There are various tools available in Exchange Online to investigate messages tagged as Junk-Mail and spoof messages by Microsoft Defender for Office 365 or Exchange Online Protection (EOP).
This article reviews the most important tools, namely Exchange Message Trace, Threat Explorer, Message Header Analyzer, and Advanced Hunting. I also provide some practical advice about how to use Threat Explorer to investigate malware.
Exchange Message Trace vs. Threat Explorer
Message tracking is a crucial task for any Messaging Administrator trying to understand mail flow. It shows you what client or server created an email, and the servers an email transits until it reaches its destination. In Exchange Online, you can use the Message Trace tool to track or trace a message. If you want to get more insights about message tracking through the Message Trace tool, see this article.
When it comes to Junk-Mail, more information than message tracking information is needed. Thus, Message trace is no longer the best tool of choice. You need a tool that also provides you with some insights into the scanning, such as the X-Headers of the SMTP Header. For that reason, Microsoft created Threat Explorer – a tool to investigate why EOP considers an email Junk-Mail or Spoof. To outline the main differences between the two tools, here’s an overview:
- Exchange Message Trace allows you to have data available for message trace its route as email messages as they travel through Exchange Online. You can determine if a message was received, rejected, deferred, or delivered by the service. It also shows what actions were taken by EOP on the message before it reached its destination. Message Trace also allows you to search and trace messages, tracking data for up to 90 days. If you want to read more details, see this article.
- Threat Explorer is a tool to help you to investigate and respond to email threats:
- Find and investigate any malware detected by Microsoft 365.
- Identify the threat reason and what detection technology was applied.
- View phishing URL(s) of emails. A phishing URL is a fake website that should look like a legitimate website but wants to trick you into entering your personal information, such as passwords.
- Start an automated investigation and response process from a view in Threat Explorer.
- Investigate malicious email.
Threat Explorer also allows you to investigate messages for up to 30 days. For more on Threat Explorer, check out this article written by Tony Redmond.
Both Threat Explorer and Exchange message trace are in the Microsoft 365 Defender admin center. You need to be either a Global Administrator or Security Admin to use Threat Explorer, and a Security Reader to use Exchange message trace. Exchange message trace can also be directly accessed from the modern Exchange Admin Center (EAC).
Cybersecurity Risk Management for Active Directory
Discover how to prevent and recover from AD attacks through these Cybersecurity Risk Management Solutions.
The Two flavors of Threat Explorer: Real-time detections and Threat Explorer
Life would have been that easy if there was only one Threat Explorer tool available. However, I must tell you that there are also multiple flavors of Threat explorer available: The “full-features” Threat Explorer and the Real-time detections tool.
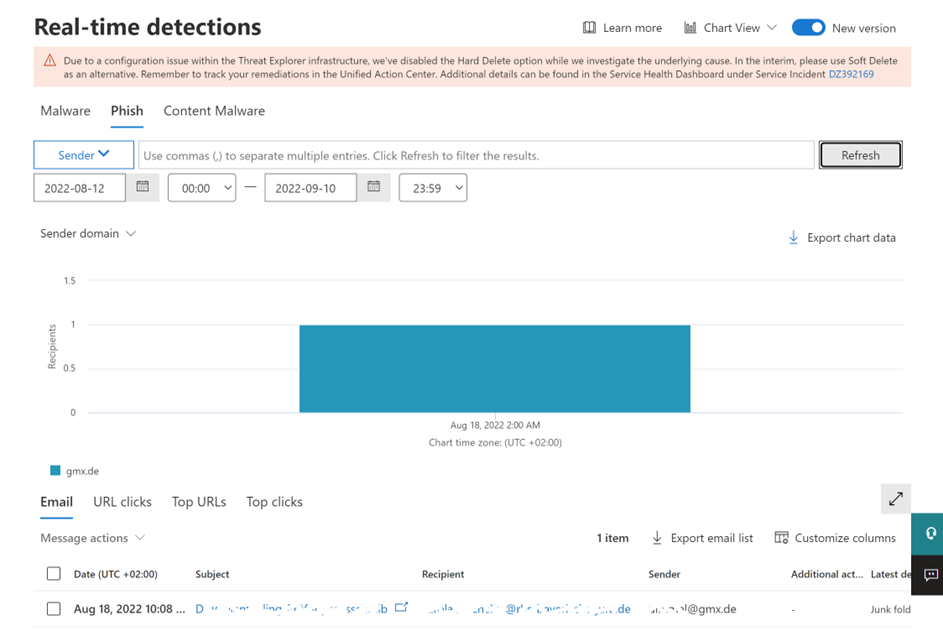
- Real-time detections (figure 1) allow you to view and analyze detections in real-time.
