But Only if You Have Defender Plan 2
Last September, Microsoft announced the redirection from the old Office 365 Security and Compliance center to the new Microsoft 365 Defender portal as “the new home for all Office 365 customers who protect their organization’s email and collaboration tools.” It’s a clumsy turn of phrase, but it means that the Defender portal is where you go if you use Exchange Online Protection, Microsoft Defender for Office 365 Plan 1 or Plan 2. This page describes where features are now found.
Microsoft Defender for Office 365 is part of the overall Defender suite. Exchange Online Protection, which is part of Microsoft Defender for Office 365 Plan 1, is included in Office 365 E3. However, if you want to get Plan 1, you need an upgrade, Plan 1 includes features like Safe attachments (for email, Teams, SharePoint Online, and OneDrive for Business), Safe links, real-time malware detection, and anti-phishing. Plan 2 is where automation, investigation, and remediation kicks in. Although Plan 1 is worthy and useful, Plan 2 is where the interesting stuff happens, which is why it’s part of Office 365 E5 and Microsoft 365 E5 (remember, prices increase on March 1). Defender Plan 2 isn’t the only thing that’s included in Office 365 E5. You get a lot of added functionality in that SKU, so this is unlikely to be the deciding factor for a purchase.
Threat Explorer
Two of the unique Plan 2 capabilities drew my attention. The first is Threat Explorer (Figure 1), Microsoft’s single pane of glass view of email traffic within an organization presented with the intention of highlighting threat. Because user data is accessible through Threat Explorer, accounts need specific permissions like global administrator or security administrator to use the capability (see this page for permissions required for Defender).
