A business that wants to deploy Exchange Server 2010 POP3 is most likely going to do it for users to remotely access their email from outside of the network. For a network that uses ISA Server 2006 as a firewall there are a few simple steps involved in opening up access for the clients.
Creating the Mail Submission Protocol Definition
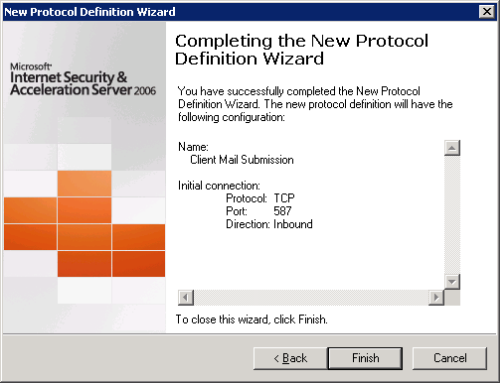
The first step is to create a new protocol definition in ISA Server 2006 for the port on which clients will send mail. As we saw in the previous articles on configuring Windows Live Mail for Exchange 2010 POP3 and publishing POP3 client settings to users the Receive Connector on the Exchange 2010 Client Access server uses TCP port 587. There is no default protocol definition in ISA Server 2006 for this port.
In the ISA management console go to the Toolbox in the right-hand pane and in the Protocols section click New -> Protocol.
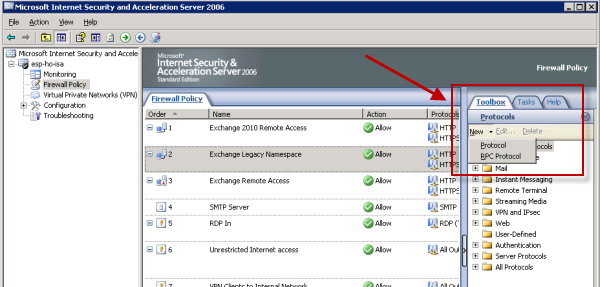
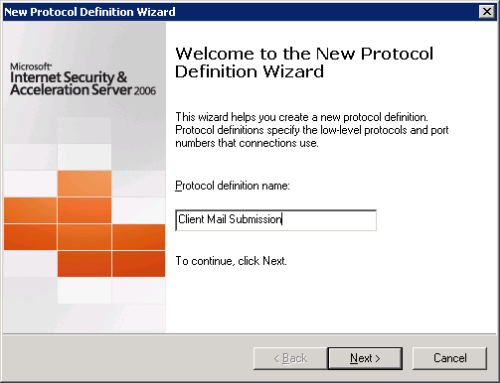
Give the new protocol a meaningful name.
Click the New button to configure the port for the new protocol.
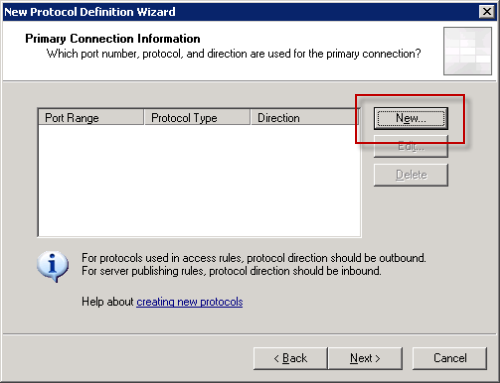
Configure the protocol for TCP, Inbound, on port 587.

Don’t configure any secondary connections.
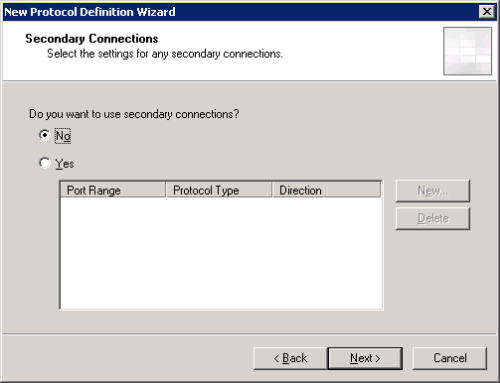
Click Finish to complete the new protocol definition.
Creating the ISA 2006 Access Rule for Exchange 2010 POP3 Clients
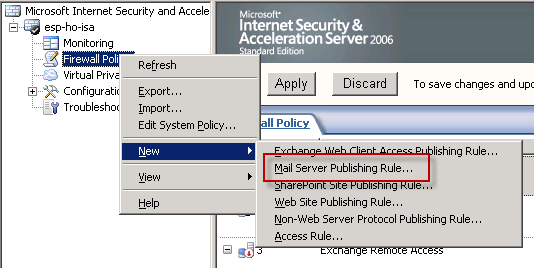
The next step is to create the access rule itself. There is a mail server publishing wizard that you can use to set up access rules for POP3, IMAP and SMTP but because it doesn’t include the option to set up the correct client mail submission port we’re using in this scenario, which means a little modification is needed at the end.
