The Third Teams Channel Type
Shared Channels are now generally available (August 2022) to all tenants.
It’s a year since Microsoft first announced Microsoft Teams Connect (shared channels is the first feature under this moniker) and the feature is much anticipated. The delay is explained by the need for the functionality to mature, bugs fixed, and some supporting capabilities (Azure B2B Direct Connect) to become available.
Shared channels are the third type of Teams channel. According to Microsoft, the new channels enable “users to collaborate seamlessly with internal and external partners beyond the boundaries of a team.” You could say the same for Teams up to now using both standard (regular) and private channels. The big difference is that “Once added to a shared channel external users can access the channel right from their Teams account without having to switch organizations.” In other words, unlike the guest membership used to access teams belonging to other Microsoft 365 tenants, which require users to switch clients to access those tenants, the new mechanism allow users to remain connected to their home tenant while they interact with others through shared channels.
Among the goals Microsoft has for shared channels are:
- Eliminate the need for tenant switching. Teams clients display shared channels along with teams and channels from the user’s home tenant. Being able to move between channels without going through the context switch involved in a tenant switch is a big thing because it makes collaboration simpler and more natural.
- Reduce over-sharing: Instead of making someone a guest member in your tenant and giving them access to all the resources owned by a team, you invite them to share a channel and limit access to just the resources available to the shared channel.
- Reduce team proliferation: Team proliferation is bad because it creates more groups and sites. A shared channel creates a collaborative space within a team and avoids the need to create a separate team. Private channels also reduce team proliferation using a different approach (a subset of team members). Even with shared channels, it’s likely that tenants will continue to have to manage group (team) sprawl.
Three Channel Types
Table 1 lists the essential characteristics of the three types of channels available in Teams.
| Channel type | Max. number in team | Membership | Collaboration | Dependency |
| Standard (Regular) | 200 | Tenant and guest accounts. | Open within team | Azure B2B Collaboration |
| Private | 30 | Subset of team. | Focused with subset of team | Azure B2B Collaboration |
| Shared | 200* | Invited set of users from tenant and other Teams tenants. | Flexible cross-organization controlled by Azure cross-tenant access policy | Azure B2B Direct Connect |
Table 1: The different types of channels available in Teams
* The maximum number of shared channels per team will be available when Microsoft makes the feature generally available later this year.
You can’t convert a channel from one type to another. Once selected at creation, a channel remains in its type until its deletion. With that in mind, let’s discuss some of the mechanics involved in using the new technology.
Teams shared channels bring their own challenges – read more!
Policy Control for Shared Channels
Microsoft originally introduced the Teams channel policy to control the creation of private channels. The policy now handles shared channels too. You can manage the Teams channel policy through the Teams admin center (Figure 1) or with PowerShell (using version 3.1.1 of the MicrosoftTeams module).
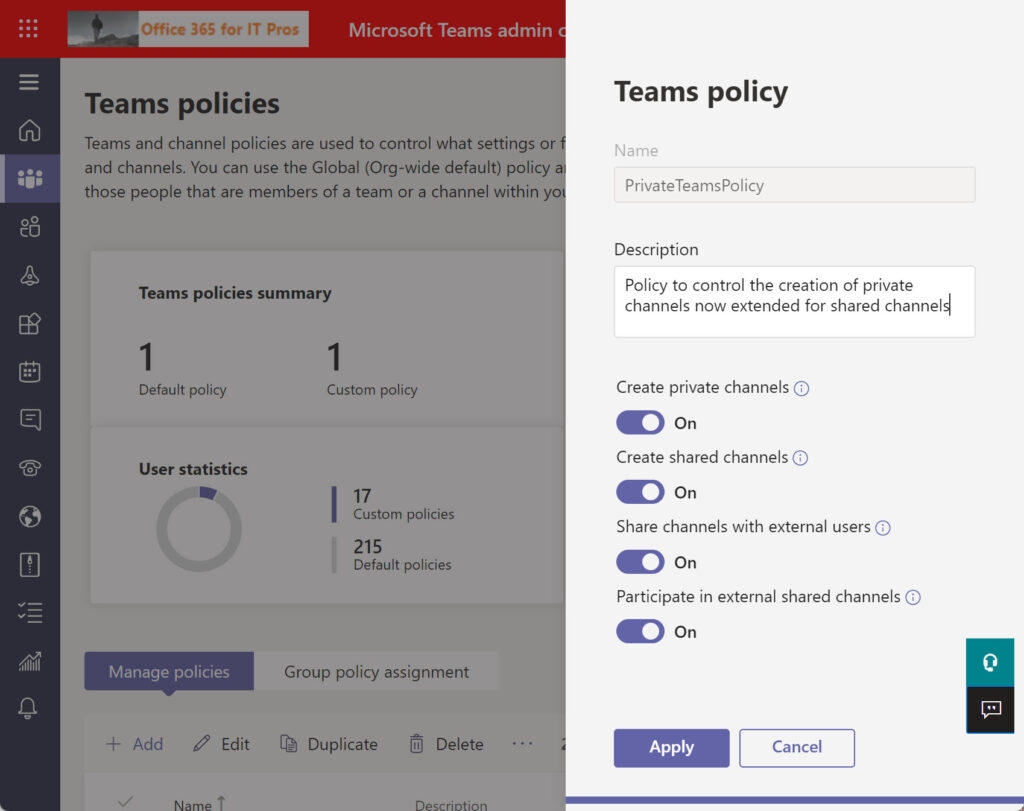
For instance, here’s how to list the set of Teams policies in a tenant and reveal if each policy permits the creation of shared channels and inviting external users to join.
