Important Change Coming on May 15
Microsoft published message center notification MC251870 (Microsoft 365 roadmap 68863) on April 21 to warn tenant administrators that Microsoft Graph privacy controls will replace the Office Delve privacy control after May 15, 2021. This is an interesting change first announced in August 2020 which deserves some examination and potential action as the switchover approaches.
Delve, the Office Graph, and Privacy
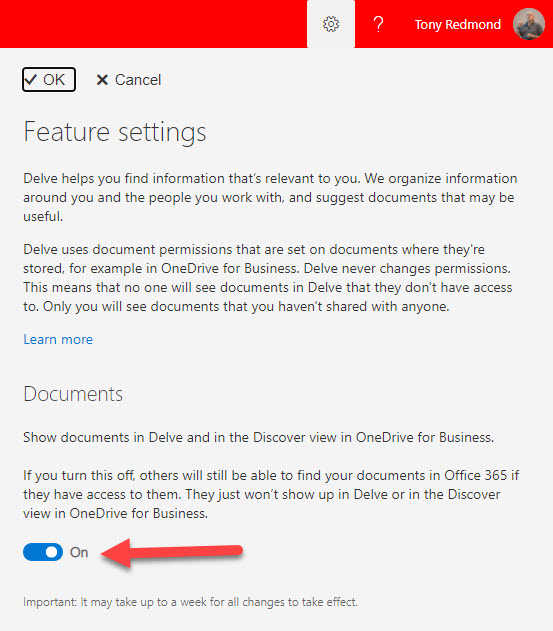
The first thing to understand is the Delve privacy control and its function. Users set the control in Delve feature settings (Figure 1). When enabled, documents owned by the user become candidates for Delve and OneDrive for Business to highlight to other people who have access to those documents.
A useful script to report on the Delve setting for user accounts in a tenant is available in GitHub.
The privacy control exists because many users feared that Delve would reveal confidential information to others. In fact, poor permissions practice is invariably the root cause of when Delve shows documents to other people which should not have been. The rule is simple: if permissions on a document allow someone to see it, Delve might highlight the document to that person. The privacy control stops Delve showing documents belonging to a user and calms the harassed nerves of those who imagine that Office 365 might let some of their secrets into open view.
Delve was the first Office 365 application which attempted to use insights powered by the Graph to help people master information. In 2015, the Graph meant the Office Graph, a database which stores information about items like documents and people as nodes in a graph index. The Office Graph connects different items together by understanding the relationships between the items. By applying machine learning and analytics, Microsoft constructs insights from the graph data to allow applications like Delve present information to users.
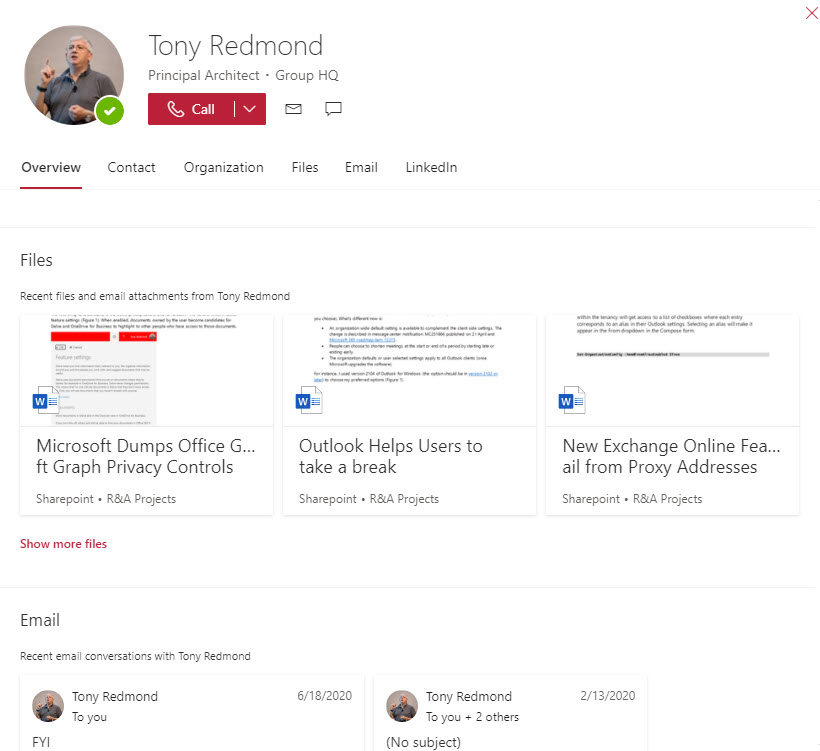
An example insight is the set of documents authored by others Delve suggests to a user. If a user sets their privacy control to exclude their documents from the Office Graph, the analytics creating the insights can’t access this data and the documents will never feature. Other insights created by the Office Graph include the set of suggested SharePoint sites shown to a user, the recommended feed in the Outlook mobile app, and the documents shown on users’ profile cards (Figure 2).
