The first step in configuring a new SSL certificate for Exchange Server 2013 is to generate the certificate request.
More information about SSL certificates for Exchange Server 2013
In this example I am generating an SSL certificate request for a server named E15MB1 in the exchange2013demo.com domain, that is installed with the Client Access and Mailbox server roles. The server will be an internet-facing Client Access server, and so the following names will be included in the SSL certificate:
- mail.exchange2013demo.com
- autodiscover.exchange2013demo.com
Note: this is an example only. Make sure you do the proper planning so that you include all of the required names in your own SSL certificate request.
The certificate request can be generated using the Exchange Administration Center.
Open the Exchange Administration Center in your web browser and navigate to Servers -> Certificates.
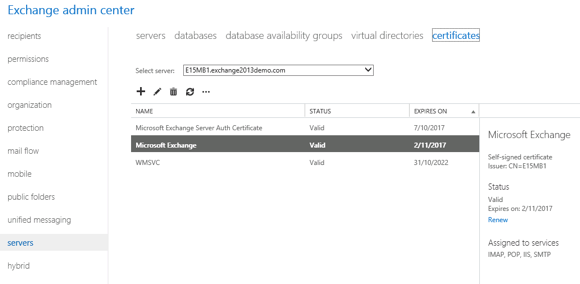
Click the “+” button to start the new Exchange certificate wizard. Choose to create a new certificate request and click Next to continue.
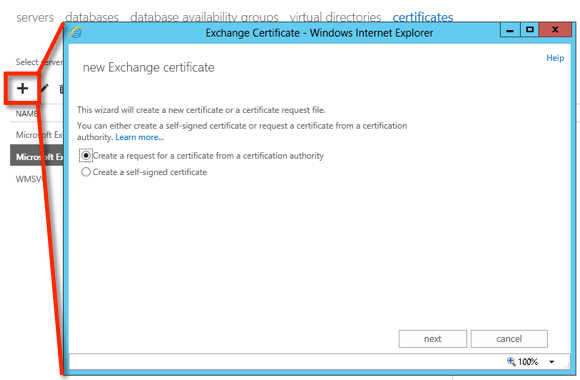
Give the new certificate a friendly name and click Next to continue.

Do not choose to create a wildcard certificate. Although wildcards are supported for Exchange they are not supported for some interoperability scenarios with other server products. Click Next to continue.

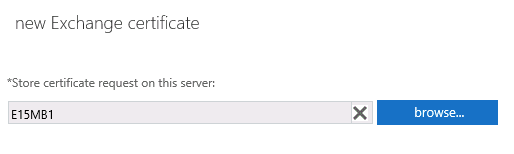
Click Browse and choose an Exchange server to store the certificate request (this is the server that will hold the pending certificate request while you wait for the certificate to be issued). In this example I am storing it on the server E15MB1. Click Next to continue.
Click the Edit button and enter the domain name that clients will be using to connect to each service, for example mail.exchange2013demo.com for OWA.
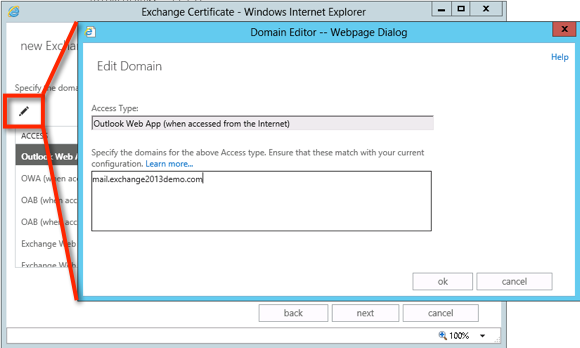
If multiple services such as OWA, OAB, OA, EWS and ActiveSync will be using the same external name you only need to enter the name once for one of the services, and then you can click Next to continue.
A consolidated list of names is presented. Note that the server’s NetBIOS name (short name) will be present in this list, and other unwanted names may also appear, depending on how you completed the previous step. Remove any of the names that you do not want to be included in the SSL certificate.

