Updates for Exchange 2013, 2016, and 2019
Earlier today, Microsoft released security updates for Exchange Server 2013, 2016, and 2019. The updates address known vulnerabilities, which means that they fix problems known to exist in the wild. It’s therefore important to install the security updates as quickly as possible, especially on any Exchange server connected to the internet. Microsoft says that they are unaware of any attackers exploiting the vulnerabilities, but the nature of the beast is that once people learn about software vulnerabilities, the affected servers become candidates for compromise.
The security updates are for:
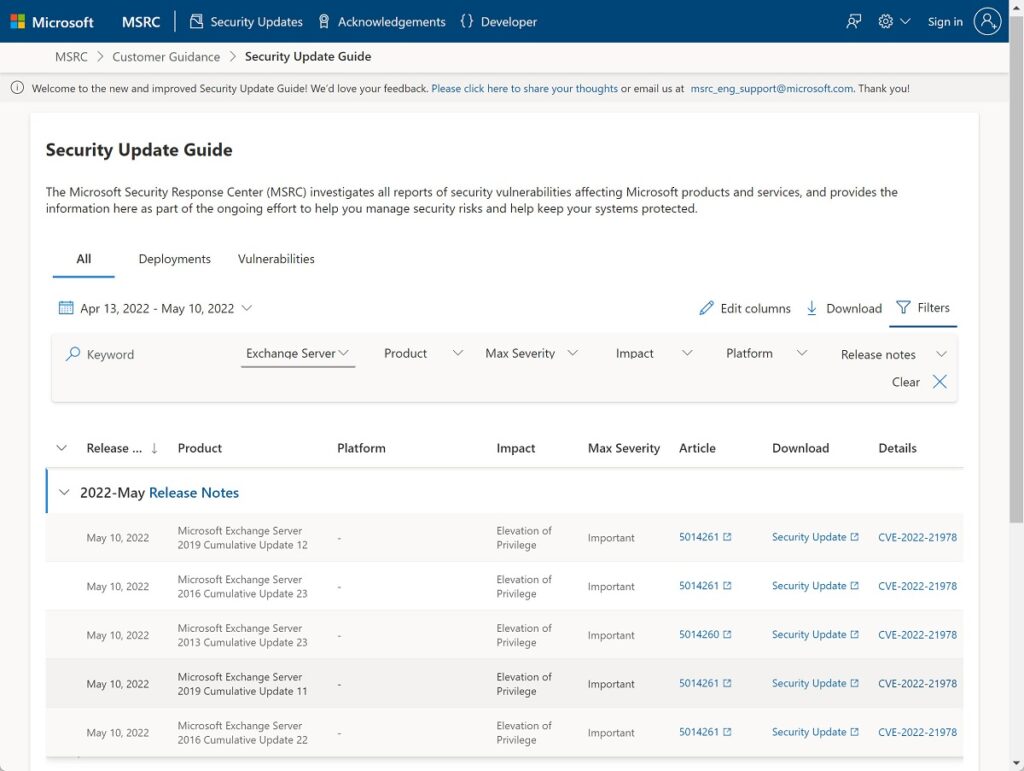
Details of the vulnerabilities fixed are available in the Microsoft Security Response Center (Figure 1). It looks as if the problems are all elevation of privilege, which isn’t good news because this kind of problem can allow attackers to take complete control of servers.
Exchange Online and Hybrid Servers
Apart from upgrading hybrid servers used with Exchange Online, no further action is necessary to protect Exchange Online. As you’ll recall, Microsoft recently released an update to allow organizations to remove the last physical Exchange server in a hybrid environment. The big caveat here is that this is only possible after the installation of Exchange 2019 CU12. Other considerations exist, like having to perform recipient management through PowerShell, but the existence of vulnerabilities in on-premises servers underlines the value of being able to remove unwanted servers.
Auto-Elevation to Install Security Updates
In a separate post, Microsoft explains that they are now releasing security updates and hotfixes as self-extracting auto-elevating executables. This is in addition to the existing Windows Installer Patch format. The reason for the change is that Microsoft receives support calls when administrators have problems applying security updates, many of which are because the installation runs without sufficient permissions. Microsoft notes that this can leave an Exchange server “in a bad state,” which is putting it mildly. Auto-elevation of permissions should address the issue.
Prepare Active Directory
The last point of note is that Microsoft emphasizes the need to run the Exchange server installation program with the /PrepareAllDomains switch AFTER installing the security update. This command makes sure that the domains in your Active Directory forest are prepared for Exchange server. The account used to run /PrepareAllDomains must be a member of the Enterprise Admins security group.
