In all my years as an Exchange Server administrator the most common “whodunnit” scenario is being asked to find out who sent a specific message from a shared mailbox.
Consider a scenario where a shared “Help Desk” mailbox is used by a reasonably large team of IT staff, and they all have Send As permissions for the mailbox (for legitimate purposes such as sending out system outage and maintenance notifications).
One day a help desk operator has a brain fart and sends an email to the whole organization that causes some bad feedback.
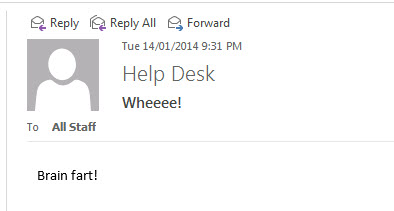
Youve been tasked with finding the culprit and there are a few angles of investigation that you’re considering, such as finding the IP address that submitted the message and tracing that back to a workstation, trawling through sent items of help desk staff, or even just flat out asking people (this one works sometimes, don’t rule it out).
It would be a lot easier if Exchange could just tell you who sent the message.
The good news is that Exchange Server can tell you this (in Exchange 2010 SP1 or later, and Exchange 2013), using a feature called mailbox audit logging. The bad news (if you can call it that) is that the feature is not enabled by default, and needs to be turned on *before* the email is sent to capture the action in the audit log.
So, assuming mailbox audit logging is already enabled for the Help Desk mailbox, we can perform an audit log search to find out who took the Send As action at that time.
Performing Mailbox Audit Log Searches Using the Exchange Admin Center
In the Exchange admin center navigate to Compliance Management and choose Auditing. There are several items in that section but we’re interested in “Run a non-owner mailbox access report” in this case.
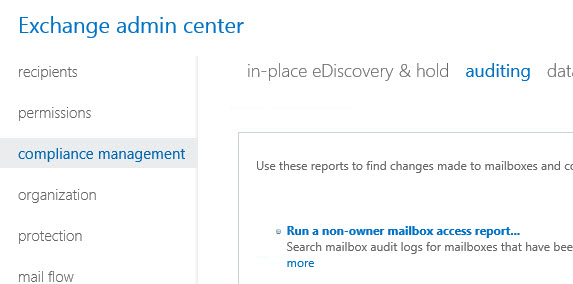
Set the date range you’re interested in, and then click on Select Mailboxes to add the specific mailbox you want to search. Finally, set the search type to “All non-owners”, and then click Search to begin.
After a few moments your search results should appear. If you’ve picked a large date range, or a mailbox with a lot of non-owner activity, then you may have quite a lot of results to scroll through.
But for this example we can see that someone has in fact performed a “Send As” on the date in question, with the matching subject line of the email that causes all the fuss to begin with. So it seems we have our culprit, caught red handed, thanks to mailbox audit logging.
Performing Mailbox Audit Log Searches Using the Exchange Management Shell
Naturally we can also perform this search using PowerShell and the Search-MailboxAuditLog cmdlet.
For example, to search the “Help Desk” mailbox audit logs between the 13th and 15th of January 2014, the following command is used.
[PS] C:\>Search-MailboxAuditLog -Identity "Help Desk" -LogonTypes Delegate -StartDate 1/14/2014 -EndDate 1/15/2014 RunspaceId : d8142847-166a-488a-b668-f7b84c3f3ceb MailboxGuid : a0f10db1-5268-47a5-8f71-d1e65f55c653 MailboxResolvedOwnerName : Help Desk LastAccessed : 14/01/2014 9:31:08 PM Identity : exchange2013demo.com/Company/Resources/Help Desk IsValid : True ObjectState : New
We can see a result, and the time stamp matches the email message that was sent, but little else is shown about the event. To see more we need to use the -ShowDetails parameter.