Get-CsTeamsChannelsPolicy | Format-Table Identity, AllowSharedChannelCreation, AllowChannelSharingToExternalUser
And here’s how to assign a Teams policy to an account. In this instance, the name of the policy is a hint that it blocks channel creation:
Grant-CsTeamsChannelsPolicy -PolicyName NoSharedChannels -Identity Ben.Owens@Office365itpros.com
If an admin blocks a team to guests, either by assigning a container management sensitivity label which blocks guest access to the team or by updating the group properties, users can’t invite external people to share a channel. Also, make sure that the external federation settings in the Teams admin center allow access to domains hosting accounts you want to invite to join shared channels.
Creating Shared Channels
The UI to create a new shared channel is like creating any other channel with one exception. As you can see in Figure 2, there’s an option to share the channel with all members of the team which owns the channel. A shared channel has two modes of membership: direct membership (when someone is added explicitly to the channel), and implicit membership, when they gain access through their membership of a team. If you add the owning team to a shared channel on its creation, the team members join via the implicit model.
I haven’t added an emoji to the channel name (shared channels has its own indicator), but I think these channels are a good example of where emojis can highlight a special object in Teams.
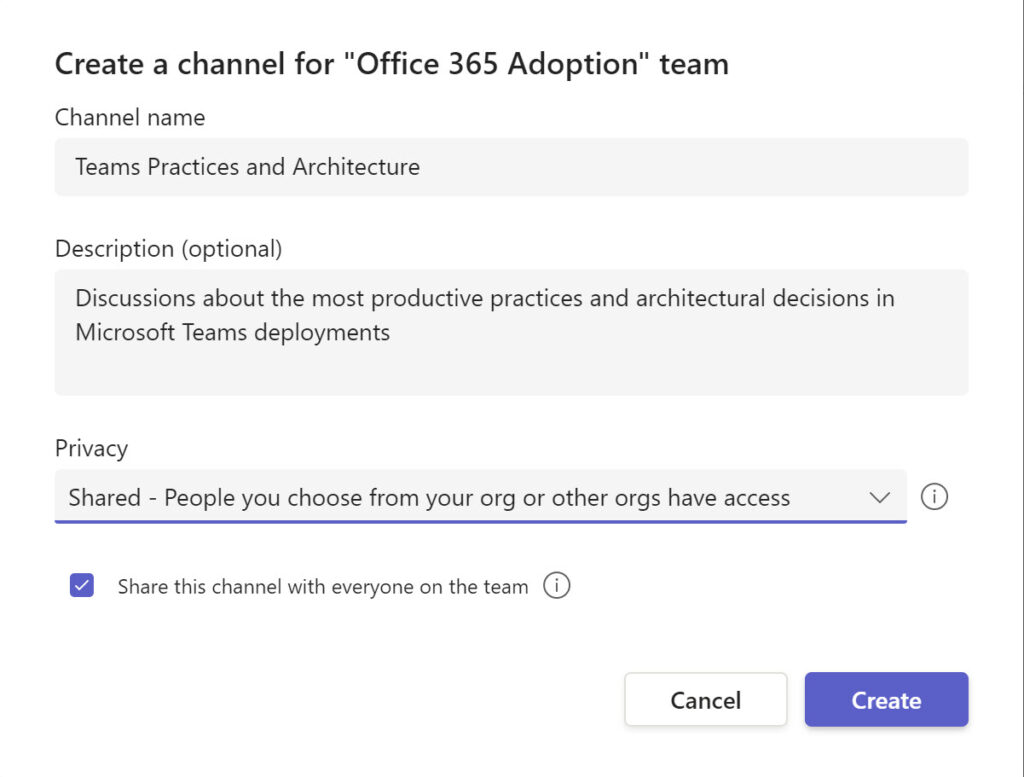
The option to add existing team members to a shared channel underscores a critical point. Members of the team which host a shared channels don’t necessarily become members of the channels. The person who creates the channel becomes its owner and it’s up to them who should join the channel to collaborate. These can be individual users or teams from your tenant or other tenants.
Just like a regular channel, a channel owner can add apps and tabs to a shared channel. However, some apps might only work with tenant users because they require an update to deal with external members. The owner of a team can view shared channels and even remove a shared channel without being a member of that channel.
External Collaboration and Cross-Tenant Access
Shared channels don’t use Azure B2B Collaboration, so external members don’t need guest accounts in the host tenant to access the channel. Instead, these channels depend on a different mechanism called Azure B2B Direct Connect. In practice, this means that your tenant respects the credentials users obtain by authenticating against their home tenant. A single channel can support users drawn from multiple external tenants. If an administrator revokes cross-tenant access for another tenant, users from that tenant will lose access to shared channels within an hour.
Unlike Azure B2B Collaboration, which allows guest accounts to come from both Microsoft 365 tenants and non-Microsoft domains, currently shared channels are only accessible by users with an Azure AD account. Extending to support MSA accounts might be in the future.
To allow people from other Microsoft 365 tenants to share a channel, you must configure Azure AD cross-tenant access to permit collaboration with other tenants. Likewise, tenants that host remote users must allow those uses to collaborate with your tenant. These settings only apply to Teams for now, but it’s easy to imagine that Microsoft might extend this capability to cover other applications in the future.
