During an Exchange 2003 to 2010 transition a legacy namespace is configured for users who are connecting to Exchange 2003 mailboxes. The Exchange Server 2010 SSL certificate includes the legacy name in its Subject Alternative Name (SAN) field, but this certificate then needs to also be installed on the Exchange 2003 server.
Export the Certificate from Exchange Server 2010
To export the certificate from Exchange Server 2010 launch the Exchange Management Shell and run the following commands.
First determine the thumbprint of the SAN certificate that is installed.
Get-ExchangeCertificate Thumbprint Services Subject ---------- -------- ------- E8D129180C1334D50DBE17A26795BEE0A0AEA9B3 ...WS. CN=mail.contoso.local, OU=IT Dept, O=Contoso Pty Ltd, L=Brisban... C5C2B0F04397D1C2C2C9834C48B268EA53F835B4 IP..S. CN=ex2010
In this example the thumbprint is “E8D129180C1334D50DBE17A26795BEE0A0AEA9B3”.
Next export the certificate to a file by running the following command.
$file = Export-ExchangeCertificate -Thumbprint E8D129180C1334D50DBE17A26795BEE0A0AEA9B3 -BinaryEncoded:$true -Password (Get-Credential).password
A popup dialog appears for you to enter a password to protect the private key. The username field is not important but requires something to be entered in it for the dialog to accept, so just enter “username” and then a strong password.
Next run the following command to generate the file.
Set-Content -Path "C:Adminex2010cert.pfx" -Value $file.FileData -Encoding Byte
Copy the file to the Exchange Server 2003 server.
Import the Certificate on the Exchange 2003 Server
On the Exchange 2003 server launch mmc.exe and add the Certificates snap-in to the console, choosing the “Computer account” context.
Choose Local Computer and then click Finish, Close, and OK to return to the console.
Right-click Personal and choose All Tasks –> Import. Step through the Certificate Import Wizard choosing the certificate file that was copied from the Exchange Server 2010 server.
Enter the password that you used when the certificate was exported from Exchange Server 2010.
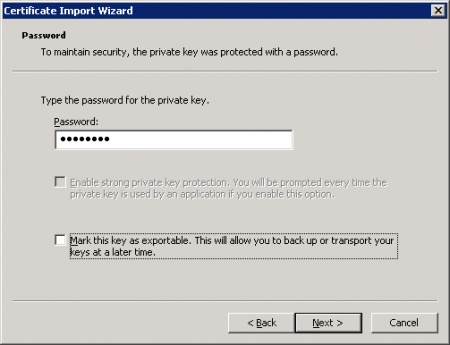
Place the certificate in the Personal certificate store.

Complete the wizard and confirm that the import was successful.




Pingback: Exchange 2016 FAQ: Can I Re-Use My SSL Certificate?
Pingback: SSL Certificate Installation and troubleshooting Exchange 2010 / 2013 « TechRid
I purchased a 3 party cert from Go Daddy. The cert request was generated from my exchange server called Server1. I have a second Exchange server called Server2. I included the name for Server1 and Server2 in the cert I down loaded from Go Daddy as the cert would cover 5 names. I down loaded the cert from Go Daddy and completed the request on Server1 the exchange server that requested the certificate. Then I enabled all the services I wanted to uses with this certificate. I want to then export the certificate to a file and import the certificate into Server2 and the certificate covers the name of Server2 as well. Server2 keeps on telling me that the thump print is all ready in use. So I requested a new cert from Server2 and want to use this Go Daddy certificate to secure this server but don’t know how to go forward from here. I see the enrollment request in the Console Root For Certificates, but I don’t know to use the console to full fill the request.
I’m confused. If you have generated a new certificate request (CSR) from Server2 it is exactly the same process you used to acquire the certificate for Server1. You submit the CSR to your CA of choice (such as GoDaddy) and they issue you the certificate.
Your site is amazing! I want to set the new SAN cert up, but I’m not yet ready to switch to OWA to the new server. In that case, should I also include the internal FQDN of the 2003 server in the SAN cert? I’m concerned if I import the new cert on the 2003 server without it, I’ll run into name mismatch errors. Thanks!
The cert on the 2003 server should include any names clients already use to connect to that Exchange server via SSL. For Exchange 2003 that usually just means the public namespaces for OWA etc, as there are no web services used internally that might be running on the FQDN with SSL enabled by default (like AutoDiscover in 2007/2010/2013).
So in my experience, the existing public namespaces plus the new legacy namespace are usually enough.
I try to export my verisign SAN certificate from the new exchange 2010 to my 2003 legacy exchange server, but when i use your procedure, after try to export receive the error: The private key couldn’t be exported as PKCS-12. It either couldn’t be accessed or isn’t exportable. How can i resolve this….. thanks in advance.
Did you have any respond about this? I’m Having the samen problem
You guys have any updates on this issu? Having the same problem here.. I think the certificate was generated and imported with the option of exportable private key unmarked.
Regards.
Contact your certificate issuer and get it rekeyed or reissued.
Paul, It is possible to export a ceritfied from exchange 2007 to exchange 2010 🙂 ?
Yes, correct.
So you import the cert. Do you have to go into IIS and change the cert the website uses?
After importing the Exchange 2010 cert into the front-end exchange 2003 server. does the server need a reboot?
No restart required. Just bind the cert in IIS.
Very nice post, if I have a front end server for OWA 2003, do I need to import it on that server as well?
thanks,jb
Hi Jason, import it anywhere that will be accepting SSL connections for the name(s) in the cert. The 2003 FE will be accepting SSL connections to the legacy name, so yes, import the cert there.
Thanks for the reply!! We created and imported the cert today. I just haven’t flipped the DNS yet.
Thanks for this, can’t believe this is not explained anywhere on MS Technet.
One additional step if you already have a certificate on the Exchange 2003 server – is to run the Cert wizard in IIS and Replace the existing cert with the new imported one.
I currently have a exchange 2003 with standard SSL with Certificate Authority. Do I need to remove this Standard SSL and create a SAN SSL on the Exchange 2010 server and them export the exchange 2010 cert. to exchange 2003 server?
If I remove the standard SSL what happens to my OWA and RPC withun HTTPS connections?
When I export SAN SSL to exchange 2003 for co-existence can I only add the legacy name in my internal DNS zone?
Alan, Exchange 2010 works best with SAN certificates. Trying to use a single name SSL certificate with Exchange 2010 is frankly a nightmare.
You only need to export the SAN certificate to the Exchange 2003 server if you plan to run in co-existence for a period of time. The point of doing this is so that the Exchange 2003 server has a valid certificate installed with the legacy namespace as one of the subject alternate names.
OWA and RPC should continue to work as long as the SAN certificate includes whatever name your users use to connect to those services.
The legacy name needs to be resolvable both internally and externally.
OK so when I create the SAN cert on Exchange 2010
For OWA:
Intranet = serverexchange2010.domain.com
Internet = mail.domain.com
Legacy:
Intranet = legacy.serverexchange2003.domain.com
Internet – legacy.mail.domain.com
So legacy.serverexchange2003.domain.com will point to the owa link on exchange 2003 server instead of exchange 2010?