Start the Mail Server Publishing Rule wizard.
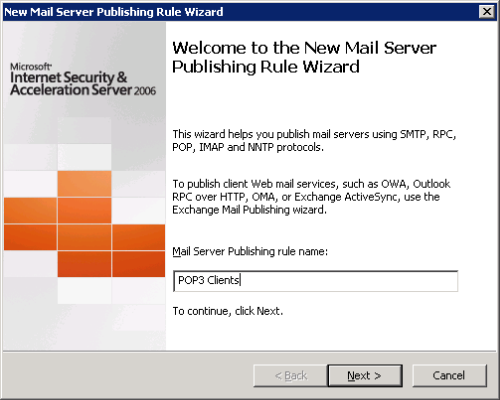
Give the rule a meaningful name. This name will then be appended automatically by ISA server depending on the protocols you choose in the next steps.
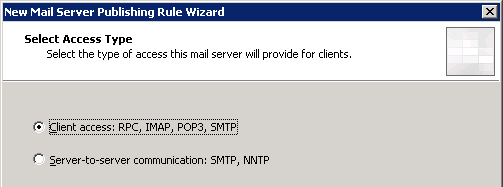
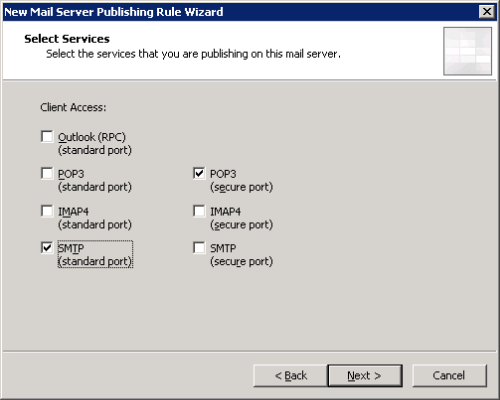
Set the Access Type to Client Access: RPC, IMAP, POP3, SMTP.
Tick the boxes for secure POP3 and standard SMTP (we’ll be changing the SMTP one shortly).
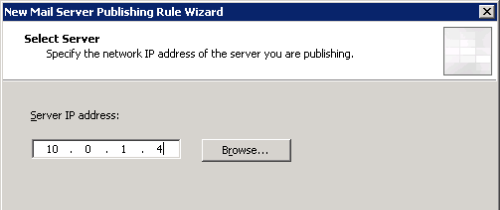
Enter the IP address of the Client Access/Hub Transport server. Note if these are different servers in your network you would just need to run the wizard twice to create one rule for POP3 to the Client Access server IP, and the other for SMTP to the Hub Transport server IP.
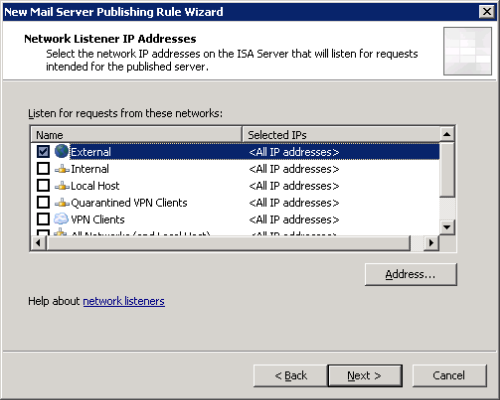
Set the listening network to External.
Click Finish to complete the wizard.
The two newly created rules will be visible in the Firewall Policy. Double-click the SMTP rule to open it.
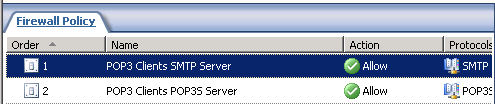
On the Traffic tab change the protocol from SMTP to the Client Mail Submission protocol we created earlier.
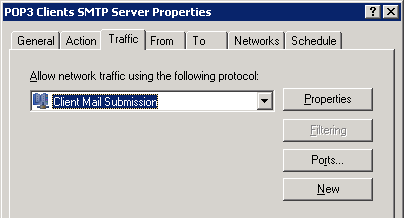
Click OK to apply the change to the rule.
The final step is to click Apply to commit the changes to the Firewall Policy.
![]()
You can now test the firewall rule with an email client outside of the network.




Hi,
we’ve tried to publish IMAP Server ( Exchange 2010 ), by this way over ISA Server 2006.
The ISA Server is configured with two Nic’s as DMZ between the external and an internal
Firewall. We’ve tested with the Microsoft Remote Connectivity Analyzer an IMAP Connection, this Connection will be portforwarded from the external Firewall to the isa Server. But the isa Server block this Connection. In the logfile you see, the Network package will be routed from
Client ip to the local ( ISA Server ) IP-Address.
Do you have an idea, what could be wrong?
We’re shure it is an Problem by the portforwarding an the isa Server.
Thank You
Alex