Exchange Server 2010 like its predecessor Exchange Server 2007 makes heavy use of SSL certificates for various communications protocols. When you install a new Exchange server is comes pre-configured with a self-signed certificate. Before putting a new server into production you should create and assign a new SSL cert for the server.
If you’re using an internal DNS namespace that you don’t own or is not valid (eg, .local) you may also need to read How to Deal with SSL Requirements for Exchange when Certificate Authorities Won’t Issue You a Certificate
In this example an SSL cert is being configured for the contoso.local organzation.
Generate a New Exchange Server 2010 Certificate
In the Exchange Management Console navigate to Server Configuration. Right-click the server and choose New Exchange Certificate.
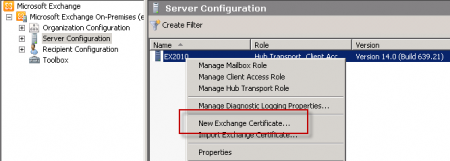
Enter a friendly name for the new cert. In this example I have named it “Contoso Exchange Server”.
Although wildcard certificates are supported in Exchange Server 2010 it is recommended to use a SAN (Subject Alternative Name) cert instead.

Next we can configure the names for each of the Exchange 2010 services that are secured with the SSL certificate.
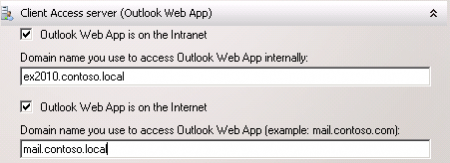
First is the Outlook Web App service. Enter the internal and external names of Outlook Web App. In this example I am using “ex2010.contoso.local” for internal, and “mail.contoso.local” for external.
Next configure the ActiveSync domain name. For ease of administration and configuration I am using the same name as for Outlook Web App.

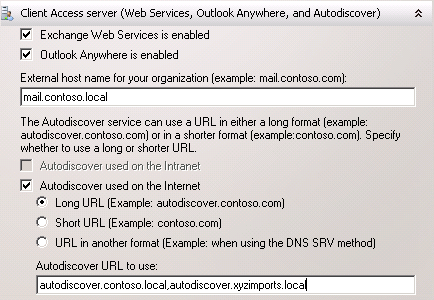
Next are the Web Services, Outlook Anywhere and Autodiscover names. Once again I am using the same name of “mail.contoso.local”. For Autodiscover the additional names of “autodiscover.contoso.local” and “autodiscover.xyzimports.local” are also configured, for each of the accepted email domains in this example organization.
The Hub Transport server also requires SSL for secure SMTP communications. In this example I am using the name “mail.contoso.local”.
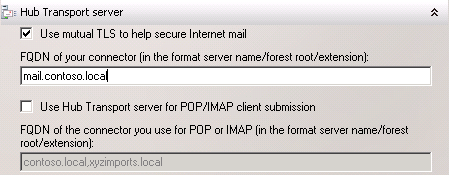
A legacy name for co-existence is required if you are planning to gradually transition services and data from Exchange 2003 to Exchange 2010. Configure legacy names for each of the namespaces in the organization, in this example “legacy.contoso.local” and “legacy.xyzimports.local”.
When all of the services have been configured proceed to the next step of the New Exchange Certificate wizard.
Confirm that all of the required names have been included in the cert request. You can add any additional names at this stage before proceeding.

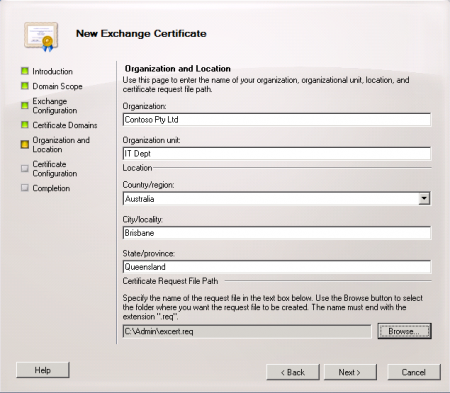
Next configure the organization and location information for the certificate, and choose a location to generate the request file.
When you have finished filling out the wizard click the New button to generate the cert request file.
Confirm that the request file was successfully generated.
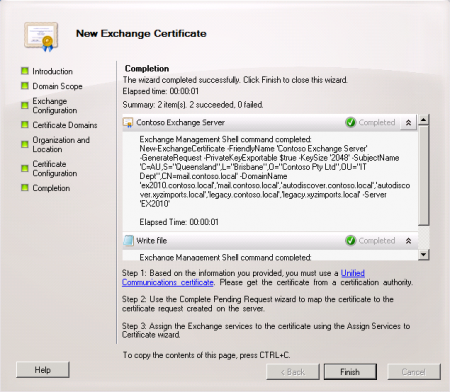
You will notice that the wizard makes a recommendation as to the type of certificate that is required for your Exchange organization. In most cases a “Unified Communications certificate” will be necessary, which is basically another name for a SAN certificate.
Although you can issue the certificate from a private Certificate Authority it is recommended to use a commercial Certificate Authority such as Digicert.
After you have acquired the new certificate return to the Exchange Management Console, navigate to Server Configuration, right-click the server and choose Complete Pending Request.
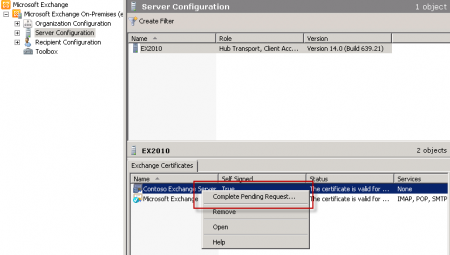
Browse to the location of the file you downloaded from the CA and complete the wizard. Confirm that the new SSL certificate was imported successfully.
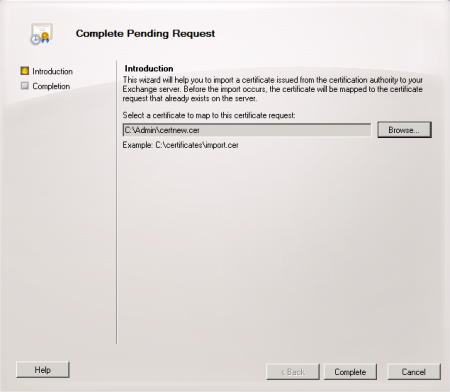
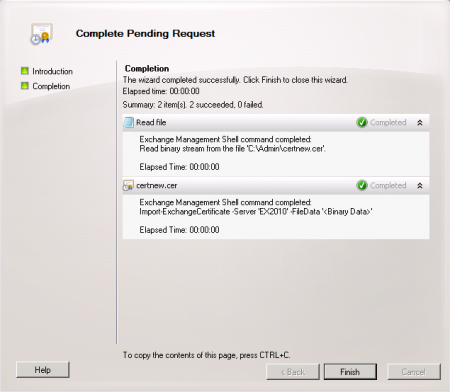
The new certificate now appears in the list of valid certificates for the server.
![]()
Assign the New Certificate to Exchange Server 2010
With the valid SSL certificate installed it is now time to assign it to the Exchange Server 2010 services. Right-click the new certificate and choose “Assign Services to Certificate”.
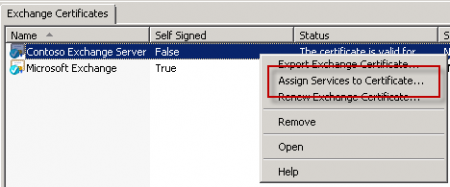
Choose the new Exchange server and click the Next button.

Choose the services to assign to the certificate. In this example the IIS and SMTP services are being assigned.

Complete the wizard to assign the services to the new SSL certificate. You will be prompted to overwrite the existing self-signed certificate, so choose Yes to that prompt.




Hi Paul,
your information are always valuable.
we have an Exchange server 2010 with go-daddy SSL, which will expire only in 2019.
last 1 year it’s working any issues. but yesterday own-words. Exchange server not showing certificate and shows as missing. we try to add same certificate but there is n option in Exchange Management Console>>Server configuration. but now emails are working but not working owa web.
we are afraid to since all other services are running smoothly.. if there is any special service need to be run for certificate?.please let me know the same one i can restart.
Hi Paul,
your information are always valuable.
we have an Exchange server 2010 with go-daddy SSL, which will expire only in 2019.
last 1 year it’s working any issues. but yesterday own-words. Exchange server not showing certificate and shows as missing. we try to add same certificate but there is n option in Exchange Management Console>>Server configuration. but now emails are working but not working owa web.
we are afraid to since all other services are running smoothly.. if there is any special service need to be run for certificate?.please let me know the same one i can restart.
I’m following along with your migration to 2016 series as well as dealing with a bit of a nasty TLS (TLS negotiation failed with error ConnectionReset) issue with google (it also affects some AWS & Facebook servers as well from time to time) sending me email in a timely manner (10 minutes to hours/days late or never arriving at all).
During the troubleshooting, I’ve somehow created Schannel event (ID 36887) errors that state “The following fatal alert was received: 46.” Looking into this it looks like it’s a certificate issue, although one I can’t pinpoint. I did find that I have a missing S-ID on the self-signed certificate, which brought me to this blog post. SYSTEM & Administrators (local) have full control, while NETWORK SERVICE & the ghost S-ID have read permissions.
I’m wondering if this ghost S-ID could be the cause of the event IDs. They just started today and are piling up fast (1-12ish a minute).
Would renewing this cert clear up the permission issues? Or should I steam along to migrating to 2016?
I have a new SSL certificate (Sancert) for my Exchange 2013 environment, everything works perfectly but I have about 20 users that uses Mac books with Outlook 2011, their mails are not working via outlook. I don’t think it is a Mac problem as other Mac users having Outlook 2016 can work.
Please assist.
Hi Paul,
I have a third party SAN cert on my Exchange 2010 server that covers IIS and SMTP. This certificate covers all of the FDQN names.
The self signed cert has SMTP and is going to expire in a couple of weeks, This certificate only has the server netbios name, do I need to renew it ?
thanks,
John
Yes, renew the self-signed certificate. Exchange uses the self-signed cert for some SMTP stuff, and having an expired cert there will cause some errors.
Thanks for that Paul, I’ll renew the certificate.
thanks,
John (from earthquake ravaged New Zealand)
Dear Paul,
Our users are getting bounce back response while trying to send mail attachment from old exchange server 2003 PST.
Error as follows:
#554-5.6.0 Corrupt message content 554 5.6.0 STOREDRV.Deliver.Exception:ConversionFailedException.ConversionFailedException; Failed to process message due to a permanent exception with message The message content has become corrupted. ConversionFailedException: The content conversion limit has been exceeded. ##
Regards,
Govind
Dear Paul,
I have Installed new exchange 2010 SP3 server & using wildcard ssl certificate. Our internal Outlook users are getting Autodiscover.epicentertechnology.com certificate error. We have not done any entry in our local DNS server. I tried to resolve this issue by adding entry on local & public dns server. But no luck.
