When an SSL certificate has been installed on an Exchange 2013 server it is not automatically enabled for any of the Exchange services such as IIS (for OWA, Outlook Anywhere, ActiveSync etc), POP, IMAP or SMTP.
The administrator must manually assign the certificate to the services that the SSL certificate is intended to be used for.
In the Exchange Administration Center navigate to Servers -> Certificates and choose the server that has the SSL certificate you wish to assign. The certificate must already been in a valid status before you can proceed further.
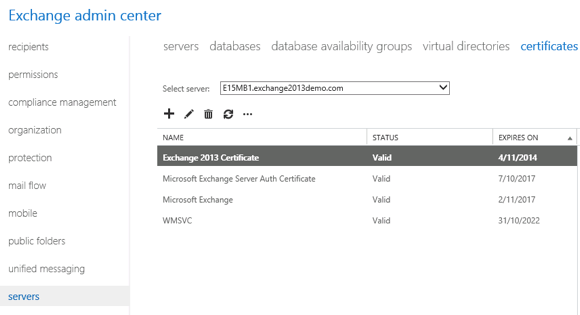
Click the edit icon and then select Services.
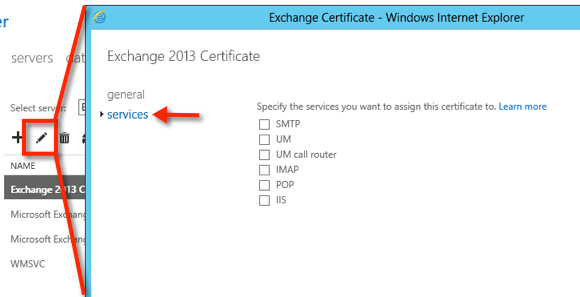
Tick the boxes for the services that you wish to assign the SSL certificate to, then click Save. The typical services to assign to an SSL certificate are IIS and SMTP.
See also Checkboxes Greyed Out When Managing Services for an Exchange 2013 SSL Certificate.
If you are overwriting existing certificates you will be prompted to confirm that.

If you are using the same SSL certificate on multiple servers you can also export/import the certificate to those servers.
To test that the SSL certificate is working you can browse to the Outlook Web App URL for that server and see whether you receive an invalid certificate warning from your web browser.
If you’re interested in how Exchange handles selection of a certificate when multiple certificates are bound to the SMTP protocol, here are some articles that explain it:



Thanks for valued Information , Paul .
I have acertificate installed on three exchange 2016 servers contains SANs ( Mail, auto discover )
and working fine ,
But the problem i s when opening ecp url like : https://EXCH-server-name/ecp
certificate invalid because doesn’t have Server names ,
can i make once certificate for OWA and Auto discover and another for ECP urls ?
Could you help please.
We used self signed certificates currently. I’ve been asked to assign a friendly name, via our external dns, which I’ve done, to our external ip address for OWA. This is to avoid getting certificate mismatch warnings.
I’ve purchased a new certificate against this friendly name. I’ve then bound this in IIS to the OWA site.
When browsing to OWA, users do not get the certificate mismatch warning anymore.
But within 30 minutes, Outlook desktop clients were getting a certificate warning. I’ve reverted back so that all services in IIS use the self signed certificate. Warnings stopped. When installing Outlook, I’m always prompted to install a self signed certificate.
I’ve changed nothing in the Exchange Admin Center.
Thanks.
If I have a hundred servers that I need to enable the certificate on (Digicert replacement of Symantec) what kind of gotchas am I looking at. I was thinking something like:
import-csv ExchangeServers.txt | ForEach-Object -Process {Enable-ExchangeCertificate -server $_.Server -Thumbprint “<thumbprint of cert" -Services "SMTP,IMAP,POP,IIS" }
As far as I can tell, this should work, or am I missing something?
Hey Paul,
I currently have Symantec certs installed on my Exchange 2013 servers, Digicert took over the service and provided me new certs without having to generate a new CSR, can I still go through this process to install these or do I need to do it another way?
so in selecting from multiple, still valid certificates, what matters only is the “most recent Valid from date”. so two identical valid certificates, one issued (valid from) January 1 and the other issued (valid from) March 4, the latter will be selected.
