Exchange Server 2010 makes use of SSL certificates for securing network communications between servers and clients. An example of this is Outlook Web App (OWA) which uses the HTTPS protocol for users connecting via their web browser (eg https://webmail.company.com/owa).
In this article:
- Introduction to SAN Certificates for Exchange Server 2010
- Enabling SAN Certificate Support for Windows Server 2003 Certificate Services
- How to Request a SAN Certificate for Exchange 2010
- Completing a Pending Certificate Request for Exchange Server 2010
Introduction to SAN Certificates for Exchange Server 2010
Traditionally SSL certificates were issued for a single name (such as the webmail name above), however this is very limiting because once an SSL certificate is bound to an IP address that IP address is not able to accept connections addressed to different names over SSL, or at least not without the name mismatch causing a warning message to the connecting client.
This became an issue for Exchange Server 2007 and 2010 because, depending on the server roles installed, the server may need to accept SSL connections to several different names such as:
- the server’s FQDN (eg ex3.exchangeserverpro.net)
- webmail and other published names (eg webmail.exchangeserverpro.net, mail.exchangeserverpro.net, mobile.exchangeserverpro.net)
- multiple DNS namespaces (eg autodiscover.exchangeserverpro.net, autodiscover.xyzimports.com)
Configuring multiple IP addresses, DNS records, IIS instances, and SSL certificates for all of the possible names in an Exchange organization would be tedious and expensive.
The X.509 certificate standard has catered for this for a long time now with a feature known as Subject Alternative Names. Basically this allows a single SSL certificate to be configured with a primary name and then multiple alternative names, making it valid for all of the required names that clients and other servers will be connecting to.
SAN certificates are available from most commercial providers however some organizations choose to issue them from their own private certificate authority. Windows Server 2008 Certificate Services supports SAN certificates by default, however Windows Server 2003 requires the option to be manually enabled first.
Enabling SAN Certificate Support for Windows Server 2003 Certificate Services
You can check an existing Windows Server 2003 CA for SAN support by using the certutil utility from a command prompt.
C:\>certutil -getreg policyEditFlags
HKEY_LOCAL_MACHINESYSTEMCurrentControlSetServicesCertSvcConfigurationcaPo
licyModulesCertificateAuthority_MicrosoftDefault.PolicyEditFlags:
EditFlags REG_DWORD = 15014e (1376590)
EDITF_REQUESTEXTENSIONLIST -- 2
EDITF_DISABLEEXTENSIONLIST -- 4
EDITF_ADDOLDKEYUSAGE -- 8
EDITF_BASICCONSTRAINTSCRITICAL -- 40 (64)
EDITF_ENABLEAKIKEYID -- 100 (256)
EDITF_ENABLEDEFAULTSMIME -- 10000 (65536)
EDITF_ENABLECHASECLIENTDC -- 100000 (1048576)
CertUtil: -getreg command completed successfully.
If there is no EDITF_ATTRIBUTESUBJECTALTNAME2 flag then you can enable it by running the following command.
C:\>certutil -setreg policyEditFlags +EDITF_ATTRIBUTESUBJECTALTNAME2
SYSTEMCurrentControlSetServicesCertSvcConfigurationcaPolicyModulesCertifi
cateAuthority_MicrosoftDefault.PolicyEditFlags:
Old Value:
EditFlags REG_DWORD = 11014e (1114446)
EDITF_REQUESTEXTENSIONLIST -- 2
EDITF_DISABLEEXTENSIONLIST -- 4
EDITF_ADDOLDKEYUSAGE -- 8
EDITF_BASICCONSTRAINTSCRITICAL -- 40 (64)
EDITF_ENABLEAKIKEYID -- 100 (256)
EDITF_ENABLEDEFAULTSMIME -- 10000 (65536)
EDITF_ENABLECHASECLIENTDC -- 100000 (1048576)
New Value:
EditFlags REG_DWORD = 15014e (1376590)
EDITF_REQUESTEXTENSIONLIST -- 2
EDITF_DISABLEEXTENSIONLIST -- 4
EDITF_ADDOLDKEYUSAGE -- 8
EDITF_BASICCONSTRAINTSCRITICAL -- 40 (64)
EDITF_ENABLEAKIKEYID -- 100 (256)
EDITF_ENABLEDEFAULTSMIME -- 10000 (65536)
EDITF_ATTRIBUTESUBJECTALTNAME2 -- 40000 (262144)
EDITF_ENABLECHASECLIENTDC -- 100000 (1048576)
CertUtil: -setreg command completed successfully.