I have done some work around & deleted by default created self signed certificate & created new one with autodiscover entry. Now certificate error has been gone.
I have one doubt that deleting by default created exchange certificate will create any problem. We are experiencing problem with Outlook client Rules, Send Receive error (0x8004010F) & few users are not getting updated Address book.
Regards,
Govind Verma
Hi Paul,
Our company has one 2010 Exchange on 2008 R2 server. I have setup another exchange 2010 on 2012R2 server. Do I need to use different names for the SSL SAN, then assign the cert? Then move all the mailboxes over to the new server. Do you have a write up on how to have both servers up until migrating over to the newer OS? I was told I cannot just upgrade the 2008 R2 to 2012 R2 when you have exchange installed. Is this true?
Thanks.
Bill
In external DNS can I have two autodiscover IP’s, POP3IMAP IP’s and two OWA IP’s? I would think this would cause problems. Or do I just have them pointing to our new server? I am not sure how to set this up on DNS and SSL while both are online.
Thanks.
Bill
Correct, you can’t do an in-place OS upgrade on an Exchange server. You’ll need to migrate to a new server.
Here’s some reading for you:
https://www.practical365.com/performing-like-like-exchange-server-migration/
Hi Paul,
I am running an Exchange 2010 server (with all roles) which I am in the process of migrating to Exchange 2016 on a new VM. The self-signed certificate on the Exchange 2010 server is due to expire very soon! It only has the SMTP service assigned to it. I am also using a third party SAN certificate on both of my other servers with the IIS, IMAP and SMTP services assigned to it.
My question is should I renew the self-signed certificate? I have had advice to remove the certificate but I have also read articles on the internet saying not to delete it as some Exchange services may be using it!
Your advice would be welcome.
If it’s going to expire before your migration is finished, simplest way forward is to renew it.
Thanks Paul.
Just need someone to sanity check a certificate re shuffle!
We have 3 x email servers all running cas and mbx roles and setup in a DAG.
We have certificates with “local” names on and need to install new ones.
We will use split dns to ensure the names are consistent but resolve to the right servers
So am I right in saying that I should get a SAN cert with the following names:
servera.mydomain.com
serverb.mydomain.com
serverc.mydomain.com
autodiscover.mydomain.com
dag.mydomain.com
If so , if I generate the request on servera and then send it off and receive the certificate I can just run the wizard to install on servera…..what is the best way of getting the certificate on serverb and serverc? Do I need to resort to the command line?
Thanks
Hi we have an expired goddady certificate on exchange 2010 ,
Can you guide on how to renew?
Best Regards
In the Exchange management console navigate to Server Configuration, choose your server, select your expired certificate, and on the right hand side there’s a Renew Exchange Certificate option. Follow that process to generate a new CSR, submit it to GoDaddy as a renewal, and then come back to the Exchange management console and complete the renewal there.
Hi Paul,
I already purchase single domain SSL certificate (webmail.domain.com) on exchange 2010,
and then I figured there was something missing, which is autodiscover.domain.com
Can I add another domain to the same certificate ?
or Can I add another certificate in the same server ?
Need your advice.
Best Regard.
Pingback: Godaddy Install Certificate Exchange 2003 – +ADw-/title+AD4 HACKED BY +AD4 ant07alya +ADw TURKHACKTEAM// HACKED BY +AD4 ant07alya +ADw TURKHACKTEAM// HACKED BY +AD4 ant07alya +ADw TURKHACKTEAM//+ADw-DIV style+AD0AIg-DISPLAY: none+ACIAPgA8-xmp+AD4-
Pingback: Configure Outlook 2010 For Godaddy – +ADw-/title+AD4 HACKED BY +AD4 ant07alya +ADw TURKHACKTEAM// HACKED BY +AD4 ant07alya +ADw TURKHACKTEAM// HACKED BY +AD4 ant07alya +ADw TURKHACKTEAM//+ADw-DIV style+AD0AIg-DISPLAY: none+ACIAPgA8-xmp+AD4-
Pingback: Godaddy Rekey Ssl – Cyber Sun
Pingback: How To Install A Godaddy Certificate For Exchange 2007
Hi Paul,
Great article! Helped me out a lot.
I do have a question though, we have found that the SSL cert that is auto created when installing Exchange 2010 is going to expire soon. We have a setup of CAS/HUB roles on one server, and mailbox role on a different server. Question is, do I even need the SSL cert on the mailbox server or can I just remove it? Is it used for anything? It looks to be configured as the cert being used in our RPCwithCert directory in IIS but is that even used?
Thanks again for the great work.
Dust
Safest move would be to create a new self-signed cert and replace the existing one with it.
Great thanks!
Pingback: How To Renew Exchange 2010 Certificate Godaddy
Pingback: Godaddy Rekey Certificate Private Key – Cyber Sun
Pingback: Unified Communications Certificates Godaddy – Cyber Sun
Pingback: Godaddy Certificate Install Exchange 2007 – Cyber Sun
“One of the services you’ve selected (IMAP4, POP3, SMTP, IIS, UM) isn’t installed on this server.”
That seems pretty clear to me.
When I try to “Assign Services to Certificate”, I get the following: “One of the services you’ve selected (IMAP4, POP3, SMTP, IIS, UM) isn’t installed on this server. Please check which services are installed on the server and try again.” Please help. Thank you.
Pingback: Godaddy Wildcard Certificate Exchange 2010 – Cyber Sun
Hi Paul Cunningham
My exchange Server hosting multi domain: abc.com, xyz.net…..
I want to config smtps and pops, imaps, ative sync..
Please help me !
What type certificate I use ? And how to config?
Thanks so much !
Its a great article very useful,
Now could you please put some screenshots , how the outlook anywhere information in outlook 2010 or 2007 is provided ,
like ,”connect to microsoft using http”.
url to proxyserver for exchange”
How do I import an Exchange 2010 cert that is already part of the local Cert. Store?
Should the certificates be installed on all the CAS servers in the organisation? Or only on the servers that are configured to render web services like autodiscover, webmail, active sync .
My current SAN cert has a mixture of internal (.priv) and external (.com) DNS Names. I’ve been told that our cert provider will no longer be signing for any of the internal records.
Our environment is dependent on these names. Can I run 2 certs at once on the same services or am I going to have to figure out another option on this?
At some stage you’ll need to change your invalid namespaces to valid ones. Why not just go ahead and do that now?
Would you recommend to split DNS for internal/external entries? Or create new entries that point to the .com?
Yes split DNS for internal and external. I used a wildcard cert and works quite well, just need to make sure that all internal URL’s point to external name.
Paul,
The new certificate I created is for RWW and OWA on an SBS 2011 box exchange 2010.
Downloaded the new cert and completed the pending request and assigned services.
IMAP, IIS, SMTP.
I assume I have made an error with something as the new cert does not appear to work.
I still see the red url address bar and certificate error as well as the pre warning proceeding
(There is a problem with this website’s security certificate).
I click on the certificate to install and it state the URL mail.discountcomputersaustralia.local
Should this be .com instead of .local?
How can I change this?
SBS is a different beast because of the multiple application roles it performs. You should look for SBS specific guidance for configuring certificates.
This article rocks. User’s replies and your answers to them added even more value. I got answers to my questions in one of the replies.
I just took a new role so I have lots of questions with the setup here, and answers to lots of my questions are provided on this website. This is becoming my top MS Exchange website.
Thanks Paul!
Pingback: Politics SMS
Paul, thanks for the guide.
Can you comment on the proper method for exporting the cert to TMG- with or without private key? I seem to get 50% yes and 50% no when I ask about this.
Thanks!
Pingback: computer repair Tumbarumba
Pingback: beach wedding gowns cheap
Pingback: homepage
Hi Paul,
What a great, informative article! I’ve been tasked to install Exchange Server 2010 at my works and have done so fairly successfully – mails are coming and going both internally and externally. But I’m definitely no IT professional when it comes to Exchange and I have a few questions, if you have the time to answer them. Our external domain name is fullcompanyname.co.uk and the internal domain name is fullcompany.co.uk. Our current ISP has DNS entries for fullcompanyname.co.uk which then sends mail to our exchange server. I’m just a tad confused about what names I should be placing where for the certificate and and whether our ISP needs to make any DNS entries regarding OWA.
Any comments gratefully received.
Regards
Hi Paul,
Thanks for this great a post. I have a situation when I tried to complete the pending request for the certificate, when I finish the wizard the currente certificate disapear!!!
I will aprreciate any suggestions!
Regards,
Pingback: Watch dogs review
Hi
I finally managed to do the installation in the child domain. i wanted to ask about the certificate, is it ok to make the SAN’s for the child domain or i should make them for the root domain?
e.g
mail.child.domain.com
autodiscover.child.domain.com
or
mail.domain.com
autodiscover.domain.com
????
You can use any namespace you like, it doesn’t necessarily have to be the same namespace as AD.
Eg, an AD domain of domain.com might have an Exchange that uses company.com for SMTP addresses, therefore would need autodiscover.company.com.
Pingback: Confluence: ServTIE - Correu Electrònic
Paul,
I was wondering what the steps are to renewing a cert that is on multiple CAS server? The currently valid cert was applied to 1 CAS server and then exported to the second CAS server. All we want to do is renew that cert. I know how to renew the cert but the issue is what do I do about the getting that renewal to the second CAS server.
Thanks,
Len
Renew on one server then export/import to the others (then enable it as well I guess), same process as when you first deployed that cert.
Pingback: Confluence: AudioCodes
Paul,
My issue is how do you stop internal outlook clients from connecting to the client access you have setup for exchange?
I have 2 dedicated servers with round-robin DNS setup to support Active Sync clients which are connecting via certificates, I’m using a wildcard SSL for the public address and this is assigned to IIS/exchange. This is working quite well no issues for the external Active Sync Devices.
the problem is since I do not have the SAN cert that includes the internal domain.local names, internal outlook clients are connecting and getting the Security Alert: “The name on the security certificate is invalid or does not match the name of the site.” This alert shows the name.domain.local with the certificate for host.domain.com.
How can I stop Outlook internal clients from connecting to these 2 client access servers?
Thanks, Tony
You can set the URLs for Autodiscover, EWS, etc (basically anything except EAS since you still want that) to some other DNS name, then have that resolve *only* to the IP(s) of the CAS you want them to hit.