Hi Paul,
I was happy to see that you were still answering some questions so I’m hoping you’d have a min to answer mine.
I just renewed my cert, and when attempting to to assign the iis service from the gui, exchange prompts me with: “Warning: Do you want to enforce SSL communication on the root web site? If not, rerun the cmdlet with the -DoNotRequireSSL parameter”
What is this in reference to? I’m hesitant to move forward from here.
Thank you,
~Ty
Have you manually turned off the SSL requirement on the IIS website in the past?
Hello Paul,
I have question please
I am using a public certificate from godaddy, and I see that WMSVC certificate will be expired in few months
Is it mandatory to renew it?
Thanks,
Mina
Hello Paul,
I have question please
I am using a public certificate from godaddy, and I see that also Microsoft Exchange Server Auth certificate will be expired in a few weeks months
Is it mandatory to renew it?
Thanks,
Mina
Dear Paul,
Thank you for informative article. I am facing with the weird issue. Hopefully you can help me to solve it. In the past, I already had a Exchange certificate for our Exchange Server 2013. For now, It was expired; hence, I must renew this certificate with the new one by ADCS(certsrv) via Windows Server 2012 R2. It seem to be worked properly, but whenever our client open their outlook, the error appeared that show outlook client keeps connecting to my expired certificate.
How could I delete permanently the old certificate?
P/S: Although error pop-up showing off time by time, our client still send/receive message successfully.
Did you enable the new certificate in Exchange? It should be enabled for IIS/HTTPS services.
Yes. I already enabled the new certificates in my Exchange . In particular, I enabled SMTP, IMAP, POP and IIS. Do I need do anything else?
Have you tried restarting IIS?
Yes. I did restart IIS. However, outlook of client still pointing to my old certificate. Does it relate to ADDS? My Exchange Server 2013 was set up to operate on Premise.
Clients don’t point to certificates. They connect to an IP address based on a DNS lookup of the client access namespace. It’s possible what you’re seeing is caching on the server side, but an IIS reset should have cleared that. It’s also possible your clients are connecting to an IP address you’re not expecting them to, so you would need to use the Outlook connection status box or something like Fiddler to work that out.
Paul,
Thank you for the info you supplied. I had a strange issue. I installed a new GoDaddy Cert on my servers. All the SANs have the autodiscover and the server names. I applied it to the IIS service only and OWA and phones worked fine but all of my outlook clients continued to prompt for credntials. Was I supposed to also change the SMTP service with the new cert?
The certificate shouldn’t have the server names on it. It should only have the client access namespaces (e.g. OWA, EAS, Outlook Anywhere, EWS, Autodiscover, etc). If you’re getting Outlook client prompts then it’s likely you’ve missed a namespace or misconfigured a virtual directory.
Hi Paul,
I have the below setup. Do i need to import and export SSL to second CAS server
EXCH-MBX1 – Mailbox Role – Installed in HQ
EXCH-MBX2 – Mailbox Role – Installed in HQ
EXCH-CAS1 – Mailbox Role – Installed in HQ
EXCH-MBX3 – Mailbox & CAS Role – Installed in DR.
All servers in same subnet. When both server fails on HQ the database moves to EXCH-MBX3 successfully but outlook can not connect.
The certificate needs to be installed on all servers that are configured with the same CAS namespaces.
Hi Paul,
after i assigned ssl certificate to service SMTP. i cannot send or recieve any email, email is stay in draft.
Please help me.
Thanks
Hi all,
please help me this issue.
after i assigned ssl certificate to service SMTP, i cant send email. if i delete ssl certificate then i send email normal.
Thanks in advance!
I wish I had another Exchange server to look at for reference, but could you tell me if you see anything wrong with our cert stores? I’m wondering if something is out of place there. It’s hard telling who might have done what manually here. Thanks!
http://imgur.com/a/AqfEb
http://imgur.com/a/BmZ9O
Somehow our Exchange server managed to get two certs assigned to IIS, which I believe is the reason behind the Schannel errors in the event log on the Exchange server (I posted screen shots and more details here: https://community.spiceworks.com/topic/1891263-schannel-errors-on-exchange-2013-server). Any suggestions on how I should proceed? Thank you!