Once Threat Explorer loads, the email entity page allows you to view up to 30 days of email traffic details, the URLs contained in email, what URLs receive clicks, top users targeted by spammers, where email comes from (based on geo-location), and so on. You can also see that accounts marked as priority users are highlighted.
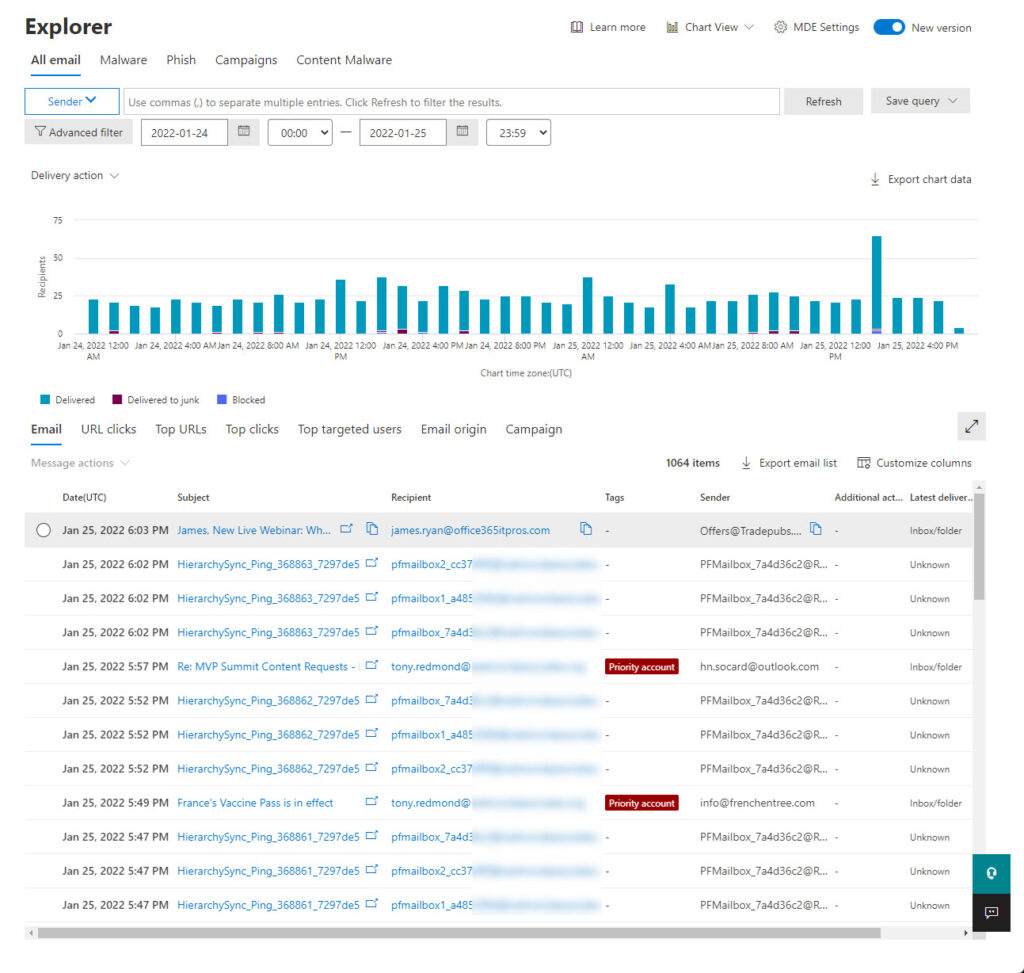
Not everything works in Threat Explorer as smoothly as I would like. For instance, the top targeted users view reported several people as being the target for several attempts (spam, malware, phishing?), but the details pane displayed no information about the messages marked as attempts. The view of email is cluttered by large quantities of messages generated by Exchange Online to synchronize public folder hierarchies (you won’t be bothered if the tenant doesn’t have any PFs); these obvious and well-known system messages should be filtered out. And Threat Explorer is slow to move from one option to the next, probably because of the amount of data it must handle. That’s not a criticism of the software – it’s more of a reflection on the amount of processing performed by Threat Explorer to make sense of email traffic.
If you discover a message of interest, you can view its details in a fly-out window. This is a super-useful tool because it presents a bunch of interesting information in one place. Take the message details shown in Figure 2, which is a piece of commercial email sent on behalf of a company. We can say this because the return path is different to the P2 sender and redirects responses to a marketing system (Data Loss Prevention policies changed recently to use the P2 sender to focus on the purported sender rather than return-path addresses). The headers are extracted and can be pasted into Microsoft’s message header analyzer site, which works like the Outlook Message Header Analyzer add-in.