The CertSvc service may need to be restarted for changes to take effect.
Next you must restart Certificate Services for the change to take effect.
C:\>net stop certsvc The Certificate Services service is stopping. The Certificate Services service was stopped successfully. C:\>net start certsvc The Certificate Services service is starting. The Certificate Services service was started successfully.
The server is now ready to issue SAN certificates.
How to Request a SAN Certificate for Exchange 2010
The next step is to create a certificate request from the Exchange server. You can perform this task from the Exchange Management Shell, or from the console.
For an example of the Exchange Management Console steps see the previous article here.
From the Exchange Management Shell use the New-ExchangeCertificate cmdlet to generate a certificate request. In this example I am requesting a certificate with the following attributes:
- A friendly name of “Exchange 2010 Certificate”
- The server’s FQDN
- The alternative names of mail.exchangeserverpro.net, autodiscover.exchangeserverpro.net, and webmail.exchangeserverpro.net
I’m also using -GenerateRequest to create a certificate request rather than simply creating a self-signed certificate.
[PS] C:\>New-ExchangeCertificate -FriendlyName "Exchange 2010 Certificate" -IncludeServerFQDN -DomainName mail.exchangeserverpro.net,autodiscover.exchangeserverpro.net,webmail.exchangeserverpro.net -GenerateRequest -PrivateKeyExportable $true
The command will output a certificate request that looks similar to this.
-----BEGIN NEW CERTIFICATE REQUEST----- MIIEPDCCAyQCAQAwJTEjMCEGA1UEAwwabWFpbC5leGNoYW5nZXNlcnZlcnByby5u ZXQwggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQCnbhSAM0y26udUo/+8 yvufXrv0AcuzcLYc/9wxNjgOZjmkQUqXEvrxXXrIzCciWL1KDTYjJyVXNkjqCsB3 8tdLWS7tLR/OLj0Px7bsUkTuJKl95DeYGJwxginMjvVKrdxMkPJloWY6i+5ZzHfs jhK0+bboyaoQMopwnya7AK0H5AfSDUd+hFzbgpX8hdj7hkMVwCS257/fsNkoJbxA xC7C9Yk06onHypefiz+uTubNULjKBKdtJiyesj6hakyG1tFddsvv6yqwjtAefyVZ vYWbkSJiXTwALuOrePlt3wGa12ZxqYwl2Mf98gdb2fTq2M6TosPE0PIxoDZvBzV2 IHZxAgMBAAGgggHQMBoGCisGAQQBgjcNAgMxDBYKNi4xLjc2MDAuMjBlBgkrBgEE AYI3FRQxWDBWAgEFDBtFWDMuZXhjaGFuZ2VzZXJ2ZXJwcm8ubG9jYWwMEEVYQ0hT RVJWUFJPXEVYMyQMIk1pY3Jvc29mdC5FeGNoYW5nZS5TZXJ2aWNlSG9zdC5leGUw cgYKKwYBBAGCNw0CAjFkMGICAQEeWgBNAGkAYwByAG8AcwBvAGYAdAAgAFIAUwBB ACAAUwBDAGgAYQBuAG4AZQBsACAAQwByAHkAcAB0AG8AZwByAGEAcABoAGkAYwAg /wQEAwIFoDCBhQYDVR0RBH4wfIIabWFpbC5leGNoYW5nZXNlcnZlcnByby5uZXSC ImF1dG9kaXNjb3Zlci5leGNoYW5nZXNlcnZlcnByby5uZXSCHXdlYm1haWwuZXhj aGFuZ2VzZXJ2ZXJwcm8ubmV0ghtFWDMuZXhjaGFuZ2VzZXJ2ZXJwcm8ubG9jYWww DAYDVR0TAQH/BAIwADAdBgNVHQ4EFgQUbaUvsgyyRXS0lEHebbnvEqpd7VwwDQYJ KoZIhvcNAQEFBQADggEBAEQ5GtxZGMf3rw+gGuIj+A8exB7bM2aSg9Z9X6RyNtHX 3iuCHPEOUdkZFSTR3CWoMal1FcH/r1yzCPXKTWDtyMIzi4tiHA/+V2nXALhH6Fbv c8G0l47iIGlbvuBkBDTxhmLubXgXGAp1dRfwRXd1Vqy0eDe/0LxlUAwq+Kb/RRLw UaUf3eVrbQUpWNqEmLcorp3mpwnoqAB+GhP+j0ERCquP629xdlHS2yz3fNfn4xGU Sv/i5FLUf6WmVJu+kjQ50wlh5nE+XiwQmsta0MNUnqIXu9dDXnOpx+VdmuKdEXlh /zAHMofanelZ/UUBv7mdwMG3E5U17nJ/VoiIAZAygg0= -----END NEW CERTIFICATE REQUEST-----
Copy the output to your clipboard for the next steps.
