Microsoft has shipped an update for Outlook for iOS and Android that includes support for device PIN policies. The new version number with this feature for both iOS and Android versions is 1.0.4.

Lack of support for PIN policies was one of the major criticisms of Outlook for iOS and Android when it first shipped. Basically the application would successfully connect to Exchange or Office 365 if the mobile device policies required a PIN, even when the device itself had no PIN. In effect it was ignoring the mobile device policies set by the organization. This caused some organizations to decide that blocking the app was the the safest approach.
I tested the new version of the app on both iOS and Android and confirmed that the PIN requirements are now enforced.
On iOS if the mobile device has the PIN removed the Outlook app blocks the user from accessing any of the email accounts in the app until the non-compliant account is deleted from the app.
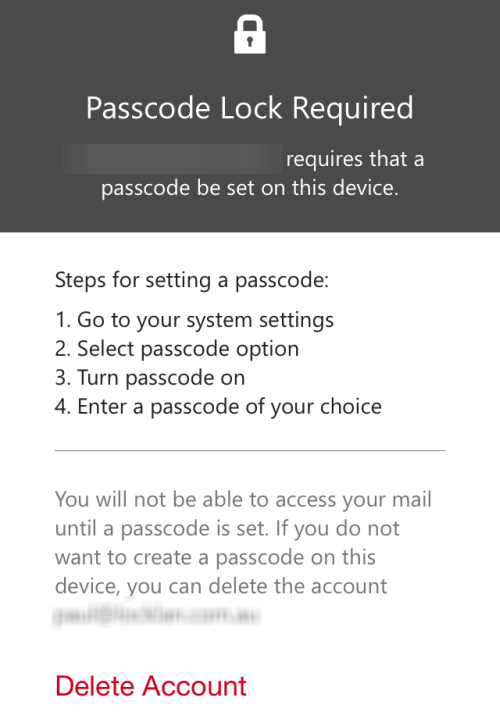
This actually means that the user can’t access any email account in the app, even normal consumer accounts like Outlook.com, as long as the non-compliant account is still configured. A little disruptive to the end user perhaps, but it certainly achieves the desired outcome from a corporate security perspective.
For Android the behaviour is a little different, with the user prevented from removing the PIN code from the device (or at least this is how my Nexus 7 tablet behaved).
Unfortunately this isn’t a clear win for Microsoft or customers. There are some caveats here that you need to be aware of.
When Outlook for iOS and Android connects to your Exchange or Office 365 services it does not connect directly. Instead it connects to some servers that Microsoft operates, and those servers connect to your network to retrieve the user’s emails. This acts as a kind of proxy and allows the application to remain light-weight, be developed and optimized faster, and do intelligent processing of your emails.
However what this also means is that no matter how many devices you are using Outlook for iOS and Android on, you only see one device association for your mailbox.
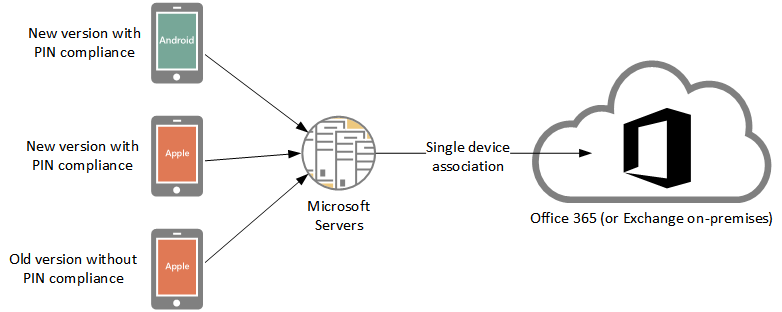
In the example above an Android device and two iOS devices are connected to a mailbox, but the mailbox only shows a single device association.
PS C:\> Get-MobileDevice | where devicetype -eq "Outlook" | select Device* DeviceId : AB5F6EFCDA6E681E DeviceImei : DeviceMobileOperator : DeviceOS : Outlook for iOS and Android 1.0 DeviceOSLanguage : DeviceTelephoneNumber : DeviceType : Outlook DeviceUserAgent : Outlook-iOS-Android/1.0 DeviceModel : Outlook for iOS and Android DeviceAccessState : Allowed DeviceAccessStateReason : Global DeviceAccessControlRule :
There is no distinction between different devices, nor is there any distinction between different versions of the application. I can still connect a non-compliant version of the application to my mailbox and it will work. Only the devices with the new version will enforce the PIN requirement.
This puts organizations who want to allow the new version of the application in a tricky situation, because removing their device access rule will allow the non-compliant versions to connect again. There is a slightly cumbersome middle ground, where a quarantine rule is used until the IT team is able to confirm that the end user is on the newer version of the app before allowing the device to connect. That process wouldn’t scale very well though.
I’m sure Microsoft has plans to resolve this in a future update, perhaps by updating the user agent or some other characteristic of the app to allow the specific versions to be blocked/allowed with device access rules. But at least we’re seeing the rapid development and updates that were promised when the app was first launched.



I have below two queries :
1) Microsoft stores our organization password on their “cloud” servers in order for the app to work correctly. Is that Correct ?
2) The App has a direct link within it to DropBox, Google Drive and OneDrive. A user can take any attachment within an email and upload it to his/her personal account on one of these sites. Is that Correct ?
IF yes, then most of organization would block this app citing security reason
The Real Person!
Author Paul Cunningham acts as a real person and passed all tests against spambots. Anti-Spam by CleanTalk.
1) Credential handling is explained here:
https://www.practical365.com/outlook-for-ios-and-android/
2) Do you already block those services from your corporate network? If so then yes, the mobile app would be a concern.
I don’t know about “most” organizations needing to block the app. A lot of orgs I work with don’t block Dropbox, OneDrive etc, and when I explain the credential storage to them have no particular concerns there. But each organization should make their own assessment and act accordingly.
Thanks for this update, I appreciate it. Looking forward to future posts as new updates are released for this app
Any word if Microsoft are still using servers hosted on AWS, or have they moved these servers onto their own infrastructure (Azure, etc?)
The Real Person!
Author Paul Cunningham acts as a real person and passed all tests against spambots. Anti-Spam by CleanTalk.
Still hosted in AWS, it is on their roadmap to move to Microsoft cloud.