At some point in time after you’ve installed an SSL certificate for Exchange Server 2013 you’ll need to renew that certificate. Hopefully you aren’t scrambling to complete this task because your certificate has expired. Most certificate authorities will email you warnings about impending certificate expiry, but the nature of many corporate procurement processes means those reminders often go to some general purchasing team rather than to the technical folks in IT who really need to know about it.
If you’re curious about your current Exchange certificates and their expiry dates you can always run my Exchange certificate report script.
The process for renewing an SSL certificate involves:
- Generating the renewal CSR
- Submitting the CSR to the certificate authority (and paying them of course)
- Installing the certificate that the certificate authority provides to you
An SSL certificate renewal will usually mean you are submitting the CSR to the same CA that you originally acquired the certificate from. If you’re using a different CA this time around you should just generate a new CSR for a brand new certificate instead. Sometimes we just need to switch to a different CA for some reason such as technical issues or customer service.
Note that generating the renewal CSR doesn’t cause any change or interruption to the existing certificate on your server. Also, you do not need to wait until the certificate has expired or is about to expire before you begin the renewal process. Most CAs will add any days still remaining on the certificate to the new certificate as well. For example, if you still have 30 days remaining on your certificate, and you renew it for 1 year, you’ll have 1 year plus 30 days on the new certificate. So renewing your certificate well in advance of it expiring is a good idea since it ensures that you have time to go through any purchasing or payment processes within your organization that may cause a delay.
Open the Exchange Admin Center and navigate to Servers -> Certificates. Select the server that has the expiring certificate and click the Renew link.
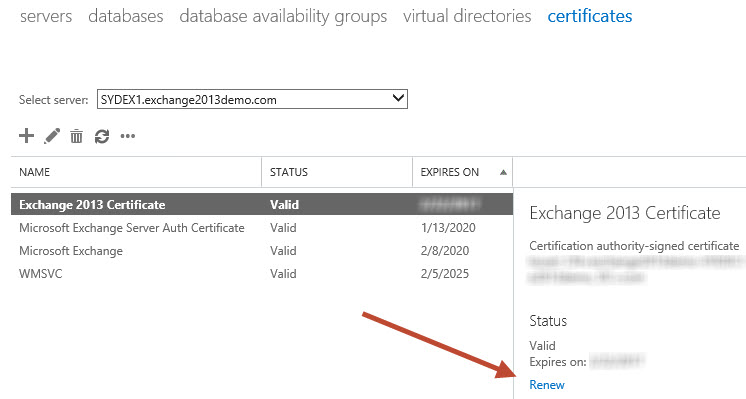
Enter the UNC path to a location that the Exchange servers can write to. Typically this will be a network share that has full control permissions granted to the Exchange Trusted Subsystem group, but you can just as easily use one of the system drives on an Exchange server as I’m doing here.
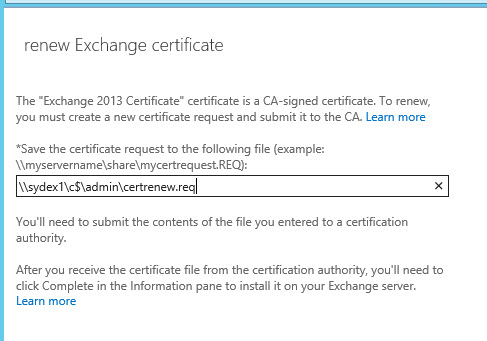
Next, take the CSR info (you can open the .req file in Notepad if you need to copy/paste the contents into a web form) and submit them to your CA (such as Digicert). If you’re unsure of the exact steps check with your CA’s support pages for any instructions. When you’ve downloaded the new certificate place the file somewhere that you’ll be able to access it via UNC path. The same location used to store the certificate request earlier is an easy choice.
In the Exchange Admin Center select the certificate that has the status of “Pending request”, and click the Complete link.