Exchange 2013 has two IIS websites; a front end website, and a back end website. The back end website is usually left alone and can keep using the self-signed certificate.
I’ve seen SChannel errors on Exchange servers when the private key for the certificate is missing or corrupt. That’s something the certificate MMC snapin could tell you.
Thank you, Paul.
Is there any way to determine what the back end is using for a cert? If I removed the self-signed and it’s attached to the back end, would the back end find the CA cert and use it?
Both private keys are in Personal>Certificates and Trusted Root Certification Authorities>Certificates.
You shouldn’t remove the self-signed certificate. If you’ve removed it, you’ll need to replace it with another self-signed certificate containing the server’s short name and FQDN, and re-bind it to SMTP and to the back end IIS site.
No the back end won’t “find” the CA cert and use it. IIS doesn’t pick its own certificates autonomously.
I didn’t remove the self-signed cert.
I’ve read that others are excluding the Schannel events from the event viewer. I’d much rather find an answer to what’s causing them but have had 0 luck. Do you think it’s a sign of an underlying problem or are they safe to ignore if everything appears to be working OK?
Thank you, thank you, thank you! This sort of clear, specific information is sorely lacking in Microsoft’s documentation. You are heaven sent and now bookmarked.
Pingback: Exchange 2013 Add public certificate and enable it - Proxima's IT Corner
What if you don’t overwrite certificate? What will happen in that case?
Exchange will continue using the certificate as the default transport certificate.
Is there a way to manually undo that “No” and make it “Yes”? What will happen if default certificate expires and renewed certificate did’n overwrite? IIS works with renewed (when you open OWA) but what about smtp, is it going to work?
Thank you for your answer.
IIRC, re-running the enable-exchangecertificate command for your preferred certificate will ask you again.
If the default cert expires I think it’s not catastrophic but it does cause some issues. Best to avoid it of course, which I try to, hence why I can’t easily recall the bad things that happen if you don’t 🙂
hi Mr.paul
after assign certificate i could not login ecp pannel
Paul,
After importing the certificate and assigning services, I ran some connectivity tests at exrca.com to verify. It passes with a warning I’m not sure how to interpret:
Analyzing the certificate chains for compatibility problems with versions of Windows.
Potential compatibility problems were identified with some versions of Windows.
Additional Details
The Microsoft Connectivity Analyzer can only validate the certificate chain using the Root Certificate Update functionality from Windows Update. Your certificate may not be trusted on Windows if the “Update Root Certificates” feature isn’t enabled.
Elapsed Time: 1 ms.
Hi Paul
Thanks for the article. 1 question though, whats the purpose of assigning a certificate to SMTP? I can understand IIS for OWA.
Is the main purpose for assigning a cert for SMTP service related to the Outlook client connection to the server encrypting the connection?
Cheers
Jay
SMTP connections can be encrypted using TLS, which requires a certificate.
Here is the solution I found for how to assign the certificate to the receive connector via PowerShell nothing in the Web UI worked for me.
You need to get the cert finger print
[PS] C:Windowssystem32>Get-ExchangeCertificate -server MYSERVER
Thumbprint Services Subject
———- ——– ——-
ABCBADCD3C8BE1B285BE787AFA369CF558331123 …WS.. CN=mail.company.com
Determine the connector on port 587 you want to assign the cert too.
[PS] C:Windowssystem32>Get-ReceiveConnector -server MYSERVER
Identity Bindings Enabled
——– ——– ——-
MYSERVERClient Frontend MYSERVER {[::]:587, 0.0.0.0:587} True
The use the following commands to assign your cert.
Edit: removed commands that WordPress was mangling.
Your syntax is mangled by WordPress, but that’s okay, I’ve covered it with correct syntax in this article already:
https://www.practical365.com/configuring-the-tls-certificate-name-for-exchange-server-receive-connectors/
Note, you don’t assign certificates to connectors via the Exchange Admin Center. All you can do is enable a certificate for SMTP. The steps you found are then used to tell the connector which certificate to use (because multiple certificates can be enabled for SMTP).
