Role Based Access Control (RBAC) enables us to control the level of administrative control granted to IT staff and users in an Exchange organization. Exchange Server 2010 and later versions ship with a number of built-in role groups that we can make use of without having to create our own custom RBAC roles.
For example, Organization Management is a powerful group that grants almost complete administrative control over an Exchange organization, whereas Help Desk is a more limited role that only allows some recipient management tasks to be performed.
Hopefully you’re already making good use of the built-in RBAC roles, or creating your own custom roles, instead of simply granting all of your IT staff Organization Management privileges. Even so, from time to time it is a good idea to review your RBAC role group membership to verify that IT staff have the minimum required access.
I’ve written a simple PowerShell script that will enumerate the membership of the role groups in an Exchange organization and produce a report listing the user accounts that are members of each group, as well as other interesting information such as whether the users are enabled or disabled, and how long ago they changed their password. It can be alarming to discover that an Organization Management role group member hasn’t changed their password in several years.
You can download Get-RBACGroupMemberReport.ps1 from TechNet or Github.
Run the script from a server or workstation that has the Exchange management tools installed. The script also relies on some cmdlets from the Active Directory PowerShell module, so that also needs to be installed on the system.
There are no parameters or switches required, simply run the script from PowerShell.
PS C:\Scripts\RBAC> .\Get-RBACGroupMemberReport.ps1
Some progress information is output to the console as it runs.

A CSV file is produced for each group that contains one or more members, as well as a Summary.csv file.
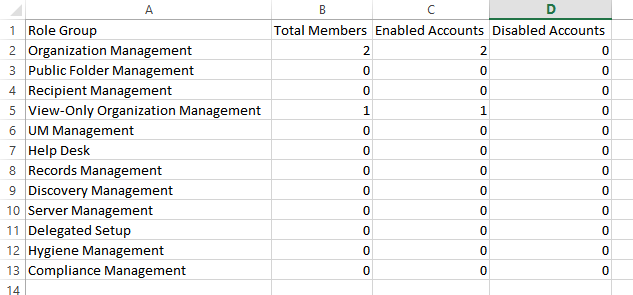
The Summary.csv file will show you the count of members per group, including enabled/disabled user counts.
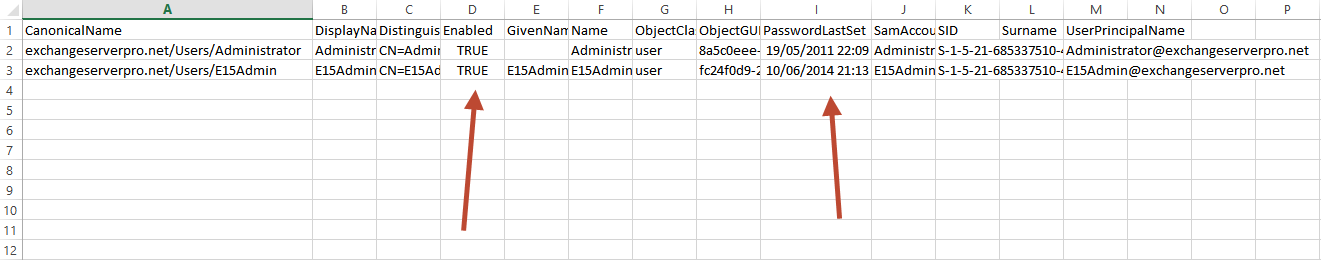
The CSV file for each role group will also show you which users are enabled/disabled, and the age of their passwords.
Use this script to regularly review your RBAC role group membership and keep your Exchange organization secure.
Feedback and questions are welcome in the comments below.



Hello,
Do you have a similar script for Exchange online?
TY in advance!
Diwakar
The Real Person!
Author Tony Redmond acts as a real person and passed all tests against spambots. Anti-Spam by CleanTalk.
Like https://office365itpros.com/2021/05/18/microsoft-365-role-groups/?
Hello,
can the script be executed under an exchange 2016 environnment or does it need some minor changes to work?
Thanks
Hello,
Do you have a similar script for Exchange online?
TY in advance!
MD
I’m getting an error running the script. Windows 10 with Exchange 2010 Management Tools. Script is able to connect to my exchange server and the script displays the AD Forest and the AD DC. Then, the following error appears:
The type initializer for ‘Microsoft.Exchange.Diagnostics.ExTraceConfiguration’ threw an exception.
+CategoryInfo: Operation Stopped: (:String [], PSRemotingTransportException
+FullyQualifiedErrorId: JobFailure
+PSComputerName:
Then, script displays Finished. The script barely stays on screen long enough to get this error screenshot so I can investigate, and all google searches didn’t provide me with an adequate solution.
Is there a way to receive the results as email? I am planning to create a task in task scheduler for this but would be nice to receive the results as email to the admin.
The Real Person!
Author Paul Cunningham acts as a real person and passed all tests against spambots. Anti-Spam by CleanTalk.
Short answer, yes.
Longer answer, you’ll need to look at how to send email using PowerShell. It doesn’t take long to learn, and some of my other scripts have that code in them that you could re-use.
How to detect an azure role was created and the name does not start with ” RABC -” (the dash have a space before and after ) i need power shell script
Stupid question, but where are the csv files produced by this script?
Answered my own question – in the directory where the script was run. I think we should be prompted by the script for the destination location instead of defaulting to the current directory. I am not a script-er at all, so if these comments are out in left field, then let’s just leave them there.
Its start then I get a Powershell has stopped working:
Problem Event Name: PowerShell
NameOfExe: powershell.exe
FileVersionOfSystemManagementAutomation: 6.2.9200.16398
InnermostExceptionType: System.NullReferenceException
OutermostExceptionType: System.TypeInitializationException
DeepestPowerShellFrame: unknown
DeepestFrame: oft.Exchange.Diagnostics.SystemTraceControl.Update
ThreadName: unknown
OS Version: 6.1.7601.2.1.0.16.7
Locale ID: 1033
Read our privacy statement online:
http://go.microsoft.com/fwlink/?linkid=104288&clcid=0x0409
If the online privacy statement is not available, please read our privacy statement offline:
C:Windowssystem32en-USerofflps.txt
I had also made sure to add ‘Import-Module ActiveDirectory’ for the AD PS commands to work.
The script works great, except I am getting a referral error because it is searching against a root domain contoso.com and a child domain sales.contoso.com for get-aduser. Since I’m not a scripting guru, I was wondering if there was a way to edit this for the domain/subdomain scenario?
The Real Person!
Author Paul Cunningham acts as a real person and passed all tests against spambots. Anti-Spam by CleanTalk.
It’s already written to handle multi-domain forests. What error do you see?
Hi Denise
In the line:
$RoleGroupMembers = @(Get-ADGroupMember $RoleGroup.Name -Server $rootDC -Recursive | Get-ADUser -Properties CanoniCalName,DisplayName,SamAccountName,UserPrincipalName,Enabled,PasswordLastSet)
Add: -Server $rootDC”:3268″ in get ADUser
e.g.
$RoleGroupMembers = @(Get-ADGroupMember $RoleGroup.Name -Server $rootDC -Recursive | Get-ADUser -Server $rootDC”:3268″ -Properties CanoniCalName,DisplayName,SamAccountName,UserPrincipalName,Enabled,PasswordLastSet)
Global Catalog (Catalogue) knows all!
🙂
Hi Paul, Nice script. Just something I had to change, I needed to add ‘Import-Module ActiveDirectory’ for the AD PS commands to work. Also, I’ve tested this on an Exchange 2010 server running on Windows 2008 R2. After adding the additional module, everything seems to work fine. Thanks for the script :).