[PS] C:\>Search-MailboxAuditLog -Identity "Help Desk" -LogonTypes Delegate -StartDate 1/14/2014 -EndDate 1/15/2014 -Sho
Details
RunspaceId : d8142847-166a-488a-b668-f7b84c3f3ceb
Operation : SendAs
OperationResult : Succeeded
LogonType : Delegate
ExternalAccess : False
DestFolderId :
DestFolderPathName :
FolderId :
FolderPathName :
ClientInfoString : Client=MSExchangeRPC
ClientIPAddress : 192.168.0.181
ClientMachineName :
ClientProcessName : OUTLOOK.EXE
ClientVersion : 15.0.4551.1004
InternalLogonType : Owner
MailboxOwnerUPN : Sarah.Jones@exchange2013demo.com
MailboxOwnerSid : S-1-5-21-2175008225-1847283934-4039955522-1471
DestMailboxOwnerUPN :
DestMailboxOwnerSid :
DestMailboxGuid :
CrossMailboxOperation :
LogonUserDisplayName : Sarah Jones
LogonUserSid : S-1-5-21-2175008225-1847283934-4039955522-1471
SourceItems : {}
SourceFolders : {}
SourceItemIdsList :
SourceItemSubjectsList :
SourceItemFolderPathNamesList :
SourceFolderIdsList :
SourceFolderPathNamesList :
ItemId :
ItemSubject : Wheeee!
DirtyProperties :
OriginatingServer : E15MB1 (15.00.0775.022)
MailboxGuid : a0f10db1-5268-47a5-8f71-d1e65f55c653
MailboxResolvedOwnerName : Help Desk
LastAccessed : 14/01/2014 9:31:07 PM
Identity : RgAAAAD2fF/dZobvQoWbbV7P6N7eBwD7Y5OF+DDRQZRz1a4+yUyzAABaldDBAAD7Y5OF+DDRQZRz1a4+yUyzAAB
aldDCAAAJ
IsValid : True
ObjectState : New
As you can see we get the same information that reveals the sender of the email message, as well as some extra info that may be useful as well.
Summary
In this article I’ve used a common scenario to demonstrate the value of mailbox audit logging, as well as demonstrating how to perform simple mailbox audit log searches. Hopefully by now you can see the value of mailbox audit logging and are considering enabling it in your organization, even if only for your most important/shared mailboxes.




Thnx for the post , you helped me a lot !
Hi Paul,
Using your Get-MailboxAuditLoggingReport.ps1 script on a shared mailbox, I was surprised not to see all people who used it to send messages as the shared mailbox – I could find only one entry whilst 15 messages were sent from the shared mailbox.
When running the CMDlet directly, filtering on -Operations SendAs, I could find what I was looking for.
In your script, I modified the following line :
$auditlogentries = Search-MailboxAuditLog -Identity $identity -LogonTypes Delegate,Owner -StartDate (Get-Date).AddHours(-$hours) -ShowDetails
And replaced it with :
$auditlogentries = Search-MailboxAuditLog -Identity $identity -Operations SendAs -StartDate (Get-Date).AddHours(-$hours) -ShowDetails
And then I could find the information. But now I miss the other information (not a big issue because usually we are only searching for the real sender).
Any idea why it does not return the expected results ?
Thanks !
Luuke
Hi Paul,
Using your Get-MailboxAuditLoggingReport.ps1 script on a shared mailbox, I was surprised not to see all people who used it to send messages as the shared mailbox – I could find only one entry whilst 15 messages were sent from the shared mailbox.
When running the CMDlet directly, filtering on -Operations SendAs, I could find what I was looking for.
In your script, I modified the following line :
$auditlogentries = Search-MailboxAuditLog -Identity $identity -LogonTypes Delegate,Owner -StartDate (Get-Date).AddHours(-$hours) -ShowDetails
And replaced it with :
$auditlogentries = Search-MailboxAuditLog -Identity $identity -Operations SendAs -StartDate (Get-Date).AddHours(-$hours) -ShowDetails
And then I could find the information. But now I miss the other information (not a big issue because usually we are only searching for the real sender).
Any idea why it does not return the expected results ?
Thanks !
Luuke
What does SourceItemFolderPathNamesList mean? I can’t find any info on some of the results listed.
I found this MS article but it doesn’t mention this specific parameter.
https://technet.microsoft.com/en-us/library/ff459237(v=exchg.150).aspx
If you get a hold of the original received email headers itself.
You could find the X-Originating-IP (Source IP of the machine that made the SMTP connection) in the email header.