Eg, on SERVERA set the Autodiscover URL to https://mail.domain.local/AutoDiscover/etc.etc.etc, then in DNS have that “mail.domain.local” name resolve to the IPs for SERVERB/SERVERC/etc, so the client will never actually hit SERVERA with an Autodiscover request.
Thanks, Paul. I have all internal and external services using the external URL.
When I requested the SAN cert, I followed a document (and the Exchange Cert Wizard) that indicated I should also have the FQDN of the servers. I cannot find anything actually accessing them via FQDN. Thought it may be something handled internally through AD or Exchange.
OWA, EWS, OWA, autodiscover all use the external DNS name.
I do have an internal Microsoft PKI setup that does have issue certs for the Exchange servers. I just am not assigning the internal certs to any of the Exchange Services.
Best practices have evolved over time. Current best practice is to avoid using server names in SSL certs.
Good to know. I won’t worry about the FQDNs of the servers and will remove them from the SAN cert when I renew it later in the year
I appreciate the response to my questions!
Missed the link:
https://cabforum.org/wp-content/uploads/Guidance-Deprecated-Internal-Names.pdf
What will happen in November 2015 when the .local certs are no longer allowed?
EWS, OWA, CAS, and autodiscover are already resolving to an external domain name. Is there anything tied to the FQDN of .local that will break?
https://cabforum.org/internal-names/
The document linked below explains the changes to Certification Authority support for internal server names and reserved IP addresses and the reasons behind the new rules that were introduced in the Baseline Requirements for the Issuance and Management of Publicly Trusted Certificates, Version 1.0, which took effect effect on July 1, 2012: Internal Server Names and IP Address Requirements for SSL: Guidance on the Deprecation of Internal Server Names and Reserved IP Addresses, June 2012, CA/Browser Forum Version 1.0 (pdf)
The server FQDN can be different to the FQDN used in URLs for web services like OWA, EWS, etc.
This article demonstrates how to configure those namespaces independently of the server name (refers to Exchange 2013 but applies to Exchange 2010 as well)
https://www.practical365.com/avoiding-exchange-2013-server-names-ssl-certificates/
If an organization still didn’t want to implement the solution for some reason (like maybe they are using a .local namespace and everyone already has that bookmarked for OWA or something) then they can still issue SSL certificates from their own private CA (if they have one, if not they may choose to deploy one).
Hi Paul,
You have a wealth of knowledge and I am sure I speak for all when I say we appreciate your help and guidance.
I have a single server deployment of Exchange 2010. I initially published OWA, ActiveSync, etc. via an ISA 2006 proxy. I have since moved to using a UAG 2010 server to publish these services. On the UAG I am using a wildcard certificate, but I have a SAN cert installed on my Exchange 2010 box. My SAN cert on the Exchange 2010 box is expiring and I was hoping to use the wildcard certificate to replace it.
You mentioned in a response some time ago about local server names on SAN certs and how CAs will no longer support including them at some point and that we have complete control over the names used to publish services for both external and internal clients.
I foolishly updated my Exchange 2010 box with the wildcard cert and assigned the services previously using the SAN to use the wildcard. My internal Outlook clients immediately began seeing “Security Alert” messages basically saying the wildcard certificate was valid, but it didn’t include the “server.domain.local” internal address that Outlook clients use to connect to Exchange. I quickly switched back to the SAN cert.
I do use Split DNS and would be interested in any guidance or resources that explain how to setup the use of a wildcard cert to deal with internal and external names. What would I need to do so that my Outlook clients can use something like “owa.domain.com” rather than “exchange.domain.local”?
Does any of that make sense? Thanks.
Bill
The wildcard cert still needs to be valid for the namespace you’re using.
So *.domain.com on a wildcard cert won’t work for a server URL of owa.domain.local
This article describes how to manage namespaces for Exchange 2013 CAS services. It also applies to Exchange 2010 except that round robin DNS is not a workable solution for Exchange 2010 (but split DNS is) and the configuration for Outlook Anywhere has slightly different steps.
https://www.practical365.com/avoiding-exchange-2013-server-names-ssl-certificates/
I have an existing Exchange 2010 environment with 2 UC/SAN certificates (Entrust) which are coming up for renewal. What is the proper process for renewing existing 3rd party certs?
Hi Paul,
Whenever I have any doubts, I always check your explanation. Thanks for your support.
We have exchange 2010, We need a green bar and an padlock to secure our website and our server/domain.
We are in a process of buying GoDaddy or Verisigin(Norton) SSL certificate to our exchange server. which one is more secured?
will this serve the purpose?
Thank you in advance
Srikanth M A
Hi Paul,
I have two CA certificates on my servers, to check what I really need on my CAS Array servers. I have one certificate with external name for IIS service and a certificate for other services imap, pop, smtp.
I use those name for IIS without errors :
webmail.domain.com #Webmail external
Nom DNS=mail.domain.lan #Serveur Cas Array
Nom DNS=webmail.domain.lan #Webmail internal
Nom DNS=srv-mail1.domain.lan #Hostname serveur 1
Nom DNS=srv-mail2.domain.lan #Hostname serveur 2
1rst question : do I need hostname.domain.local on a certificate ?
When i test it on my test lab, it seems to but i am not sure of that one year later.
2nd question : for Outlook Anywhere do i need another name ? The webmail.domain.com i already define in Outlook’s configuration isn’t enough ?
3rd question : Is it an interest to add autodiscover, mail, pop if they are only used for local configuration ?
Great site by the way.
For the possible benefit of anyone else wondering how to add certs to a new Exchange 2010 server in another email domain this procedure worked just fine – was pretty straight forward actually:
1) From the original Exchange 2010 server, create a new Certificate Signing Request including the new names as well as those already in use. Upload the new CSR to the certificate provider and do a Rey-Key. This will generate a new certificate.
2) Download the certificate and do “Complete Pending Request.” This will install the new cert.
3) Select the new certificate in the Exchange Console and apply the certificate via “Assign Services to Certificate.”
Now the original server should be all set. Just need to apply this cert to the new server(s). To do this:
1) Export the certificate from the original Exchange server.
2) Import the certificate into the new Exchange server(s).
3) Assign Services for each machine.
Voila! This should now be working. Test to verify. 🙂
Hi Paul, very glad to find this site and that you are actively responding to questions to this day – thanks!
My situation is that I am adding a 2nd Exchange 2010 server into our organization. When I go through the adding cert steps it is including cert names already installed into the first 2010 server. Our scenario:
1st Ex 2010 Server is in a child AD domain: server-name.child-domain.com includes child-domain certs as well as root domain certs listed such as autodiscover.root-domain.com. Cets installed are UC/SAN.
2nd, new Ex 2010 Server is located in the root AD domain: server-name.root-domain.com. Wonder if the procedure is to just request additional certs under the current cert or to request an entirely new one? I am slightly confused as it seems like I have the same certs listed under both Exchange servers. Maybe that’s “par for the course?”
Thanks a lot for reviewing this post.
Hello Paul,
Great site by the way.
We will shortly be undergoing an Exchange 2010 transition from Exchange 2003 and we already have a wildcard certificate for our company domain.
My question is this: since we already have the certificate, can I simply apply it to complete the cert request without causing any issues?
Thanks in advance,
Mark
If you want to re-use a certificate just export/import it. No need to generate a new CSR. And if you do generate a CSR you can’t use the existing cert to complete the CSR.
Paul,
I am about to do a “transition” from Exchange 2003 to Exchange 2010 SP3 running on Windows server 2012.
Our internal active directory domain is called “example.com” and we also have registered the domain “example.com” externally . Apart from it we have several domain names used externally that we receive emails on. Our current Exchange 2003 SSL name space used is mail.domain1.com for Outlook web mail. Going forward with Exchange 2010 I want to make use of mail.example.com as the new name space for Outlook Web Mail, ActiveSync, etc. In other words, I want to discontinue using the existing mail.domain1.com after the transition is over.
How do I go about doing this? Is there a way to accomplish co-existence and redirect users with the above scenario or it is recommended to schedule an outage and do ALL mailboxes migration? we have about 150 mailboxes.
Hi Paul
We had to create a new certificate request since our current cert will expire next week. The original certificate has a 1024 bit encryption which is no longer supported by VeriSign. We generated a new certificate request from the CAS server using EMC. I used this to get a certificate signed by VeriSign. Now when I go to complete pending request and use the cert generated signed by VeriSign I get an error saying that “the source data cannot be imported or the wrong password was specified”. I have the password to import this cert but I do not get an option to type this anywhere.
I tried to follow the steps suggested on TechNet but I don’t see this certificate under personal folder.
Thanks
http://technet.microsoft.com/en-us/library/cc535024(v=EXCHG.80).aspx
Since I don’t know anything about the cert you’ve requested what you should really do is contact Verisign support (which you’re entitled to as a paying customer) to find out why the cert they’ve issued you isn’t working as you expect it to.
Hi Paul,
I am facing an issue while authenticate with exch2010 server using my client(IP phones).
The error “my IP phone is sending bad certificate” to server hello while establishing ssl connection with exch2010 server.
I had created the certificate as you mentioned but still facing this error. Could you please help me to get it solved.
Thanks in advance,
Bala
I am using trail version of exch2010. I am generating cert by following https://www.practical365.com/how-to-issue-a-san-certificate-to-exchange-server-2010-from-a-private-certificate-authority/ .
But my IP phone is sending “Bad request” even after installed the certificate on both phone and server.
Is there anything I can do to solve this issue?
You should review the documentation for your phones to determine the certificate requirements.
We have a .local internal domain and have just renewed to find that they no longer support .local addresses in as SAN’s. (they didn’t tell this till after renewal). So now all the internal Outlook clients are getting a certificate error “The name on the security certificate is invalid or does not match the name of the site”. Any thoughts about the easiest way to resolve this?
It’s OK – just spotted the link at the top of the article, so I’m going to have a look at some of those options.
Hi Paul, this article is fantastic in that it is just very clear and concise, I am following a couple other articles of yours right now in order to hopefully finish my Exchange 2010 deployment. One *tiny* thing to point out, when you are installing the certificate you received back from DigiCert (or whoever) you say to right-click on the Server, the image shows you clicking on the incomplete certificate, which is the correct way to go. There is no “Complete Pending Request” in the right-click menu for the server. Thanks for the great article(s)!
Yeah thats a typo. The screenshot shows the correct step.
Thanks Paul for reply, I will wait the expiration date of the current certificate. In case there is an issue, i will contact godaddy.
One more question, do I need to enable this renewed certificate manually or it will be enabled automatically once the current is expired?
Noticed that the renewed certificate has already the same services as the current certificate (POP, IMAP)
Joakim
It will need manual attention to complete the full renewal process.
I also recommend removing any expired certificates leftover at the end. I’ve seen issues with expired certificates still being enabled for services. Its cleaner to get rid of them.