The SharePoint Option
Tenants can disable access to the Office Graph for SharePoint Online for all users by updating the Delve option in the classic settings section of the SharePoint admin center (Figure 3). This setting trumps individual settings. In other words, if SharePoint Online blocks Delve, users cannot enable documents visibility in Delve settings for their account.
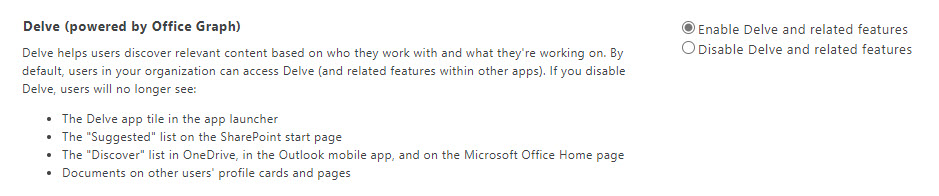
The SharePoint admin center used to present this option as disabling Office Graph. This caused all sorts of problems as people thought that if they disabled the Office Graph, they would also disable the Microsoft Graph. These are different entities. The Microsoft Graph powers the Office Graph but disabling the Office Graph for document insights does not stop applications like Teams and Planner which are built using the Microsoft Graph APIs from working.
Moving Privacy Controls to the Graph
Microsoft says that before May 15 they will take a snapshot of the current privacy settings in a tenant and use that snapshot to update the new Graph privacy controls to match what’s already in place. After May 15, administrators should use the Graph privacy controls. Microsoft also say that tenants who have disabled the Office Graph setting for SharePoint Online need to move to the Graph privacy controls. The existing Delve controls will remain in place and Microsoft will apply the strictest of the Delve and Graph privacy controls defined in a tenant.
All of which leads to the question of what Graph privacy controls are available. Two exist:
- isEnabledInOrganization: This setting controls if insights are available within an organization. By default, the setting is enabled. If disabled, no insights are created.
- disabledForGroup: This setting holds the GUID (object identifier) for an Azure AD group. The Microsoft Graph ignores data belonging to members of the group when it generates insights. I describe how to update this setting using the Graph Explorer in another article.
Both settings are in the Graph organization configuration and apply to the Graph Insights resource type. What’s changed since Microsoft’s original announcement in August 2020 is that administrators can use the Microsoft Graph PowerShell SDK to manage the settings. I downloaded the Microsoft Graph PowerShell SDK from the PowerShell gallery and followed the Microsoft documentation to manage the privacy settings.
Updating Graph Privacy Settings with PowerShell
To check the current configuration for privacy controls, we need to:
- Connect to the Graph with Connect-MgGraph. You will be asked to perform a device authentication.
- Use Get-MgOrganization to grab the tenant identifier. You don’t need to run this cmdlet if you already know the tenant identifier, but it is convenient to store the tenant identifier in a variabe
- Run the Get-MgBetaOrganizationSettingItemInsight cmdlet to fetch the current privacy settings. Notice that the DisabledForGroup setting is populated with the identifier for a group holding the users who do not want their data used for insights.
Connect-MgGraph -Scopes "User.Read","User.ReadWrite" $TenantId = (Get-MgOrganization).Id Get-MgBetaOrganizationSettingItemInsight -OrganizationId $TenantId Id DisabledForGroup IsEnabledInOrganization -- ---------------- ----------------------- c9758609-d33b-4eea-976b-d8e43a2ad135 True
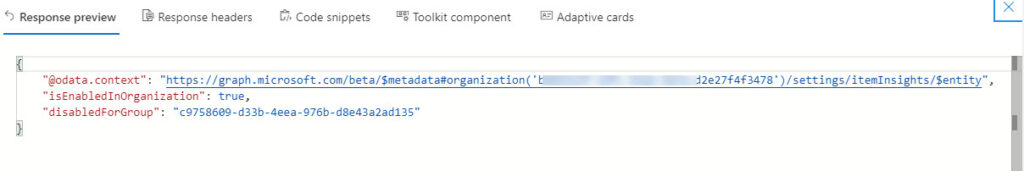
Using the URI https://graph.microsoft.com/beta/organization/GUID-org-id/settings/iteminsights in the Graph Explorer fetches the same information (Figure 4).
To update the organization setting to disable insights, you connect using a different scope (permission) required to update the settings. Once connected, run the Update-MgBetaOrganizationSettingItemInsight cmdlet to set IsEnabledInOrganization to $False. This cmdlet is picky about the colon and will fail if you omit it.