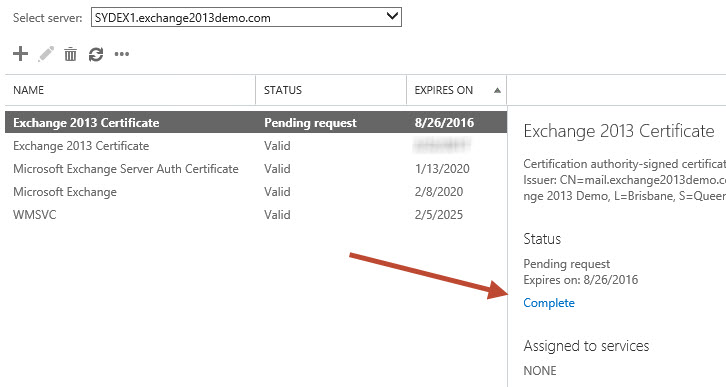
Enter the UNC path to the certificate file and click OK.
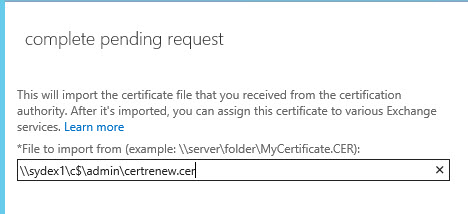
The new certificate will appear in the list. If you’ve got multiple certificates with the same name the renewed one can usually be identified as the one with the expiry date further in the future. The new certiifcate may appear enabled for IMAP and POP, which is fine.
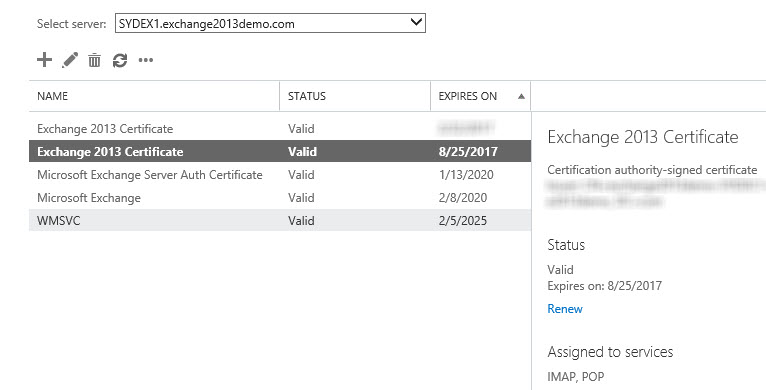
Before you enable the new certificate for IIS or SMTP, if you have multiple Client Access servers that are load-balanced with the server you’re currently working with, and therefore all of those load-balanced CAS need the same SSL certificate, you should first export and import the SSL certificate to the other servers.
After you’ve imported the certificate to all of the other servers you can enable the SSL certificate for the necessary services, such as IIS and SMTP.



Good day,
i have exchange server 2013, and the certificate expired so i renewed by clicking RENEW on EAC
which was successful and i did iisreset as well. many system outlook connected and working fine but some are not connected with the error code 8.
though web access is also working fine .
what can i do to resolve those system outlook 2007 that could not connect (security certificate of the proxy server)?
Just wanted to share some experiences we got after following this guide. There is an additional step that we had to go through after renewing the certificate and that is assigning the new certificate to the site “Exchange Back End” in IIS. Select bindings on the “Exchange Back End” site and select https (port 444) – here you have to select your new certificate. After you’re done, do an “iisreset”. Please note that this will interrupt the service for your end users, so pick a time accordingly to your SLA.
Before we made this change we had issues with users complaining about spontaneous logouts from OWA and we were unable to login to ECP (login loop).
According to some other guides on this topic, this is related to the renewal being done in the ECP.
Hi Paul,
I’ve tried to renew my cert using the procedure, but have run into a strange problem. When I click on the pending request and type in the unc path to my new certificate, I get the following error:
“The imported certificate file for server XXXXXXXX failed to access for the following reason: Access to the path ‘\\server\share\xxxxxx.crt’ is denied.”
The share is valid, and I can even type the UNC path into the RUN from my Exchange server command and it brings up the folder contents OK.
Am at a loss on this.
Thanks,
Tony
Tony, have you verified the permissions for the UNC path?
