New Group Ownership Governance Policy is Generally Available
Microsoft announced the general availability of the Group Ownership Governance policy on April 26, 2022 (MC364773). The new policy, otherwise known as the ownerless groups policy (which is how Microsoft’s documentation refers to the policy), helps organizations ensure that every Microsoft 365 group (and team) has at least one owner.
Microsoft has been working on this policy for years. Now that it has eventually landed, it’s worthwhile asking if the policy has any value. It’s obviously good that groups have owners, but:
- Groups and teams continue to work happily without owners. Conversations continue and members can access files in the SharePoint sites owned by the groups.
- Administrators can perform ownership functions (like adding new members) if necessary.
- Intelligence exists in Microsoft 365 apps to stop groups and teams from becoming ownerless. For instance, if you are the last owner in a group and you attempt to leave it, OWA won’t let you (Figure 1). Similar blocks exist in Teams and SharePoint Online, and if you try to remove the last owner using PowerShell by running a cmdlet like Remove-AzureADGroupOwner, the last owner logic prevents this from happening.
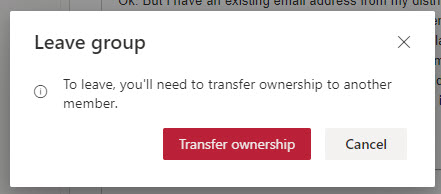
In the past, groups could get into an ownerless state without much difficulty. The logic in apps to prevent accidental ownership removals stopped many groups from losing their last owner. Today, groups usually only become ownerless when they only have a single owner, and an administrator deletes the owner’s account using PowerShell or a Graph query.
Even if a group falls into an ownerless state, it’s not a disaster. It’s certainly an undesirable condition when no one takes care of a group, but it’s not terrible.
Configuring the Ownerless Groups Policy
The first step to detecting and fixing ownerless groups is to enable the ownership governance policy. Go to the Microsoft 365 admin center and select the Microsoft 365 Groups settings under Org settings. You’ll then have the chance to enable and configure the policy (Figure 2). Note that you must specify a user account or a Microsoft 365 group as the sender for communications about expiring groups.
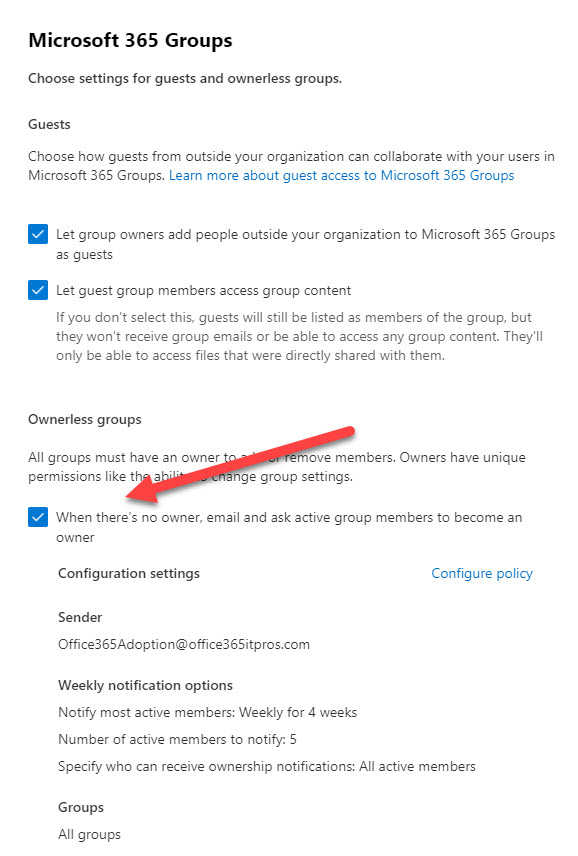
The policy settings control what happens to ownerless groups (Figure 3).
