Cutting Off Spammer Opportunities in Onmicrosoft.com Domains
The fight against spam is an ongoing and constant battle that’s not going to finish anytime soon. Spammers constantly search for new techniques to defeat the barriers erected by Microsoft and tenants. A recent development is the amount of spam generated from Microsoft 365 tenants set up by spammers as a platform to send their rubbish to unwilling recipients.
The way things work is that spammers sign up for a new tenant, either a developer tenant (which comes with free licenses), or a normal tenant, and promptly start to send emails. A normal Microsoft 365 tenant is usually the better option for spammers because Microsoft imposes a lower threshold for the volume of outbound messages for developer tenants.
Microsoft recently moved to stop the abuse of developer tenants by insisting that those who sign up for a developer tenant must have a valid Visual Studio subscription. “Valid” means that the person who signs up for the tenant must provide a credit card. It’s not clear if this step is to dissuade spammers as it’s always possible to use a stolen or otherwise compromised credit card for the short period that spammers need to send as many messages as possible before they are detected and stopped.
Fallback Domains
In any case, tenants report that they see a large volume of messages coming from onmicrosoft.com domains. Interestingly, a recent update (in preview) allows tenants to have up to five onmicrosoft.com domains. The original service domain added when creating the tenant counts as one and is the fallback domain, or the default routing domain for the tenant.
To add a new onmicrosoft.com domain, go to the Domains section under Settings in the Microsoft 365 admin center. Select the current fallback domain and then the option to add a new onmicrosoft.com domain (Figure 1).
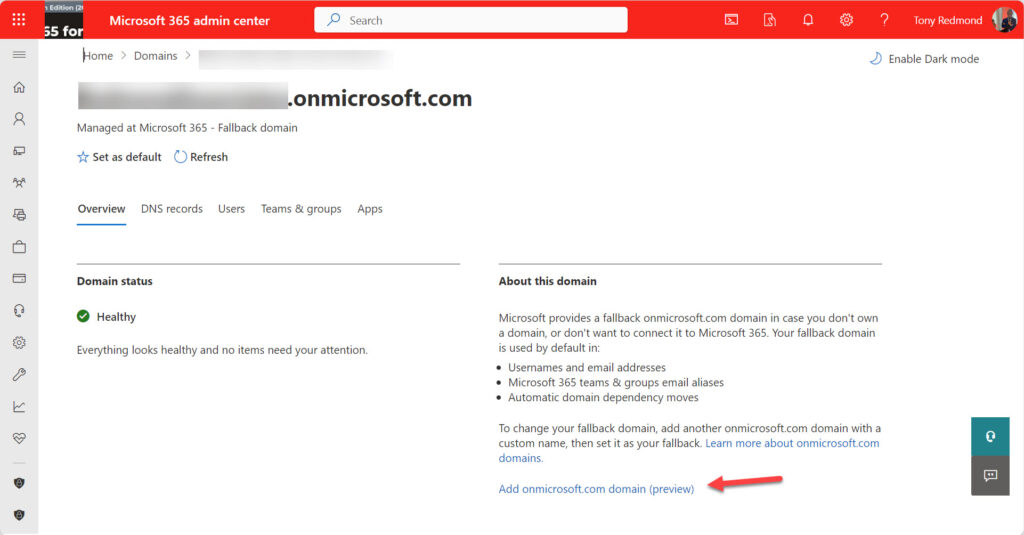
Enter the name of the onmicrosoft.com domain you want. Microsoft 365 checks if the domain is available (not already assigned to another tenant) and if so, adds it to the set owned by the tenant (Figure 2) and sends an email confirmation to all global administrators. Once the tenant has five onmicrosoft.com domains, it is blocked from adding more. Currently, there isn’t a way to remove an onmicrosoft.com domain.

All the onmicrosoft.com domains owned by a tenant can be used for SMTP proxy addresses for mail-enabled objects. For instance, Kim.Akers@ballyconneely.onmicrosoft.com is a routable address that Exchange can use to deliver email to the mailbox that is assigned the address.
Obviously, some customer demand exists to justify support for multiple onmicrosoft.com domains for tenants. Perhaps it’s to support the needs of organizations with multiple operating units. In any case, you can make any of the onmicrosoft.com domains the fallback domain for the tenant by selecting the domain and choosing the Make fallback domain option.
Switching fallback domains has no effect on the SMTP addresses for existing mail-enabled objects. However, the new fallback domain becomes the source for MOERA (Microsoft Online Exchange Routing Address), which means that new mailboxes and Microsoft 365 groups receive a proxy address for the fallback domain. For instance, if you create a Microsoft 365 group called “Insurance Assessors,” the group will have an address like Insurance.Assessors@ballyconneely.onmicrosoft.com in its set of proxy addresses.
Being able to create up to five onmicrosoft.com domains per tenant might give spammers more flexibility in how they send email. Who knows if this is a contributing factor in the perception that more spam circulates from onmicrosoft.com addresses?
Suppressing OnMicrosoft.com Email
Some valid messages come from onmicrosoft.com addresses. For instance, system-generated notifications sent to external addresses come from the Postmaster. By default, the postmaster address defined in the transport configuration is blank and Exchange Online uses an address from the fallback domain. You can update the configuration for a tenant to set any address you like. The address doesn’t have to belong to a mailbox.
Set-TransportConfig -ExternalPostmasterAddress Postmaster@office365itpros.com
Apart from traffic such as system notifications, few “regular” messages that users would want to receive come from onmicrosoft.com addresses. At least, that’s the assertion made by many commentators. I think there’s value in the idea as I cannot think of anyone who sends me email using their fallback address.
If you consider the theory accurate, then it’s reasonable to say that your tenant should not allow any traffic from onmicrosoft.com addresses to flow through into user inboxes. The easiest way to apply such a restriction is to create a mail flow (transport rule) to either block messages or divert them into the quarantine. I’ve been using such a rule for about a month and haven’t noticed any issues.