Create a SHARE with EVERYONE Read and Write
Leave default NTFS Permission
After completing the tasks delete the SHARE or move the files
Hi
I have just renewed my Exchange2013 mail certificate even though it has still 31 days remaining. I ran a powershell script to find out if the new cert has been installed with the added days and it has. Great. Now i have two mail ssl certs (one about to expire in 31 days and other to expire in 397 days). I ran “Get-ExchangeCertificate | select thumbprint,services,notafter,subject,certificatedomains | where {$_.Services -match “SMTP”} | fl ” and i see that the old cert has services bound to them. I followed your other article to remove these services “Enable-ExchangeCertificate -Services None -Thumbprint xxx” and it does not seem to remove it.
also to note, both certs have the same services enabled, i am running Version 15.0 (Build 1395.4)
Can you assist please?
Thank you
Mabsy, you have to remove the old certificate manually with the command “Remove-ExchangeCertificate -Thumbprint xxx”. Paul got a guide for that as well: https://www.practical365.com/exchange-server/remove-ssl-certificate-exchange-server-2013/
Hello Paul,
I am having a challenge renewing a self-signed SSL certificate for my exchange 2013 Deployment. I have tried several times and I don’t seem to make any headway. Briefly:
– My Certificate expires on the 15th of April 2019.
– I have gone through the process of requesting and renewing the self-signed certificate
However, After I click on the Complete hyperlink and point to the location of the new certificate, I observe that new SSL certificate still shows that it will expire on 15 April 2019.
I have gone through the renewal process more than 5 Times buts till get the same expiry date insted of some date next year. Please help
Hi Paul,
I currently have Symantec certs on my exchange 2013 servers. Digicert issued me a new cert without creating a CSR, can I still go through these steps to replace them even though I did not create a CSR?
Hi Paul,
Using as schema what reported in your procedures I performed the renew of an Exchange certificate who were near to expiration.
After have performed this activity our Exchange 2013 environment have stopped allowing access to Outlook Web Access and Exchange Admin Center Web pages.
Apart what mentioned before nothing else was changed on everything is composing our Exchange environment or that is placed on the perimeter of it.
The login page is show and after the user have entered credentials the system display the inbox screen just for few seconds and after that go back to the login screen.
All Outlook clients have instead continued working fine and this also email client are using the same way in order reach the Exchange infrastructure.
Our Exchange environment is based on 24 servers that are decoupled from clients via an F5 load balancer.
All the Exchange servers are hosting both CAS and MAILBOX role.
At least apparently seems like sessions between servers are not managed well.
The only workaround have solved at least temporarily the issue and has given us a little bit more time in order investigate more deeply was set on F5 the kept of session affinity.
What could be occurred?
Thanks in advance ad regards,
Denis.
If you have load-balanced servers, they all need to have the exact same certificate for HTTPS. So if you’ve renewed or replaced the certificate on one server, that certificate must be exported and imported to all of the other servers as well.
I done also this but nothing is changed.
Thanks for this, it worked exactly as you described but I’m left with one question now I’ve enabled the services for my new certificate – the old one is still there. Can/should I remove it? It seems to me it should be irrelevant since it’s been replaced by the renewal.
You can remove the old/expiring certificate.
Hi,
I have now listed the invalid and valid certificat, how gonna the new certificate overcome the old one, my outlook still use the old one, thanks.
Hi Paul
i have multiple exchange serves. i assigned the iis and smtp services before exporting the cert to the other servers. how do i now get the sert on the other servers?
See the links at the end of the blog post.
we have exchange 2010 certification to be renewed and we have hybrid deployment in place. whether we need to rerun hybrid configuration after we renewed the certificate
If you are to renew the certificate while keeping the same name, you would not have an issue with Mail flow with Office 365. As an extra measure of security, you can take a log of all your connectors’ settings, on-prem and in the cloud, so you would have a reference point in case anything goes wrong (it shouldn’t). Also, you can always run Hybrid Configuration Wizard for any issues in the connectors, as it usually recreates the connectors and starts a new hybrid setup. But please only do this if you mail is not flowing from Exchange to Office 365 or vice versa.
Hello Paul,
We have just renewed our certificate but phone clients are showing an unvalidated certificate error. It seems these clients are being presented with the expired certificate and not the renewed one. The old one has been removed so I’m not sure where the clients would be getting this from.
Any load balancers or reverse proxies involved?
Also have you run the tests at ExRCA.com?
We use TMG
ExRCa test for activesync gives error A certificate chain couldn’t be constructed for the certificate…..chain status =NotTime Valid
Did you update the cert on the TMG?
