In my previous article, I explained how to use Defender for Cloud Apps to prevent information leakage for Microsoft 365 and Third-Party apps. This time, I would like to go deeper into some policies that can enhance the security and compliance of the apps protected by Defender for Cloud Apps.
Defender for Cloud Apps includes several different policies to address different scenarios. Details can be found in Microsoft’s documentation. In this article, we focus on how to apply the Defender for Cloud Apps’ Session and File policies in some common situations.
Prevent Upload/Download Malicious Files
Defender for Cloud Apps is essentially a reverse proxy sitting in front of your cloud apps. There is no perfect place to check if files that users want to upload or download contain malicious content, but Defender for Cloud Apps can do the job. You can configure a session policy to have all files scanned using the built-in Threat detection engine before the file reaches the underlying cloud apps. The same applies for downloading files from cloud apps.
A Defender for Cloud Apps session policy controls what to do when traffic passes through its “reverse proxy.” Many actions are supported, such as scanning for malicious files during user uploads, and downloads, or stopping a user from performing some type of activity, such as:
- Perform DLP check against the text copy and paste from and/to the file stored on SharePoint Online or OneDrive and then prevent users from doing the copy and paste. For example, you can block users from copy and paste passport numbers from/to the document.
- When users are outside of the corporate network, you can also prevent them from downloading the files. This is a very common usage scenario for Defender for Cloud Apps in almost all my clients
To implement blocking upload malware to Microsoft 365 or any SaaS apps protected by Defender for Cloud Apps, we create a session policy like the policy shown in Figure 1. To make our life easier, Microsoft includes a number of templates in Defender for Cloud Apps, so we just need to modify the template to suit our scenario. Let’s use the Block Upload of Potential Malware template as a starting point.
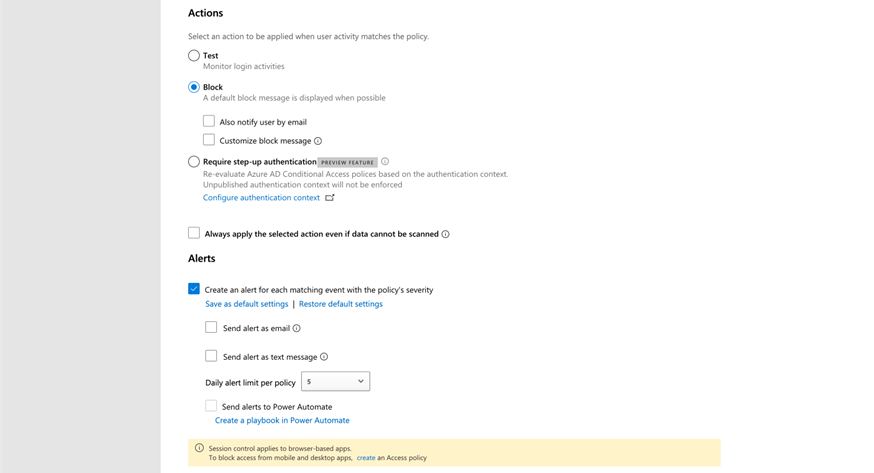
In the session policy, we specify the kind of apps to scan and the actions to take. In the policy shown in Figure 1, I decided only to scan and block any malicious files detected. You must enroll the cloud apps to Defender for Cloud Apps before you can use the session policy. Enrolling means that all the traffic going in and out will be inspected and processed by Defender for Cloud Apps to allow the session policy to work.
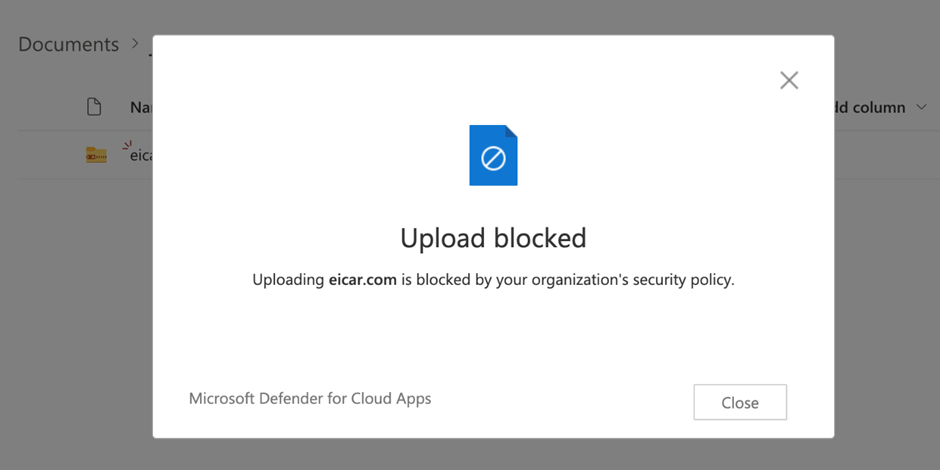
Figure 2 shows what a user sees if they attempt to upload a file with malware to SharePoint Online.