The rule I use (Figure 3) is simple:
- Look for messages where the from address is from an onmicrosoft.com domain.
- Redirect the messages to the quarantine unless they come from two specified domains (that I use for testing).
Redirecting traffic to the quarantine allows the review of blocked messages to ensure that legitimate traffic isn’t held up. If quarantine policies allow, users can release quarantined messages. MC711335 (30 January 2024) says that an update to quarantine policies will allow users to mark emails from trusted senders so that Exchange Online Protection will no longer block them. This change should help organizations who want to move away from the Outlook junk email filter to tenant-wide spam control. Microsoft expects to complete deployment of the update worldwide by mid-March 2024.
An Array of Mail Flow Rules
I already use mail flow rules to suppress email from top-level domains popular with spammers and automate the process to add new domains to the blocked list with PowerShell. I also have mail flow rules to block administrator accounts from receiving email to lessen the chance that a phishing attempt might arrive in the mailboxes of highly-permissioned accounts. Blocking traffic from onmicrosoft.com domains is just another tweak to my tenant’s email defense.
Adapting Defenses to Accommodate Change
Change happens all the time. Spammers change their techniques. Microsoft updates its software to resist spam and to introduce new facilities for tenants to use. The point is that tenant defenses against spam need to accommodate change too. Stay aware of what’s happening in the real world, what Microsoft is doing, and how others are adapting to new conditions, and then make your mind up about what to do, like adding a new mail flow rule.





I love the idea of applying this kind of limiting to improperly-configured postmaster addresses…..in theory. Unfortunately, in my experience, the overwhelming majority of legitimate M365 tenants are improperly configured and do not use an RFC-compliant “postmaster” address. After testing the rule for the last 30 days, every single detection has been a false positive due to the external party’s improperly-configured legitimate tenant.
So the lesson is that admins need to weigh risk in both directions: do you block attacks as well as legitimate bounce/error email, etc. from tenants who are not knowledgable enough to configure “postmaster” for their domain, or do you allow the legit-but-improperly-configured bounces yet also open your users up to attacks. It feels like a lose-lose situation. I wish that Microsoft would (retroactively) require proper “postmaster” (as well as “abuse”, etc.) configuration when you add a domain — doing so would solve a lot of the problem here.
Armands, I had to make things a bit more complicated over the last few weeks, as there are some other exceptions and Microsoft’s “Bookings” feature manifests itself in different ways. My current Rule is:
Apply this rule if:
Includes these words in the sender’s address: ‘onmicrosoft.com’
and Is received from ‘Outside the organization’
Except if:
‘Content-ID’ header contains ”bookings_reminder’ or ‘bookings_teams”
or Includes these words in the sender’s address: ‘postmaster’ or ‘.onmicrosoft.com’
or sender’s address domain portion belongs to any of these domains: ‘.onmicrosoft.com’
or Includes these words in the message subject or body: ‘onmicrosoft.com/bookings/’ or ‘Microsoft Bookings’
or ‘Content-Type’ header matches the following patterns: ‘text/plain; name=booking.ics’ or ‘method=CANCEL’ or ‘method=REQUEST’
I tried creating this rule, but it isn’t clear to me what options you selected to create the “apply if” and “except if”. I tried the message properties and message header properties, but the options didn’t seem to reflect what you set. Can you offer a pointer? Thanks.
Apply if the address in the message matches the pattern onmicrosoft.com unless it comes from your own domain or any other onmicrosoft.com domains known as good senders.
I started quarantining onmicrosoft.com emails and it’s catching a ton of spam, thanks! But based on the last few weeks of data, I’ve also seen legit emails from the MS Bookings feature getting snagged, since Bookings seems to send messages by default from the sending tenant’s onmicrosoft.com domain. So I added another Rule Exception that allows a “Content-ID” header of “”, which seems to be a common feature of those messages.
Whoops, looks like the Commenting engine filtered out the header value in my previous comment. The value is “bookings_reminder” surrounded by pointy-brackets.
Thanks John!
Hello, John! It`s not working for me, can you please explain bit more? Only Header with anything related to Bookings is ” X-MS-TrafficTypeDiagnostic” containing example value of: “…6105:EE_BookingsEmail|DB1P…”. Creating rule with exception, based on this header is not working for me.