If it is your first time working with Exchange Server 2010 then you will quickly realise that you need to learn about the relationship between Exchange 2010 and SSL certificates.
Looking for information about Exchange 2013 SSL certificates instead? Click here to find out more.
SSL Requirements in Exchange Server 2010
Prior to Exchange Server 2007 an Exchange server could be deployed and by default would not require SSL for any of its communications. The wise move when deploying Exchange Server 2003 (for example) was to install an SSL certificate for IIS and use SSL for external access (eg Outlook Web Access and ActiveSync).
However this was not mandatory and it certainly isn’t unusual to encounter legacy Exchange environments that allow external access over insecure HTTP connections.
For Exchange Server 2007, and then again with Exchange Server 2010, Microsoft changed the default behaviour so that SSL was required for many services, even when they are only used internally. So a newly installed Exchange Server 2010 server that hosted the Client Access server role would have SSL enforced for services such as:
- Outlook Web App
- ActiveSync
- Exchange Web Services
- Outlook Anywhere
The administrator could disable that SSL requirement, but again the wise move is to protect Exchange Server 2010 communications with SSL encryption rather than allow them over insecure HTTP connections.
Because the SSL requirement is on by default the Exchange 2007 and Exchange 2010 servers are installed with a self-signed SSL certificate. This self-signed certificate does the job of securing any SSL connections, however because it is self-signed no connecting clients or devices will trust it, so it is unsuitable for long term use. The administrator needs to install a new SSL certificate for Exchange Server 2010.
If you’re using an internal DNS namespace that you don’t own or is not valid (eg, .local) you may also need to read How to Deal with SSL Requirements for Exchange when Certificate Authorities Won’t Issue You a Certificate
Exchange 2010 SAN Certificates
Administrators who have installed SSL certificates for Exchange before may be familiar with the general process involved. But they might not be familiar with the SSL certificate requirements for Exchange Server 2010.
In short, Exchange Server 2010 will respond to connections on multiple names. These names typically include:
- The fully qualified domain name (FQDN) of the Exchange server, eg ex2.exchangeserverpro.net
- DNS aliases for external access, eg mail.exchangeserverpro.net or webmail.exchangeserverpro.net
- The Autodiscover name of each SMTP namespace in the organization, eg autodiscover.exchangeserverpro.net
This makes a standard single-name SSL certificate unsuitable. Instead, Exchange Server 2010 must be installed with a SAN certificate.
SAN stands for Subject Alternative Names and is a type of SSL certificate that has an attribute that stores additional names for the SSL certificate to apply to. For example, here is the certificate used to secure Outlook Web App for Microsoft.
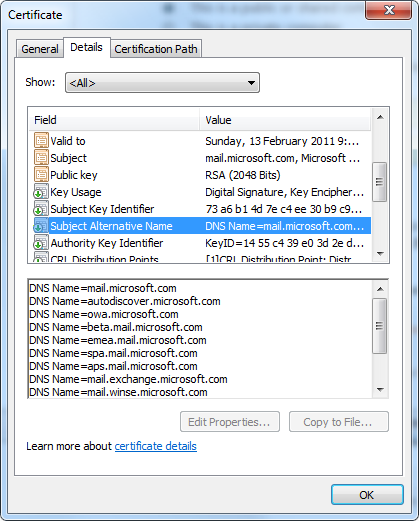
In Exchange Server 2007 it was possible to make a series of configuration changes so that a single-name SSL certificate would work. However these changes were complex, especially in larger environments, and the cost to perform and maintain them (in terms of administrative time spent) far outweighed the cost of a genuine SAN certificate from a commercial Certificate Authority.
Where to Buy SSL Certificates for Exchange 2010
There are lots of commercial Certificate Authorities to choose from when buying an SSL certificate for your Exchange Server 2010 servers.
My recommendation is to use Digicert’s Unified Communications Certificate, which I like for the pricing, generous licensing terms, and support such as unlimited reissues of the certificate (if for example you forget one of the alternative names the first time you request the certificate).
How to Install an SSL Certificate for Exchange Server 2010
The process to acquire and install an Exchange 2010 SSL certificate is as follows.