By default, Azure AD turns external collaboration off, so you must configure a cross-tenant policy to cover the relevant organizations before proceeding to add external members and teams. The policy you configure can restrict access to specific organizations, teams (groups), and users. It’s wise to start with a simple policy that allows access to a single other tenant (or all tenants) and build from there. Remember that the other organization must configure their policy to allow collaboration with your tenant. This is a two-way street.
Adding External Users and Teams
To add external members, select Share channel from the channel menu and then:
- People (individual users from inside or outside your tenant). Users from your tenant don’t have to be a member of the host team.
- With a team (an external team).
- With a team you own (from your tenant).
Figure 3 shows the process of sharing a channel with several external users. For each, you must enter their email address, which Teams validates to make sure the domain belongs to a tenant configured for cross-tenant access. If you enter an address from another tenant, Teams reports that it can’t find a match (the lookup against Azure AD failed).
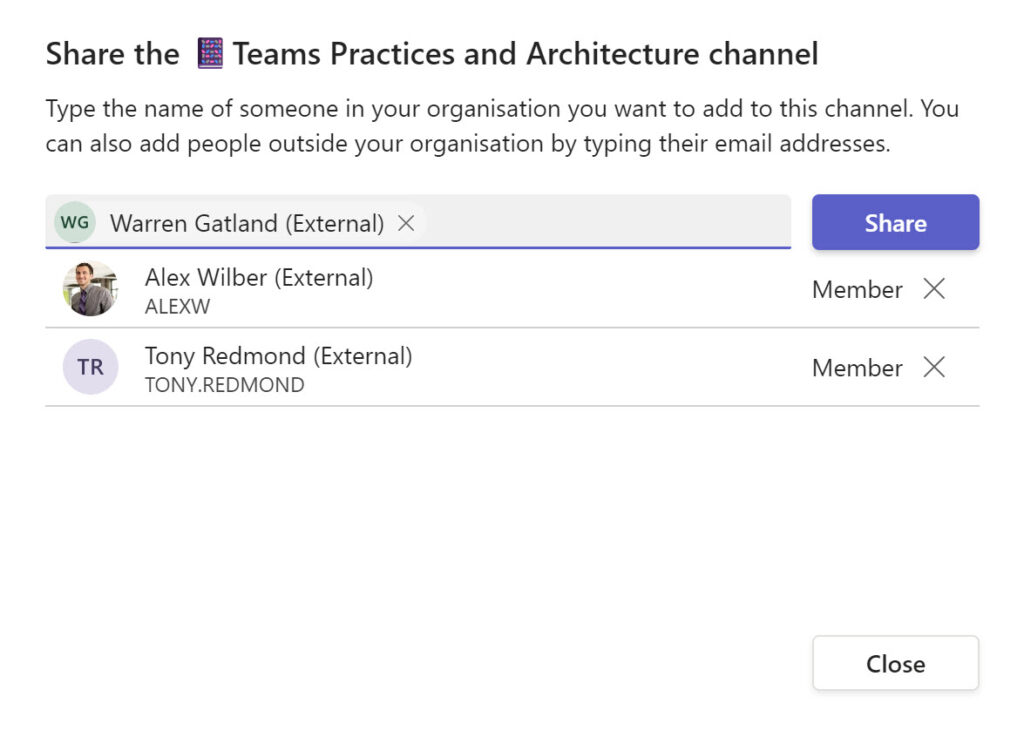
The first time an external user accesses the channel, they must give consent to the host tenant to access details of their account. Although Azure AD creates nothing for an external user in a host tenant, apps like Teams need to display details of external users like their profile (name, email address, and picture). The consent covers display of this information in the channel membership roster and profile cards.
After adding users from your tenant to a shared channel, you can promote them to become channel owners. External users can only ever be members and cannot become channel owners. They also have a limited view of organizational information about team members from outside their name (email and name only), but they can chat or call other channel members.
Sharing a Team with Shared Channels
Shared channels use different approaches when adding teams to membership. If the channel owner owns the target team, they can grant access to everyone in that team in one operation. It’s simply a matter of selecting the team to add and confirming that the addition should happen.
Adding a team that the channel owner doesn’t own is a different matter. The channel owner sends an invitation to the team owner to collaborate (Figure 4).