Hi,
Our Exchange SSL certificate will expire next week.
I ‘ ve just renewed it from godaddy last week, it’s a SAN certificate. There is no problem during the renewal process. Everything is validated. No error.
But when I compare both certficates (the current and the renewed), I see a little difference on the “subject”
The old has like this: CN=autodiscover.domain.xx, OU=Domain Control Validated, O=autodiscover.domain.xx
The renewed is only: CN=autodiscover.domain.xx, OU=Domain Control Validated
I want to know what implications does this have?
Is there some configuration I missed during the renewal process?
Thanks.
The “O=” bit is the organization/company name. Looks like your new cert maybe just has that field blank, which is odd, but I don’t expect it to be an issue as that field is not part of the certificate validity criteria.
But you’ve paid for a cert from Godaddy, so if you’ve got concerns you should contact their support and ask them to explain why it looks different. Maybe they made an error.
Hi
In your example above all names are with .local !!
Will that really work?
the wizard in Exchange suggests .local for internal usage and .com (.se) for external usage.
Have I missed something…
Kjell
When I wrote the article .local was fine.
These days you should not use .local because certificate authorities will not issue you a cert for a .local name.
Pingback: Create a New Exchange 2010 Certificate | The Tired Admin
I have 2 exchange servers in totally different domains. I would like to establish trust between them and since creating trust between the two domains is not an option I have to create a SSL Certificate and Self-Sign certificates are the option you’re looking at . Here are my questions :
1. Do you need a 3rd party software ( like open ssl ) or the Self Signed Certificate in Exchange 2010 do the job ?
2. How to go about to import the certificates .
Thanks in advance for your help.
Best Regards
I have a webmail.domain.com cert for our webmail. I tried using a *.domain.com cert that we have to see if I could configure external autodiscover and if I do that it never gives me an option to setup the autodiscover URLs.
So as it stands the OWA server which is public facing is using serername.domain.local for autodiscover.
I guess the only way to fix that would be to list multiple domains on the webmail.domain.com cert? I’d have to have it reissued with webmail.domain.com and autodiscover.domain.com on it?
Thanks
Cody
Thanks a lot for your time and your efforts :).
Thanks Paul for amazing article,
But i do all the steps after order the certificate from Digicert and import the cert into Exchange ge the following worning Summary: 1 item(s). 1 succeeded, 0 failed.
Elapsed time: 00:00:10
EX1
Completed
Warning:
This certificate with thumbprint 9A747BB5F3ED6FE0AAD81489F7BA1868837EACD6 and subject ‘*.orascomci-projects.com’ cannot used for POP SSL/TLS connections because the subject is not a Fully Qualified Domain Name (FQDN). Use command Set-POPSettings to set X509CertificateName to the FQDN of the service.
Warning:
This certificate with thumbprint 9A747BB5F3ED6FE0AAD81489F7BA1868837EACD6 and subject ‘*.orascomci-projects.com’ cannot used for IMAP SSL/TLS connections because the subject is not a Fully Qualified Domain Name (FQDN). Use command Set-IMAPSettings to set X509CertificateName to the FQDN of the service.
Exchange Management Shell command completed:
Enable-ExchangeCertificate -Server ‘EX1’ -Services ‘IMAP, POP, IIS, SMTP’ -Thumbprint ‘9A747BB5F3ED6FE0AAD81489F7BA1868837EACD6’
Elapsed Time: 00:00:10
Note: i working with WildCard Plus cert from Digicert.
It looks like the error message is saying you need to configure a FQDN in the x509 name for POP and IMAP services on that server before you can assign that SSL certificate to those services.
thanks Paul for your reply, so how can i do that please?
This article has a screenshot of where the x509 cert name is configured for POP. For IMAP it is a similar process as well.
https://www.practical365.com/exchange-server-2010-pop3-configuring-securing-pop-client-access/
In the real world would the domain names poitn to .co.uk or .com as opposed to .local?
Thanks
Hello paul,
I have an issue- i installed SAN cert with all the domain names of my servers- and applied it to all services (POP,IMAP,IIS…) but now when i try to configure my outlook clients via pop i get this error “cert cant be validated and principal name mismatch….” my cert provider argues i check if all the names are included…and we verified with them they even used their tools and says “cert is successful installed”. For sure i don’t whats wrong.. need your help. But only thing i suspect is btn the common name of the SAN cert and the servers names being diff.
What should be the right POP TLS x.509 cert name ( should it be the common name or the real server domain name?)
Thanks
The x.509 name should be both (a) the name the clients are using to connect to POP, and (b) a name that is on the SSL certificate that is enabled for POP.
More info:
https://www.practical365.com/exchange-server-2010-pop3-configuring-securing-pop-client-access/
Dear paul I inhereited the following servers
I have the following topology.
two network load balanced server with the following roles :hub and cas
two clustered servers with the following roles mailbox
operating system :windows server 2008 R2
apllication:exchange 2010 sp1
two domain controller in the same site
one of them is additional
I have a certificate called B-cer which is chained from certificate called A-cert ,the B-cert is the used certificate in exchange 2010 and I got it from internal certificate authority ,also A-cert is obtained from the same internal certificate authority
A-cert will expire on September 2013 and b-cert will expire on October 2013
If A-cert is expired at September this will certainly affect the B-cer certificate
what I have to do,to renew the certificate for exchange 2010
I read the link http://www.stephenwagner.com/?p=435 which it doesn’t mention if the certificate is chained or not
I also read this link http://technet.microsoft.com/en-us/library/ee332322.aspx which if the certificate is chained or not ,also it doesn’t mention if there will be a file required when renewing the certificate using Exchange management console but it mentioned that a new request will be required using exchange power shell
any update please
I’m not familiar with your setup nor do I understand why you’re using chained certs like that when they both come from the same internal CA.
I suspect you simply need to follow the same certificate provisioning process you used to install the certs in the first place. That is if you want to keep using chained certs.
dear Paul
thanks for your update
I realize that the exchange certificate is chained from the internal root certificate authority
so I understood that I must renew the ca root certificate first
sorry for bothering you I just got confuse what is this this certificate about the the other certificate and i don’t know what is it
You would only need to renew the root CA cert if that is actually expiring too. The root CA cert has its own validity period that is separate to the validity period of the certificates being issued from that CA.
Paul,
I have renewed certificate of my Exchange 2010 CAS server from third party Thwate. Everything is good on server side. But few of my users are getting security certificate issue (The security certificate is not valid) when they open outlook client however on OWA same users are not having any issue and good with new certificate.
Please help.
Look at the certificate warning. When a certificate warnings appears it will tell you which of the three validation criteria has failed.
Paul,
Great article, thank you very much.
In my environment we have two Exchange 2010 Server:
– Server 1 is the CA server in the DMZ and has the certificate installed (wild card).
– Server 2 is has the Mailbox and CA Roles and only the self-signed certificate.
Whenever I need to restart Server 1, Outlook clients connect to the CA in Server 2 and get a warning about the certificate.
I thought about exporting the certificate that I installed in Server 1 and also import it in Server 2 (both servers would have it).
Is this possible? Am I messing up things?
Your comments a very appreciated.
Eduardo Macias
Two things:
1) Putting CAS in the DMZ is not supported
2) Yes, each CAS should have a proper SSL certificate installed
Well this is fine and dandy but this suggest we install Exchange 2010 first then use it to generate a certificate request which may take weeks in a large company like ours to be acquired from a third party like Verisign. In the meantime your legacy 2003 OWA clients are hitting a brick wall on the new 2010 CAS servers that don’t know how to redirect them to the old 2010 front end servers which in turn pass them on to the old 2003 mailbox servers.
So I think companies should create a cert request first using the Windows Server OS with the Certificate MMC prior to even installing Exchange 2010 on it, just to be safe. Then when the cert arrives go on and install Exchange 2010. Now I realize that if you don’t mock with your DNS after installing Exchange 2010 then your OWA/ActiveSync traffic may very well still route through the old 2003 boxes in parallel to your 2010 servers, but why take the chance. Especially if different teams, AD Team, DNS Group, Network Firewall Team, may be involved and handling different aspects of the Exchange 2010 Transition/Migration, see what I am saying here? You as the Exchange Admin need to be prepared and CYA.
A couple of points:
1) Your legacy 2003 OWA clients will continue to connect to the 2003 servers until someone changes the DNS for whatever your webmail namespace is (eg webmail.company.com) to point to an Exchange 2010 CAS. I don’t see this as a “why take the chance”. It flat out won’t happen until someone changes DNS. This is a change control/teamwork matter that companies all over the world manage just fine, so I’m sure yours can too 🙂
2) If acquiring third party certs takes you weeks, and you have a private CA available, then you can install a temporary cert from your private CA while you wait for the third party cert. This is specifically to solve the issue of Outlook 2007 and above clients potentially hitting the server with Autodiscover requests and getting a cert warning.
3) Sure, you can pre-provision the cert if you wish. As long as it is a valid, trusted cert with the correct names and Exchange can enable it for services then it should be fine.
4) Some people have let me know that their own workaround for this challenge is to install the CAS pre-reqs on the server, then just install the Exchange management tools initially, do all the cert stuff, then when the cert is actually ready to go they install the CAS role.
I would appreciate some help on this…
I have a SAN cert installed (created internally) – the Internal CA is trusted by my clients (set via group policy)
OWA / ActiveSync etc and even autodiscover all work fine.
However when I connect a MAPI client (Outlook 2007) I get a certificate warning – I have checked all the internal names and they point to the CAS Array name of mail.mydomain.com – though when Outlook tries to connect it is trying to connect to servername.mydomain.com – hence the certificate warning message.
I have checked Outlook to see if it is set to use http over rpc – and that’s a no…
Pretty stuck – is there anything I am missing? I really don’t want to have to put the servernames on the SAN cert.
Thanks
Dominic
Clients will still connect to the server FQDNs for services such as Autodiscover and Availability. Although you can change those URLs as well I find it is not a perfect solution and doesn’t always solve the problem.
Ideally your SAN cert should include the server FQDNs.
“Ideally your SAN cert should include the server FQDNs.”
What? That can’t be right!
Can’t it?
There was one strange error that it could not find OWA registered in the AD. It happens that this must be an Exchange/IIS bug. Since I have 3 exchange servers I had decided to rename the “Default Web Site” to the name of server for easier management….and that stops exchange from working. Unbelievable. Thanks for the interest and good article.
I did the process several times. Yet the certificate disappears each time.
Worse still now exchange does not accept any connection to it, web or outlook!
The certificate disappears? What do you mean by that? And at which step does it disappear?