In particular, a commercial certificate authority will not issue you a certificate for a server’s NetBIOS name, an IP address, or a namespace that you can’t verify that you own (eg a .local domain), so you must remove any of those names from your certificate request before you click Next to continue.
Enter your organization details and click Next to continue. For some certificate providers this information needs to match the information that is in the public WHOIS data for the domains that you are requesting a certificate for. If it does not match there may be some additional manual verification steps required before the certificate will be issued, which may slow down the process a little.
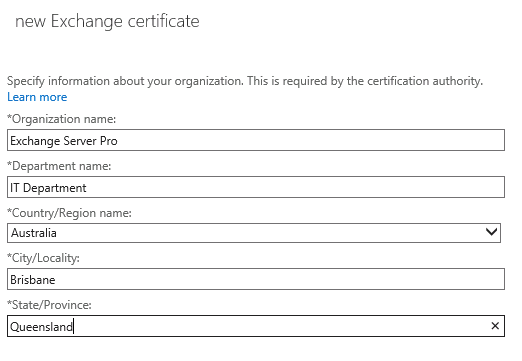
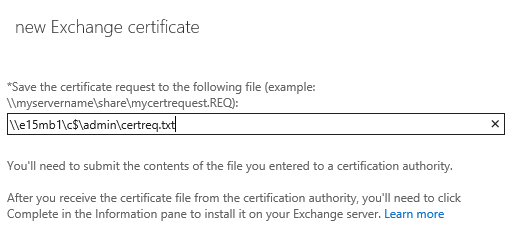
Enter a valid UNC path to store the certificate request file, and click Finish.
The pending certificate request is now visible in the Exchange Administration Center.

The certificate request file is also able to be found in the UNC path that was nominated.
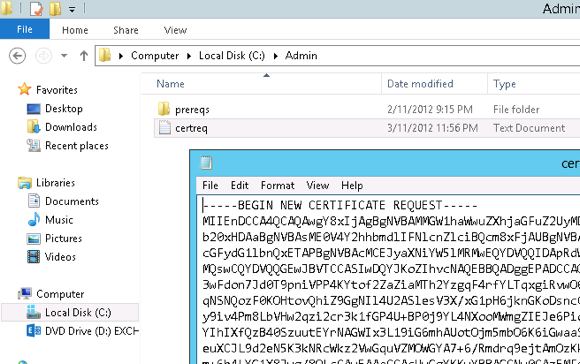
The next step is to submit the certificate request to a CA so that the SSL certificate can be issued. For commercial certificate authorities I recommend using Digicert.
If you are planning to use a private CA instead then follow these instructions to submit the certificate request and download the SSL certificate.