Thanks for your helpful articles. There’s one think i’ve been struggling with for a long time and still i haven’t been able to find a solution.
I have to certificates installed on my server: mail.myserver.net and autodiscover.myserver.net
I can assign mail.myserver.net for iis owa etc. but it’s automatically assigning this certificate to auto discover to.. how can i set a separate auto discover certificate?
I just can’t find the proper solution, so for now i’m not using mail.myserver but only auto discover.myserver for all services, that’s working but it’s not a nice url to use.
Only one certificate can be assigned to IIS, which is then used for all HTTPS services (including Autodiscover). The solution is to use a SAN certificate.
https://www.practical365.com/exchange-server-2013-ssl-certificates/
i installed a new certificate from GoDaddy and it’s showing as “valid” in the ecp for the services smtp and iis as describe in this post.
anyway, the smtp service is now enabled on two certificates (the new godaddy and the old one from thawte who will expire in some weeks).
i tried to disconnect the services on the old certificate by powershell:
enable-exchangecertificate -Thumbprint xxxxx -Services None
The command runs without an error, but the old certificate still exist for the smtp service.
can someone show me how to disable the smtp service from the old cert?
how can i check, which certificate is used by the SMTP Service? Godaddy should be prefered for this service.
Many thanks for your answers!
You can remove an expired certificate by running Remove-ExchangeCertificate with the thumbprint value for that cert.
Done! Perfect! Thanks for your help
Pingback: Digicert Vs Godaddy Ssl – Cyber Sun
Hi All,
I am facing an issue with Exchange Certificate. I have enabled exchange services with my wild card certificate. But when I connect via IMAP, it is keep prompting for username/password. ECP is showing that services are bind with my certificate but imap is not working on port 993. Can anyone help me in this regard?
Anees
Hi to all,
I have a question regarding microsoft-server-activesync. I have installed a new exchange 2013 and outlook internally and owa externally (https://clientname.dyndns.org/owa) were working fine with the self-signed certificate generated during setup.
After changing the external url for microsoft-server-activesync to “https://clientname.dyndns.org/Microsoft-Server-ActiveSync”, EAS was working but after a while now it sees a previous old certificate that I was using on the phones and that is expired.
Also my externally “https://clientname.dyndns.org/OWA” is not working anymore and also is seeing this old certificate now. How can i solve this?
Now only my outlook clients are connecting to outlook with the self signed certificate generated by the setup. Can I have my local outlook clients using the self signed certificate generated by the setup and create a new certificate only to be used by OWA and EAS for mobile?
I really appreciate any help…
Only one certificate can be bound to IIS on Exchange for use with OWA, EAS, and any other HTTPS services.
Sounds like you’re seeing different results for internal vs external clients. That suggests to me that a firewall, reverse proxy, or load balancer is being used to handle the incoming connections from external devices, and that most likely has the old expired certificate still configured on it.
Maye you have some idea about a little problem?
I want to let my users to use a receive connector for relay – it is authenticated and requires SSL.
I have installed a certificate for: emailserver.company.com
This sertificate is enabled for IISI, IMAP, and SMTP. With IIS and IMAP, it’s fine – but when i try to to a SMTP session over SSL, the server offers me the default self-sigen sertificate created during install (it works – but gives a security warning for the clients). Have been trying to tell Exchange to use the emailserver.compnany.com certificate for SMTP SLL conections, but failed. I just cant make the proper certifikace as “default”, and with SMTP it’s not that simple, as with other services – if i enable the next certificate for SMTP, the previous certificates stay enabled too.
Any thoughts?
Vahur
Have you had any luck on this issue? i think we are experiencing the same over here.
J
Hello, I have the same issue as above where my SMTP relay refuses to use the cert I purchased even though it is listed to use SMTP as one of the services. Did you get this resolved? And if so, how? – Thank you in advance!
Never mind, I got it figured out. You have to create a new Frontend Receive connector and change the FQDN of that new connector to the same as cert. ie. mail.domain.com
Jason
I’m extremely pleased to find this great site. I wanted to thank you for your time for this particularly wonderful read!! I definitely loved every little bit of it and i also have you book marked to check out new information on your site.