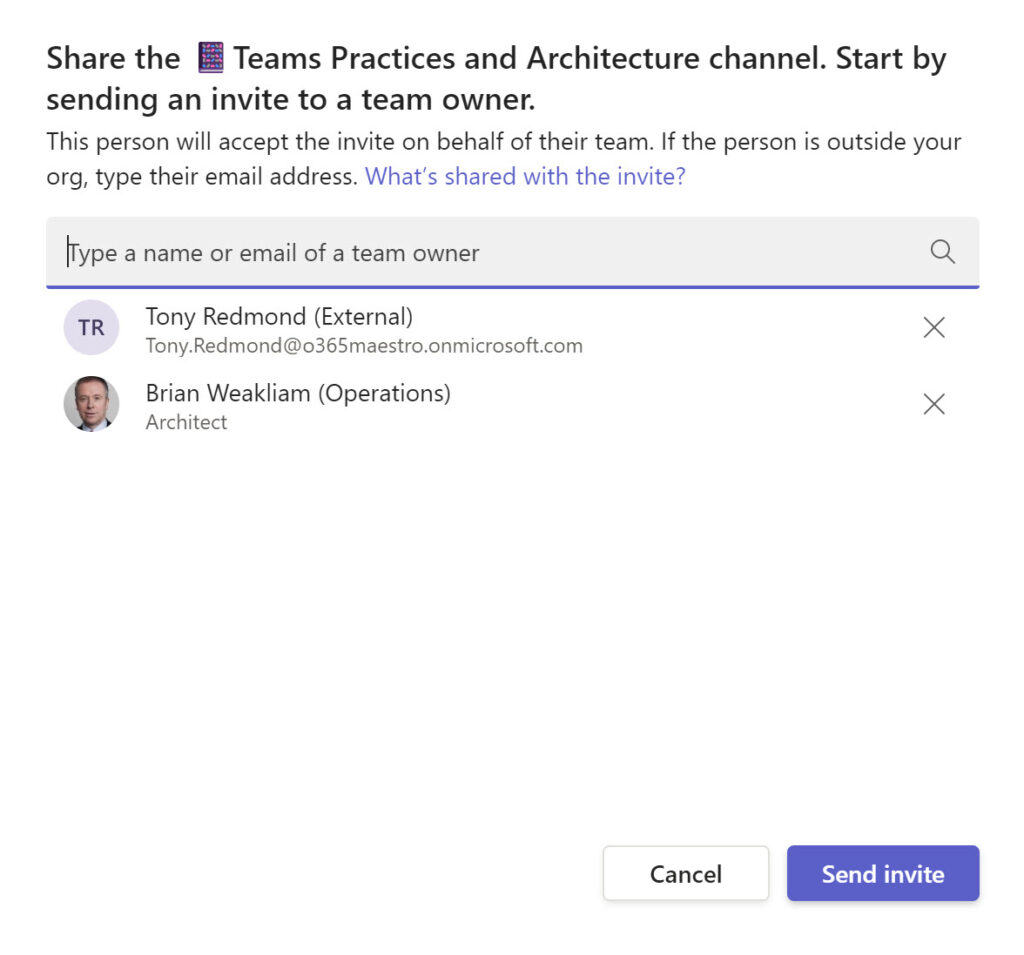
The invited team owner sees the invitation in their activity feed (Figure 5) and has 14 days to accept the invitation. After this period, the invitation lapses and is no longer valid.
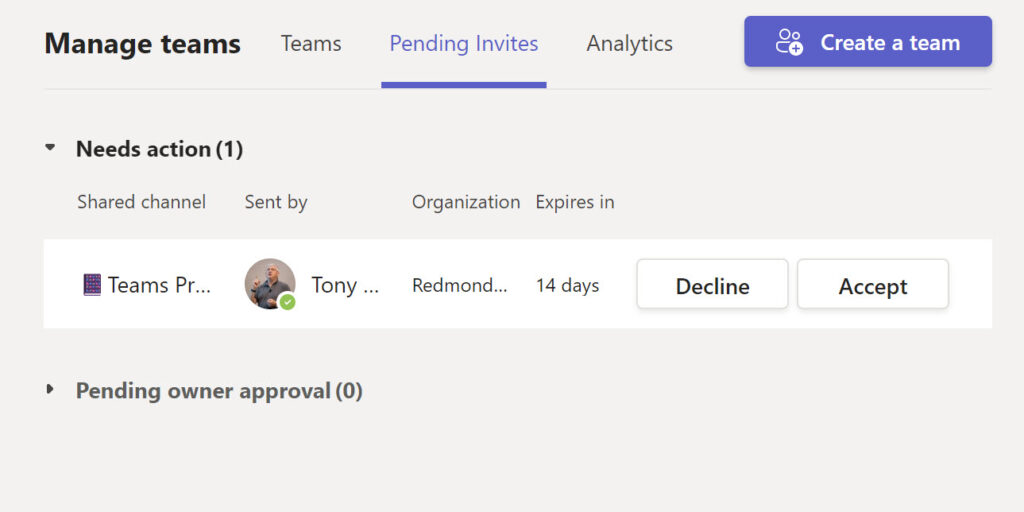
While an invitation is active, the channel owner sees it listed in the Sent Invites tab of the Manage channel option (Figure 6).
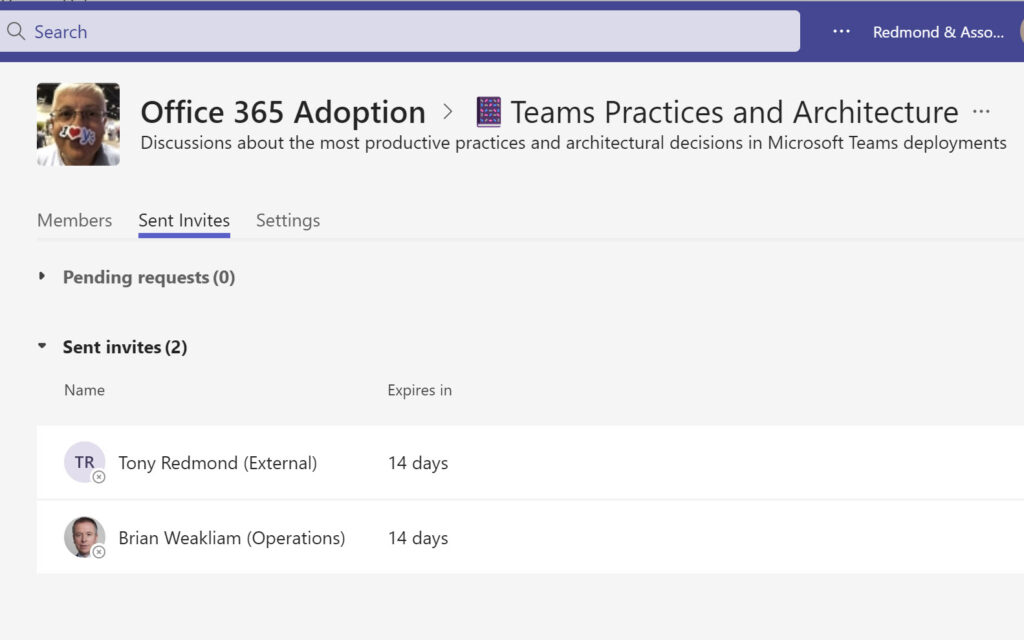
Accepting Invitations
If they accept the invitation, the team owner then decides which team to accept the invitation on behalf of. Of course, they might be the owner of just one team and the choice is easy, but if they are an owner of multiple teams, they can choose for which team to accept. An owner of an org-wide team can’t add it to a shared channel.