- Generate a new certificate request using the wizard built in to Exchange Server 2010
- Submit the certificate request to your chosen Certificate Authority
- Install the issued SSL certificate on the Exchange 2010 server
- Assign the new SSL certificate to the appropriate services on the Exchange 2010 server
The complete process is demonstrated in this article:
If you are performing these steps for training or demo lab purposes you may wish to save money and issue the certificate from a private Certificate Authority instead. If that is the case then follow the steps in this article:
When using private Certificate Authorities you can potentially encounter trust issues that prevent Exchange 2010 from using the certificate. See this article for details of how to fix this problem:
And finally, in some network environments with restricted access to the internet you may find the new SSL certificate can’t be used by Exchange 2010 because it can’t check it against the certificate revocation list. If that happens to you follow the steps in this article to solve the problem:




Did anyone figure out how to renew exchange 2010 self-signed certificates with SHA -2 encryption.
how we can replace the certificate for the hybrid
I have only small query i just wanted to know, my exchange 2010 certificate is going to expire end of this month October . i tried to renew the certificate .once i try to submit certificate to internal authority getting error //((Request Mode:
newreq – New Request
Disposition:
(never set)
Disposition message:
(none)
Result:
The data is invalid. 0x8007000d (WIN32: 13)
COM Error Info:
CCertRequest::Submit: The data is invalid. 0x8007000d (WIN32: 13)
LastStatus:
The operation completed successfully. 0x0 (WIN32: 0)
Suggested Cause:
The certificate request contained bad data. If you are submitting a saved request, make sure that the request contains no garbage data outside the BEGIN and END tags, and that the file containing the saved request is not corrupted. )
so i issue new certificate successfully but validity didn’t extend still showing same validity end of October please help me out..
The Real Person!
The Real Person!
Seems like you’re not copy/pasting the right info from the certificate request. Hard to say though, since I can’t see what you’re doing.
Please explain how to change exchange 2010 to renew self-signed certificates with SHA -2 encryption.
I have issue with Intermediate certificate on UTM. UTM need PKCS#12 or PEM certificate . To generate PEM certificate I need , Public , PEM Private key, intermediate certificate and PEM SSL certificate . How to generate PEM Private key from Exchange Server 2010 if you lost your PEM private key ? I did try with different way generate intermediate but still UTM complain that cd certificate chain is broken.
Hi Paul,
Do you recommend adding multiple Domain names (FQDN) in single SSL certificate?
My client uses 4 domains but right now the SSL certificate has only one domain in the SAN SSL certificate. So only one Autodiscover record for domain1.com. But some users using domain1.co.uk as primary smtp and get certificate error in Outlook.
We are planning to buy Organisation SSL certificate which will be expensive but will include all the Four domains with respective autodiscover entries also.
I guess no changes required on the virtual directories as we are keeping the original domain as it is? Just the DNS entry for the new domains.
Many thanks
Extremely helpful post. Wish to return back to the community soon.
If I make all url’s for Exchange 2010 the same name then I can use one SSL cert correct?
Thanks Daniel
The Real Person!
The Real Person!
Yes, in fact it is recommended to use as few certs as possible, so the same cert for multiple servers is ideal.
Pingback: England And Scotland Info At Wikipedia
Paul,
Thanks for this article. I also have bought your bood on migrate exchange 2003 to Exchange 2010 but I am still unsure on creating SSL CSR for my Exchange 2010. After reading the book and watching the video, I wasn’t sure for my environment how it needs to be entered since the internal domain is different than external domain. I still have exchange 2003 running with a valid SSL for OWA users. My internal domain for AD is xyzcompany.int but my external DNS domain is xyzcompanycorp.com. The exchange 2003 OWA DNS is mail.xyzcompanycorp.com.
I have setup Exchange 2010 CAS and HUB. During SSL creation, for OWA, I have entered
exchange2010server.xyzcompany.int for OWA Intranet and mail.xyzcompanycorp.com for OWA internet. For activesyn and autodiscover, I entered, mail.xyzcompanycorp.com. For Outlook anywhere, I entered, mail.xyzcompanycorp.com, xyzcompanycorp.com as well. For HUB transport, I entered, xyzcompanycorp.com, and for Legacy, I entered, legacy.xyzcompanycorp.com. I am not sure if this is correct or not.
Any suggestion or am I in right track?
thanks!
Pingback: simply click blog.clone-army.org
http://www.digicert.com/internal-names.htm
It might be worth adding to this some information around the planned changes by the CA/Browser Forum preventing internal names on certificates after Nov 2015. I haven’t looked but im sure you already have something up on here around the split DNS solution etc.
Excellent site by the way. Keep up the great work.
Lee
Pingback: building consultants
Paul,
Your tips for exchange server been very helpful for our business. Our team regularly follow your recommendation and solutions for exchange set-up and troubleshooting.
SSL certificates are the most common in 50% plus troubleshooting. You recommended Digicerts UC certificates and we purchased many certs from them for our customers. We paid too much for UC certificates.
Recently I searched for alternate option that can offer same features and good in price. I found Comodo UC certificates but they are almost same in price compare to Digicert.
I’m worried that single domain ssl cost too less and SAN/UC certificates cost too much. I contacted many ssl suppliers, both direct CA and reseller channel.
