP) guidance. This approach, along with the adoption of the Zero Trust Model, aligned with contemporary security paradigms, signifies the importance of a least privileged access strategy by segmenting networks into isolated zones. This not only reduces lateral movement but also minimizes the blast radius when attacks occur. Despite these advancements, the ongoing criticism of complexity and cost remains a core challenge for AD.
Lack of Flexibility and Innovation: AD is sometimes seen as a legacy technology that is not well-suited for the modern and dynamic IT landscape. In fact, the results from Gartner’s 2021 survey titled “AD in Transition” revealed that “AD remains a critical system for an overwhelming majority of organizations; however, its place in their IT landscapes is undergoing a profound change.” Given that AD’s role is diminishing, organizations are grappling with several questions. They are considering its potential replacement, integration with cloud platforms, and the optimal migration approaches for AD-integrated applications and systems. Additionally, they are exploring the availability of cloud alternatives for managing Windows devices within on-premises AD environments.
AD has been accused of being too rigid, inflexible, and slow to adapt to the changing needs and expectations of users and organizations. It has also been criticized for lagging in innovation and offering limited support for non-Microsoft platforms and applications. Notably, prior to the latest updates rolled out on April 28, 2023, and August 8, 2023, the last enhancement to AD Domain Services was introduced alongside Windows Server 2016 in October 2016, over six years prior.
The vulnerabilities and criticisms surrounding AD have prompted some customers to explore alternatives, ranging from open-source solutions like FreeIPA and OpenLDAP to cloud-based services such as Entra ID, Okta, and Ping Identity. Many organizations with existing AD infrastructure have adopted hybrid models, combining on-premises AD with cloud-based identity management platforms to address their current needs and security concerns. According to Microsoft as far back as 2018, 75% of tenants with more than 500 employees using Microsoft 365 are synchronizing their on-premises Windows Server AD with Entra ID, up from 59% nine months earlier. However, there continues to be a sizable push towards reducing reliance on AD and transitioning applications, identities, and devices to cloud management platforms. Despite this shift, AD remains a widely used and trusted solution for numerous organizations, with Microsoft making strategic investments in its ongoing development and improvement. As the IT industry continues to evolve, so does AD, at least for the time being.
For the 25th anniversary, I reached out to Sean Metcalf (PyroTek3), CTO of Trimarc Security and Microsoft Certified Master in AD to ask him, considering the current landscape of identity security, how do you perceive the role of Active Directory in modern organizations?
“Despite the cloud surge, Active Directory’s critical role endures, although challenged by vulnerabilities, migration difficulties, and security lapses that have led to some major breaches. Yet a strong focus on identity security is making Active Directory pivotal in enhancing defenses and thwarting attacks.
Sean Metcalf, 2024
Staying Relevant in the Future?
The 25-year journey of Active Directory showcases resilience and adaptation, filled with significant milestones, challenges, and constant evolution. While celebrating its achievements, it’s crucial to acknowledge the vulnerabilities and criticisms that have punctuated AD’s journey. As we’ve seen, major security breaches have cost millions and crippled organizations worldwide, highlighting the urgent need for robust security measures. Additionally, AD’s design complexities, maintenance challenges, an aging workforce of skilled professionals, and the swift move toward cloud technologies present significant hurdles for organizations dependent on AD for identity management.
Despite these obstacles, AD remains a cornerstone of identity infrastructure. AD’s presence is significant in modern IT environments, albeit amidst a changing landscape where organizations are increasingly embracing cloud-based solutions and hybrid models.
AD’s future success depends on addressing current challenges and adapting to emerging trends. For instance, the transition towards a more Decentralized Identity (DCI) infrastructure could require AD to undergo further adaptations in its architecture and functionality or cease to be relevant entirely. Other trends like the march towards a passwordless world may further render AD less a candidate for innovation but a catalyst for an alternative in on-premises authentication and access management. As Microsoft continues to address critical issues such as Kerberos and NTLM vulnerabilities, the trajectory of AD will be shaped by its ability to meet the ever-changing needs and security landscape challenges of organizations worldwide.
Looking ahead, it appears that AD is poised for ongoing evolution and adaptation. Recent investments by Microsoft in security, performance, and scalability indicate a commitment to meeting the evolving needs of IT infrastructures in the near term. We sought Microsoft’s insights on AD’s future, but they declined to elaborate beyond publicly available information, which is minimal. Despite this, the consensus among experts I consult is that AD will remain relevant for at least another decade. However, this outlook comes with a caution: sustaining AD as it currently exists could present significant challenges. At 25 years old, AD wasn’t designed for the security demands of today’s landscape. Alex Weinert, Microsoft’s VP of Identity Security, succinctly captured the issue, stating, “AD is where we are being attacked.” This vulnerability arises from weak configurations, bad practices, or neglect, making AD an easy target for malicious actors to compromise and then move laterally into the cloud.
As organizations delve into the complexities of digital transformation, the importance of identity management becomes increasingly clear. Although AD’s future remains uncertain and might be replaced with a more lightweight version, the demand for on-premises authentication and authorization will persist. High-security scenarios in government, research, and manufacturing sectors underscore the impracticality of a fully cloud-managed model. Thus, it’s imperative for Microsoft to provide clarity on AD’s roadmap, allowing organizations to plan their on-premises identity management strategies effectively. Should AD be phased out, transitioning away from its extensive dependencies will require considerable time and effort for organizations.
In closing, we extend our heartfelt gratitude to the visionaries, developers, administrators, and countless others who have contributed to the creation, evolution, and enduring legacy of AD. Happy 25th Birthday Active Directory!