Open your web browser and navigate to the web enrollment URL of your Certificate Services server (eg http://ca-server/certsrv). Click on Request a Certificate. Note if you are running a Windows Server 2003 CA you may need an update to the web enrollment pages before you can proceed any further.
 Choose Advanced Certificate Request.
Choose Advanced Certificate Request.
 Choose to Submit a Certificate request…, because we’ve already generated the request on the Exchange server earlier.
Choose to Submit a Certificate request…, because we’ve already generated the request on the Exchange server earlier.
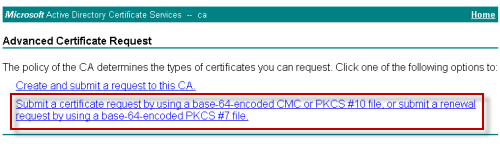 Paste the generated certificate request data into the form, and choose Web Server as the certificate template. Click Submit to continue.
Paste the generated certificate request data into the form, and choose Web Server as the certificate template. Click Submit to continue.
 When the certificate has been issued download the certificate file to your Exchange server.
When the certificate has been issued download the certificate file to your Exchange server.
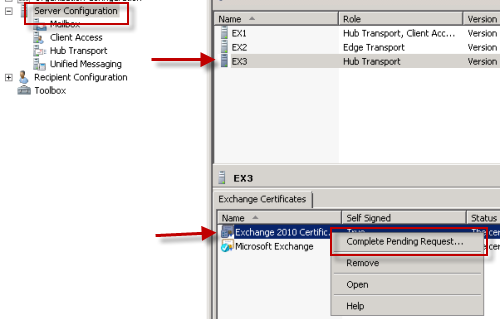
Completing a Pending Certificate Request for Exchange Server 2010
The certificate has been issued and downloaded, and now the pending certificate request needs to be completed for Exchange Server 2010.
Launch the Exchange Management Console, navigate to Server Management, and choose the server that you imported the certificate to. Right-click the new certificate and choose Complete Pending Request.
Browse and select the certificate file that was downloaded, and the continue to complete the wizard.
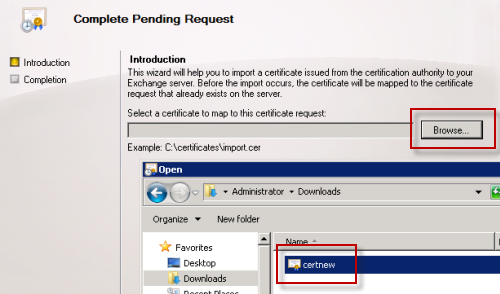
The certificate has now been installed and is ready to be assigned to Exchange services.
If you encounter an error message stating that “The certificate is invalid for exchange server usage” then see this article for the solution.




Hi Paul,
I have followed this guide to generate the Certificate from Private CA, I have also sucessfully Exported this Certificate to Exchange server and as well as assigned the Services to the certificate also.
all seems to be working fine and my Internal User doesnt even realize any changes. but today i have just check the properties of my Certificate and in the certificate information, it only shows,
This Certificate is intended for the following Purpose(s):
> Ensure the identity of a remote computer.
is it correct or i have exported the wrong certificate.
thanks
Please help
Very useful article
Hello Paul,
I have read a few of your articles to help understand Exchange better being new to it. I have a question and you may have to explain it to me like I’m 5. I am trying to deploy O365 in our environment and running into road blocks with Exchange, DNS and certs. I inherited Exchange and the setup looks different that what has been described in most books. It looks like we have the same issue you are describing but unsure of how to resolve because of the slight differences. Ok we are a gov agency ( I changed info for obvious reason):
internal domain is: citizens.gov
mail server is: mail.citizens.gov
Our MX record is mapped to mail.citizens.state.gov
Exchange cert is owa.citizens.state.gov — no SANs attached.