We found cheapest UC certificate from ssl2buy.com. I checked with this company and their partners, they’re very trusted ssl supplier. I purchased 5 UC certs for trial and all works fine. They sell comodo uc certificates just for $60. I could secure 4 domain names – $15 per domain. I found interesting is, I could add more domains and-sub-domains in same ssl. I installed the same ssl on multiple IIS servers. This ssl reduced ssl budget almost 60%. Apart from the pricing, they offer good tech support, automated processing and 30 days refund.
I recommend you share this website to your readers:
https://www.ssl2buy.com/comodo-multi-domain-ssl.php
Eric
“This makes a standard single-name SSL certificate unsuitable. Instead, Exchange Server 2010 must be installed with a SAN certificate.”
Guess this answers my question unless it really can be worked around.
Doesn’t installing E2010 immediately break E2k3 mobile access?
Since Exchange without mobile access is almost useless in this day and age, how the heck can we achieve zero down-time if we have to install E2010 generate a certificate and wait for validation?
Thanks for putting up with me!
Paul,
Great resource.
If we plan to move the mailboxes from E2k3 to 2010 over a weekend, can we just export/import our current simple mail.domain.com certificate?
Thx.
hi,
do i need a ssl certificate for Active sync for mobile devices
The Real Person!
The Real Person!
Yes, mobile devices will attempt an SSL connection to your server, so an SSL cert is required for the server.
Some more info for you:
https://www.practical365.com/exchange-2010-activesync/
the generated .req file is corrupted we c’ant generate a certi what shoud we do nowing that we have local cert autoraty
hi,
i Want to ask you a question when publishing outlook anywhere ( for exchange 2007/2010 ) do we need a public
certificate or the Private CA enough ?
and thanks in advanced.
Hi Paul,
Is there anyway to delete Default Email policy in 2010, which was synchronized by exchange 2003
Pingback: Microsoft Exchange Server - Sysnative Forums
Pingback: Creating a Certificate for Exchange 2010 | viruk67
Pingback: Tofa IT » How to Deal with SSL Requirements for Exchange when Certificate Authorities Won’t Issue You a Certificate
Hi Paul – what do we do when we can no longer get SAN certs with .local addresses in them? Can we get Exch 2010 to function properly with just the public FQDNs in the SAN cert?
Thanks,
Matt
P.S. Great site by the way.
Paul
I commented on a recent article you submitted discussing Exchange 2013 DAGs. I have a question about SSL Certificates and how they work in a DAG. Currently we have a UC cert on our Exchange 2007 server. In a DAG, do you need a cert on each server? I suspect you do, but can you explain how this should work in the new 2013 Exchange DAG?
Paul,
I read several of your articles concerning Exchange 2010 certificates since I just installed SBS 2011 for a client.
In your article, under ‘Where to buy SSL certificates for Exchange 2010’ , you recommend the DigiCert Unified Communications certificate. However, based on the DigiCert website’s info and my own experience the DigiCert UC certificate does not include SSL certification. After having installed the UC certificate OWA still complains that the web site certificate (self-signed) is untrusted.
Looks like the SSL certificate is sold separately and is also needed from DigiCert to complement the UC certificate.
Like the other comment says, otherwise this is a helpful and well written article which certainly put me on the right path to solving many of my certificate installation related questions.
The Real Person!
The Real Person!
“After having installed the UC certificate OWA still complains that the web site certificate (self-signed) is untrusted.”
If you’re connecting to OWA and still seeing the self-signed cert then it indicates that you have not enabled the new certificate for the correct services.
Note the four step process after the “Where to buy…” section in the “How to install…” section. Step 4 is:
“Assign the new SSL certificate to the appropriate services on the Exchange 2010 server”
That is demonstrated towards the end of this article on configuring an SSL certificate for Exchange 2010:
https://www.practical365.com/configure-an-ssl-certificate-for-exchange-server-2010
Pingback: Publishing Exchange 2010 Outlook Web App with ISA Server 2006
Pingback: Exchange ActiveSync/Windows Phone Outlook Error 80072F0D
Pingback: FAQ: Do I Need Autodiscover Names in the SSL Certificate? « MidThought's
Pingback: Securing Exchange Server 2010 POP3 Remote Access
Just to let you know that you should add the certificate authority COMODO. Your page hits almost at top in our country for exchange 2010 certificates (google serch). We however, use COMODO mainly because prices are extremely cheaper than verisign. And security is not a concern because all the Cert Authorities out there are supposed to comply with strict standards in the industry.
Anyways, excellent article.
Pingback: Exchange SSL Certificate Management Survey
Pingback: Exchange 2010: Autodiscover Names and SSL Certificates
Pingback: Configure an Exchange 2010 SSL Certificate
Pingback: Autodiscover and SSL Warnings during Exchange 2010 Migration « Microsoft geek
Pingback: Autodiscover and SSL Warnings during Exchange 2010 Migration - Exchange Server Pro
Pingback: Exchange 2010 SSL Certificates – Exchange Server Pro « JC’s Blog-O-Gibberish