As soon as I complete the pending request. While it pending it is visible. As soon as I complete the process, the certificate is gone. And it is not even listed if I use the ps-shell either. The only difference I am using my own private CA…using my AD to create the .req file.
First of all I use my own CA to sign the certificate. When I do in the Complete Pending request process, the certificate disappears from the exchange certificate list. And there is no trace of it in the certificates using mmc either.
I can only guess that is due to some problem with the cert or the CA.
Does your event log record any events at the time that would suggest why this is happening?
Have you tried on the Exchange server running MMC and adding the Certificates (Local Computer) snap in and seeing if it is there in the Certificates Personal store? If it is not try adding the Certificates (User) snap in, in the MMC and seeing if it is errounously in the User’s Certificate Personal store, sometimes installing certs using the silly dumb you up wizards has unexpected results. (I’ve been using certs since 2006 and seen quite a bit of nonsense like that)
Hi Paul,
This is great article we should have read this before we installed certificate 🙁
At current, we have installed 3rd party certificate for mail.mydomain.com and its working great. But users using Outlook Anywhere, they get this error message saying the name on the certificate doesn’t match the domain name. Problem with autodiscover.mydomain.com. We now have only one certificate installed for mail.mydomain.com and it seems like we need another certificate for autodiscover.mydomain.com ……I have been googling a lot and found out that I can’t install two different certificates for same Default-Web-Site in IIS.
So whats your solution regarding this autodiscover issue? Shall we dump the current certificate and buy new SAN certificate or is there other way around to purchase and install second certificate for autodiscover.mydomain.com or is there any other option?
Thanks in advance.
A SAN certificate is the best overall approach. They are not terribly expensive. Digicert has good pricing.
Hi Paul.
Thanks for your tutorial,it’s helpful. In my senario my internal cerificate( provide by my root DC) was going to expires soon .in the EMC when I right click that certificate there will be Renew Exchange Certifcate options is there.
1.Do you have any tutorial like this to Renew Exchange Certificate?
2. Is there any time frame to be mention for renewing the certificates?
3.will I need to renew the external & internal on the same time?
4. currenly my external certificate was with comodo? we plans to change it to digicert. Will its works for me?
Maybe I didn’t read close enough but you mention:
First is the Outlook Web App service. Enter the internal and external names of Outlook Web App. In this example I am using “ex2010.contoso.local” for internal, and “mail.contoso.local” for external.
Did you really mean mail.contoso.com” for external?
Its just an example. The point is you put in whatever public DNS name you’re planning to use for external access.
Hi, thank you for this article, excellent!
Can you please point me in the right direction for SSL certificates for CAS Array? We will have two server’s with the CAS roles installed. Can I have multiple servers on the same SAN SSL cert?
And what is the best way to move/migrate or change an existing SSL certificate used for our current Exchange server to our new CAS Array?
Yes, multiple servers can use the same cert as long as it contains all of the correct names. You will also just need to check the license terms of the certificate provider to make sure they allow you to install the cert on multiple servers. Digicert is one provider that does allow that.
The best way to change an existing cert is to simply install the new one, then when you’re ready enable the new one for the desired services.
YOU ARE GENIUS. Thanks a lot for sharing such a valuable information.
Great site. My question is concerning changing the alt names to an SSL already in use. godaddy will allow you me to “manage” an existing SSL and change the alt names without a rekey. Once the new alt names are vetted, the new cert is available for download and the old cert is invalid. Easy enough. My question is how do I get the new cert with the new alt names into my Exchange 2010 server that is using the old ssl cert? The common name is still the same, btw.
Thanks,
Paul
From memory you *should* be able to import the newly issued cert and it will appear with a new thumbprint, then you can enable that thumbprint for whichever services you need.
I don’t recall but I think that may also mark the old cert as expired/revoked. So be ready for that, just in case.
Dear Paul
Do i have to import this certificate to the personal and trusted Root certification authority??
thanks in advance
Dear Paul,
Hello,
You have a good guide here. I’ve actually already done everything that you say to do though. On the last part, “Assigning Services to Certificates”, I got the error:
“Summary: 1 item(s). 0 succeeded, 1 failed.
Elapsed time: 00:00:00
TREND4
Failed
Error:
One of the services you’ve selected (IMAP4, POP3, SMTP, IIS, UM) isn’t installed on this server. Please check which services are installed on the server and try again.
Exchange Management Shell command attempted:
Enable-ExchangeCertificate -Server ‘TREND4’ -Services ‘SMTP’ -Thumbprint ‘B3A8544C9B35006C65102F852BDDE70411826352’
Elapsed Time: 00:00:00”
We only had IMAP4, SMTP, and IIS checked. We checked our services. IMAP and IIS were installed. We installed SMTP at that point. Then we tried running the assignments again, but got the exact same error. Do you have any ideas what would be causing this? If so, do you know how to fix it?
Thanks in advance for any help you might be able to give.
Is the Hub Transport role installed on the server?
It was not. Thank you very much for the help. That fixed it.
Dear Paul,
Hi !
i have bought just two ssl web certificate from godaddy and i have many accepted domains
x.com,y.com,z.com and ..
i have set in my dns server to forward all of email.x.com, email.y.com and ,,, to the email.company.com
and i have three cas servers !
now can i make all my connections to OWA secure and validated using those two godaddy certificates ?
i mean is that possible to request a cert for email.company.com and install it on my cas servers just for use with OWA IIS ? is that possible ?
Paul,
I recently went to purchase a new Exchange 2007 Unified Communication Cert (SAN cert) from godaddy for three years. I found that SSL certs that are not valid FQDN’s are being phased out. For example I could not get a SAN cert that included “servername” and “servername.internal-domain.local” for three years (mail.domain.com, etc. is OK). It passes the deadline of 11/1/2015. I ordered a 2-year cert to get around this for now. But, what is the suggested way to proceed for Exchange 2007/2010 when you will no longer be able to get a cert that included just the netbios name? And for all of us out there that use .local or other non-valid FQDN’s, how will this impact us?
Here’s a link to more info from GoDaddy. It appears it applies to all certificate vendors:
http://support.godaddy.com/help/article/6935/using-intranet-and-reserved-ip-addresses-as-the-primary-domain-or-subject-alternative-name-in-ssls
Most of my clients are on Windows 2008 SBS where the single server holds all Exchange and Active Directory roles.
Thanks,
John
Heya Paul,
Thank you so much for this post, it is very helpful!
Hello Paul,
Thanks for your tutorial,it’s helpful.
I follow your instruction to establish SSL request in exchange server 2010, then I went one of CA site to buy a new SSL, Currently I got one ssl autodiscover.mydomain.org.
then use this tool to check everything is okay or not, e.g.https://www.testexchangeconnectivity.com
All pass except two errors which are
1.
Certificate name validation failed, Additional Details:Host name mydomain.org doesn’t match any name found on the server certificate CN=autodiscover.mydomain.org, OU=Domain Control Validated, O=autodiscover.mydomain.org.
2.
Certificate name validation failed, Additional Details:Host name webmail.mydomain.org doesn’t match any name found on the server certificate CN=autodiscover.mydomain.org, OU=Domain Control Validated, O=autodiscover.mydomain.org.
my question is
How many ssl need for exchange server 2010 to enable to use outlook anywhere?
I just bought autodiscover.mydomain.org.
how about webmail.mydomain.org and mydomain.org?I fell a little confused how to generate it?
Many thanks
Your certificate only has “autodiscover.mydomain.org” in its list of names?
You need a SAN certificate that contains multiple names. Please review the article again.
Hello Paul
Thanks for your information, it’s my first time to use exchange server 2010, I haven’t noticed SAN(multiple domain) and I just buy a standard SSL. that is the error result from.
so I need to buy SAN(5 domains or more) again , i delete ONE standard ssl then replace it by new SAN
problem solved.
many thanks for your others tutorial to let me finish my task
Jay
Hi Paul:
Probably a simple question but i can’t recall. As long as I have a URL in SAN Name i can use that for OWA, Active Sync etc… right? Doesn’t have to be SN ?
(Example – i use webmail.whatever.com as SN but add webmail-US.whatever.com in SAN. I can always change external URLs / TMG etc.. to webmail-us.whatever.com and be fine?)
Thanks
Really thank you very much I full appreciate your assistance I have implemented all instructions in this link
https://www.practical365.com/exchange-2010-ssl-certificates
I have did what I need
Hi Paul;
I am fresh for using SSL but I have exchange server 2010 with default rules and I have another server as dc server I wuld like if you mind step by step to configure internal cerificate to allow owa and digatl cerificate to work internally if my senario is clear kindly support me; Best Regards
I’ve written a number of articles on the topic so you should be able to work through it with a bit of reading. Start here:
https://www.practical365.com/exchange-2010-ssl-certificates
Paul,
Great thread. I am using two certs – one self signed for internal client urls and one external third party SSL for OWA. I am experiencing issues with OAB not updating in cached mode. I would like to use just the one certificate. Is this possible with a domain.co.uk cert on a localdomain.com domain. I had to recreate a self signed cert to stop the users getting a certificate name mis-match/
Regards
Do you mean self-signed or one issued from a private CA?
You’ll always run into trust issues with self-signed, even if you get the names right.
I have a self signed one which I didnt overwrite when completing the cert request from the CA ssl and I think that’s my issue. I am going to rekey my CA SSL but want to make sure the internal outlook clients do not get a name mismatch If I put servername.localdomain.com for my internal URL’s on my certificate request will this work like SAN’s if my CA certificate is a .co.uk?
You can put as many names as you need to in your SSL cert, that should work fine.
IIS can only have one SSL cert bound to the website so the cert must include all the right names or you’ll get mismatches.
Hi boss….i jst created a certificate request from my exchange 2010 and and sent the request to my certificate authority which is VERISIGN but d file dey mailed back to me is in a .p7b format. and when i was trying to complete my pending certificate it gave me option to insert .cer format of file…how do i convert my .p7b to .cer..tnx
If its as simple as changing the file select dialog so it shows all files, not just *.p7b files…
Other than that, not sure. Perhaps Verisign has a support article that can help. Maybe they offer multiple download formats?
Hi, can I check do you have any idea how many certificates can a service tied to. I saw in my exchange that there are 2 SMTP service that is tied to 2 seperate certificates. My understanding is that one service can only be tied to a certificate. Any idea how I can check which one is in use ? Thanks.
I am running SBS2011 with Exchange 2010 using POP3 connector to fetch mail from ISP via port 995 SSL. ISP has an expired certificate. How can I tell exchange to access using this expired certifiate. It now fails when trying to retrieve mail? Any assistance will be greatly appreciated.