Hi everyone, it’s my first pay a visit at this web page, and article is genuinely fruitful for me, keep up posting these articles.
Is there a way to go back and update the certificate if you opted for “no” in the gui?
Hi All,
I am getting error once i enabled go daddy SSL certificate on passive node.
Certificate imported from active node and enabled services. its asked to overwrite the certificate and i confirmed to proceed. after that users are getting security alert error while opening outlook from active node.
Security alert with active node host name.
Information you exchange with the site cannot be viewed or changed by others. However,there is problem with the site’s security certificate.
Please help me to resolve this issue.
Pingback: SSL Certificates for Exchange Server 2013
Pingback: exercise for weight loss
Hi all, question, what types of certs exchange 2013 manages? does it allow wildcards, and multiple domains?
Regards
Here you go:
https://www.practical365.com/exchange-server-2013-ssl-certificates/
@Rick
I did in the end. There’s a tool I used which takes the urls per service and the certificates you want and goes through ex2013 setting all the vdirs etc in the way I needed. I was initially sus about anything other than my hands meddling with exchange but it came recommended by another internal exchange engineer here, and worked a treat.
And the url you’re no doubt hanging out for is this I think from a quick mobile search. http://www.digicert.com/internal-domain-name-tool.htm
Best of luck!
Ryan
@Ryan,
Hi Ryan,
Did you ever get a solution for your problem, we have a similar issue we are facing and would appreciate any feedback from your experience.
Thanks in advance
Rick.
Hoping you can help Paul,
I’ve setup a single server Exchange 2013 env, external webmail.domain.com and internally they access Outlook Anywhere with either exchangeserver.ad.domain.com or autodiscover.ad.domain.com (not sure which), I have two Wildcard Certs. *.ad.domain.com and *.domain.com.
How can I secure the webmail.domain.com with the one External *.domain.com SSL cert and the other Internal outlook anywhere, which in my mind is still IIS with a different internal cert for *.ad.domain.com internally? It seems one or the other… ?
Appreciate your thoughts…
Pingback: Avoiding Server Names in SSL Certificates for Exchange Server 2013
Hi there,
does anyone made it to use a wildcard cretificate with exchange 2013 and imap ?
WARNING: This certificate with thumbprint and subject ‘*.domain.tld’ cannot used
for IMAP SSL/TLS connections because the subject is not a Fully Qualified Domain Name (FQDN). Use command
Set-IMAPSettings to set X509CertificateName to the FQDN of the service.
Trying to set the fqn gives no error
[PS] C:Windowssystem32>Set-IMAPSettings -server -X509CertificateName mail.domain.tld
WARNING: Changes to IMAP4 settings will only take effect after all Microsoft Exchange IMAP4 services are restarted
after service restart same error as above when trying to enable ssl.
I currently have a certificate from GODaddy on my existing production Exchange 2007 Server. I am now adding Exchange 2013 to my domain to run in parallel until I have all of my mailboxes migrated. How can I take the existing cert that is running on the 2007 server and add the Exchange 2013 server to it as well,.
My cert from GoDaddy allows for multiple domains/servers. Can I just add the new server to the cert then download and import to the 2013 Server?
Hi Paul,
For internal user/non-domain PC, do I need to create certificate ? and do I need to configure DNS record ?
I generally recommend creating new certificates instead of relying on the self-signed ones.
Yes you’ll need to create DNS records for any names/aliases you plan to use for different services (eg mail.domain.com).
Should we delete the old self signed certs after we get our new certificates or just leave them as is? Thank you for great information on Exchange 2013!
You can leave them. Especially if they are still bound to backend Mailbox server role services.
Very informative article. I was trying to do the same method of creating, importing and enabling certs i used in 2007, and it more or less failed. Seems they changed the semantics of the powershell commands. So here is a question, I have deployed my new certs. In the past (2007) you removed the old certs. However there are 3 default certs, I am unsure if I am supposed to remove them or not, especially one of them CN=WMSvc. That sounds important?
The shell parameters have changed a bit I think. 2010/2013 make it much easier to use the console/EAC tools to manage certs (for most scenarios) so I generally recommend people just use those.
You can leave the default certs there.
Pingback: SSL Certificates for Exchange Server 2013