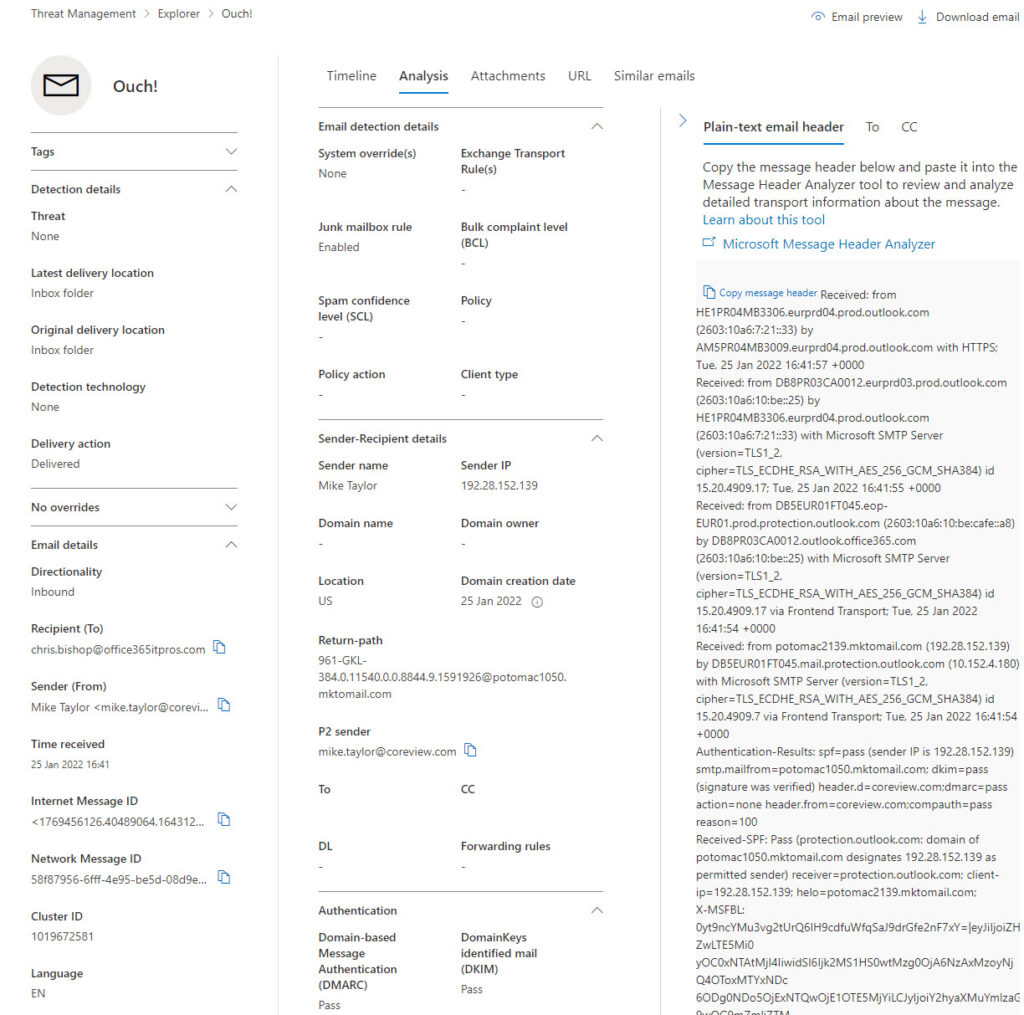
What’s missing in Figure 2 is any information about the SCL and BCL scores attributed by Exchange Online Protection to the message. I didn’t see this information show up for any message I examined, which might be due to a bug or some misconfiguration in my tenant. What does show up in the Email detection details section is information about policies applied to email which cause messages to be dealt with as spam. Messages detected as phishing display information under Detection details.
If the message being examined is in a cloud user mailbox, it’s accessible to Threat Explorer to preview or download the content. You can see these options in the upper right-hand corner of Figure 2. Messages blocked as phish cannot be previewed or downloaded through Threat Explorer.
What was interesting about the preview feature is that it decrypts messages protected using Office 365 Message Encryption (OME) or sensitivity labels. I assume Exchange Online uses its super-user permission in the same way that it can decrypt messages passing through the transport pipeline.
Some might be worried by administrator access to user data, especially when they learn about the decryption capability. However, those investigating an issue need tools to do their job and understanding why messages are problematic might require sight of their content. In any case, administrators have other ways to access mailbox data (like conducting a content search and exporting the results to a PST file), which is why organizations should limit permissions whenever possible and ask administrators to use non-permissioned accounts for day-to-day work.
Automated Investigations