We have 2 DNS Forward Lookup Zones: citizens.gov and citizens.state.gov
We have a few problems:
1. A name mismatch error certificate error recently starting appearing saying mail.citizens.gov is not on certificate.
2. I need to reconfigure my certificate to include all necessary SANs for O365. Not sure what all should be included. Should I include:
autodiscover.citizens.gov, autodiscover.citizens.state.gov, owa.citizens.state.gov, mail.citizens.state.gov, mail.citizens.gov
3. This has stalled the O365 migration as DNS and certs have to be set up properly.
In regards to issue 1, I believe that issue will be resolved once I get the certificate issue resolved. However I am not sure if I should put/able to put the internal names on the cert like (anyname).citizens.gov. Should i resolve this with DNS if so what records would I need?
I have to generate a new cert with SANs. What should be included? do I need to put
Thanks! This is exactly what I needed.
Pingback: iphone unlocking in rolling meadows
Hey Paul,
Quick question. Have you ever seen a situation where you issue an SSL cert from a CA server on MS Server 2008 with the SAN information, but then once you try to access the FQDN from a web browser you get an error. On the bad cert there is no more SAN field and the error message is “mismatched address?”
Anything would help!!
No SAN info on the cert? Perhaps the wrong cert is being used. Have you checked that the correct cert has been enabled in Exchange?
Paul ,
I have one just like it ( http://faragesolutions.files.wordpress.com/2013/04/proxy.jpg?w=650 ) scenario . Using two Exchange , only one of them is accessed as a proxy .
In Exchange that is facing internet , I use a digital certificate with the public domain ( webmail.name.com ) and my OWA is configured to ( External: webmail.name.com ) and (Internal : webmail.name.com ) .
You Exchange that are not face to internet , OWA is configured to ( External: empty) and ( Internal : servername.local ) . This Exchange user when connecting with Outlook client is generating validation error name ( servername.local ) , because as I’m using the same Exchange certificate that is facing internet . So the audience is trying to validate the certificate name that is not registered as an alternative name.
question : the exchange that is not facing the internet, I need to use the same public certificate that is in exchange that is facing the internet? or can I just use an internal certificate?
Thank you.
Pingback: How to generate a SSL certificate for Exchange 2010 Pacific Technologic Systems
Thanks for this Paul!
I was getting a bit confused as to why after completing the previous request I had (using a technet guide) my cert was disappearing from Exchange.
However – Your guide was much clearer, and worked first go!
Hello
I set up two CAS servers in NLB mode
cas1.domain.local
cas2.domain.local
and the name of NLB: mail.domain.local
Do I put the netbios name server if the certificate SAN, or I will just put the name of nlb: mail.domain.local
thank you
The intro section of this article explains which names to include. I’d recommend you read that.
The NLB cluster name doesn’t need to be included. Neither does the CAS Array name (which is not necessarily the same as the NLB cluster name, though they can be the same). The names that need to be included are any that clients will be connecting to over HTTPS.
Great post again Paul.
I have a certificate issued by Verisign that will be expiring soon. Since I have no external facing services there doesn’t seem to be any point in paying for renewal. Is it safe to simply allow the existing cert to expire and issue one from my CA to “replace” it, following the above instructions?
Don’t wait for it to expire. If it expires clients will begin showing certificate validation errors to your end users. You should replace it before it expires.
Yes, if you choose to go with a private CA you can follow the instructions above to provision the cert, then make sure you also enable it for the services previously associated with the old cert.
Hello, I followed this article because my client with Exchange 2007 has an internal domain name of cjn.com but they do not own cjn.com so I cannot get a UCC cert from GoDaddy to cover the FQDN of their exchange server. Consequently, users get an SSL error every time the open Outlook.
I installed a Certificate Services server and followed your article. Now, users no longer get the SSL error when they launch Outook, but IE complains about the cert when they go to OWA:
“The security certificate presented by this website was not issued by a trusted certificate authority.”