You only need to run /PrepareAllDomains once per organization (not after updating each server) and the change applies to all servers within the organization. Microsoft says that the step is necessary “because of additional security hardening work for CVE-2022-21978,” which is one of the vulnerabilities addressed by the updates.
Ready, Steady, Go
Last year’s Hafnium experience taught everyone how quickly attackers can exploit unpatched servers. Don’t let your server be compromised because of a known and patched vulnerability. Carve out some time to install this security update on your on-premises servers.




Updating cu23 on edge sever required any special consideration or additional steps like do we need to re-subscribe edge subscription? Please advise.
Also, please let me know CU23 on hybrid exchange 2016 required any additional steps or we can just run with elevated cmd.
I’m not aware of any impact the installation of a CU has on an edge subscription. There’s no difference to installing the CU on a hybrid server.
can someone help in this case when we send email to any reception using mx.google.com we receive this error.
Your message wasn’t delivered due to a permission or security issue. It may have been rejected by a moderator, the address may only accept email from certain senders, or another restriction may be preventing delivery.
mx.google.com gave this error:
[37.xx.xx.xx] Our system has detected that this message is likely unsolicited mail. To reduce the amount of spam sent to Gmail, this message has been blocked. Please visit https://support.google.com/mail/?p=UnsolicitedMessageError for more information. t7-20020a05600c198700b003a04aec7e9esi8099351wmq.21 – gsmtp
Google doesn’t like the email you send. Is your domain on a blocked list by any chance?
Hello
After installing 2016 CU23 I’m seeing a lot of “Failed to read in memory manifest validation XSD schemas for version ‘1.1’.” warnings in the application event log (Id 6010, source “MSExchangeApplicationLogic”). There’s no additional information in these warnings. Any idea what’s that supposed to tell me?
A single server generated over 5.000 of these warnings during the last 10 hours.
KB5014261 has been installed after CU23
Thanks
Niko
It looks like some file might be missing. You could try installing CU23 again (make sure that you use an account with admin privileges), or file a support incident with Microsoft to see what they think.
We have not applied the may SU, but we installed cU23 for Exchange 2016 in may; at that time, we ran AD and Exchange schema updates.
We are going to apply for May SU. Do we still have to /preaparalldomains on one server?
It wouldn’t do any harm to run /prepareADDomains on one server. That way you’re fully covered.
We have not applied the May SU, but we installed cU23 for Exchange 2016 in May and left the SU not to install in May; at that time, we ran AD and Exchange schema updates.
We are going to apply for May SU. Do we still have to /preaparalldomains on one server?
Hi tony
can you please tell the user impact during the CU23 update.Will outlook have issue while running the patch although its hybrid environment.
Thanks
Apart from the normal downtime, I haven’t heard of any issues with Outlook following the CU23 update. That being said, there are many versions and configurations of Outlook running in the real world, which is why it’s wise to test an update before applying it to production servers.
is there any know issue reported after this may 2022 update for Active Sync connecting from android
Tony, regarding the /PrepareAllDomains command. We have two Exchange servers – Do we need to patch both servers first and THEN run the /PrepareAllDomains or can we just patch one, run the /Prepare and then get the 2nd one patched? That wasn’t made clear in any documentation I’ve read so far. Yes, it says it’s only needed to be ran once per org and after patching, but that still didn’t clarify how that works with multiple servers. Thanks!
Ah-ha, found it on their blog:
Can we run /PrepareAllDomains before all of our Exchange servers are updated with May 2022 CU?
Yes. There is no dependency between running of /PrepareAllDomains and installation of updates on all servers. /PrepareAllDomains can be run when as least one machine is updated (from that machine) but could be postponed and be run when you are ready to address that particular CVE.
The important thing here is that /PrepareAllDomains exists to make sure that Active Directory is secured against a known vulnerability. As Microsoft points out, you apply the SU to at least one server (which updates the organizational information) and then update Active Directory. It would be nice if everything was in one procedure, but they are separate…
hi
whether we need to run the prepared command run two times. one is before C23 installation and another one before security update. whether it is necessary to execute two times
It is necessary to run the update and then run Setup /PrepareAllDomains.
If we are currently on Exchange 2016 CU22, should we install this new Security update before updating to CU23, or at the same time? If at the same time, which order should they be installed? SU first and then CU23, or CU23 first and the SU? I’ve been scouring online documentation and I can’t find a clear answer to this.
Thanks for all you do.
I would apply the security update now, unless you’re ready and waiting to go to CU23. In that case, I’d go:
CU23.
SU for CU23.