The Investigations section was the second part of Defender for Office 365 Plan 2 which drew my attention. Administrators tend to have less time than they’d like to deal with threat, so Defender can respond to problems it detects using a component called automated investigation and response (AIR). I found one instance of an active investigation (Figure 3), sparked by the arrival of a phishing message addressed to multiple mailboxes.
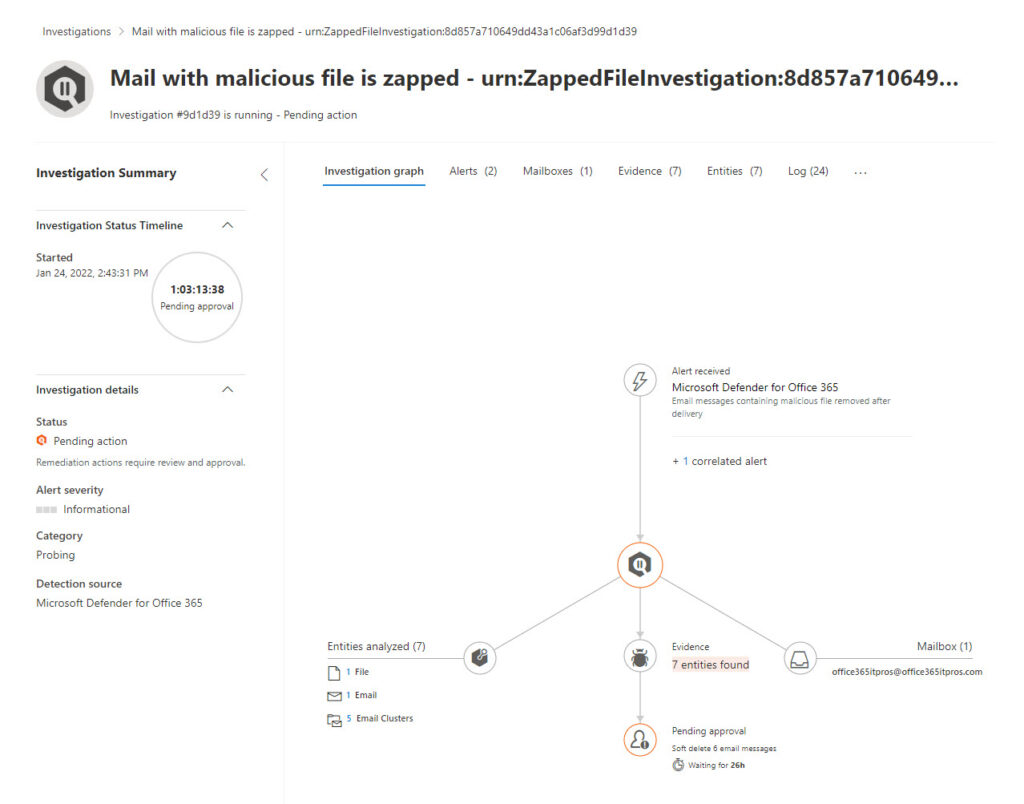
found the most interesting data to consider is the evidence assembled to decide that a message is problematic. Selecting the evidence tab, we see seven indicators that an issue exists (Figure 4). Taken together, the individual strands of evidence like the kind of content (in this case, a notification of direct deposit to a bank account), recipients, attachments, and signs of of known malware make the case that this message requires action.
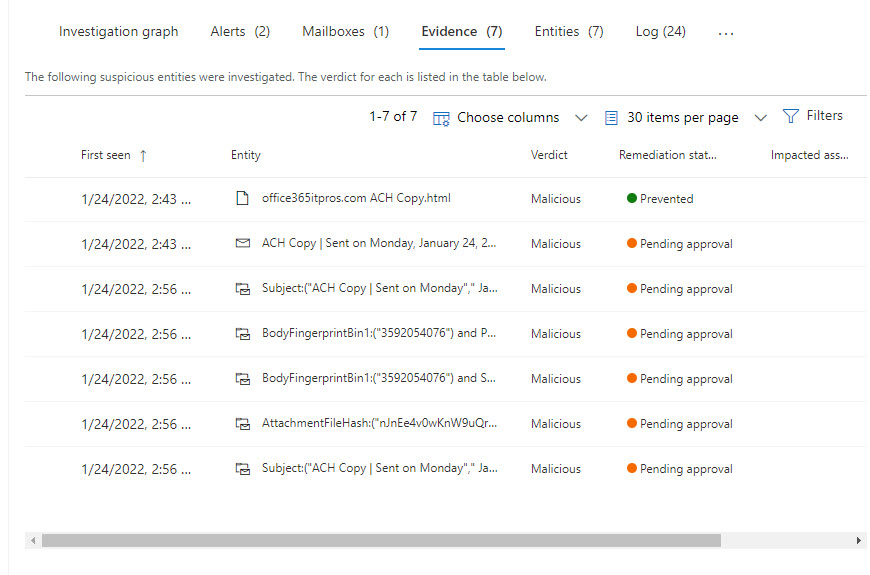
When AIR finds a problem message, it proposes an appropriate remediation action like removing copies of the message delivered to user mailboxes. AIR doesn’t take the remediation action until approval is given by a security administrator. You can see that all the evidence (“entities”) shown in Figure 2 are pending approval. To approve, you select one or all the entities, and approve the suggested action. My experience is that Defender takes some time to process approved actions, but they do happen eventually. In this case, because the message was a phishing attempt, the Zero-hour auto purge (ZAP) feature moved all copies of the message to the Junk Email folder without user intervention.
To validate that ZAP took care of the problem, you can run a content search to look for copies of the message using its subject and export the search results. Any detected messages should be in the Junk Email folder. If you want to remove these messages permanently, you can run a purge action for the content search.