Is there anyway around this? Once again, this is Exchange 2007 not 2010.
Thanks!
Thanks Paul, all your articles make my life with exchange bliss m8
Hi
I would like to follow the steps mentioned in the article above to issue a new certificate from my own server…
My Exchange server is a member server. Can I install the AD Certificate Services on the Exchange Server (eg a member server) or is it better to install the Certificate server on the DC ?
hi Paul,
thanks for your help, now the certificate is not self signed..that’s fine but it apears with in red meaning that the server coundn’t find the revocation list, wich i importe from my CA and install it on the server BANK certificat but still havin’ the problem
regards
hi,
i have two DCs and a domain wich my user’s trust :DC1, DC2 i found a CA on the DC2 but my exchange organisation is on a diffrent domain with two mailbox on DAG and CAS Hub and two DCs but no CA on this domain
my problem is that when i tried to generate a certificat on my CAS as shown on steps and sign it on the CA that my user’s trust, the certificat request is always keeping peending and self signed.
MY ORGANISATION:
DC1
DC2 with CA on it
EXCH_DC1
EXCH_DC2
EXCH_CAS
EXCH_MBOX1
EXCH_MBOX2
The certificate request will remain pending until you download it from the CA and complete the pending request.
i did it and on may way for that it was all “green” it seems to be correcte, but unfortunetly the certificat is still peending and self signed 🙁
i have 2 physical separate sites as two child domains US.acme.com and the other as IN.acme.com. The user base is present in these two domains. The exchange is installed on the root domain (Acme.com).Now i want to go with one single certificate for exchange 2010(not the wild card). I want to ensure that US users connect to the US Exchange(CAS+HT+MB) and India Users connect to the India EXchange(CAS+HT+MB). The question is should i have two separate autodiscover entry in the SAN or is it possible or necessary? And if it only requires one entry, i need to understand how the autodiscovery works for a user who sits externally to connect to the mail server. In the sense what mechanism takes place to ensure that the user connects to the right CAS server.
Hi,
I am in the same situation.
Certificate MisMatch OR Outlook …. proxy server…Error 8, works fine when connect through VPN or internal LAN. IMAP & POP is working fine.
Exchange Test says the same thing.
The site has SBS 2011, Exchange 2010, Outlook 2010 external client and NO Public SSL yet.
I realised there is no entry for Autodiscover.EXTERNALDOMAIN.NAME (e.g. autodiscover.contso.com) on the certificate created by SBS. How would I add a domain to current certificate?
I am unable to issue a new certificate as certsrv is not loading.
Strangly, outlook is pulling all the information from Server externally.
Any experience ?????
Providing the exact error message in full would be a big help here.
Hi Paul, thank you or this very valuable article.
Some users would like to access to Outlook Web Access from a computer ouside of the domain and dns.
So they access by ipaddress, not by the fqdn: https:///owa.
It works fine but they still have certificate error , even when i put the ipaddress as an Altrnative Name (SAN).
But if they update their host file and access to OWA by he fqdn it works.
What could be the problem? Is it possible to access to owa url by ipadress without having certificate issue?
hanks
Romain
You should create a public DNS record for OWA and have your users use that.
Note that recent changes in the rules governing how SSL certs are issued means you won’t be able to get certs for IP addresses or short names (eg “owa”) in the very near future.
Better off doing it the right way right from the start 🙂
what can i do to start useing Outlook for remote users and other servides which require trusted certifficates
I successfully created a new Exchange 2010 SP2 certificate. Downloaded and installed the certificate as per GoDaddy kb. After I had successfully completed the “Complete Pending Request” I dont see the new certificate in EMC. The only certificate I can ses is the first “Microsoft Exchange” certificate which gets automaticly installed while installing MS Exchange. My Exchange 2010 SP2 runs on second 08 R2 Ent server.
So in the EMC you created the certificate request, and were able to see the pending certificate request, but then it just disappeared when you completed it?
thats correct, I can still see the first certificate “Microsoft Exchange” which is the self signed certificate but not the one which I had created and used it to purchase a Godaddy cert and later cant find in EMC after completing pending tasks.
This is my fifth exchange 2010 deployment this year but first with SP2 and I had never had this issue in any version of exchange earlier
Interesting.
