During the recent issues with iOS 6.1 causing excessive transaction logging on Exchange servers many administrators took steps to block iOS 6.1 devices from their servers using ActiveSync device access rules.
But when Apple released iOS 6.1.2 (which may or may not actually fix the problem) they noticed that upgraded devices weren’t being automatically allowed to connect to Exchange again.
To demonstrate this I put an iOS 6.1 block rule on my test server, connected at least once to confirm my device was being blocked, and then updated the device to iOS 6.1.2.
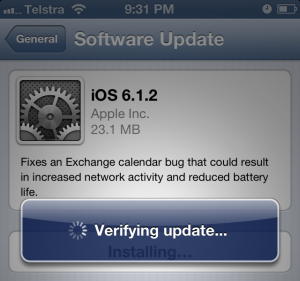
After running the update the device still can’t connect to Exchange. A look at the device state still shows that it is blocked by the rule put in place for iOS 6.1, even though I upgraded to 6.1.2.
[PS] C:\>Get-ActiveSyncDeviceStatistics -Mailbox alan.reid | select device* DeviceType : iPhone DeviceID : ApplC39GQ8NNDTDL DeviceUserAgent : Apple-iPhone4C1/1002.142 DeviceModel : iPhone4C1 DeviceFriendlyName : Black iPhone 4S DeviceOS : iOS 6.1 10B142 DeviceAccessState : Blocked DeviceAccessStateReason : DeviceRule DeviceAccessControlRule : iOS 6.1 10B142 (DeviceOS) DevicePolicyApplied : Default DevicePolicyApplicationStatus : AppliedInFull DeviceActiveSyncVersion : 14.1
I don’t want to remove the device access rule because the bug still exists in iOS 6.1 and other devices might still be running that version and try to connect to the server again.
So what can I do to let the updated device gain access to the server again?
One option is to remove the device from Exchange entirely. This causes it to be assessed as a new device the next time it connects, and in this scenario would be allowed to connect.
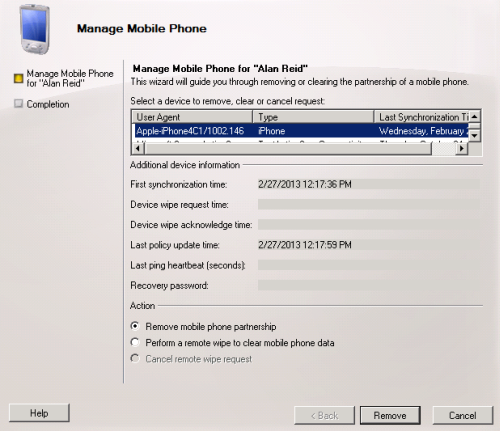
However at a large scale this may be impractical and cause a lot of administrative effort.
Another option is to use a device access rule that quarantines devices instead of blocking them. For example, here is a device access rule that quarantines the iPad 3 running iOS 6.1.
New-ActiveSyncDeviceAccessRule -QueryString "iOS 6.1 10B141" -Characteristic DeviceOS -AccessLevel Quarantine
When the device attempts to connect it is put in the quarantine state instead of being blocked.
[PS] C:\>Get-ActiveSyncDeviceStatistics -Mailbox mary.hayes | select device* DeviceType : iPad DeviceID : ApplDLXH8DELDVGJ DeviceUserAgent : Apple-iPad3C3/1002.141 DeviceModel : iPad3C3 DeviceFriendlyName : Black iPad DeviceOS : iOS 6.1 10B141 DeviceOSLanguage : en-GB DeviceAccessState : Quarantined DeviceAccessStateReason : DeviceRule DeviceAccessControlRule : iOS 6.1 10B141 (DeviceOS) DevicePolicyApplied : Default DevicePolicyApplicationStatus : AppliedInFull DeviceActiveSyncVersion : 14.1
After updating the device to iOS 6.1.2 it is allowed to connect again with no administrative action required.
[PS] C:\>Get-ActiveSyncDeviceStatistics -Mailbox mary.hayes | select device* DeviceType : iPad DeviceID : ApplDLXH8DELDVGJ DeviceUserAgent : Apple-iPad3C3/1002.146 DeviceModel : iPad3C3 DeviceFriendlyName : Black iPad DeviceOS : iOS 6.1.2 10B146 DeviceOSLanguage : en-GB DeviceAccessState : Allowed DeviceAccessStateReason : Global DeviceAccessControlRule : DevicePolicyApplied : Default DevicePolicyApplicationStatus : AppliedInFull DeviceActiveSyncVersion : 14.1
So which is the smarter approach?
- Blocking devices gives the administrator the most control over when the devices are allowed to connect to the server again. In the case of iOS 6.1 multiple updates have since been released that do not solve the very serious problem of excessive transaction logging, therefore the continued blocking of the device is a good thing. However when the bug is fixed the administrators will have to spend more time unblocking devices, which is possibly a costly exercise in very large scale environments.
- Quarantining devices is the least administrative effort, because an updated device will automatically be allowed to reconnect when it updates to a version that has no block/quarantine rule configured on the server. However the risk exists that an administrator will process a quarantine request and allow a device running one of the bad iOS versions to begin connecting to the server again.
As you can see neither approach is entirely perfect but fortunately administrators have some choice and flexibility in how they deal with this issue.



For me, quarantined devices could still fill up my log drives…
At my workplace, the system admins have opted for the first option: blocking devices. While I agree that this provides more control to the admin, the problem is that we have 2 that collaborate on a part-time basis so it is really difficult for them to keep track of all devices (e.g. the ticket system needs to be updated but overworked admins barely have time to finish all tasks…and then go update the ticket system!). The two part-time admins spend so much unlocking devices that this effort becomes too costly. Given the experience at my company, I would ask for people to opt for option 2.
Quarantining has to be the best way as it keeps management to the minimum, if you block then depending on the size could become very time consuming.
I assume that it would also allow you to let your bosses device sync? while keeping others quarantined as this can also cause headaches bigger than the initial problem.
Hi Paul, is it possible – if I have the device ID of the users iPad running 6.1, to do a quarantine on that single device rather than just removing or wiping it?
In the EMC the only 2 options are ‘Remove mobile phone partnership’ & ‘Perform a remote wipe’.
I only have a small number of users running 6.1, so I’d prefer to ‘suspend’ their syncing until they upgrade, but I need to do it on a user by user basis as I have 1 very important user, away on a fund raising trip and if I blocked his phone, it would NOT go down well 🙂
Cheers Shane.
I haven’t tested whether changing a block rule to a quarantine rule means that the blocked devices switch to a state of quarantine. But maybe that is one approach.
So in Powershell, is there a cmdlet that I can run, with the users device ID then, to block that device rather than delete or wipe it? In effect, just suspend syncing until I can confirm that it’s at 6.1.2?
Paul/et all is there a way to block unknown versions of IOS via this method (and the ones in your earlier article)?
IE- to block future versions of IOS until we can test them?
For unknown devices you’ll want to look at the default access level:
https://www.practical365.com/preventing-new-activesync-device-types-from-connecting-to-exchange-server-2010