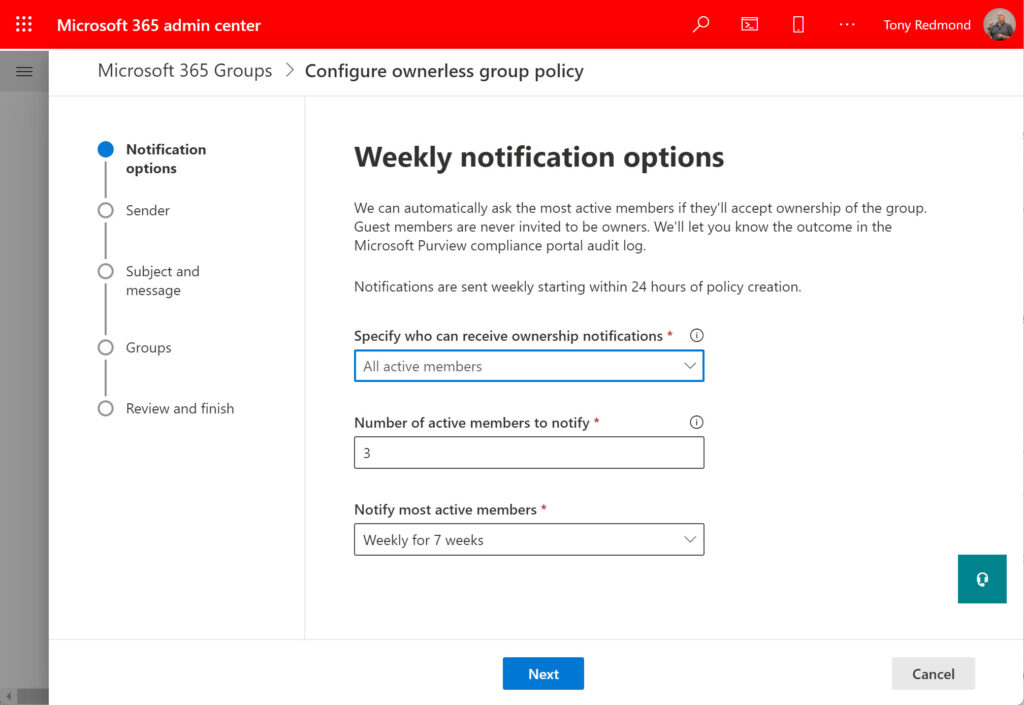
The Notification options in Figure 3 govern:
- Which group members receive notifications when a group becomes ownerless. By default, a random selection from the remaining active tenant members (not guests) in an ownerless group will receive notifications. An active group member is someone who participates in the group (for instance, by posting to a group conversation or channel). The selection process does not take existing group ownership into account.
- If you want to limit the set of people to receive invitations to become group owners, you can select a security group. Exchange Online will then only send invitations to the members of the security group. You can also block accounts from becoming group owners.
- The number of members to receive invitations to become group owners. The minimum is 1 and the maximum is 90.
- How many times the people nominated to become owners receive email notifications. This can range from once (weekly for 1 week) to seven times.
The next step selects the mail-enabled object the notifications about ownerless groups come from. The object can be a user mailbox, shared mailbox, or group. I use a shared mailbox and it’s worked well.
You can customize the text and subject of the notification emails and include a URL to a website to help users understand what to do when they receive an invitation to take over a group.
Finally, you select the set of groups that come within the scope of the policy. The default is to apply the policy to all groups, but you can select specific groups. If you do, you’ll discover that the UI used to select groups is suitable if you only want to choose a couple of groups. Thereafter, the UI proves to be boring and cumbersome. This is somewhere that an adaptive scope would be useful to identify target groups.
Engage with Microsoft 365 experts like Tony Redmond at The Experts Conference 2022 in Atlanta, GA September 20-21. Ask your questions 1:1, get hands-on in our M365 Managements Shortcuts Village, and network with peers!
Licensing
Traditionally, Microsoft required Azure AD Premium P1 licenses for add-on management capabilities for Microsoft 365 groups like the expiration policy. The good news is that tenants with Office 365 E3 or above licenses do not need additional premium licenses for “basic” operation of the ownerless group policy. Basic means that you don’t use a security group to allow or block certain users from receiving ownership requests. If you decide that tenant admins need to control who receives invitations, each of the tenant accounts in the groups coming within the scope of the policy must have an Azure AD Premium P1 license.
Detecting Ownerless Groups
Once the ownerless group policy is active, a background job scans for ownerless groups weekly. When the job detects an ownerless group, it sends an email to selected members to ask them to take ownership. The email is an actionable message (which only works when the recipient is signed into their home tenant) allowing the recipient to accept or refuse ownership. Figure 4 shows an example of an invitation for a user to become a group owner.
