Let’s face it, the internet is full of bad advice, especially when it comes to technical topics. And I’m not talking about articles or blog posts you might find that are just badly written, or are wrong for your specific scenario but correct for others. I’m talking about advice that is wrong on every level and should not be followed.
Case in point, the question of whether to disable the Windows Firewall on Exchange servers.
I get it. The Windows Firewall has caused you some problems in the past (I’ve been there, it’s not fun). So you turn it off on all your server builds, because your servers are sitting safely on your internal network protected by your network firewall. But the fact is that is a bad practice, and one you should move away from. Especially when it comes to Exchange servers.
Exchange setup will add rules to the Windows Firewall to allow Exchange to work, it’s that simple. You don’t need to disable the Windows Firewall. If you have extra requirements for your Windows servers (such as a special port used by your monitoring system agent) then add a rule to the server’s firewall. Use Group Policy to do it, if you want to save some time.
And if you see advice like this on the internet, ignore it. It’s wrong and dangerous.
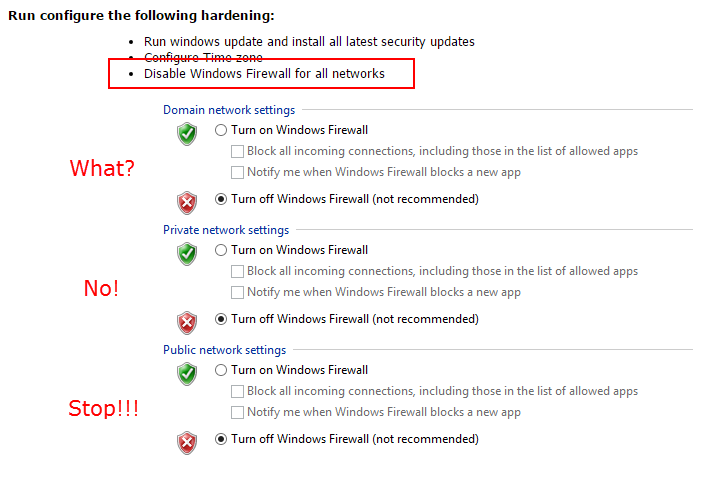



Paul, you have always given excellent advice, but this article directly contradicts what the MS Exchange team says. https://technet.microsoft.com/library/bb331973(v=exchg.150).aspx. They say “We do not support restricting or altering traffic between internal Exchange servers….” I have security auditors cringing about the Windows firewalls being off on my Exchange servers, so I’m looking at turning them back on. I did see the Exchange firewall rules were automatically created, so I wonder why the Exchange team says it is not supported. Any thoughts?
The Real Person!
Author Paul Cunningham acts as a real person and passed all tests against spambots. Anti-Spam by CleanTalk.
That article is referring to network firewalls, not the Windows firewall. Microsoft supports the use of the Windows firewall and Exchange setup adds the necessary rules for Exchange to function. As you’ll see from the comment by Brian Day at Microsoft on this blog post, Exchange actually expects the firewall service to be running:
https://blogs.technet.microsoft.com/exchange/2013/02/18/exchange-firewalls-and-support-oh-my/
He says you can disable the Windows firewall if you want to. He doesn’t say that you *should* do it, and I think he’s being diplomatic about the topic (also keep in mind that blog post is from 2013) by even suggesting that it’s okay.
I can be more straightforward about it in my advice. Don’t disable the Windows firewall on your Exchange servers.
Hope that helps.
Only problem is that ping is not working with firewall. So exception would be a good idea but that also makes vulnerable to death of ping attack.
The Real Person!
Author Paul Cunningham acts as a real person and passed all tests against spambots. Anti-Spam by CleanTalk.
You think someone on your network is going to launch a “death of ping attach” against your Exchange server?
The reason firewall is being disabled is not because well known apps like exchange, but because port requirements for custom app/tools/monitoring.
In that case I think the Admins should be going through and figuring out what’s needed and what’s not. To leave an entire server vulnerable just out of convenience seems a bit silly.
leave the firewall alone. default settings. i guess the reason some admins disables the firewall is the lack of knowledge on how to allow the custom services/ports they require thru the firewall.
it is much easier to just disable it than learn how to work with the firewall.
A good alternative is to leave the Firewall Service on but Allow all traffic by default.
Go to Administrative Tools > Windows Firewall with Advanced Security
At the bottom of the firewall profiles (eg Domain, Private and Public) there is a link to “Windows Firewall Properties”. set those to allow by default instead block.
If you prefer command prompt will by like:
Netsh advFirewall Set domainprofile Firewallpolicy allowinbound.
In this way you leave full firewall functionality but without blocking any thing (outbound is allowed for any by default)
I use this when installing new servers (services) and when done and everything is working I tune the firewall till it is working and remove this “policy”
forgot to say that in this way Installation programs are be able to write their firewall rules as when the firewall normally functions. It actually is, you only allow ANY traffic
Productions servers need a firewall on the host. We have already seen breaches over well known ports within a LAN. Intruders breach the edge firewall then your production server is an open door.
Resource load of the firewall should be factored into the design phase.
If your a sys admin supporting Windows servers please take time to learn the Windows firewall, it works.
The Real Person!
Author Paul Cunningham acts as a real person and passed all tests against spambots. Anti-Spam by CleanTalk.
No that’s not a good alternative.
It would be helpful if you could go into elaboration as to why disabling the firewall is a bad idea. Many environments use alternative host based that generally advocate disabling the Windows firewall to prevent conflict (McAfee HIPS is a notable example). If your qualms involve leaving the system unprotected, that’s one thing, but if we’re talking about performance or functionality impacts that would be good to state outright. I’ve heard it told that the Windows firewall service functions as an extension to the RPC stack and performance is impacted when disabled.
The Real Person!
Author Paul Cunningham acts as a real person and passed all tests against spambots. Anti-Spam by CleanTalk.
Leaving the host unprotected is the obvious downside, but there’s also the fact that some people actually turn off the firewall by disabling the service, which is a mistake that begins with the notion that the firewall should be disabled in the first place. Unfortunately, people who should know better are making the recommendation to disable the firewall on Exchange servers, and leading people down this bad road.
I won’t comment on third party replacements other than to say I’ve never met one that lived up to its marketing promises, or wasn’t harmful to the performance and stability of the server.
When firewall is enabled Exchange setup creates exclusions as described. If you disbale the firewall exclusions do not get created so turning on the firewall later is a pain in the you know where.