- Threat Explorer provides all functionality that Real-time detections offer, but even more: You can investigate all emails, not only phish or malware-detected messages, as seen in figure 2. It also allows access to your campaigns, namely coordinated email attacks, including phishing and malware, to test your users. And you can remediate threats (including triggering an Automated Investigation and Response investigation).
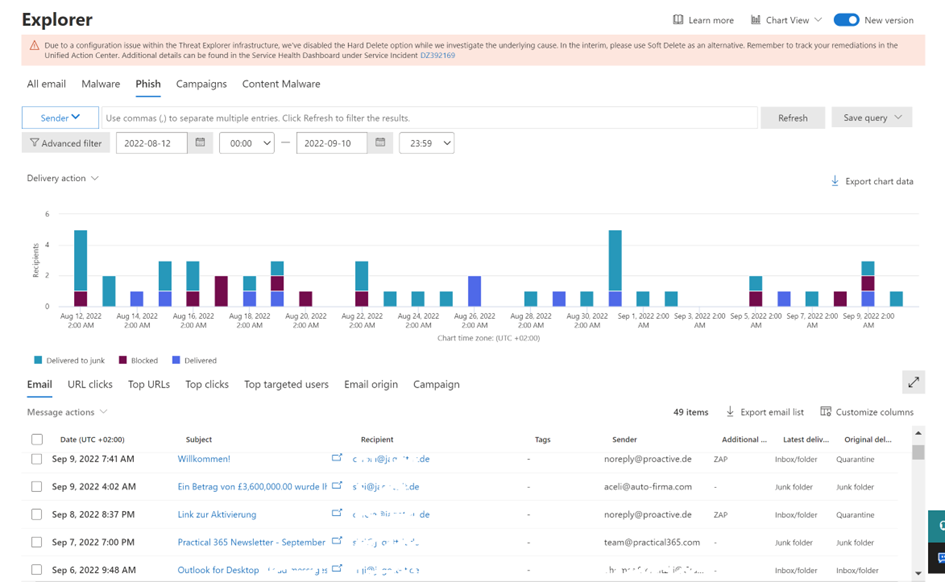
Depending on your Microsoft Defender for Office 365 plan (MDO), you will get the tool:
- MDO Plan 1 (included, for example, in the Business Pro or M365 E3 licenses) will give you the Real-time detections tool.
- MDO Plan 2 (included, for example, in the M365 E5 license) will give you the Threat Explorer.
Of course, MDO Plan 1 and Plan 2 are also available for purchase separately.
Using Exchange Message Trace and Threat Explorer to investigate Junk-Mail
Let’s look at how to investigate Junk-Mail.
The first step is to identify the message to investigate. The most common method is by searching for the message as part of an Exchange Message trace, or in Threat Explorer.
When using Exchange Message trace, click on the message to see delivery information for the message. To see why a message was filtered by Junk-Mail, click View message in Explorer on the right details pane to investigate the message in Threat Explorer (Figure 3).
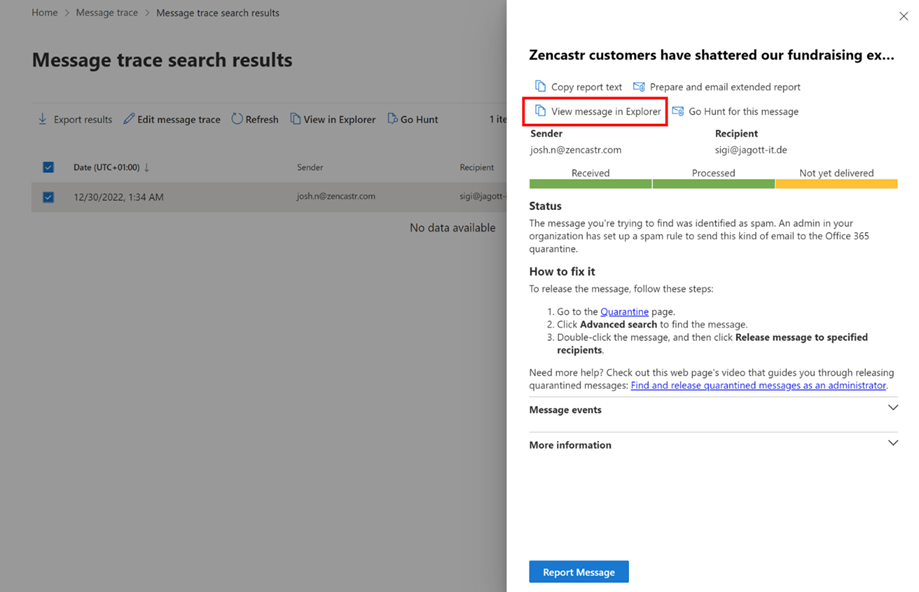
This option opens Threat Explorer in the Microsoft 365 Defender admin center to examine the message and its delivery details. It will also show you a summary of the delivery details, including Threats and Detection technologies (Figure 4).