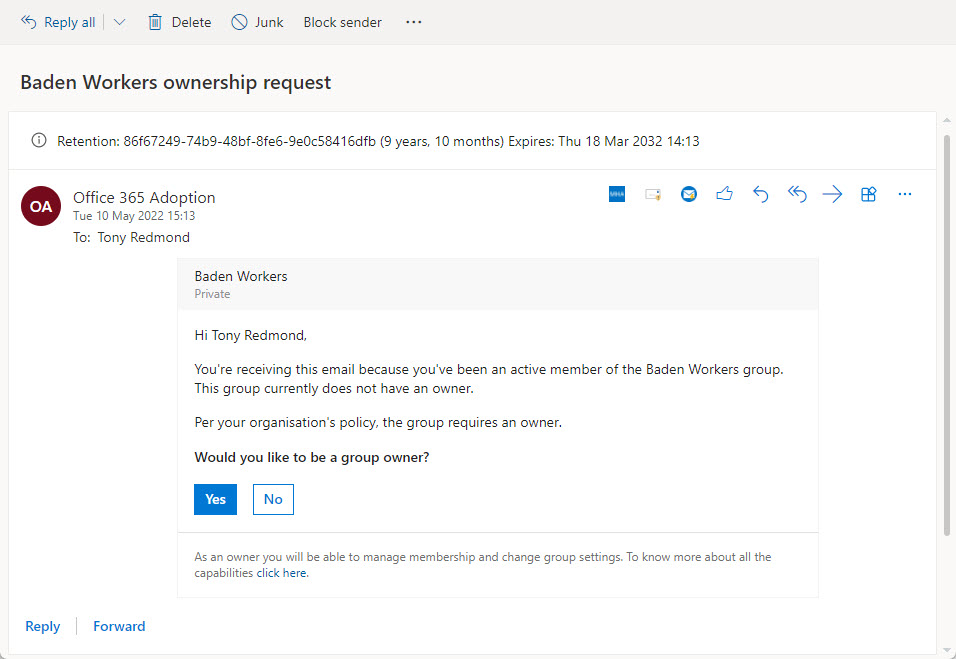
Of course, the hope is that one of the active group members will accept the responsibility and become the owner. Once this happens, the group is no longer ownerless, and the policy stops worrying about it. Until the next time that an administrator deletes the last owner account.
Get the 13 FAQs on Office 365 Groups in this eBook to better manage and secure your environment.
Auditing
Like other Microsoft 365 operations, when users interact with ownerless policy actions, Microsoft 365 captures audit events. And like events generated by other Microsoft 365 operations, some PowerShell code is required to extract and report the details of an event. Here’s a quick script to find and interpret the audit events captured when users receive notifications (which is how you discover who are chosen as active users) and respond to the invitations to take over group ownership:
$StartDate = (Get-Date).AddDays(-90); $EndDate = (Get-Date) #Maximum search range for audit log for E3 users
Write-Host "Searching for audit records for Ownerless Group Operations"
[array]$records = search-unifiedauditlog -StartDate $StartDate -EndDate $EndDate -Formatted -ResultSize 5000 -Operations OwnerlessGroupNotificationResponse, OwnerlessGroupNotified
If (!($Records)) { Write-Host "No audit records found for group ownership processing..." ; break }
$Report = [System.Collections.Generic.List[Object]]::new() # Create output file for report
ForEach ($Rec in $Records) {
$AuditData = $Rec.AuditData | ConvertFrom-Json
Switch ($Rec.Operations) {
"OwnerlessGroupNotificationResponse" {
$Detail = $Auditdata.ExtendedProperties | ? {$_.Name -eq "ResponseType"} | Select -ExpandProperty Value
$Action = "Response: " + $Detail
$ReportLine = [PSCustomObject] @{
TimeStamp = Get-Date($AuditData.CreationTime) -format g
Event = $AuditData.Operation
Group = $AuditData.GroupName
User = $Auditdata.Members.EmailAddress
Response = $Auditdata.ExtendedProperties | ? {$_.Name -eq "ResponseType"} | Select -ExpandProperty Value
OwnerCount = $Auditdata.ExtendedProperties | ? {$_.Name -eq "OwnerCount"} | Select -ExpandProperty Value
Action = $Action
MemberCount = $Auditdata.ExtendedProperties | ? {$_.Name -eq "MemberCount"} | Select -ExpandProperty Value }
}
"OwnerlessGroupNotified" {
$Detail = $Auditdata.ExtendedProperties | ? {$_.Name -eq "FirstNotificationDate"} | Select -ExpandProperty Value
$Action = "First notification: " + $Detail
$ReportLine = [PSCustomObject] @{
TimeStamp = Get-Date($AuditData.CreationTime) -format g
Event = $AuditData.Operation
Group = $AuditData.GroupName
User = $AuditData.Members.EmailAddress -join ", "
OwnerCount = 0
Action = $Action
MemberCount = $Auditdata.ExtendedProperties | ? {$_.Name -eq "MemberCount"} | Select -ExpandProperty Value }
}
}
$Report.Add($ReportLine)
} #End ForEach
$Report | Out-GridView
For example, the output for the audit event captured when I accepted the invitation shown in Figure 4 is:
TimeStamp : 10/05/2022 14:27 Event : OwnerlessGroupNotificationResponse Group : Baden Workers User : Tony.Redmond@office365itpros.org Response : AcceptOwnership OwnerCount : 1 Action : Response: AcceptOwnership MemberCount : 15
Alternatives to the Ownerless Groups Policy
It’s not difficult to find ownerless groups with PowerShell. For example, the script below uses Microsoft Graph PowerShell SDK cmdlets to retrieve the set of Microsoft 365 Groups for a tenant and check each group to ensure that an owner exists. If not, the script flags the problem:
Connect-MgGraph
