Microsoft has published a new resource describing the network ports for clients and services in Exchange Server 2013.
Previous versions of Exchange Server have had this information published, and one of the unfortunate side effects of having that information available was that some customers tried to use it as the basis for placing restrictive firewalls between their Exchange servers, or trying to deploy unsupported scenarios such as placing Client Access servers in a perimeter network.
Perhaps that is one reason that this network ports guidance has been slow in coming out for Exchange Server 2013 as well. Either way, it’s available now and I’m sure it will be very interesting and useful to a lot of Exchange admins.
Be sure to read all the caveats.
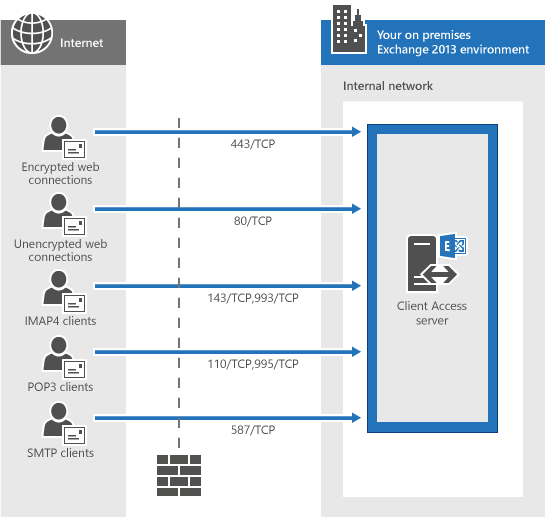
This topic provides information about the network ports that are used by Microsoft Exchange Server 2013 for communication with email clients, Internet mail servers, and other services that are external to your local Exchange organization. Before we get into that, understand the following ground rules:
- We do not support restricting or altering network traffic between internal Exchange servers or between internal Exchange servers and internal Active Directory domain controllers in any and all types of topologies. If you have firewalls or network devices that could potentially restrict or alter this kind of network traffic, you need to configure rules that allow free and unrestricted communication between these servers (rules that allow incoming and outgoing network traffic on any port—including random RPC ports—and any protocol that never alter bits on the wire).
- Edge Transport servers are almost always located in a perimeter network, so it’s expected that you’ll restrict network traffic between the Edge Transport server and the Internet, and between the Edge Transport server and your internal Exchange organization. These network ports are described in this topic.
- It’s expected that you’ll restrict network traffic between external clients and services and your internal Exchange organization. It’s also OK if you decide to restrict network traffic between internal clients and internal Exchange servers. These network ports are described in this topic.



Hi Paul,
I have been trying to run Exchange Admin Centre on Exchange 2013 for 2 days. But, I can’t
I am having connection problem to https://localhost/ecp/?ExchClientVer=15 after certificate renewal.
I have a wild card from AlphaSSL. It looks ther is no problem with the wild card. I have installed on exchange 2013 server as well as IIS servers which we have 2 IIS servers.
Can you be able to make a comment on this issue ?
Thank you.
Hello,
Can I find a Microsoft doc recommand using any-any between DCsDCs, ExchangeExchange and ExchangeDCs.
hi
below the artical
https://learn.microsoft.com/en-us/exchange/plan-and-deploy/deployment-ref/network-ports?view=exchserver-2019
Hey paul how are you doing….I have a network scenario like these DMZ- Edge server->Internal mail server and whenI try to access owa from external corporate network it just displaye’s me IIS home page only and I cound’t get anything related to owa or ecp. everything sending and receving is working inside and outside. My point is how to fix these kind of problems…and do I need to open my firewall rules from server farm->to DMZ or DMZ -> Internet which way I need to use.
Only showing me the IIS default website page When am gonna access it from the external network my domain is like these https://mail.domain.com.et/ when i try these option it shows me IIS home page only. Please any one if there is I can change and tell me.
Paul,
We have exchange 2013 deployed and outlook clients are domain joined (Y) .
Mailbox user objects are created in a resource forest named X .Users actually authenticate using their normal Windows credentials from one of the “Y” child domains.A one-way forest trust between X and Y is set up to enable authentication requests to be processed correctly.Each user account in the ” Y” account forest is populated with both the mail and DisplayName attributes from the resource forest (X) mailbox object that the user is associated with Autodiscover is used for initial configuration of clients which are domain joined and SCP is used instead of DNS .
We have few clients connecting from outside firewall and we have opened related ports and everything works fine ,except for initial confiuration of outlook clients.
Can we know what ports to open (for teh Y DC or X DC) for this autodiscover to work from outside the firewall?
Autodiscover uses HTTPS (TCP 443).
Hi Paul,
We have Exchange in Resource forest and we provide a Mailboxes to users in different trusted domains (partners)
Is there specific guidance for ports between Exchange in Resource forest and DCs in User forest?
Thanx
Sam
This is the only guidance I’m aware of:
https://blogs.technet.microsoft.com/exchange/2013/02/18/exchange-firewalls-and-support-oh-my/
Hi Paul,
I’m moving my CAS server to a different subnet than my DC. What port does the CAS and DC need to communicate so that I can open that in my firewall?
Thanks in advance!
Open all ports. Microsoft doesn’t support firewalling Exchange and DCs from each other.
Thanks champ 🙂
Hey Paul,
Thx for the prompt reply.
You saying use any-any rules from the Subnet containing the Exchange 2010 CAS/HT/MBX to the subnet containing Exchange 2013 CAS/MBX?
Regards
Hendra Tan
Here’s what you need to read:
http://blogs.technet.com/b/exchange/archive/2013/02/18/exchange-firewalls-and-support-oh-my.aspx
Hi Paul,
Our organisation is moving from Exchange 2010 to Exchange 2013.
We are building Exchange 2013 on a new environment, then we are going to migrate the mailboxes from 2010 to 2013. Hence there is going to be a coexistence going on for a while until all of the mailboxes are migrated (we have more than 20,000 mailboxes)
There is a firewall between the two sites.
I have been looking for information about ports I need to have opened to allow everything to function whilst in coexistence. But the information seems to be very hard to find. Do you happen to know?
Thanks 🙂
Hendra Tan
Use an Any-Any rule between the Exchange servers. It is not supported to firewall Exchange servers from each other.