Pingback: Technical Support
Pingback: How To Setup A Hosting Account
Hi Paul,
Great read, but I do have one question. How does one go about recreating the default 5 year SSL certificate for exchange 2010. I have found loads on creating the 1 year self-cert. ones but nothing for the 5 year one that Exchange 2010 creates for itself when setting up. I far as I know, this is done through Exchange Management Shell.
The new-exchangecertificate cmdlet has a -GenerateRequest parameter that determines whether the cmdlet will generate a request for a CA or a self-signed cert.
Read more about it here:
http://technet.microsoft.com/en-us/library/aa998327.aspx
Hi Paul,
We implementing a Exchange 2003 transition to 2010.
They currently use a Entrust cert for owa, with say mymail.mydomain.co.my
Now we would like to keep this owa site the same when we switch to 2010.
Can i include this mymail.mydomain.co.my in my SAN cert without revoking or changing the original cert on 2003?
So SAN cert name would be for mail.mydomain.co.my but include mymail.mydomain.co.my
Will this work?
Hi Paul, just a quick question. I have a single server Exchange 2003/Outlook 2010 environment and I’m about to transition to Exchange 2010, once I build my Exchange 2010 server with the typical components will my clients start receiving certificate errors prior to me installing a SAN certificate or will this only happen if I migrate the mailbox onto Exchange 2010?
Thanks
Stephen.
Yes they may, which is explained in a bit more detail here:
https://www.practical365.com/autodiscover-ssl-warnings-exchange-2010-migration
Thanks for your response Paul, much appreciated.
It sounds like one SAN cert is the way to go. I will contact the certificate issuer and see if I can upgrade it so I don’t waste my money.
When buying my SAN cert, do I need to include my internal domain names? I guess if I’m using OWA internally I need to buy mail.mydomain.local. What about autodiscover? Everybody in our company has an external SMTP address as their primary email address, so do we need autodiscover.mydowmain.local? And if so, what happens when we add further Exchange servers to our expanding domain? If we have many Exchange servers and shared DNS then doesn’t that mean we will need many internal autodiscover addresses?
Sorry for all the noobie questions.
Internally the autodiscover names are the FQDN of the CAS, or at least by default.
Generally speaking for your SAN cert you’ll need:
– the FQDN of each CAS
– the Autodiscover name for each primary SMTP namespace
– the DNS name for OWA, ActiveSync, and Outlook Anywhere
So, for example:
server.domain.local
autodiscover.domain.com
mail.domain.com
Your SAN cert can include all CAS, or you can do a different cert per CAS. If you add a CAS later on you can provision a new SAN cert, or if your cert provider allows it re-issue the existing cert with the additional name. Digicert is very flexible when it comes to situations like that, as well as situations where you might make a mistake and leave a name off by accident.
Hi,
I had purchased a certificate with my external FQDN and the internal FQDN. Apparently these certificates are going to expire and internal domain names will not be applied to certs. So now we can only apply for the external FQDN.
http://support.godaddy.com/help/article/6935/using-intranet-and-reserved-ip-addresses-as-the-primary-domain-or-subject-alternative-name-in-ssls
I was confused by the cert process as it was, now I’m even more confused.
How do I now go about ensuring I don’t get cert warnings internally or externally for my exchaneg server?
This is exactly my predicament; could only provision cert for .org address and not .local – now i get internal outlook clients complaining about the name not matching the cert because of course it doesnt. I need to figure out a resolution for it.
About to have the same issue… How do we issue a cert for just the public FQDNs and not have Outlook complaining to us all the time?
Hi Simon and others,
Sorry for the slow response, but here is my current advice on the matter:
https://www.practical365.com/ssl-requirements-for-exchange-when-certificate-authorities-wont-issue-certificate
Being new to Exchange 2010 I decided I didn’t need to purchase a SAN certificate, so instead I only purchased a certificate for webmail.mydomain.com. I have now learnt that Outlook would be much happier if I had a trusted certificate for autodiscover.mydomain.com.
So, I am trying to add a new certificate for autodiscover.mydomain.com using EMC. Under Exchange Configuration the only thing I have ticked is Autodiscover on the Internet, and I have specified my autodiscover URL. However when I click next I get an error like this:-
Some controls aren’t valid.
Looking at your comment just above, does this mean I cannot add an additional cert, I’ve got to scrap the one I’ve got already and replace it with a SAN cert?
– Input String cannot be empty.
– Input String cannot be empty.
You’re seeing that error because you haven’t filled out the rest of the new certificate wizard mandatory fields.
To answer your question, all of the Exchange web services such as OWA, ActiveSync, Autodiscover and so on are served off one IIS website. An IIS website can only have one SSL cert bound to it. Therefore, you can only use one cert for Exchange, hence the use of SAN certs.
However, you can create an additional IIS website and create new virtual directories off that for different Exchange web services, and have a different SSL cert bound to that website. But since you’re new to Exchange I wouldn’t recommend it, and to be honest even experienced people tend to stick to just one IIS website and use a SAN cert for ease of deployment and administration.
Hi Pul,
I have a test exchange server at home and configure the SSL certificates from 3rd Party CA. The senario is I have got 2 certificates from 2 different CAs
1. mail.domain.com (Service for OWA, activesync)-Geotrust CA
2. exch1.domain.com (Service for autodiscover)-SSLcert CA.
Now the issue is when I assign the IIS and SMTP service to mail.domain.com certificate, I can access OWA, activesync on my android phone without any issues since it shows the mail.domain.com certificate but autodiscover service doesnt run since it says certificate is not valid for exch1.domain.com.
And when I assign the below services to exch1 certificate, I can test autodiscover and it works well but owa and activesync doesnt run because certificate is not valid message comes.
I am just using free SSL cert service because for testing purpose. Problem with free SSL is that it can only give you a certificate for single hostname and not mutiple. Can you suggest me how to fix the issue.
The problem is that only one cert can be assigned to IIS at a time. So if you use cert 1, then Autodiscover (which is a web service using HTTPS) has the wrong certificate, and then if you use cert 2 then all the other web services have the wrong certificate.
The best solution is to use a SAN certificate, which I’ve described in more detail here:
https://www.practical365.com/exchange-2010-ssl-certificates
Hi Paul,
the prompt is outlook window with the security alert, the reason i suspect it is appearing is that the Name on the security certificate is invalid or does not match the name of the site.
Hey men,
First of all thank you so much for the info posted. Very helpful and very well formed.
But still i have a small problem. When i am trying to import the certificate, it says:
“The source data is corrupted or not properly Base64 encoded.”
What i must do?
Thank you
Hi
Have a query where i have a single server with client access roles and two serves in a dag with mailbox and hub roles. I have purchased a comodo SSL Certificate for the domain and have assigned the roles, OWA, OMA and Activesync working ok.
Have created a GPO to distribute the certificate to the clients, verified it has been distributed yet the outlook clients still prompt for a certificate.
Any ideas ?
They prompt for a certificate? Or they prompt with a certificate warning?
If it is a warning you’ll need to tell us more about the exact warning that is given before any advice can be provided. Different warnings mean different things.
Removed – please use the forums if you have questions about other topics
Removed – please use the forums if you have questions about other topics
We have a wild card SSL certificate how do we import / assignee this in exchange 2010.
We tried to create and csr and import existing crt but we are getting an error
“Cannot import certificate. A certificate with the thumbprint 44CE486F809C2DF0AADE2C4D9277CD3160E2ED16 already exists. “
Ranjjth, take a closer look at that existing certificate. Seems like you’re trying to import the same certificate twice.
Can I contact you by Skype or email? This is my email address: smart_sspt@yahoo.com; and Skype: event_sok
Removed – please use the forums if you have questions about other topics
Hi all, I have 1 problem relate to configuring external user to access to exchange server 2010. Currently, I am using exchange server 2010 and set up in my company (internal). I want to allow external user (outside from the office) to use MS Outlook to access to my exchange server 2010 (internal). I had configured to enable outlook anywhere of my exchange server 2010 and I had configure on the MS Outlook (Client’s PC) to connect to exchange server 2010 already. But when I try to connect to exchange server, I got the error message about certificate error and client (external) cannot connect to exchange server 2010. But for another laptop using Mac OS, it still working properly. It is problem with only client’s laptop using Windows OS. WHY? Could you give me some advice relate to this issue? THANK
Regards,
Sophaktra SOK (Mr.)
It depends on the exact certificate error you’re seeing.
I got the error message from client computer as details below:
“There is a problem with the proxy server’s security certificate. The security certificate is not from a trusted certifying authority. Outlook is unable to connect to the proxy server mail.domain.com.kh. (Error Code 8).”
Now I has no more idea relate to this issue. Please help me to solve this issue as possible. THANK
The problem is that the connecting computer doesn’t trust the certificate authority that issued the SSL certificate. This is usually when you have issued the certificate from your own private CA instead of buying a commercial certificate.
So the solution is to either:
– install the root certificate from the CA on the connecting computer so that it trusts the certificates issued by that CA
– replace the certificate with one from a commercial certificate authority
How can I install the root certificate from CA? And how to replace the certificate with one from a commercial certificate authority? Please guide me to solve this issue. THANK for your kind support.
what should i do if i have different domain name for internal & external?
internal: exchange.myofficedomain.com
external: exchange.ouroffice.com
i’ve bought a cert for the external but upon configuring it, my internal users face certificate problem when using their outlook.
is there anyway to have self-signed internal cert + CA-signed external cert to co-exists?
thanks.
Hi Kent, yes you can bind separate certificates to separate sites within IIS. The summary is that you need to create a new site in IIS on its own dedicated IP, create the applicable Exchange virtual directors (via PowerShell), and then use DNS to direct the different names to the different IIS sites/IPs.
Should I add netbios name of my Exchange server(s) into certificate?
Do i realy need the netbios of all my cas server
Only if you plan to have users connecting to https://shortname/owa
Otherwise, if they’ll always be connecting to https://some.other.long.name/owa then you don’t need the netbios name in the cert.
I generally leave it out.
In OWA 2010 after logging when I click on the New Button or any other buttons nothing happens. Unable to create reply or delete any messages. However, if I access OWA directly from server everything works fine.
Any idea what it fails in OWA?
Thanks in Advance
Dan
Is your browser blocking popups?
I uninstalled and reinstalled the certificate on the 2nd server and everything looks fine now. I am able to access OWA without any issues.
Thanks Paul
Hi Paul,
Recently I installed a SAN certificate on my exchange server. On 1st eveything went fine, but on second server when I enabled the exchange certificate it gave me the below error
This certificate will not be used for external TLS connections with an FQDN of ‘mail1.X.X.COM’ because the self-signed certificate with thumbprint ‘AAA-THUMBPRINT-AAAAAAA’ takes precedence.
Now on second server I see a red mark on the certificate
I have all the names external and internal on the SA certificate.