[array]$M365Groups = Get-MgGroup -Filter "groupTypes/any(c:c eq 'unified')" -All
ForEach ($Group in $M365Groups) {
[Array]$Owners = Get-MgGroupOwner -GroupId $Group.Id
If ($Owners.Count -eq 0) {
Write-Host $Group.Displayname "has no owners"
}
}
Another example uses the Get-UnifiedGroup cmdlet. This works well for smaller tenants but could take a long time in larger environments.
$Groups = (Get-UnifiedGroup -ResultSize Unlimited | Select DisplayName, ManagedBy)
$Groups | ? {$_.ManagedBy.Count -eq 0}
After finding an ownerless group, it would be easy to add code to randomly select a tenant account from the group membership and make them the group owner.
The added value of Microsoft’s ownerless group policy is automatic processing, more nuanced selection of potential owners from active members, auditing, and actionable email communications to ask those selected to take control. You could code up these features, but as Microsoft includes basic operation of the ownerless group policy in Office 365 E3, it’s a no-brainer to put this policy in operation.
Engage with Microsoft 365 experts like Tony Redmond at The Experts Conference 2022 in Atlanta, GA September 20-21. Ask your questions 1:1, get hands-on in our M365 Management Shortcuts Village, and network with peers!





Tony, great info here.
I am testing this process in our dev environment before going live with it. I read from another contributor that the process should send a message within 24 hours of a group becoming ownerless. Your article states the process runs weekly. I made a group ownerless a few days ago by soft-deleting the owner account, but have not yet received a message to any of the test members. I just made a separate group ownerless by hard-deleting a separate owner account and I’m waiting for a result. I am using a Team-backed Microsoft 365 group to send the messages assuming that fulfills the 365 group or user mailbox requirement of the policy config.
Aside from the audit log, are you aware of any other way to see if the process is actually running and failing somewhere? Or should I just be patient and assume it will eventually get to a point where it does its weekly run?
Just wait. You can’t control when the background process runs. It can be bumped because some other service processes take precedence. The goal is to run weekly, but it might take longer.
The email sent is being stripped of formatting and Action buttons. I have seen the FAQ issue and verified what they recommended. Same behavior with different send accounts.
Have you logged a call with Microsoft Support? They can check what’s going on in the tenant… we can’t!
I tried using a shared mailbox for the notifications and found the notifications were never sent. I waited about a week to see if they would send. I don’t know if the documentation was updated after the article but after updating the shared mailbox to a M365 group the emails started to be sent out.
Here MS says that Shared mailboxes are not supported. I was confused too.
https://learn.microsoft.com/en-us/microsoft-365/admin/create-groups/ownerless-groups-teams?view=o365-worldwide#:~:text=Note%20that%20shared%20mailboxes%20are%20not%20supported.%20The%20sender%20must%20be%20either%20a%20user%20mailbox%20or%20a%20group%20mailbox.
Is it possible to change the email to show the First name rather than the display name?
The email is generated by Microsoft. You’d have to ask them. I suspect not.
Is it not possible for Distribution Lists?
No. Maybe this will help: https://office365itpros.com/2018/11/15/finding-inactive-distribution-lists/