Dynamic Membership Depends on a Well-Maintained Directory
Updated 14-Sep-2023 (the administrative unit cmdlets are in the beta module of the Microsoft Graph PowerShell SDK V2).
Many of you commented positively about my coverage of the importance of having a standard process to create new Azure AD user accounts. The high-level message in the article is that organizations should pay attention to populating account properties because of the many ways that Microsoft 365 apps use these properties. In this article, I want to cover a preview feature called Dynamic Administrative Units.
You’re probably familiar with regular administrative units, containers that can hold user accounts, groups, and devices. Control over administrative units can be delegated to specific accounts or groups to support scenarios like country-level management of user accounts. In other words, if the User Administrator role for an administrative unit is assigned to a group, the members of the group can perform actions authorized by the role (like updating account properties) for any account in the administrative unit.
The Downside of Administrative Units
Administrative units are useful, but they have a downside. That is, the need for manual intervention to populate the members of the administrative unit and to maintain the membership thereafter. It’s perfectly feasible to make sure that administrative units have accurate memberships, perhaps with some PowerShell scripts in the mix, but it’s not interesting work.
Microsoft believes that they have a solution in dynamic administrative units, launched in preview in April 2022. Dynamic administrative units work just like dynamic Azure AD groups by using rules to calculate membership. The point is that if you go the extra mile to make sure that account properties are accurate, membership rules will find the right accounts or devices for a dynamic administrative unit. In the remainder of this article, we focus on using dynamic administrative units for accounts.
The cmdlets to work with administrative units are currently accessed through the beta endpoint. If you connect to V1.0 instead of beta, you won’t see the cmdlets described here.
Creating a Dynamic Administrative Unit
The approach taken to using dynamic administrative units is like dynamic groups. You need to know the appropriate properties to use for the membership rules. Typical choices include:
- Country
- Department
- Office
It’s important to know which account properties provide the foundation for a dynamic administrative unit. If these properties are absent or inaccurate, the membership rules won’t work. After deciding what properties to use, it’s a good idea to audit the properties. For instance, let’s assume that you plan to use the Department property to create a dynamic administrative unit for members of the IT Department. Running this PowerShell code will find the accounts:
Get-MgUser -Filter "department eq 'IT'" | Format-Table DisplayName, UserPrincipalName -All
If you see the set of accounts you expect, you know that everything works. On the other hand, if some expected accounts aren’t present, it’s an indication that either some accounts need to have their properties updated or the query should be broadened to find those accounts.
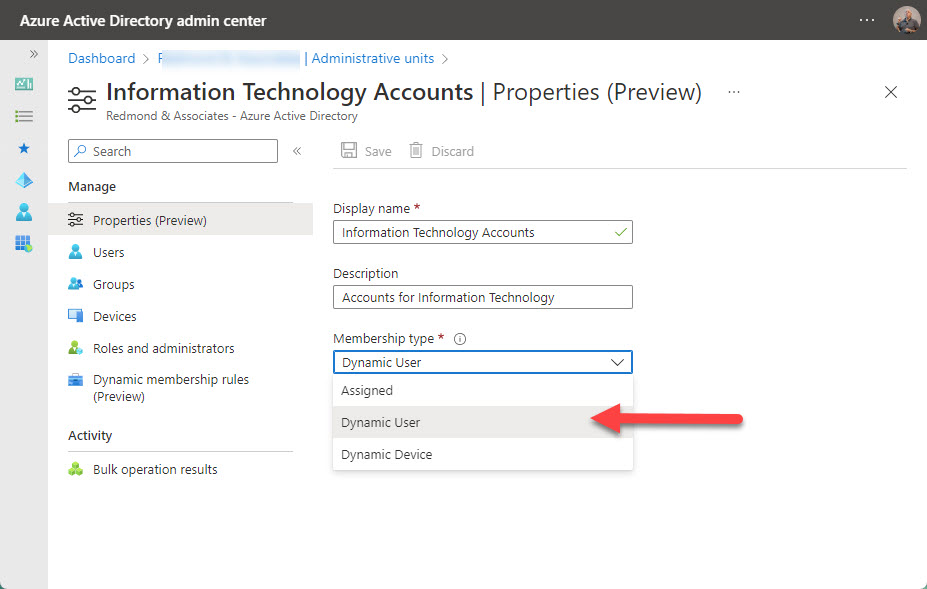
To start, select Administrative Units from the Azure AD admin center menu and create a new unit. All administrative units start off as basic containers. When the new unit is available, open its properties and switch its membership type from Assigned (the default) to Dynamic User (Figure 1).