Hi Paul
I am wondering with all exchange certificates if ever my certificate renewal fails will the mail flow for my environment fail? Assuming that my certificate is already expired?
Yes and no, depending on the type of mail flow. Obviously it’s best to avoid expiring certificates in the first place.
hi Paul, thanks for your nice article. It makes the thing easy for me doing it.
We have two Exchange 2013 servers in a fail-over cluster and DAG. Both servers are mailbox and CAS. The servers use different certificates for the 4 services (IMAP, POP, IIS, SMTP). Server1 is the primary.
Now both servers, this certificate is going to expire soon. I have done renewal of certificate for Server2, got the new certificate but having the same name which is fine, I can identify the new cert by expiry date. The issue is that, only IMAP and POP is showing in new cert->services. Old one still have all 4. Should I just select other two services in the new certificate, and will that take it off from the old one? What if both old and new ones have all 4 services – can I then delete the old certificate? I cant un-select any of 4 services from old cert, the boxes are greyed out.
and should I do the same thing on my primary server Server1 (renewal of certificate and moving the services and delete old one later)?
Much appreciate your advice.
Hi Paul,
I am about to renew my existing certificate this week but I am getting confused if the same certificate needs to be pushed at the client side as well..
Need your guidance on this.
Regards, Kapil K
No, not necessary unless you’re provisioning the certificate from a CA that your clients don’t already trust, in which case you would need to distribute the root CA cert to the clients. But for certificate renewals that isn’t likely to be an issue.
Hi Paul,
I have the CA template validity period of 2 years, but when i renew the request is 1 year.
Do you know how i can get a certificate valid for 2 years?
Thank you
Been a while since I looked at it but I believe all the requests are for 1 year and it’s the CA that controls the actual duration when it issues the cert.
I think the problem is the validity period of the certreq of the exchange because my CA template is set to 2 years. I haven’t found a powershell command with parameter to change it.
Thanks
What problem?
There’s no parameter of New-ExchangeCertificate for setting a duration on the request. Like I said, from memory it’s controlled by the CA when it issues the cert, not by the Exchange server when it generates the request.
Hi Paul,
Hi Paul,
Very informative, clear and useful article. However, we have different scenario. Currently, we are running Exchange 2013 CU15 on-prem. Hardware Load Balancing layer-7 (with SSL offload on LB) is in place for all Exchange services. Previously, we have requested and issued 3rd party certificate from GlobalSign (because of migration from O365). At the moment, there is no added value to renew certificate issued by GlobalSign due to costs and we would like issue certificate using internal MS PKI.
How things are different in comparison to renewal process? It is clear that service disruption is expected since we need to replace them on Exchange side in conjunction with LB. What recommended steps would be in consideration this particular case?
Thank you in advance.
Why do you say there is no longer a need for a third party certificate?
We are fully on-prem and there are no plans to go on O365 in short or long term.
That’s still not a good reason to stop using third party certificates.
I agree with you since it will have probably wider impact for activesync users no matter that we use on-prem MDM solution. In addition to that, will also have wider impact on Mac workstations because they do not have internal CAs. Both are business critical services.
Quick question – will it have the same impact from connection side if we make a final decission to use 3rd party certificate further? We still need to renew certificate on LB side (due to SSL offload) and each CAS servers because we do HTTPS probing from LB to Exchange servers.
Renewing the certs is not a big deal. Start the renewal process. When your provider issues you the new cert just plan a maintenance window to complete the renewal, export/import to the other servers, and import to your load balancer as well.
Paul – Can I complete the certificate request, but wait for an interval to actually assign services to it? i.e. – will completing the CSR cause any brain-pain to Exchange, or will it just continue to use the old soon-to-expire certificate until I assign services to the completed CSR? Don’t you love these silly probing questions? Thanks for your answers, it’s great to have your skills at our disposal for those of us who don’t do this but every 3 years.
Until you assign the new cert nothing should change. I am doing mine via Digicert right now so that’s the basis for my info. If in doubt, schedule the work for out of business hours in case something goes different for you.
Since nobody has asked this, I thought I would. After completing the certificate request, then assigning services to it (SMTP, IIS, etc.), do any services need to be restarted? Does the Exchange server require a reboot?