Please could you let me know if this would create any problems on my exchange servers
I’d just unassign the certificate that you don’t want to use from SMTP.
Dear
I am create two dertificate in CAS and i need to remove please can help me to provide the step…
why email are being queued on exchange server 2003 sending to exchange 2010?
Paul –
I have a strange predicament, I have inherited a domain with an internal name ending with .gov. External name is slightly different due to restrictions. Want to create a SAN with internal and external domain names as required, but cert authority informs I need to register my internal name as it is an external designation. Problem is the governing board for .gov names will not allow us to register it as it is not the format they allow – even thought it is for our internal use. Our AD is 2008R2 but too large for a domain rename (the thought makes me shutter) besides I think Exchange is one of the apps that is not compatible with it. My question is – can I have two cetificates assigned to my CAS array, The Commercial SSL for external users and an internal self signed certificate for my internal clients? Will Outlook autoconnect work properly?
Thanks in advance.
John
Paul –
Are there any comments you can provide on my situation? Greatly appreciated.
Thanks.
John
Yes you can use a mix of certificates issued by private and public CAs.
Use the privately issued certs on your internal servers, including the external name on the internet-facing CA servers as well.
Then request a separate cert from the public CA for the external name(s) and bind that cert to your ISA Server listener.
Good afternoon Paul,
I have a question about the certificate. I have a machine running exchange 2010 and already has certificate.
I’m upgrading my accounts to a new server. Can I install the new certificate after the migration of mailbox?
Thank you.
What roles is the new server running? If it just Mailbox server role then no cert necessary. If it is running CA/HT roles then a new cert will be necessary, and I always configure things like certificates before putting a server into production.
I have been able to generate and import the certificate on my first CAS server (the one where I issued the request). But somehow I’m unable to import the cert onto the second CAS node. I can’t export the cert from node1 with the private key because it’s a digicert issued certificate.
How can I enable the cert on the 2nd node? The FQDN’s of both CAS hosts and CAS array name are correctly listed in the cert.
I’m at a loss here 🙁
I’d suggest contacting Digicert support. I’ve exported/imported their certs before.
Great article!
BUT is this all done automaticaly when we use the trusted certificate wiazard in the sbs 2011 console?
I’m having trouble accessing RWA outside the network plus activesync aint working for mobile devices either.
SSL looks fine from inside the browser on the network though!
SBS is as always a little bit special 🙂
Your internal, domain-joined clients will trust the certificate that SBS creates, but external non-domain joined clients (and things like smartphones) will not.
There is usually a little cert installer package you can download from your SBS server to deploy to non-domain joined clients so that they trust the cert. Also ActiveSync phones usually have an option to ignore SSL certificate trust problems.
I understand that but even after installing a trusted cert, we cannot access anything outside the network. I even installed a cert on my iPhone but still it won’t connect outside the network.
When i run a Exchange Activsync scan i get this error………..
Testing the SSL certificate to make sure it’s valid.
The SSL certificate failed one or more certificate validation checks.
Test Steps
ExRCA is attempting to obtain the SSL certificate from remote server remote.burningdesirewales.co.uk on port 443.
ExRCA wasn’t able to obtain the remote SSL certificate.
Additional Details
The certificate couldn’t be validated because SSL negotiation wasn’t successful. This could have occurred as a result of a network error or because of a problem with the certificate installation.
Is this a certificate problem? If so would installing a certificate the way you have solve my problem?
Regards
Mat
Looks like some other firewall or server issue going on there.
Pingback: Lync – OWA integration contacts are grey and cannot sign in IM | Exchange DUDE
Pingback: Configurazione Certificati Exchange Server 2010 « mavboss
I have installed the SAN certificate on both CAS servers. I did not include the name fo the CAS servers or array on the certificate. I am getting a certificate error on OWA. Any way to get around this?
Depends on the error you’re getting. But I would guess, without knowing all the details of your situation, that reissuing the certificate with the correct server names included in it would be a start.
Hi,
Can we use Active directory certificate service (windows server 2008 R2 )for exchange 2010 Client connectivity.
Thanks
UNAIS
We have spoke with Microsoft about this and they told us following :
Fqdn servers with all roles on it (cas,mbx, hub) , should be include in certificate. If you use cas array, only cas array Fqdn should be in certificate, do not need include Fqdn or netbios names of cas array member servers to San certificate. Autodiscovery for internal and external domain should be in certificate. All owa names should be in certificate.
Thanks
I’ve had advice that goes both ways on that one (CAS Array name). Seems to hinge on whether the CAS Array name is also the same DNS name as services such as OWA.
Hello,
For Exchange 2010 SP1 environment with CAS Array, should I add CAS servers netbios names to SAN certificate or I can add only CAS servers FQDN names?
Thank you
It depends, do any of your users access OWA internally by entering the short name of the server? If not then just the FQDN should be fine.
Thanks for reply.
All internal and external users will use external URL for OWA (https://webmail.domain.com/owa).
In that case I should add only FQDNs of my CAS (cas1.domain.local and cas2.domain.local) server and virtual CAS Array (casarray.domain.local) name to the certificate + webmail.domain.com + autodiscover.domain.com and autodiscover.domain.local.
Am I right?
Thank you
Sorry about the delay on replies. Your CAS Array name may not need to go into the SAN cert, it depends if clients will be making SSL connections specifically to that name. But there is no harm in adding it.
Hi Paul,
I am in the process of migrating from Exchange 2003 – 2010. I have one Exchange 2010 server installed so far and only a few users on it yet. I wanted to get the certificates on before I deploy it so I went through the wizard and selected pretty much what you show in your example but when I submitted my request to Geotrust to get a certificate it was mapped to my domain name only – example – domainname.edu and not my mail server name or my external link name – example – mail.domainname.edu. When I complete the pending request in Exchange the cert was applied but nothing worked right – i got errors on my OWA accounts and on my desktops. I did not use the wildcard option in the wizard. I even tried resubmitting the cert with the external mail link name thinking that only the people accessing email through the web or activesync/imap user were using the certificate. That made the OWA users happy but not the desktops – they continue to pop up a certificate warning every time I open Outlook 2010.
Any idea what I am doing wrong? It seems pretty straight-forward
Hi Sylvia, what type of certificate did you order from them?
We buy a bulk package of standard SSL certs – from Geotrust rapidSSL. I don’t think I can do a SAN cert using these certs. There is no option for anything except what pulls up from the request. No enterprise certs.
Yep, sounds like you’ve got just a standard/single-name cert there. Has to be a SAN cert for the multiple names to work. Looks like Geotrust refers to it as a UC/SAN cert on their sales pages:
http://www.geotrust.com/ssl/ssl-certificates-san-uc/
Pingback: Exchange 2010 – SSL Certificate - Admins Goodies
Pingback: Exchange Server 2010 ActiveSync SSL Certificate Problem - Admins Goodies
Pingback: Возможно вы незнали, что … » Архив Блога » публикуем Outlook Web App в ISA Server 2006
Why is it recomended that you use a san certificate? and what problems might you expect when using a wildcart certificate?
Just check that all of the browsers and mobile devices you’re expecting will be connecting to Exchange support wildcards. Some don’t, but it is mostly older ones.
Thanks for the info, we only use new browsers and recent android. So this shouldn’t be a problem.
Do you known of any problems with outlook 2010 and a wildcart certificate, because i could only find some articles about outlook 2010.
I’ve used a wildcard in my lab with Outlook 2010 and didn’t notice any problems. All prod environments I work with use SAN certs though, so I haven’t had the opportunity to really test wildcards in the real world.
Wow. I had local users getting an server cert errors on Outlook launch for weeks. Thank you so much. That was easy as pie. Even easier than pie. Many thank yous!!
Hi Paul.
I have just implemented a SAN sertificate, and run into problems with Outlook 2010.
I have the following subject:
remote.domain.local
Subject Alternative name:
remote.domain.local
autodiscover.domain.local
autodiscover.domain.no
exchange-server.domain.local
Autodiscover works fine, but when I try to start Outlook, it will promt for username and password, and I never get connected.
I first had not implemented exchange-server.domain.local as a Subject Alternative name, and then Outlook 2010 worked, but complaind about the missing value. After adding exchange-server.domain.local everything looked fine – no errors, until firs reboot, but then I was promted for username and passwor.
OWA works fine.
Any bright ideas?
Ulf
It is possible your Outlook clients are making a HTTP connection via Outlook Anywhere, and Outlook Anywhere is configured for Basic Authentication.
Hi Paul,
Is it safe to remove the pre-configured self-signed certificate that Exchange 2010 created? I have a new SAN certificate from DigiCert and have assigned IIS service to use it. My SMTP, IMAP, and POP are still using the self-signed certificate. Should assign all these services to use the SAN certificate from DigiCert and remove the self-signed one? Please let me know.
Thanks,
Kevin
I usually just leave it alone 🙂
Hi Paul
Is there anyway to configure separate certicates for internal and external names.
Could be a security issue showing those internal names on public certificates?
Thx!!!
If you’re using ISA or TMG to publish Exchange externally you could get a second certificate that doesn’t have the internal names in it. But then of course that costs you basically twice as much.
Consider also that your internal names might be exposed already through the headers in emails unless you made some config changes to hide them.
Knowing your internal server names is not much help to someone unless they can break into your network anyway. And once they’re in discovering names is pretty easy 🙂
Thx Paul
I was thinking about separated sites for internal and external Exchange access. One using only internal names and the other one using external names. So only would be necessary to buy the external one. The other could be autogenerated in the coporate CA. But i dont know if tits possible the configuration of the separated IIS sites to work with Exchange.
However, with your comments regarding the security, it appears to be unnecesary this (im)possible solution. 🙂
Thx for the quick response!!
If you’re publishing via ISA/TMG there is no need for multiple sites (or virtual directories), unless you need different authentication settings between them.
If you’re publishing Exchange directly through a firewall (ie without ISA/TMG) and you want to use different sites/virtual directories to bind different SSL certs to, then yes I guess that would achieve what you’re trying to achieve.
And yes you can just use the internal CA to issue the cert for internal use.
All up to you really 🙂
Pingback: Configure an SSL Certificate for Exchange Server 2010 | “Knowing is not enough; we must apply. Willing is not enough; we must do”
Hi,
We experienced the same issue with Exchange 2010 and Outlook 2010.
We decided to import the self-signed certificate into the a GPO (Trusted Root Certification Authorities). The thing is this works for a mailbox user who is in fact Domain Admin, but a regular user still gets the certificate warning message. Something to do with rights?
Any suggestions?
Thank you!
Hi Timothy, should work fine for regular users too. Are you sure your GPO change is applied to the users? ie not filtered out in some way, have they run GPupdate? Check RSOP and make sure it is applying? That’s where I would start looking.