Cybersecurity Risk Management for Active Directory
Discover how to prevent and recover from AD attacks through these Cybersecurity Risk Management Solutions.
Finding Administrative Unit Members
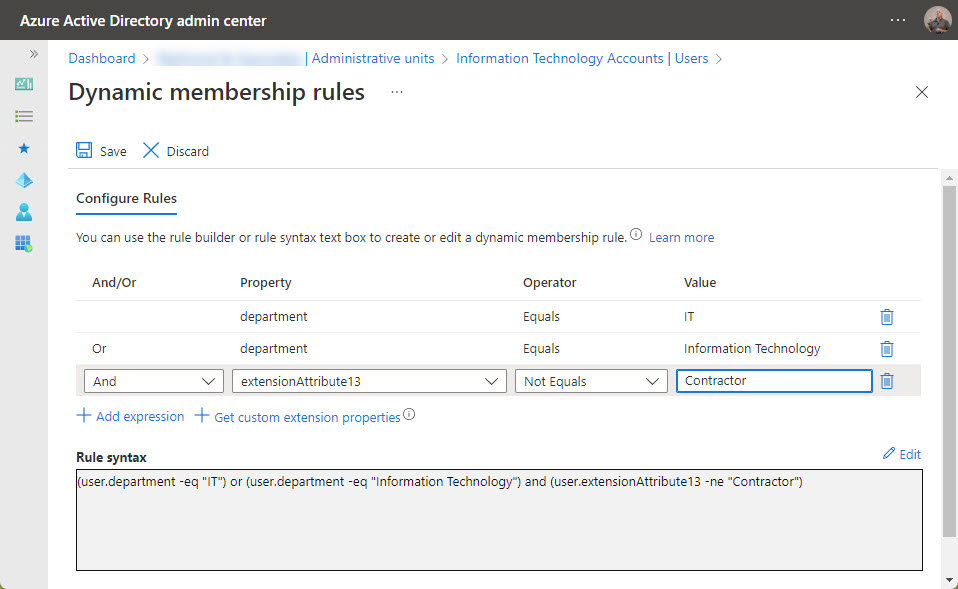
The next step is to add membership rules to instruct Azure AD how to find the members. In Figure 2, we’ve enhanced the basic query to find accounts with a specific value in the Department property to check the property for two values and to exclude accounts belonging to contractors (using one of the customizable extension properties). Saving the rule forces Azure AD to check its syntax. However, you won’t know if the rule works until Azure AD evaluates the rule against the directory to find matching accounts.
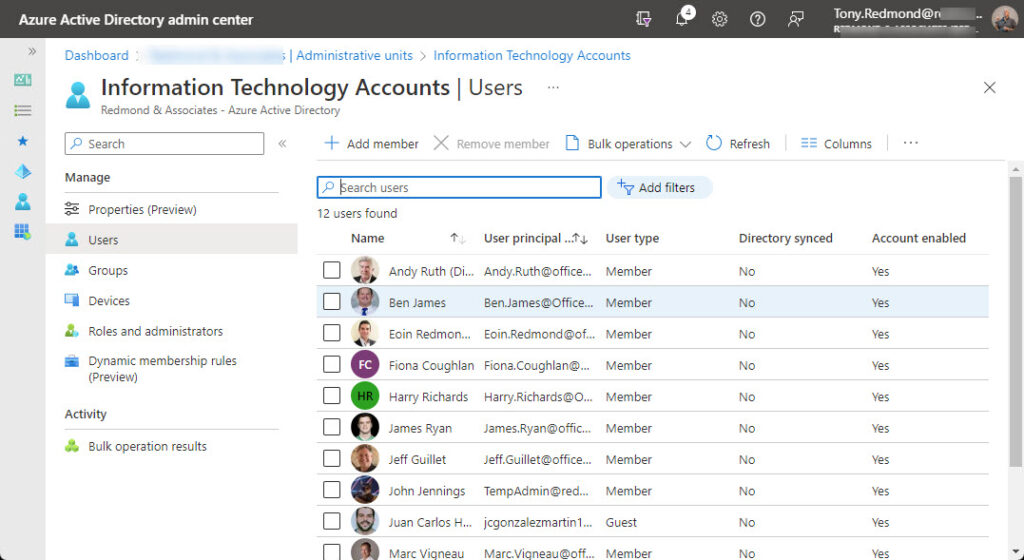
The evaluation process should happen quite quickly (within 30 minutes). When it does, the accounts found by the query can be browsed and validated, as shown in Figure 3.