Drop the email header into testconnectivity microsoft message header analyser for better view (Google it)
From this you could find the source host through below –
cmd (Windows command line interface)
> nbtstat -A X-Originating-IP
OR
>nslookup X-Originating-IP
Once you have the hostname – The Active directory users and comp should tell you who the culprit is 😀
hi @ all,
theer is great work from Paul in this link :
https://github.com/cunninghamp/Get-MailboxAuditLoggingReport.ps1
but i have a question for this script. Is it possible to add a funtion that shows me the mail adres to whom our personal send the mail? i mean i want to add a line too for MailTo . I tryed ” $reportObj | Add-Member NoteProperty -Name “Mail To” -Value $entry.MailTo ” but didnt worked.
foreach ($entry in $auditlogentries)
{
$reportObj = New-Object PSObject
$reportObj | Add-Member NoteProperty -Name “Mailbox” -Value $entry.MailboxResolvedOwnerName
$reportObj | Add-Member NoteProperty -Name “Mailbox UPN” -Value $entry.MailboxOwnerUPN
$reportObj | Add-Member NoteProperty -Name “Timestamp” -Value $entry.LastAccessed
$reportObj | Add-Member NoteProperty -Name “Accessed By” -Value $entry.LogonUserDisplayName
$reportObj | Add-Member NoteProperty -Name “Operation” -Value $entry.Operation
$reportObj | Add-Member NoteProperty -Name “Result” -Value $entry.OperationResult
$reportObj | Add-Member NoteProperty -Name “Folder” -Value $entry.FolderPathName
if ($entry.ItemSubject)
{
$reportObj | Add-Member NoteProperty -Name “Subject Lines” -Value $entry.ItemSubject
}
else
{
$reportObj | Add-Member NoteProperty -Name “Subject Lines” -Value $entry.SourceItemSubjectsList
}
$report += $reportObj
}
thank you very much.
Hi everyone
My Organization have an group email. This group mail not have mailbox, just only email address.
On this group, I have assigned another mailbox to be send as of group email . I have a question. How to tracking or audit log that group email. Could you help me?
Thanks and best regards,
ThangND
Hi!
Is there a way for a mail user in AD (with no mailbox) to connect to a shared mailbox from Exchange 2013;
Thanks in advance.
I hope I am not off topic.
I don’t know why MS jacked up the message tracking in Exchange. It was SOOOO easy in Exchange 2010 and below… Now in Exchange 2013 it’s SOOOO difficult and non-intuitive!
I’ve been working with Exchange since 5.5, I’m certainly not a newby to Exchange and message tracking… but if I want to details about message tracking, I find I’m making a google search each time
Under CU8 there seems to be a problem filtering within a single day or even filtering less than 15h17m. I’m intereesed in what happened between 7:30AM and 7:40AM but while -logontypes delegate -startdate “11/5/2015 4:23pm” -EndDate “11/6/2015 7:40AM” returns data,
-logontypes delegate -startdate “11/5/2015 4:24pm”-EndDate “11/6/2015 7:40AM” does not.
Is this fixed with a later CU?
I’ve just noticed that the last access time on the mailbox is 4:23:58PM which may explain the search failing with time details even though it still works using just the date. now to troublshoot why the last accessed time is wrong.
I totally had this working in the past, but now nothing is showing up when I do a search on any mailbox. I deleted an email from a test mailbox on purpose, but when I check the admin audit logs, nothing is coming up. What happened to the logs?
I would just double check that auditing is still enabled, that it is still enabled for the correct event types, and check whether the Audits folder is still present in the mailbox.
Yeah, those were the first things I checked. I was trying to figure out if there is something that can wipe them out, or if I can’t see admin audit logs because I’m an admin that might delete the logs I created… but then who can see them?
Pingback: Shared Mailbox Sent Items Changes Coming to Office 365
Pingback: How to Configure Mailbox Sent Items Behaviour in Exchange Server
Hi Paul,
You’re doing great work. I’m sharing my experience with Exchange too on my blog an LinkedIn.
I’ve put link to your site, because it’s not always in the top in Google search.
Regards,
Maciek
Welcome back & Happy New Year 🙂
It is indeed valuable, the scenario is most common – it has benefited me several times while kept enabled.
Those three articles of yours on auditing are nicely documented.
To Add here – I also like the idea of auditing server side executed Cmdlets(we know its all Power Shell behind GUI) what admin does to track and I use Mike’s Power Shell to get report daily via scheduled task and in turn sends email to a mailbox to keep a record just in case of need 🙂
http://www.mikepfeiffer.net/2010/08/administrator-audit-log-reports-in-html-format-exchange-2010-sp1/