Following acceptance, a validation process occurs to check that the cross-tenant policies for both tenants allFollowing acceptance, a validation process occurs to check that the cross-tenant policies for both tenants allow every member of the chosen team to share the channel. When this process finishes, the channel owner receives a notification that the invited team owner accepted their invitation. The channel owner reviews the chosen team and decides to approve or reject the addition of the team. If approved, the external team joins the channel membership (Figure 7).
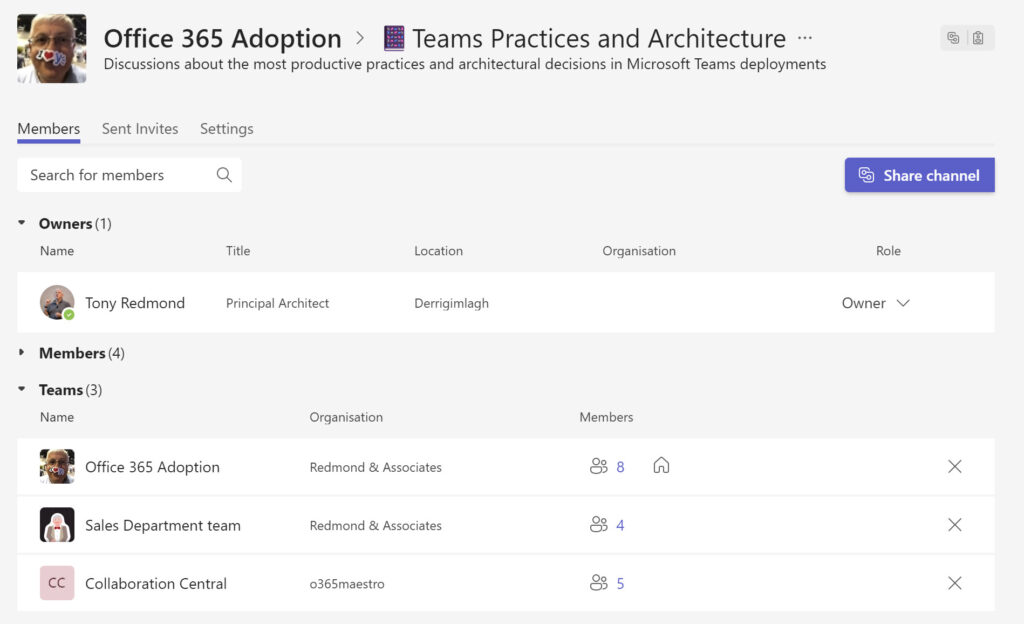
Excluding guest members, the tenant members of the chosen team gain access to the shared channel., which then appears in their client with an “External” suffix. Team members can see the full roster (list of channel members) composed of owners, individual members, and those who gain access through team membership. There’s nothing hidden.
You can’t exclude tenant members of the team from the set added to the shared channel. If the requirement is to limit access to specific people, you should issue individual invitations. People who are become members of a shared channel through membership of a team lose their access if they leave that team. Individual members keep their access for as long as they remain in the membership.
Channel owners can terminate sharing at any time by removing individual members or complete teams from the channel’s roster. Individual members can choose to leave a shared channel at any time, and a team owner can remove a team from a shared channel.
Using Shared Channels
After all that setup, adjustment of policies, and adding members and teams, it’s a relief to use a shared channel. It’s also boring because it’s all so normal. Apart from the extra icon at the end of the channel name to distinguish shared channels from regular and private channels, everything else works as you’d expect inside a channel (Figure 8).