Cybersecurity Risk Management for Active Directory
Discover how to prevent and recover from AD attacks through these Cybersecurity Risk Management Solutions.
Content policy to Block Copy and Paste and Restrict Browser Access
Another very common request from my clients when we conduct a Microsoft 365 implementation project is to allow users to access the corporate data even when outside of the corporate network, but only through Office Web Apps. Furthermore, some of my clients request to block the copy-and-paste capability when users edit files outside the corporate network or use a device that is not issued by the company.
Again, we leverage the Block Upload of Potential Malware (based on Microsoft Threat Intelligence) template provided by Microsoft to create the solution. Figure 3 shows an example policy that detects if the content user copied includes sensitive information (like a credit card number) and then prevents them from copying and pasting to the clipboard via supported applications (i.e. browsers). The detection can be based on Microsoft 365’s sensitive information type, EDM, or Defender for Cloud Apps’ own content type.
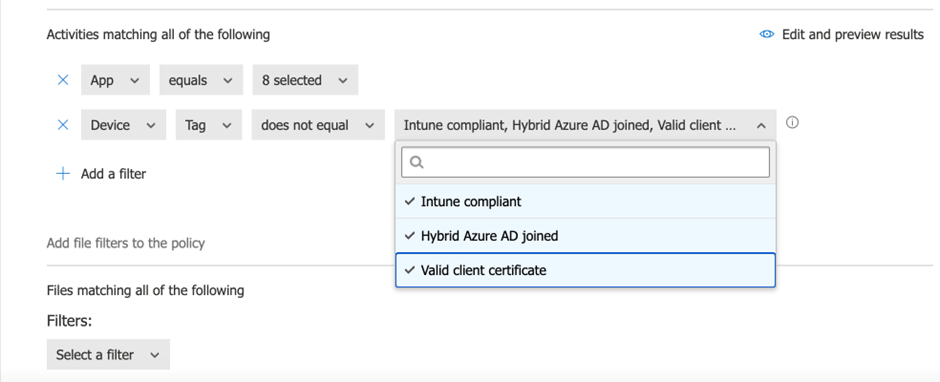
The key here is how to differentiate between corporate and non-corporate devices. One way to do that is via Intune integration. You can see that the activity matching conditions include one condition to exclude any devices that are Intune compliant (it’s probable that only corporate-approved devices will have this status) or via a digital certificate issued during the enrolment process. Personally, I always go with the Intune-compliant flag condition as it is easier to implement.
Now that we’ve got the policy to block copy and paste, let’s try it in action. I inserted some “fake credit card” numbers that match the conditions defined in the Sensitive Information type into a document and tried to copy and paste it. Figure 4 shows the resulting error.
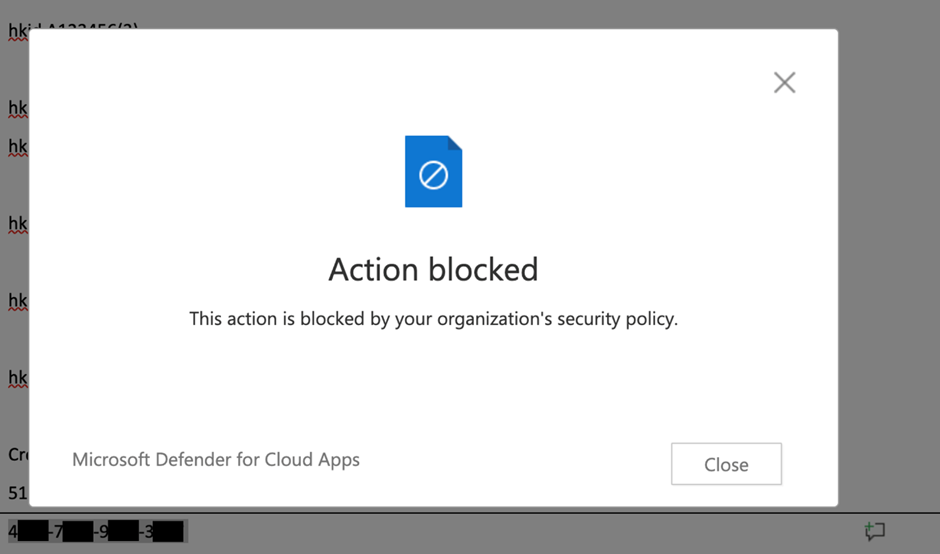
To prevent file downloads, we need another policy that looks like the one shown in Figure 5, which is based on the Block download seen in the real-time content inspection policy template.