Run MMC and add the Certificates snapin for Local Computer, and see if you can see the cert in the Personal/Certificates store there. If not, its possible it has somehow been deleted.
I just experienced the same problem as Fazlin. I looked here -> “Run MMC and add the Certificates snapin for Local Computer, and see if you can see the cert in the Personal/Certificates store there.”
I have done this and can see the default Microsoft Exchange cert for Server Authentication, as well as my new cert for Server and Client Authentication. Any hints on what has happened here or how I can resolve this?
Same problem here. I can’t believe it just disappeared!!! no error messages or anything. As John says it is in the Personal cert store along with the self signed original exchange one. I guess the only non standard thing about my set up is that I am in the process of migrating from exchange 2007 to 2010. Any ideas on how to get this cert back into exchange so I can assign services to it??
Hi, great article. Just in case it helps anyone, I had this exact problem. However it was my fault for not selecting ‘Web Server’ when I requested the certificate.
I had this exact issue too, following the go daddy KB. when importing the cert into the ” intermediate root certification I change the file search to *.* and I clicked on the .cer extension, then went to EMC and then picked it again, IE the .cer extension. The proper way is to pick the PK7 extension of the certificate files you get when importing the certificate in certificate snapin, and then the .cer when in the exchange server. Otherwise, it literally just… poof… gone. You will have to REKEY the cert because you will not have the “finish pending request” in exchange. Hope that helps everyone. p.s. I don’t know much about this, I just thumble my way through 🙂
Pingback: How to Issue a SAN Certificate to Exchange Server 2010 from a Private Certificate Authority « Raydha's Blog
Pingback: Exchange ActiveSync/Windows Phone Outlook Error 80072F0D
Pingback: Publishing Exchange 2010 Outlook Web App with ISA Server 2006
Pingback: Exchange Server 2010 SSL Certificates
Hi Paul,
Can you tell me how to generate and assign certificate for multiple CAS server exchange 2010. Further i would like to know if i generate certiifcate from private CA and assign it to CAS server is it ok
CAS server name CAS1 & CAS2
domain name which will be used for all the services is : mail.domain.com
Hi Amit, you can do it a few different ways. Either generate a separate cert for each server, or do one cert request that includes all of the CAS server FQDNs in it. You can then export the cert from the first server you install it on and import it into the other(s).
Hi paul.
i bought a SSL certificate from verisign for my exchange 2010 and it working fine when i use owa but am having a certificate mismatch error every time i open my outlook 2010 form computer that is joined to the domain
Hi Lukman, so the certificate warning box you see pop up specifically says the names don’t match?
Did you buy a SAN cert (ie multiple names) or a single-name SSL cert?
Hi Paul,
the certificate i bought was a single-name SSL cert.
but the warning i see is only on outlook
Can a Windows 2003 Standard edition CA issue certificates with SAN? For our test environment we’d like to issue the certificates from our internal CA but it’s based on Windows 2003 Standard and I have not been able to find this information. Is a Version 2 template required to issue a certificate with a SAN or can Version 1 templates work too?
Hello Paul;
Just looked at this article which was great to learn how to make an exchange certificate. Just to add in the note for this article for how to find the output a certificate request that was made in the MMC exchange console is the following:
1) Right-click the exchange certificate file which is the .reg extension.
2) select open with or open
3) open using notepad and there you will find all the information per example below:
—–BEGIN NEW CERTIFICATE REQUEST—–
xC7C9Yk06onHypefiz+uTubNULjKBKdtJiyesj6hakyG1tFddsvv6yqwjtAefyVZ
vYWbkSJiXTwALuOrePlt3wGa12ZxqYwl2Mf98gdb2fTq2M6TosPE0PIxoDZvBzV2
IHZxAgMBAAGgggHQMBoGCisGAQQBgjcNAgMxDBYKNi4xLjc2MDAuMjBlBgkrBgEE
AYI3FRQxWDBWAgEFDBtFWDMuZXhjaGFuZ2VzZXJ2ZXJwcm8ubG9jYWwMEEVYQ0hT
RVJWUFJPXEVYMyQMIk1pY3Jvc29mdC5FeGNoYW5nZS5TZXJ2aWNlSG9zdC5leGUw
—–END NEW CERTIFICATE REQUEST—–
From: Rick.C
Hi, everybody! i need your help, Powershell show this error when runing with “certutil -setreg policyEditFlags +EDITF_ATTRIBUTESUBJECTALTNAME2” command: Certutil: -setreg command failed: 0x8007000d, Certutil: The data is invalid
How i can fix this?