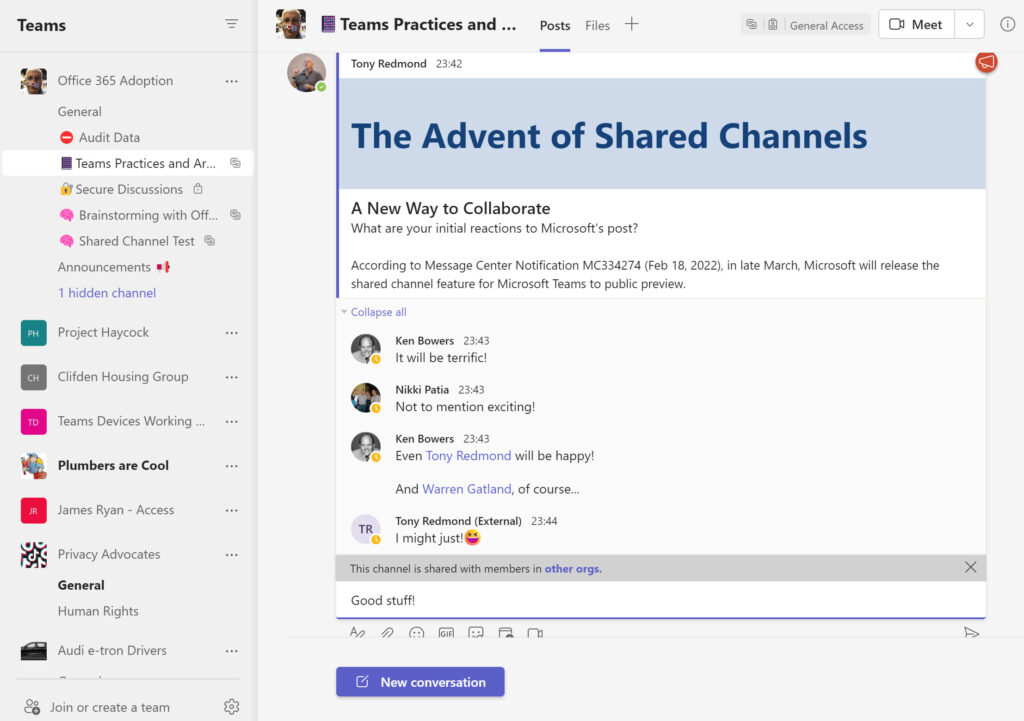
Sure, you can’t tag someone in a shared channel, but @ mentions work. An external suffix appears for external members, and Teams highlights sharing of content with people in other organizations, but apart from that, channel conversations proceed as normal.
Unlike private channels, which only support Meet Now meetings, shared channels support both Meet Now and scheduled meetings, but only for tenant users. For scheduled meetings, the person who schedules the meeting becomes the meeting organizer, but the meeting is a channel meeting, not a personal meeting. The channel meeting app does not support shared channels. I assume that Microsoft stores the calendar data in the same cloud-only mailbox created to store compliance data for the channel.
Shared channels don’t support @mentions for channel membership.
SharePoint Online and Shared Channels
Both private and shared channels have their own SharePoint team site. The shared channel site inherits its settings like privacy and guest access from the owning team; these settings cannot be overridden. If you don’t want sharees to be able to access documents stored in SharePoint, use sensitivity labels to protect the documents against all but internal access.
The sites belonging to shared channels use the same TeamChannel#1 template as used for private channels, meaning that you can do this to find the list of sites used for shared channels:
$Sites = Get-SPOSite -limit All -Filter "TEAMCHANNEL#1" | ? {$_.TeamsChannelType -eq "SharedChannel"}
ForEach ($Site in $Sites) {
$SPOSite = Get-SPOSite -Identity $Site.url -detail
$Group = Get-UnifiedGroup -Identity $SPOSite.RelatedGroupID.Guid
Write-Host "Team" $Group.DisplayName "owns shared channel site" $Site.URL}
Like private channels, if you want to include shared channels sites in an eDiscovery search, you must find the URL and include it in the search criteria.
Compliance
Microsoft says that shared channels support the full range of Microsoft 365 Information Protection features such as eDiscovery, DLP, and in-place holds. This is true, but compliance processing proceeds on the basis that the host tenant has complete control. Teams, Azure AD, and SharePoint Online capture audit events for actions of remote users in shared channels in the host tenant’s audit log. In addition, the Microsoft 365 substrate captures compliance records for messages posted by sharees in shared channels in a special mailbox in the host tenant. The substrate does not capture records in the home tenants of sharees. In effect, this means that sharing activity outside the home tenant is invisible to tenant administrators, something which might concern compliance administrators and eDiscovery investigators.
For instance, you could set up a shared channel to discuss a plan to execute some fraudulent activity and invite me to join. We could plot the details in the channel and go ahead and commit an offense. If I come under suspicion, any investigation centered in my tenant will turn up no evidence because the audit data exists in the other tenant. Unless investigators know to look elsewhere and the administrators of the other tenant co-operate, no trace of malfeasance is discoverable.
This scenario is also present when guest accounts collaborate in regular and private channels. However, the ease of external collaboration in shared channels creates potential for compliance issues that organizations should be aware of. The upside here is that the need to create and manage cross-tenant access policies means that tenant administrators know the external tenants where their users collaborate. In that respect, these channels are a step forward in terms of administrative knowledge of how people work outside their home tenant.
Administration
Microsoft has updated its administrative interfaces for shared channels (PowerShell, Microsoft Graph, admin portals). Normal channel administration applies to shared channels. For instance, if you delete a shared channel, you have 30 days during which you can restore the channel (and its SharePoint site).
Some work is necessary for tenants and ISVs to upgrade scripts and apps to deal with shared channels. Tabs and connectors work now with support for bots, message extensions, and apps coming soon.
Teams and Groups Aren’t So Connected Anymore
The new channels mark a big change in the relationship between Microsoft 365 Groups and Teams. Until now, Teams used the Groups model for identity and membership. Every group member has the same rights to access the resources of the team and group owners manage team settings and membership. The membership (roster) of the new channels accommodates people who aren’t group members. Although Teams can manage access for external members to channel conversations and the SharePoint site through federated recognition of their accounts and credentials, Microsoft needs to update other apps, like Planner and OneNote before the full power of a team is available.
Not the End for Azure B2B Collaboration
Guest users and Azure B2B collaboration will continue within Teams and other Microsoft 365 apps. There’s still value in being a guest of another organization and having access to a wide range of teams in that organization. However, it’s reasonable to expect that the number of guests accounts created in tenants will reduce over time. This is good because it avoids the current proliferation of guest accounts, many of which become obsolete soon after creation.