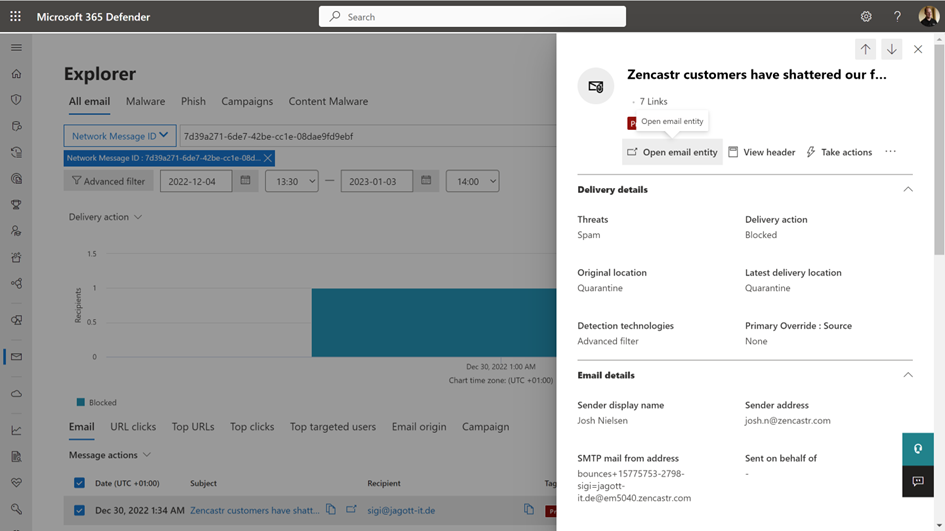
Most of the time, the overview does not give sufficient information to discover why a check performed by EOP, such as the Spam or Malware filter tagged the message. To dig deeper, click Open email entity to explore details.
Figure 5 shows that the message was scanned and considered SPAM by the Spam Advanced filter. The policy action section shows the name of the policy that tagged the message and the action invoked by that policy, which was to move the message to quarantine.
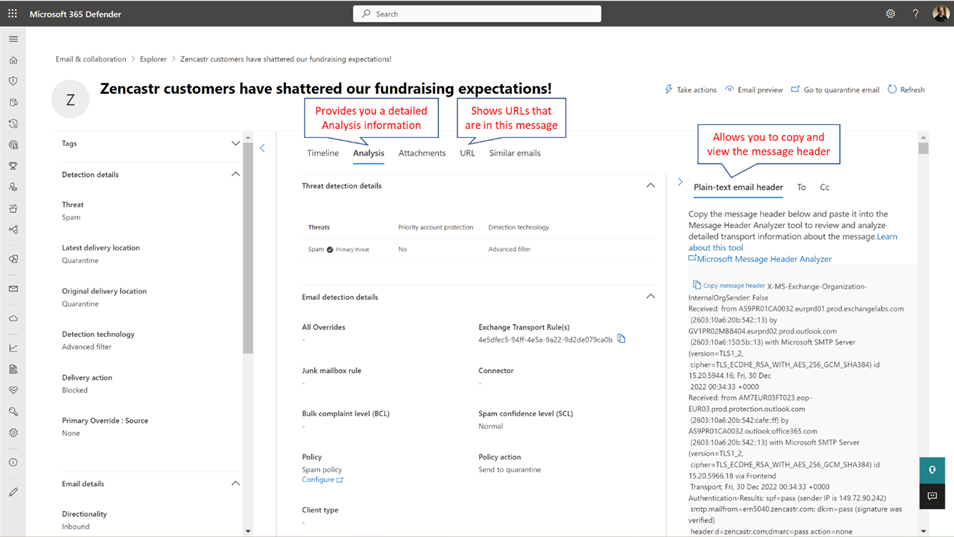
The Analysis tab provides you with the most interesting information about why the message was detected as malware or spam. The tab is divided into sections that provide you with the following information:
| Sections | What you find in this section | Best practices to look out for |
| Threat detection details | Lists all threats and their respective detection technology that apply to this message. | Identify the primary threat. If you have more threats listed here, the primary threat defines the action. As a rule of thumb: phishing threats rate higher than spam. |
| Email detection details | Lists details on Overrides, Mailbox rules, Connectors, Transport Rule(s) involved, Policy (including a link), and the Policy Action. | This section is the most important section as it will provide you with the most details. It shows you all Filter policies involved, and provides you with the Exchange Transport Rule(s) GUIDs of these policies. This allows you to use the Get-HostedContentFilterPolicy cmdlet to identify the policy responsible for the action. Note: It also should show you BCL and SCL levels, but in my environments, this did not work. The workaround for SCL is to run a Message Header Analysis. |
| Sender-Recipient details | Lists sender details, including sending IP, domain name, and creation details. | Look out for domain spoofing where the Sender domain is different to the P2 sender. |
| Authentication | Lists Internet Domain ownership authentication information, namely Domain-based Message Authentication (DMARC), DomainKeys identified mail (DKIM), and Sender Policy Framework (SPF). In addition, MDO calculates the Compauth 3-digit number using the From: domain as the basis for evaluation. Technically, it includes SPF, DKIM and DMARC to determine whether the message is authenticated. | This is an important section to identify any domain spoofing, especially when DMARC, DKIM and SPF are configured restrictive thus fail the checks. Understanding the Compauth result is also key, it can be pass, fail, softpass, or none. If it fails, you should look out for spoofing as the Sender domain might be different to the P2 sender (see Sender-Recipient details section). |