Are you copy/pasting the command from a web page, or typing it out yourself?
No, type it out myself…. but on command promt cetutil is runing without troubles, now, another problem, Exchange SA service is not running automatically and test -servicehealth command shows Mailbox Server Role: False, how i can fix this problem?
Pingback: EXCHANGE 2010: Certifcate with mutiple DNS names (private windows CA) | www.gobien.be
Pingback: Deploying Exchange 2010 SP1 in Hosted Mode, Part 1 | Memphis Technical Network
Hello, thanks for your articles about SAN certificates. I have a Q about SAN names. In the real world, SAN certificate for Ex 2010 must includes these names in cert : in the case of internal and external domain
– server FQDN (server.company.local)
– name for webaccess for external users (webmail.mycompany.com)
– name for autodiscover (autodiscover.mycompany.com)
– name for webaccess for internal users (webmail.mycompany.local)
And netbios name of server (for example “server”) is needed too ? I have read many artciles, some says you do not have to include netbios name, some articles says you have to include the netbios name.
So what about netbios name in the SAN ?
Thanks for reply.
Netbios would be needed if you plan to have your internal users hitting OWA (for example) by using the server’s Netbios name. As long as they’re hitting the FQDN then no need to include the Netbios name.
Pingback: Lync – OWA integration contacts are grey and cannot sign in IM | Exchange DUDE
What about the private key. I thought that had to be exportable when you did an Exchange Self Signed Certificate?
This article doesn’t describe a self-signed cert, it describes how to issue a cert to Exchange from a private CA.
i have installed En root CA on my Additional AD (windows 2008 r2), do you recommend it?
i just install Exchange 2010 sp1.
And i failed to issue certificate by the CA console and Web enroll, in the web enroll i cant select “web server” in certificate template. only contain “user” and “basic EFS”.
i had tried by issuing certificate request by Exchange 2010 EMC and EMS.
What can i do to over come this?
You can use your own CA if you like it just means non-domain members will not trust the CA until you deploy the root certificate to them.
If you’re not seeing the web server template I’d say your account doesn’t have permissions to request that type of cert.
Hi again, I’ve applied the new SAN certificate (created a new CA on the CAS with Windows Server 2008 R2 and issued a certificate) and assigned services (IMAP/POP/IIS/SMTP) , all worked fine for my domain joined PCs but a pc with Outklook 2010 says “the security certificate was issued by a company you have chosen not to trust “.
Can you help with this? Thanks.
your machines or users with outlook 2010 have to trust the publisher of the certificate. you can use group policy to publish the CAS’s “root certificate” to the “trusted publishers” certifcate store. outlook 2007 did not throw this error for self-signed or untrusted certificates. if the problem pc is not a domain pc, you can manually put the root certificate into trusted publishers on that pc with the Certificates mmc console.
Pingback: Возможно вы незнали, что … » Архив Блога » публикуем Outlook Web App в ISA Server 2006
Pingback: Configure an Exchange 2010 SSL Certificate
i don’t get the “begin new certificate request”/”end new certificate” text output after i run the new-“exchangecertificate … -generaterequest” command. i just get a thumbprint.
Thumbprint Services Subject
———- ——– ——-
C527BEEE14788799C6C602AAF7D6DEBFDA8509D0 …… CN=sisexcp9.student.dom
i ran the command on an exchange 2010 sp1 server running on 2008 r2.
Hi Curtiss, if you’re having problems with the shell try using the console to generate the cert request instead. Steps are here:
https://www.practical365.com/configure-an-ssl-certificate-for-exchange-server-2010
Pingback: Autodiscover and SSL Warnings during Exchange 2010 Migration - Exchange Server Pro
I was stuck with the Certification server policy. That worked also for Windows Server 2008 CertSrv.
Thank you. I’ll reference this doc in my blog.
Pingback: How to Issue a SAN Certificate to Exchange Server 2010 from a Private Certificate Authority « Alan's sysadmin Blog