The underlying query to check the accounts retrieved from Azure AD is a little more complex because the extension attributes are held as a set called onPremisesExtensionAttributes. This kind of Graph request is called an advanced query, so we need to pass the ConsistencyLevel and CountVariable parameters. Here’s the command:
[array]Get-MgUser -Filter "onPremisesExtensionAttributes/extensionAttribute13 ne 'Contractor' and (department eq 'IT' or department eq 'Information Technology')" -All -ConsistencyLevel "eventual" -CountVariable count Write-Host “Users found by query:” $Users.Value.displayName
After you’re happy that the query finds the correct user accounts, the dynamic administrative unit will continue to work as expected, assuming user account properties are correct. Once again, this underlines the importance of standardization during the account creation process.
Using PowerShell to Work with Administrative Units
The Microsoft Graph PowerShell SDK includes cmdlets to manage Azure AD administrative units. To start, the Get-MgBetaAdministrativeUnit cmdlet lists all the administrative units in the tenant:
Get-MgBetaAdministrativeUnit | Format-Table DisplayName, Description, Id DisplayName Description Id ----------- ----------- -- Ireland Ireland Region 0ee53a45-bbee-4571-a407-56acc0b944a1 Information Technology Accounts Accounts for Information Technology 150dccad-f8b8-4e54-9246-89834b8b5a25 Guests AU Admin unit for guest accounts 34d9069c-f448-41af-b14e-a8a1f4f42e77 United States U.S. Region 4d3ae8ee-212b-4be4-965c-8b5111d4488e Engineering Engineering 66faad17-cc6d-45bb-8d88-35789b9b3c00 Finance Department Users Finance people de2615e8-7c99-446c-83bd-e3a80d11ce18
To see more information about the settings for an administrative unit, expand the AdditionalProperties property. This is where Azure AD holds information about the membership type and rule.
Get-MgBetaAdministrativeUnit -AdministrativeUnitId 150dccad-f8b8-4e54-9246-89834b8b5a25 | Select-Object -ExpandProperty AdditionalProperties Key Value --- ----- @odata.context https://graph.microsoft.com/beta/$metadata#administrativeUnits/$entity membershipRule (user.department -eq "IT") or (user.department -eq "Information Technology") and (user... membershipType Dynamic membershipRuleProcessingState On
The membership rule is truncated in this output. To be certain to see the full rule, extract the properties and lookup the membership rule:
[array]$Properties = Get-MgBetaAdministrativeUnit -AdministrativeUnitId 150dccad-f8b8-4e54-9246-89834b8b5a25 | Select-Object -ExpandProperty AdditionalProperties $Properties['membershipRule'] (user.department -eq "IT") or (user.department -eq "Information Technology") and (user.extensionAttribute13 -ne "Contractor")
To find the members of an administrative unit, run the Get-MgAdministrativeUnit cmdlet. This returns the object identifiers for the member accounts:
Get-MgBetaAdministrativeUnitMember -AdministrativeUnitId 150dccad-f8b8-4e54-9246-89834b8b5a25 Id DeletedDateTime -- --------------- 96155a51-6885-4c8f-a8b6-e1614af08675 8f94abd3-b46f-4072-8ef4-af7475401b2f
The other properties for the members are in the AdditionalProperties property. Here’s how to list the display names of the members.
[array]$Members = (Get-MgBetaAdministrativeUnitMember -AdministrativeUnitId 150dccad-f8b8-4e54-9246-89834b8b5a25).AdditionalProperties $Members.displayName
In most cases, it’s easier to update administrative units through the Azure AD admin center. To do it with PowerShell, run the Update-MgAdministrativeUnit cmdlet. In this example, we first create a hash table to update the membership rule and then run the cmdlet to update the rule and the description and display name for the unit.