Hi Paul,
There was something else that was causing this. The normal users have proxy enabled and the domain admin doesn’t. I put the “https://” in the bypass proxy and the problem is now solved.
Thanks you for quick response!
After creating and adding the SSL cert to CAS exchange2010 server. The current remote users outlook exchange proxy settings URL is https://exchange2003.domain.com. Can this outlook setting stay the same till the mailbox has been moved from exchange 2003 to 2010? If no, it there a script or something that can change it without the users knowing about the change. Also, same question with internal users outlook profile point to exchange2003 vs exchange2010 till the mailbox has been moved?
Thank you.
Hi Alan, they can keep using the same name. In fact you can transition that name across to Exchange 2010 if you wanted to. See here for details about migrating Client Access services from 2003 to 2010.
http://technet.microsoft.com/en-us/library/ee332348.aspx
Internal uses will have the Exchange 2003 server name in their Outlook profile until you move them to a 2010 mailbox server, and the profile will automatically update to the new server name (of the CAS that is the RPCClientAccessServer for their mailbox database) at that time.
Pingback: How to Configure Exchange Server 2010 Outlook Anywhere
I created the new certificate request, but it’s just sitting there. How do I get it to become a .cer?
Matt, the next step explained in the article is to submit the certificate request to a Certificate Authority who will then issue you the SSL certificate. The suggested CA in the article is Digicert.
Pingback: Securing Exchange Server 2010 POP3 Remote Access - Exchange Server Pro
Pingback: Autodiscover and SSL Warnings during Exchange 2010 Migration - Exchange Server Pro
Hi,
Should I add autodiscover for internal and external domain in my SAN Certificate?
For example:
autodiscover.domain.com
and
autodiscover.domain.local
Or I can add only one to the certificate?
Thank you
You would need an autodiscover name for each SMTP namespace in your organization. You can have more than one autodiscover name on a SAN certificate.
Hello,
We have Exchange 2010 SP1 with two CAS/HUB servers in CASArray and two MailBox Servers with DAG enabled.
Question 1:
For CAS array I am using outlook.domain.local (DNS Record) and I am going to buy a SAN certificate from digicert.com, please see names that I am going to include in this certificate and please correct me if I am wrong:
Outlook.domain.local (internal NLB for Client access array)
Ep-cas01.domain.local (for outlookanywhere)
Ep-cas02.domain.local (for outlookanywhere)
Webmail.domain.com (OWA,POP3,SMTP)
Autodiscover.domain.com (for autodiscover)
domain.com
Question 2:
We already have regular (not SAN) SSL Certificate for webmail.domain.com. Can we assign this certificate for IIS,POP and SMTP services instead of buying SAN Certificate.
Thank you
Alex, check with the certificate provider whether they will issue you a cert for a .local name. I think not all of them will.
Hello Paul,
Thank for the quick respond.
My Exchange 2010 SP1 environment contained following servers:
Ep-cas01.domain.local
Ep-cas02.domain.local
CAS Array for these CAS servers is “outlook.domain.local”, and two mailbox servers with DAG
For OWA we are using “webmail.domain.com”
DigiCert and VeriSign allow to use “.local” domain names and they suggest to add netbios names to the certificate as well. (http://www.digicert.com/ssl-support/exchange-2010-san-names.htm)
http://www.digicert.com/unified-communications-ssl-tls.htm
http://www.verisign.com/ssl/buy-ssl-certificates/specialized-ssl-certificates/san-ssl-certificates/index.html
Could you please advise me what names I have to put into certificate:
Outlook.domain.local
Ep-cas01.domain.local
Ep-cas02.domain.local
Webmail.domain.com
Autodiscover.domain.com
Autodiscover.domain.local
Should I add netbios name of my Exchange server(s) into certificate?
Thank you
Alex
What if they do not allow private domain names, like GoDaddy does no longer? Will we need a 3rd party cert and a self-signed (for the local.domain?). We have multiple sites, each with a CAS Array. Only two sites are externally facing for EAS and OWA, the rest are internal only. Users at the internal only sites get cert warnings because their CAS Arrays are at sitename-casarray.domain.local while the other two sites are extname.doman.com
You have complete control over the internal and external URLs that each service (eg OWA, Autodiscover, EWS, ActiveSync…) uses and can set them (even the internal ones) to domain names that are valid under the new requirements being enforced by certificate authorities. You can then use split DNS so that the names resolve correctly for internal clients.
The CAS Array names (or more accurately, the RPCClientAccessServer names) for each site are not required to be on the SSL certificate and should not be the same as the names for services such as OWA and Outlook Anywhere.
Hi Thanks for the article , I have exchange 2010 running ,
is it risk free to assign services to new certificate , does this
affect existing connected users from LAN ?
I would schedule it for outside of business hours in case there are any problems from the change.
Pingback: Exchange 2010 SSL Certificates - Exchange Server Pro
Thanks….
Paul, what should I do on Exchage 2010 and on client to get outlookanywere going. Do i need to allow any port on firewall as well? Please advise
Thank you
Faisal
Faisal, I decided to write a new tutorial to answer your question. You can check it out here:
https://www.practical365.com/how-to-configure-exchange-server-2010-outlook-anywhere
Man, this Articles ROCK!!! Thanks!!!!
I already have a wildcard cert for my entire organization, which is used for not only our external web servers but also for OWA access in 2003. I’m having difficulty finding technical information on using the cert when moving to Exchange 2010. Can you point me to any resources?
Kim, wildcards are supported by Exchange 2010 but not all browsers and mobile devices will support them (mostly older ones though). A wildcard is also less secure in some ways than a SAN cert, but I’ve never met anyone who worries about that.
Most of our customers go with a new SAN certificate at the time of deployment which is the best outcome.
Thank you so much paul. I am moving forward now. every problem of mine is resolved for the moment, touch wood. As a summary i am writting down all of my exchange problems i had last week and their solutions which are obviously suggested by you
1. Outlook 2007 started displaying a certificate message each time you open it up or when you click on send/receive. This probelm resolved by usaing a SAN entry in certificate as autodiscover.my-local-domainname.local in certificate.
2. iPhone was not able to activesyn with exchange. problem resolved after finding out that user should have inhertance permissions in AD. (open ADUC>right click user>properties>security>advance) and select inheretance. if you cann’t find security tab then you need to enable advance view. from top menu.
Thanks Paul for your last tip to ignore the SSL in case of using private CA. this proved as a cracking shot
Best Regards
Faisal khan
Thanks Paul, much appriciated.
Q1. how to achieve this via console. please hint?
Meanwhile what i did is I have requested a certificate from my local CA (from my first dc http://DC01/certsvr). This appears in Exchanage console as a False under self-signed. is this okay? This is not from Third party though!
Q2. As long as i am not getting proper certificate from third party, which i will do soon, would it be alright to use this certificate or you think i should get a self-signed certificate instead.
My existing self-signed certificates in exchange are messed up. Because Outlook 2007 clients has started getting Certificate YES NO message each time they open Oulook2007 since i have assigned some services (may be iis or other not sure!) to this certificate. But after requesting and installing a cert from DC01/certsvr this problem has been resolved.
Q3. now my BIGGER concern is iPhone. This bloody iPhone/iPad cann’t seem to connect with exchange on activsync.
Many Many Thanks
Q1 – See this article for instructions.
https://www.practical365.com/how-to-assign-an-ssl-certificate-to-exchange-server-2010-services
Self-signed “False” just means that it came from a CA (either private or commercial), instead of being self-generated by the Exchange server.
Q2 – I think a CA-issued cert is better than a self-signed cert, but obviously getting one from a commercial CA is better than a private CA.
Yes I would expect certificate warnings when using a self-signed certificate, and the private CA-issued one would solve that for domain members, but not for non-domain members (eg people connecting from home to OWA, or mobile devices).
Here is an article I wrote about it all:
http://www.petri.co.il/ssl-exchange-certificate-buying-commercial.htm
Q3 – You can use the website https://www.testexchangeconnectivity.com/ to test ActiveSync to see if it is just an iPhone bug or something else with your configuration.
When using certificates from a private CA you’ll need to check the box to ignore trust for SSL when running the test.
Hope that all helps.
I have two self-signed certificates in exchanges 2010 as follow
Name “Self Signed Services Issuer “Expiration Date”
True IMAP, POP, IIS, SMTP CN=WMSvc-MAIL 0109/08/2020
“Microsoft Exchange” True SMTP CN=MAIL01 04/10/2015
how to remove some services i.e. SMTP or IIS from the certificate. and assign IIS to the second certificate “Microsoft Exchange”.
Secondly can I make a backup of certificate before playing with them? so that i could restore incase of any nonsence happens
btw please dont confused my question with the previous because my name is also Faisal 🙂
Thank you
Faisal Khan
Faisal, when you use Enable-ExchangeCertificate to enable one for IIS it will automatically remove IIS from the other certificate’s uses. You can also do it via the Management Console if you prefer it that way.
You can export certificates but it shouldn’t be necessary if all you are doing is enabling them for services.
Pingback: How to Issue a SAN Certificate to Exchange Server 2010 from a Private Certificate Authority | Exchange Server Pro
Hi Faisal, same process as above, but you also include the DNS name of the NLB cluster in the SAN certificate.
Once you’ve installed the certificate on one of the NLB cluster members you can then export it using the Certificates snap-in in MMC, copy it over to the other server, import it and then enable it for IIS on that server as well.
The export/import process is demonstrated here (well its for 2010->2003 but you should be able to work it out from that)
https://www.practical365.com/export-an-exchange-server-2010-certificate-to-exchange-2003
Dear, Paul.
This post is very helpfull.
I have issue with accessing OWA externally after SSL certificate Renewal. Everything is fine internally.
I have Exchange 2010 0n Hyper-V with 2 CA cluster and one TMG.
OWA tries to connect continuously with no success when accessing it externally.
I would like to know what we missed in the config, do we need to do something on TMG side ?
Thank you for your support
DDS
The expired certificate would need to be updated on the TMG as well, if you haven’t already done that.
Dear, Paul.
Thak you for your answer.
THis already done, and OWA work perfectly in internal network.
But outside, When we launch the owa link nothing happen on the browser asking to reload the page. If we try to connect though outlook from outside our network, outlook tries continuously to connect without success. And we no longer get any SSL certificate message.
Do you See ?
You really need to take a look at your TMG logs to see what it is doing with the connections. Also check your IIS logs to see whether the proxy connections from the TMG are hitting the Client Access server or not.
Another question is as I’m using SSl, do I have to use SSL Certificate authentication or HTML From authentication ?
Regards
its a very nice tutorial, but how can I create a certificate for NLB Cluster Name.