Connect-MgGraph -Scopes "User.Read","User.ReadWrite"
$TenantId = (Get-MgOrganization).Id
Update-MgBetaOrganizationSettingItemInsight -OrganizationId $TenantId -IsEnabledInOrganization:$False
Get-MgBetaOrganizationSettingItemInsight -OrganizationId $TenantId
Id DisabledForGroup IsEnabledInOrganization
-- ---------------- -----------------------
False
Insights are now disabled for every user in the tenant. Reversing the process is done by running Update-MgBetaOrganizationSettingItemInsight to set IsEnabledInOrganization to $True:
Update-MgBetaOrganizationSettingItemInsight -OrganizationId $TenantId -IsEnabledInOrganization:$True
Get-MgBetaOrganizationSettingItemInsight -OrganizationId $TenantId
Id DisabledForGroup IsEnabledInOrganization
-- ---------------- -----------------------
True
Notice that the value for DisabledForGroup is now null. To update the setting to restore the original group, we run Update-MgBetaOrganizationSettingItemInsight again:
Update-MgBetaOrganizationSettingItemInsight -OrganizationId $TenantId -DisabledForGroup "c9758609-d33b-4eea-976b-d8e43a2ad135"
Of course, the two settings can be updated together:
Update-MgBetaOrganizationSettingItemInsight -OrganizationId $TenantId -DisabledForGroup "c9758609-d33b-4eea-976b-d8e43a2ad135" -IsEnabledInOrganization:$True
What’s Important and What’s Not
If your tenant has never had users asking to disable Delve, then you don’t need to do anything. The new Graph privacy controls will come into play on May 15, and you can use them thereafter if necessary. On the other hand, if some users have disabled Delve, it would be a good idea to find out who they are and do the necessary work to switch them to Graph-based privacy controls by creating a group containing the users and updating the organization configuration with that group’s identifier.





Did anybody’ve been able to turn Item Insight off for users using a group?
I am able to apply the restricition to a group with the Update-MgOrganizationSettingItemInsight command. And I see the restricted group in the Get-MgOrganizationSettingItemInsight.
However this does not reflect on the Get-MGuserSettingItemInsight command and when I look at the Delve information of the user, i still see the files he is working on.
Only applying the restriction manually in the users profile-privacy settings or by the command Update-mgusersettingiteminsight, the setting seems to be working.
This works in my tenant. Maybe you should log a call with Microsoft support to ask them to check things out?
Thanks Tony,
already did, but it is extremly difficult to find a competent person for these kind of questions….
I hear you…
Did anybody do any tests in the UI on this.
Does turning off Item Insight for a group also turns off the UI switch of a user in that group?
I actually would expect that this is then turned off and greyed out.
But after (almost) 24 hours this is still turned on in the users UI.
https://myaccount.microsoft.com/settingsandprivacy/privacy
Thanks,
Franck
I have the SDK Version 1.6.0. As stated earlier I have a connection through Azure AD before executing the Graph commands, so therefore I assume to have a connection to AAD (eligable Role and permissions are given).
Hello Tony,
If I followed your instructions for reading the settings with the graph powershell module and I am getting an error:
In advance I connected to the corresponding AAD because at my first try, powershell mentioned that I have to have a connection
and then I executed this:
Connect-MgGraph
Select-MgProfile beta
$TenantId = (Get-AzureADTenantDetail).ObjectId
Get-MgOrganizationSettingItemInsight -OrganizationId $TenantId
and I was getting the error:
PS C:\WINDOWS\system32> Get-MgOrganizationSettingItemInsight -OrganizationId $tenantid
Get-MgOrganizationSettingItemInsight : Object reference not set to an instance of an object.
In Zeile:1 Zeichen:1
+ Get-MgOrganizationSettingItemInsight -OrganizationId $tenantid
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : InvalidOperation: ({ OrganizationI…ndProperty = }:f__AnonymousType50`3) [Get-MgOrganizationSettingItemInsight_Get], RestException`1
+ FullyQualifiedErrorId : ErrorUnHandledExceptions,Microsoft.Graph.PowerShell.Cmdlets.GetMgOrganizationSettingItemInsight_Get
PS C:\WINDOWS\system32>
What am I doing wrong?
Greetings Andre
Did you get a good value in $TenantId?
Yes I did, the value is filled correctly.
OK. I just reran the commands on my tenant and they worked OK. Are you signed into Azure AD with an admin account?
I assume you’re running the latest version of the Graph PowerShell SDK?
Hi Tony,
the same issue here, I tried on more tenants (dev (Microsoft Developer E5), test in our company),
1. I am global admin
2. I installed last version of MS Graph module
3. I use correct tenant id
The same in UI Item Insights settings in O365 Admin Center, I get exception “ErrorUnhandledExceptions” on both tenants.
I connected to my development tenant and ran the commands and everything worked. I think you’ll have to report the issue to Microsoft to discover what is causing the problem. I obviously can’t debug your tenants 😉