$NewRule = @{membershipRule='user.department eq "Group HQ"'}
Update-MgBetaAdministrativeUnit -AdministrativeUnitId 150dccad-f8b8-4e54-9246-89834b8b5a25 -AdditionalProperties $NewRule -Description "Changed because I can" -DisplayName 'Group HQ Users'
Not Email
It’s important to stress that an administrative unit exists purely as an aid for administrative operations. It’s not a source for email or a recipient for email. If you want dynamic membership for email, consider using a dynamic distribution list or a dynamic Microsoft 365 group. However, you could read the list of members from an administrative unit and add them as recipients to a message that’s sent using a Graph API.
The Directory’s the Key
Many benefits flow if an organization’s directory is well-maintained and populated with accurate information about user accounts. This is obvious when you consider administrative automation, but it’s also the case that Microsoft is leveraging the directory in many ways, such as adaptive scopes for retention policies. If you’ve done the hard work to create and maintain a well-managed directory, dynamic administrative units can help delegate user and device management away from tenant administrators.
Cybersecurity Risk Management for Active Directory
Discover how to prevent and recover from AD attacks through these Cybersecurity Risk Management Solutions.





Thank you so much Tony,
I was wondering how my PS code should look like if i want to create a bunch of Dynamic AUs from a csv file where the Rule should be for each AU for example: The user department is the display name of the AU?
I tried this: MembershipRule = ‘(user.Department -eq $DynamicAU.DisplayName)’ but seems to not be working!
Given a CSV file like this:
Name
Information Technology
Artificial Intelligence
Generative AI
You could do something like this:
ForEach ($AU in $AUs) {
$Description = (“Dynamic administrative unit created for the {0} department created {1}” -f $AU.Name, (Get-Date))
$DisplayName = (“Dynamic administrative unit created for the {0} department” -f $AU.Name)
$MembershipRule = “@{membershipRule=’user.department eq ” + “‘” + $AU.Name + “‘” + ‘”‘ + “‘}”
New-MgBetaAdministrativeUnit -Description $Description -AdditionalProperties $MembershipRule -Description $Description -MembershipType ‘Dynamic’ -MembershipRuleProcessingState ‘On’
}
I can’t test this because my Azure AD Premium licenses have expired and I am awaiting renewal, but the code above creates the rule in the correct format.
Well, I was wrong in my advice. The right way to do this is to:
1. Create a new admin unit.
2. Update the new admin unit with the properties to make it a dynamic AU.
I’ve worked out the basics of a script and will publish it when it works the way I want it to.
Try this: https://office365itpros.com/2023/09/25/dynamic-administrative-units-ps/
Thanks for the write up tony great as always. I still think the inbuilt “dynamic” AADAU aren’t great. 1. doesn’t support adding groups. 2. doesn’t support added devices and users in the one AADAU 3. Licenses are required for all your scoped admins.
For now I’m going to keep supporting this script but I am happy AADAU has gone GA. I think it was preview since 2014 which was the longest preview product I have ever seen.
https://github.com/JBines/Set-AADAUDynamic
Isn’t PowerShell wonderful?
Hi,
Great article, we are half way in on setting our path towards using these atrributes to easy up our onboarding routines.
I sometimes find that the attributes in AAD is not suiting and would like to add my own. Is that possible you think?`
For example, we have all countries, cities, departement and emails adress used in our dynamic assigment rule.
But when we try to find a way for “boardmembers” that are not in a country, city or departement the rule gets hard to achieve.
Does “custom security attributes” solve this for me or can they be used in the syntax rule for a dynamic assigned group? Thanks for one of the best blogs and materials for microsoft365 out there!
I wouldn’t use custom security attributes. There are fifteen custom extension attributes that are designed for this purpose. I compare them against Azure AD custom security attributes in https://practical365.com/azure-ad-custom-security-attributes-exo/
Here’s an example of using custom attributes in a dynamic distribution list. The same concept extends to dynamic Azure AD groups: https://office365itpros.com/2021/01/18/dynamic-distribution-lists-filters/
There is one concern that it is still not supporting user.memberof dynamic role.
I have tried to tested but it is not even able to create the dynamic role.
did it work with you ,as I need to add users to an AU based on their group membership.
Given that MemberOf is still a preview feature that offers limited functionality, its lack of support in dynamic administrative units is unsurprising.
Thank you. Great article as always. Unrelated, but have the site developers at P365 considering implementing dark mode for the site layout/articles?
I think that most of the available energy goes into writing, editing, and preparing articles for publication. But I will pass on your comment to the folks who look after the management of the site.