We’re at the beginning of the shared channels journey. Hopefully, the great hope and aspirations expressed by Microsoft at this Ignite 2021 session will come to pass and everyone will collaborate happily through enhanced sharing. We can but hope!





Great article Tony – thank you for unpacking this and in the comments further too. I am just trying to understand what happens when you create a shared channel and, at creation, select to share the channel with the host Team (i.e. select the “Share this channel with everyone on the team” checkbox). Doing that, anyone later added on the Team level will automatically have access to the shared channel via their Team membership. However, this implicit membership cannot be undone later for the shared channel (according to the Microsoft support page about creating shared channels) without the user being removed from the Team as well.
As such, if one wants to have more control over who in the host Team can access the shared channel later, it would be better to leave that checkbox deselected when creating the channel and rather manually add the host Team as a ‘member’ afterwards (so that you can more easily customise who in the Team can have access at any point).
What happens is that you bind the membership in the shared channel to the roster (membership) of the hosting team. To remove the user, you need to remove them from the team. The upside of the mechanism is that it makes it very easy to share channels with large teams (or even small teams). The downside is that you lose some control.
Thanks very much for confirming this, Tony. Agreed fully about the positive being sharing with larger teams and that it is dynamically kept up to date with whatever the host team’s membership is at any time. I just feel it would be better that one can undo this team binding for the shared channel after creation if needs be (not unlike breaking permissions of a SharePoint subsite at a later stage from its parent site). Failing that, a larger warning about this checkbox on the shared channel creation dialog box.
Thanks Tony, this article is rally useful. I have a question if you don’t mind! If I have existing Shared Channels and I deselect the ability to create (additional) Shared Channels within the Policies, does this have any effect on those existing Shared Channels please? Do the Shared Channel SharePoint sites get deleted etc?
Disabling the ability to add new shared channels has no effect on existing channels.
Hi Tony,
I am trying to add the Channel Calendar to my shared channel. Everything goes smoothly (no errors popping up). It even appears as a tab at the top of the shared channel. But then it disappears after 3 seconds. Why is that..?
I don’t believe that shared channels support the channel calendar app. That app reads events for a channel from a group mailbox and I don’t think Microsoft has updated it for shared channels.
Not able to find the external account when I use email Id via Graph API calls, but the same email Id works If I use via Teams client/browser GUI.
How it is difference from Teams GUI vs Graph API call, any suggestions please.
The below is Graph API call
Graph API: request body
{
“@odata.type”: “#microsoft.graph.aadUserConversationMember”,
“roles”: “”,
“user@odata.bind”: “https://graph.microsoft.com/v1.0/users(”)”
}
Error Message:
{
“error”: {
“code”: “NotFound”,
“message”: “Failed to find user with id ” in the tenant”,
“innerError”: {
“date”: “2023-04-25T14:03:42”,
“request-id”: “”,
“client-request-id”: “”
}
}
}
The clue is in the error. The referenced user doesn’t have an account in the tenant. Their account is probably in another tenant, in which case an inbound shared user profile will exist for then: https://office365itpros.com/2023/04/24/teams-shared-channels-profile/
Yes. but the same external email accounts works fine when you try use Teams Client GUI, when we trying to automate using Power Automate Graph API calls, it does find the account.
so how it is different from adding via Teams client vs Graph API calls, one works and other does not work.
The Teams client might be making two calls. One to get internal users, the other to get external users. Who knows? I don’t have access to the code.
update:
the scenario only works if the external user account email & UPN is same, in the Graph API call able to find the account.
But if the user account UPN is different from the email, then the Graph API calls fails to find the account. unfortunately, we only deal with external email Ids, and in fact we don’t know their UPN.
do you think any workaround?
I have no idea. I have not looked into the situation at all.
Hello Tony, thank you very much for this very complete article as always!
It says in the article that “The owner of a team can view shared channels and even remove a shared channel without being a member of that channel.”, however in our tests we don’t see that at all. On our side a team owner can’t see the shared channels if he’s not a member and can’t interact with them either. Maybe it’s something that was like this in the preview and has evolved since then?
A team owner can see the channels in a team with PowerShell and can remove the channel that way. They can also see a shared channel that they’re not a member of by using the Manage team/channels option.
Thanks for the article Tony.
Am I right in understanding that there’s no ‘Group’ for a Shared or Private Channel. So say if I have a folder on SharePoint called ‘Finance’ and I want to share this with the members of a Shared Channel called ‘Retail Shared’ or a Private Channel called ‘Retail Private’ under a Team called ‘Retail’. When I click manage access on ‘Finance’ and start to type in ‘Retail’, it only gives me the ‘top level’ members of ‘Retail’. Though I only want to give access to those in the ‘Retail Private’ or ‘Retail Shared’ channel. Is that not possible? Cheers.
There’s no group for a shared or private channel. They do have sites, but these are special sites that are “owned” and controlled by the parent team.
SharePoint doesn’t know anything about the membership roster for these channels. If you want to share files with the members of a shared channel, you’ll need to do so by specifying the members individually.
Hi Tony,
First congratulations on the article.
From what I understand from the text and the comments when an external user enters the channel for the first time, will he have to “log in” to our tenant? Even if we didn’t create an account for him? In the scenarios I’m testing, the user is receiving a pop-up to log in to our tenant and register with mfa.
thanks
To connect to a shared channel for the first time, an invited external user will have to authenticate and comply with your tenant’s requirements for authentication. For instance, if their tenant does not enforce MFA and yours does, they will have to go through an MFA challenge.