Upgrading to Get Defender Plan 2
The capabilities available in Microsoft 365 Defender for Office 365 Plan 2 won’t justify the extra expense of moving to Office 365 E5. That decision has such a large cost implication for anything but a small tenant that many factors need to come together to create a compelling rationale for the expenditure. Every quarter, Microsoft emphasizes their success in moving customers to higher-priced plans, largely because customers want to use the compliance and security functionality available in Office 365 E5 and Microsoft 365 E5 tenants. Microsoft 365 Defender for Office 365 Plan 2 is just one of the pieces that assist Microsoft to sell customers on upgrades. Viewed in that light, it’s a good tool to have if you can afford the cost.




Hi,
Is it possible to disable logging for “GetMailPreviewUrl ” ?
This tool is awesome. Any idea where the saved queries go? I often have the same criteria I look for over and over again. I tried saving a query and checking the box for “track” but can’t figure out where it goes
Check under Defender > Email & Collaboration > Threat Tracker
thank you. couldn’t find anything from the docs regarding this basic info.
Hi Tony. Pardon me for asking a silly question. After apply Defender (Plan 2) for a small subset of my users, I’m still able to view email traffic for all my users from my admin portal. Is this a transitional oversight on microsoft’s end? Or am I mistaken. Strictly speaking I’d need to apply Defender (Plan 2) license to all users I want to see in explorer correct?
Is there a way to check or download a quarantined email attachment from the Defender portal? I am trying to check the attachment of a quarantined email without having to release it. Would Threat Explorer allow me do this? Thank you
Tony Whats a query that i can build to get external email accounts added to users outlook profiles ? We are trying to first see whats out there and then proceed to either white list or restrict adding external email account to outlook profiles
You mean for external email accounts added to Outlook desktop (Win32)? Those details are in the system registry of the PC…
How? I didn’t manage to find how email previewing and downloading can be monitored and alerted.
If Threat Explorer is used to to preview or download the content of an email, is this audit logged?
I don’t know, but it would be easy to check. Use Threat Explorer to preview or download a message, wait 30 minutes, and then run Search-UnifiedAuditLog to recover all events around that time. Then you can check to see if an audit event is present for those actions.
Hi Jeffrey, the Threat Explorer email preview or download is audit logged today under AdminMailAccess. Look out for these records: “GetMailPreviewUrl”, “DownloadEmail” or “DownloadHeaders”.
CloudAppEvents
| where ActionType == “AdminMailAccess”
| extend QuarantineAction = parse_json(RawEventData.ExtendedProperties.[0].Name)
| where QuarantineAction in (“GetMailPreviewUrl”,”DownloadEMail”)
Hello,
What is the KQL query to fetch the logs of URL clicks on emails on “Advance hunting” pane as the above explanation is totally on “threat explorer” pane and its pretty good, but we are looking to collect the events/logs of url clicks on emails from “Advance hunting” pane to some other Automation tools – XSOAR & Phantom.
Can you please help me with the query logic how to achieve that?
I am no KQL guru so I am afraid I don’t know the answer to your question.
Hi Tony,
where I can find out confirmation that Defender for Office 365 P1 is part of Office 365 E3 ? I could find that only in Microsoft 365 Business Premium. Are you sure that it is not a mistake ?
It’s confusing. https://docs.microsoft.com/en-us/microsoft-365/security/office-365-security/overview?view=o365-worldwide says:
The core of Office 365 security is EOP protection. Microsoft Defender for Office 365 P1 contains EOP in it. Defender for Office 365 P2 contains P1 and EOP. The structure is cumulative. That’s why, when configuring this product, you should start with EOP and work to Defender for Office 365.
and
If you have an Office 365 E3, or below, you have EOP, but with the option to buy standalone Defender for Office 365 P1 through upgrade. If you have Office 365 E5, you already have Defender for Office 365 P2.
So I need to correct the text. In my defense, Microsoft licensing is a real bag of worms… Just look at https://go.microsoft.com/fwlink/?linkid=2139145.
I have also noticed SCL and BCL is missing and opened up a ticket with Microsoft regarding this and they confirmed it is a known issue but that was months ago and still not showing up in tenants I manage…
It’s one of the joys of the cloud that software evolves at its own pace…