ブランドコピーN
ブランドスーパーコピー通販専門店!人気N品激安!
2018年新品種類がそろっています。
品質がよい、価格が低い、実物写真!
弊店のスーパーコピー時計は品質2年無料保証になります。
日本全国送料で数量無料です。
@paul…..you are life saver. Everything I needed in one place
We have 4 accepted domain names in exchange 2013. I followed single name space configuration. I have added webmail.domain.com and autodiscover.domain.com.
For other remaining accepted domains what names should be added in the certificate? Only autodiscover.domain1.com ?
Could you please advise.
Root domain field. If you don’t want to request a wildcard certificate and instead want to specify each domain that you want to add to the certificate, leave this page blank. Choose
Exchange server 2013- I try create a new Certificate and says I haven’t got the correct permissions although I’m a domain admin.
Domain Admin is not an Exchange permission. AD admin permissions and Exchange admin permissions are two different things. It’s entirely possible to be a Domain Admin and have no permissions to do stuff in Exchange.
Hi Paul,
Thank you so much for all the helps and procedures that you give to us. unfortunately i cannot find a solution on how can I create a request for certificate that comes up in SHA2 or SHA256 in Exchange Server 2013, the CA tolds me that it only SHA1. I’d tried other solution from MS and Symantec but always resulting SHA1. hmm..
Thanks in advance!!! cheers!
Hi.
I have the same problem.
How I can resolved this.
Thanks in advance.
I have a problem with the outlook client
Once i create the .req file ,outlook stop working and give error relayed to ssl proxy server
Any ideas
Paul if we have multiple CAS Servers should we be putting both in the CSR?
You shouldn’t be putting any server names in the CSR.
Pingback: Godaddy Request Wildcard Certificate – Cyber Sun
Hi Paul,
I’ve successfully issued and installed the certificates from Digicert as you have recommended, however, since I have not specified the individual CAS server names in the certificate, rather the “exchange.domain.com” address, the “Name on the security certificate is invalid or does not match the name of the site” error appears when opening outlook.
Our certificate contains:
exchange.domain.com
http://www.domain.com.au
my cas servers are called:
exchange01.domain.com
exchange02.domain.com
Without adding the server names and re-issuing the certificate at an additional cost, what would you recommed I do if I wanted three green ticks in the outlook security alert box? Should I self-sign a certificate for my internal outlook users and name the two CAS servers in that or would that give me an error with the CA issuer?
Thanks in advance,
Alex
This is what you need:
https://www.practical365.com/avoiding-exchange-2013-server-names-ssl-certificates/
Hi Paul,
Thank you for step by step instruction. I have a question. Once I follow the steps, it will create a certificate request that expire one year. However, my certificate vendor offers three year certificate with great discount, how can I create an Exchange 2013 certificate request that will expire in three years instead of default one year?
Thanks,
-H
The validity period is controlled by the CA issuing you the certificate. There’s no change to the certificate request.
how does one generate a CSR? i installed exchange server 2013 but i am unable to get a certificate, i basically don’t know how to obtain one.
This very article you’re commenting on explains how to do that.
Paul,
Thanks for the article.
Could I use the UC cert for my office web apps farm too? Proviced I add a hostname in the final request window above like wac.exchange2013demo.com?
I know officewebapp wont allow a wildcard but will it allow the cert above?
thanks
Thanks Paul,
i have a question. If i have multi CAS in system (mailbox and cas were installed on the same SRV)
MBX1.itlab.test
MBX2.itlab.test
and external, internal URL for outlook anywhere are: mail.itlab.test
will i request certificate (https://mail.itlab.test) for only MBX1 or include MBX1 and MBX2
Pingback: Avoiding Server Names in SSL Certificates for Exchange Server 2013
Paul. Can you explain why you choose not to use wildcard certificate. I have a customer that we are migrating from Exchange 2007 to Exchange 2013. The customer has a wildcard certificate and want to continue with it
Wildcards have some support issues and caveats. For example with Exchange 2010:
https://www.practical365.com/exchange-2010-wildcard-ssl-certificates/
I’ve never used wildcards for a customer. Getting the right SSL cert is not expensive.
Thanks for a quick answer.
//Michael
What if you can’t put the CAS server/servers’ FQDN on the certificate? For example when you don’t own the internal domain naming rights and a provider such as godaddy refuses to put the name on the certificate because it can’t get verified?
I have the same problem dod you found any solution
Hi,
I have 3 windows 2008 servers.
1.192.168.0.1 AD/DNS
2.192.168.0.2 Member of domain/Exch2013
3.192.168.0.3 Member of domain/Exch 2013. I am unable to configure outlook account.
Hi,
I am unable to configure outlook.It is showing.There is a problem servers’s security cerficats.
Yes, you need to configure an SSL certificate from a trusted CA to replace the self-signed certificate on your Exchange 2013 Client Access server.
https://www.practical365.com/outlook-2013-ssl-trust-errors-when-connecting-to-exchange-server/
Pingback: Exchange 2013 SSL Certificate Organization and Department Names Wrong
hi,
im having problems with internal outlook users connecting to exchange 2013. can you please confirm that i do indeed need a CA cert for internals clients to connect to the exchange 2013 server, or is the the cert only for external users?
any help would be much appricated. thanks in advanced.
Ajay Paul
Pingback: Installing Certificates in Exchange Server 2013 | The Best Email Server
Pingback: Exchange 2013: How to Complete a Pending SSL Certificate Request | The Best Email Server