Also, you have a typo here:
“The new certiifcate may appear enabled for IMAP and POP, which is fine.”
No reboot required.
Do i need to restart IIS service post Certificate upgrade?
Paul I was able to renew the cert correctly, and delete the incorrect one I created. However I now still have a cert that says Status Dave Invalid, and when I launch EAC it tells me my cert is expired. Is there harm in just deleting the invalid date cert?
You can remove a cert if its invalid, expired, or not being used.
hello, i have followed steps but now not receiving external emails
please can you help
Start by going to https://testconnectivity.microsoft.com/ and running the inbound SMTP test.
Hi Paul, I attempted this process, but it still shows my old cert, and has a new one listed with a valid date.
I can’t remove the old one, it says that it’s tied to the federation, and im stuck in a pending request state. Any suggestions?
If you do a Google/Bing search for replacing a federation certificate you’ll find instructions on how to deal with that.
Hi Paul,
We plan to use a wild card certificate which will be used in Exchange hybrid and ADFS servers so can the CSR be generated from IIS in ADFS or EAC in Exchange server?
I prefer to generate them from Exchange, export with private key, and then import anywhere else I need it.
Thanks … that is what I did this past weekend. Good info to know for future renewals.
One other thing about this. I did the usual (“Renew” to get REG file, … Submit the REQ file to the CA … got the CER file from the CA … placed it on a UNC path and “Completed” it. Exported it to the other CAS’s and assigned the IIS and SMTP services on all the CAS’s.
Now, as I did the first one via EMC, I noticed that the “expiring” cert had disappeared. I checked the rest of the servers and it was gone on each of them as well. I noticed that when I assigned the IIS and SMTP services to each, it prompted me asking me if I wanted to replace the old expiring cert ! What ! Have you seen this before ?
Sounds like the question of whether to replace the existing *default* SMTP certificate, which is usually a “Yes” answer if the previous default was the expiring certificate.
You mention …
“Before you enable the new certificate for IIS or SMTP, if you have multiple Client Access servers that are load-balanced with the server you’re currently working with, and therefore all of those load-balanced CAS need the same SSL certificate, you should first export and import the SSL certificate to the other servers.
After you’ve imported the certificate to all of the other servers you can enable the SSL certificate for the necessary services, such as IIS and SMTP.”
… so, based on this, should I really do the cert work after hours ?
All changes carry a risk of disrupting service for end users, and one way to mitigate that risk is to perform the change outside of business hours.
Hello,
I have an Exchange 2013 Server and I have a certificate that will expire on 01/04/2017. The certificate is called “Exchange all services”. I am not sure how I should renew this certificate.
It is not a bought certificate. I think it was created with my CA server(I am not sure of this information since when I joined the company the certificate was already there).
Should I just Renew it using the ECP and then go on my CA server. All Tasks > Submit new request…? I just want to be sure I am not doing anything wrong. I have a second certificate which has no name with service SMTP only.
If you aren’t sure where the cert came from then you can check the properties of the certificate to find out.
If it came from an internal CA I recommend you replace it with one from a public CA like Digicert.
I checked the certificate is indeed from my interal CA.
I know it is better to use a public CA but that certificate is only for internal domain .local.
In order to renew this internal CA. I just need to create a new request on my internal CA?
The process is the same as I demonstrated in the article. The difference is where you submit the CSR.
Will this process(using the EAC) work for upgrading the certificate to a SHA 2 cert? Thanks.
You should check with your certificate provider how they can reissue a certificate as SHA2. They might just need you to do a renewal with a new CSR, or they might have a different process.
Do you remove/delete the old certificate once the renewed one is in place and activated on the services, or leave it be?
I have activated the services on the new certificate now, but it seems to still be using the old one which have a few days left before expiration. Will it automatically present the new certificate once the old certificate is expired?
Hi,
Thanks for this article, I have follwed it through and renewed the SSL cert on our server. I still have my old cert listed. Is it safe to delete now? It still shows as having services against it and is still in date. It doesn’t let me deselect the services although I did transfer them to the new cert.
thanks
Hi Paul,
I saw this below information in this website, However i am not sure whether its true (LINK REMOVED)
“If you need to renew an Exchange 2010 / 2013 certificate, do not use the “Renew” function of your Exchange 2010 / 2013 EMC. Indeed, it will generate CSR in binary format that is not compatible with X509 standard used by most suppliers. ”
Thank you
Shivappa Hosamani
Nope. That information is so bad and wrong that I’ve removed the link from your comment. In fact, I’d say their information is intentionally designed to try and fool people into renewing certificates with them instead of another provider, which is a pretty shady tactic if you ask me.
ahh ok, I really appreciate your help and quick response, I thought it might cause if i use “renew” function..