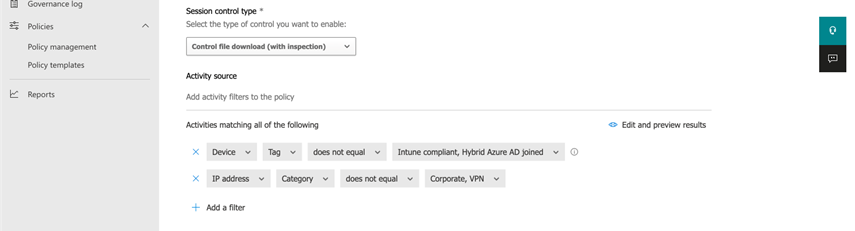
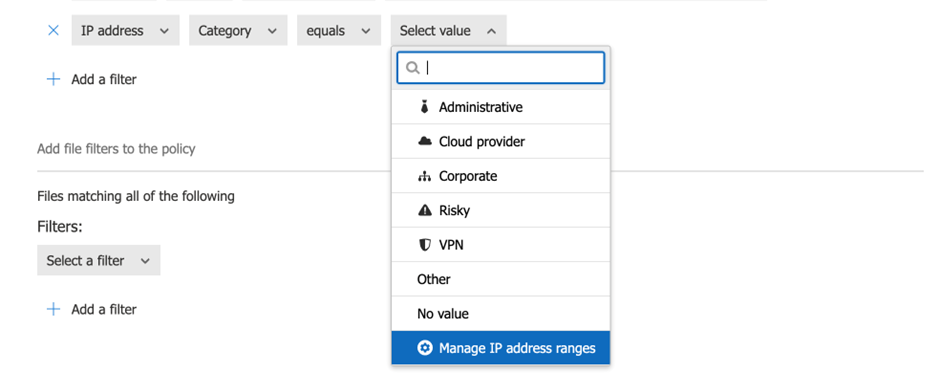
Note that in this policy, we added a condition that states that we only want to prevent downloads when a user is outside the corporate network. Remember to add the IP ranges belonging to the corporate network into Defender for Cloud Apps so the session can be classified as coming from the Corporate network. Unfortunately, IP ranges are not shared between Intune and Defender for Cloud Apps. To add IP ranges to the Defender for Cloud Apps’ network list, you can use the Manage IP address ranges link when defining the policy (figure 6).
Automatically Remove Orphaned Shared Files
Another very useful policy is the ability to detect any shared files (or links) in SharePoint or OneDrive. Users often share files and subsequently forget that the files are shared, which creates a potential risk for information leakage. Defender for Cloud Apps includes a policy called File policy to scan all files in the supported cloud apps (like SharePoint and OneDrive) and look for file matching conditions.
For example, to detect files shared for over 90 days and stop the sharing, we can create a file policy like that shown in Figure 7.
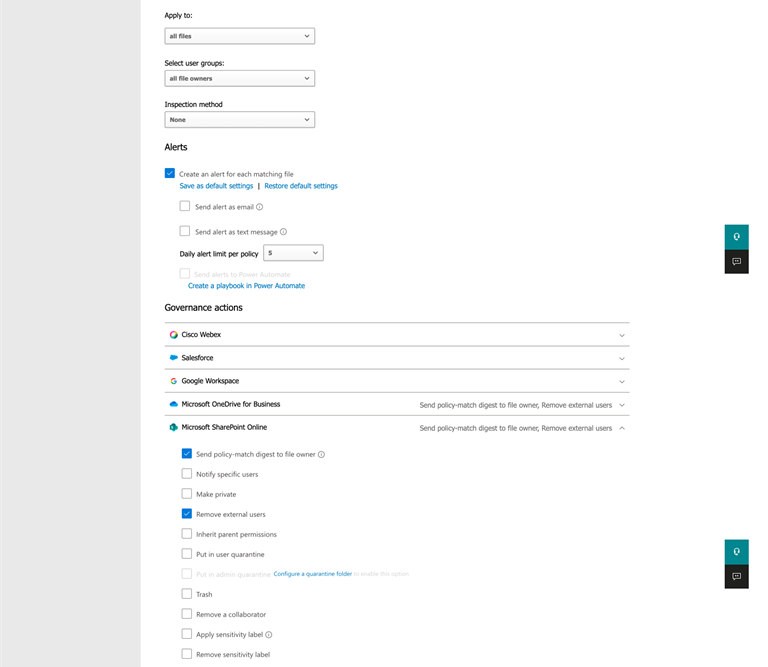
The available actions depend on the cloud apps. In the case of SharePoint and OneDrive, Defender for Cloud Apps can send a digest of what it found (files shared over 90 days) and remove the shared link. You can also do other things like making the file quarantine (i.e. hide the files from users and require an admin to check and release the file). My clients often find this capability useful to help manage sharing in SharePoint and OneDrive.
Make the Most out of Defender for Cloud Apps
Many organizations consider Defender for Cloud Apps as a monitoring or simple Cloud App Session Broker (CASB) to block access. But Defender for Cloud Apps contains other hidden gems that you can take advantage of, like the policy capabilities mentioned in this article. Furthermore, the functions mentioned in this article also support other third-party apps, like salesforce.com or slack, that support the same level of reviewing to prevent potential information leakage between different apps. One example of such information leakage would be copying and pasting personal information from Microsoft 365 to Slack and sharing it.
Cybersecurity Risk Management for Active Directory
Discover how to prevent and recover from AD attacks through these Cybersecurity Risk Management Solutions.