| Related entities | Lists an overview of attachments and links included in the message and if there are any threats found. | URLs that point to a different domain than the Sender domain might indicate that it’s a malicious message. |
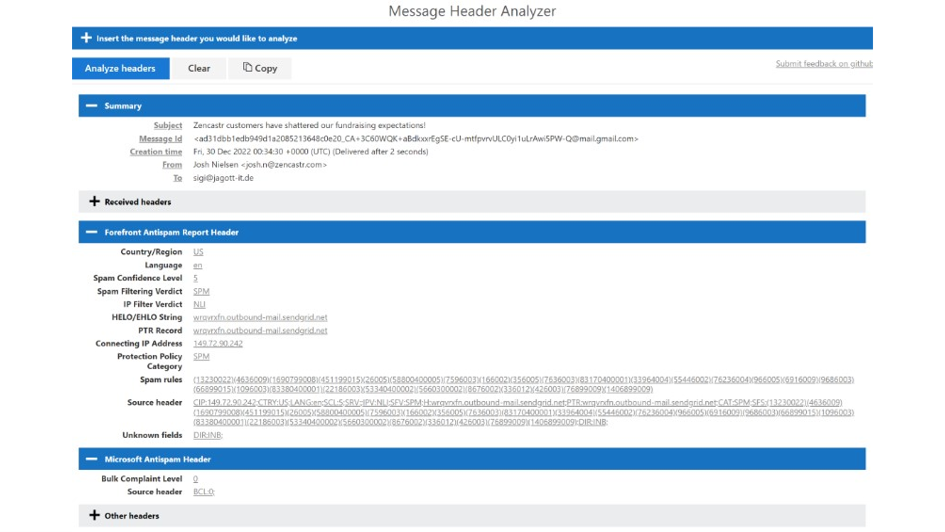
To support your investigation, you can also use the right pane of the Threat Explorer to expose the message header in plain text. It allows you to copy the header to paste it into Microsoft Message Header Analyzer (MHA), to expose SMTP header insights such as Spam Confidence Level and other details (figure 6). MHA is an add-on web-based tool, and its main function is to interpret and display message headers in a more consumable way.
What about Advanced Hunting?
In addition to the previously mentioned tools, you can also use Advanced hunting in Microsoft Defender for Office 365 admin center to investigate messages. Advanced hunting is probably the most advanced, expert-level tool to investigate messages. You can filter any messages, including searches of message content. Another advantage is that you can take action on your search results, so you can identify messages that were moved by EOP to the Junk-Mail folder and move these messages back to the users’ Inboxes.
Just scratching the surface
Understanding how to identify Junk-Mail and Spoof Messages is not an easy task. In the future, I might return to the theme to dive into the details of some of the topics discussed here, like using Advanced hunting. If you want to watch my discussions and demos on Junk-Mail filtering, a recording of my Microsoft Exchange Community (MEC) session “Use Advanced Message Tracking to identify Junk Mail or Spoofing” is online. Let me know what topics you’d like to hear about by posting a comment!
The Microsoft 365 Kill Chain and Attack Path Management
An effective cybersecurity strategy requires a clear and comprehensive understanding of how attacks unfold. Read this whitepaper to get the expert insight you need to defend your organization!





Awesome and informative post. Thanks for sharing.