Now i will proceed to renew certificate by using “renew” function..
Thank You
Hi, I could see some information in other article saying that. If we use renew function for certificate renewal, it will not provide the correct info and generated info will be in binary format, is that true ? We have ex13 servers with CU6 on our envernment.
What other article?
Hello,
I was wondering if there is an alternative method to this that doesn’t involve the CSR request? When I originally installed our certificate for Exchange 2013, I did it by obtaining a PKCS#12 cert from the CA, importing the certificate using a Powershell command and then deploying it to the relevant exchange services.
Could this approach be taken again, i.e. renew the cert at the CA, import the renewed certificate using Powershell and then reassign services to the new certificate?
I’d really appreciate your thoughts on this on as our certificate is due for renewal and I’m not sure on the best approach.
Thank you in advance.
I always do it the way it’s demonstrated in this article. I don’t really see the point in trying to do it a different way. Good luck!
Hi Paul,
Many thanks for your quick response.
The question was raised given the way we set things up initiall, this is the first renewal on our Exch2013 box so just wanted to query it.
We’ll be following the article for sure…
Thank you
Hi Mr. Paul Cunningham,
Currently our certificate will expire soon and it is used in most of the exchange services like IIS, SMTP, IMAP, OPO, and my question is, if that certificate will be renewed and still on pending process, will my exchange work well without any email sending/receiving issues??
Note: Certificate will be expired a week after and still valid
thank you for your kind response
In the article: “Note that generating the renewal CSR doesn’t cause any change or interruption to the existing certificate on your server. ”
So no, there’ll be no impact.
Thank you, I really appreciate it, I thought it will cause mail flow failure if its on pending status
Godaddy Auto renew SSL without me generating a request Please how can i make ue of this ssl since there is no renewal CSR.
I received a similar error completing these steps on Exchange 2010.
An error occurred: [CODE: -2022] [MESSAGE: CSR country code invalid.]
Cannot parse CSR. It may be invalid.
My ISP admin said that it appears to not have any locality information…?
Open the certificate store on the server and have a look at the certificate itself. Does it look like it has the locality information correctly stored?
Renewals cant be done through exchange in IIS as it doesnt let you choose a country code apparently in older IIS. Just have to do a new cert from scratch.
When using renew button as described in this guide, SSL provider returned an error: (121) -2022 CSR CSR country code invalid and after submit CSR content to support to investigate , they said if CSR file didn’t contain the following information Country,City/locality, Organization, State/province.
Any specific step required or should I just generate a new CSR manually?
Let’s say for example your certificate has 30 days left before it expires. If you renew the same certificate for 1 year, you’ll get 1 year + 30 days when the new certificate is issued.
If you create a new CSR for a new certificate, you’ll get just 1 year, and you’ll lose those remaining 30 days, because it is not the same certificate.
I’ve never encountered that particular problem. Which build of Exchange are you running right now? How old is the server (what build was originally installed when the server was set up?) and how old is the current SSL certificate?
Sorry for the delay, we still running Exchange Server 2013 CU 9. It’s around a year ago and initially deployed using Exchange 2013 with SP 1. The SSL Cert will be expired on 14 Feb 2016.
Open the certificate store on the server and have a look at the certificate itself. Does it look like it has the locality information correctly stored?
It’s possible there was a bug in the version of Exchange when you first deployed and provisioned the certificate. If it was a year ago you should have been installing with at least CU7, not SP1 (which is CU4).
Paul,
Thanks for this. I had to remove an old FQDN of an exchange 2007 server from my Digicert cert. I used the Digicert utility to create the CSR, which I used to request the new cert. I received the new cert and when I tried to import it in the EAC, I received an error message stating “error importing certificate. a certificate with the same thumbprint already exists.’
But it appears to have imported the replacement cert and I was able to activate it.