Hi Tony, this is a great piece of information which I came across when trying to figure out how Channel meetings work in a Shared Channel vs a standard channel.
I wonder if you would know the following:
My channel meeting in a standard channel sends an invite to the group mailbox, but the shared channel doesn’t seem to? This may be ‘as designed’ (due to the shared channel not being all members?), so then I thought I would @ mention the Shared Channel name so members would get a notification instead (depending on their settings), but they didn’t! So I wonder, can the shared channel members get to hear about the channel meeting in any way like a standard channel or do they just have to see that it’s live to join in the post? I appreciate I could name them individually or as a group, but they’re all already in the shared channel so I’m repeating effort! Thanks.
Shared channels don’t have a team/group. A shared channel has a membership roster made of up the people/teams added to it as members. As the article says, when you create a meeting in a shared channel, the person who creates the meeting sets everything up as a personal meeting and then the shared channel appears to take over as the owner. The meeting remains a personal meeting that the person who creates can amend.
The only way to add everyone in the shared channel to the meeting is to add them individually. It’s just the way things work today.
Is there a way to unshare the channel with one person while keeping the sharing with other people in a shared channel by any chance? Thanks!
If the person has individual membership of a shared channel (rather than through a team), the channel owner can remove them using the Manage Channel option.
In your article you mention “An owner of an org-wide team can’t add it to a shared channel.” But you don’t mention why. Why can’t a shared channel add an org-wide team as a member? If it’s just an acceptance thing in the GUI, can it perhaps be done in PowerShell?
It’s a restriction imposed by Microsoft, possibly because an org-wide team uses a special mechanism to maintain its membership roster.
Great article, thanks. I think you can add some more drawbacks to it: You can’t create a shared channel in a “Class” team type.
Also, when scheduling a meeting to the channel (instead of adding individual members), external participants don’t receive any email. They just receive an activity notification, if the opt to receive notifications for all channel activity.
And worst, the meeting won’t show up in teams calendar of external users. That is keeping us from moving forward. We are an education institution and as many others in our segment, we have separate tenants for staff/professors and students. Consolidating the tenants is a no go for us, as information barriers are not sufficient, and the complexity is exponential. Shared channels could be the right thing for us, but the calendar and the ability to schedule a meeting to all member of the channel, are basic things we need.
It’s worth to note that configuring some options in the tenant requires up to 24 hours to take effect.
It’s a nice step forward but is missing essential things. If you have some insights if these things are going to be addressed in the near future, please share.
Cheers!
Thanks. Remember that this is the first iteration of the shared channel feature and I think Microsoft focused on the enterprise market as the target for this release. Teams Edu is quite a different place, and the pressure to do something to create a better solution to cross-tenant collaboration is heightened in the enterprise compared to education. That being said, I expect to see progress in this area over the next year or so. It just takes time…
Noting that Wiki app is not supported in Shared Channels at this time.
I am also noting that standard doc apps like Word, Excel and PowerPoint are not available as channel tabs, which appears to be a randomly-surfacing bug as I’ve seen it reported on forums. OneNote, Visio and other Office apps are available. In fact this week I had PowerPoint available on Monday and it disappeared from the list of apps by Thursday. The ” Make a Tab” option is not available at the file level even for those doc types that are supported as tabs e.g. PDF.
None of this behaviour is evident in other standard channels in the same team.
The wiki is not supported for shared channels because Microsoft is trying to get away from it (which is why they are not provisioning the wiki any longer for regular channels: https://office365itpros.com/2022/07/15/teams-wiki-nomore/). As to the other apps, I haven’t noticed the problem you report. Maybe it’s just growing pains?
Hi
I Have setup the B2B Direct for teams shared channel.The Teams functionality is fine however the external user in the shared channel cannot access the sharepoint files. Does external sharing need to be activated for the Owning team for this to work ?
external people should be able to access SPO files – unless you block access in some way. B2B Direct Connect is simply an authentication mechanism. It permits access to your tenant… but it can’t stop external people getting past blocks you erect at an app level.
I’ve gotten this all working but fallen at the last hurdle. When I open Teams I can see i’ve been added to a shared channel and have the message at the top about ‘the org needs your permission etc etc’ there’s a hyperlink for ‘review permission’ but that doesn’t bring anything up 🙁
Tried both the Teams app and via the web – just doesnt do anything. any clues??
That link should bring you to a consent screen to allow you to give permission for your account information to be shared with the tenant hosting the shared channel. Can you access the shared channel?
Hi Tony,
Nomather what we try, this link isn’t getting us anywhere. All the collaboration settings seem to be in place. Any ideas?
File a support incident with Microsoft and ask them to check your tenant. If you’ve done everything as documented, it’s hard to understand what might be going wrong without access to your tenant, which I don’t have.
Matt,
Did you ever find out what caused this message to appear? Or better yet, did you find a solution for it?
Currently experiencing the same issue here.
Thanks for a great deep dive! One thing I still haven’t understood though: if you invite an individual user to a shared channel, where will they see that channel in their own Teams environment? …as the shared channel isn’t added to any one team…
One of the big advantages of shared channels is that users don’t have to switch to another tenant to access a channel. Instead, Teams creates an entry for the team that hosts the shared channel in the list of teams displayed to the user when they connect to their home tenant. In other words, the team (on another tenant) appears as if it is part of their home tenant, and the channel works like any other channel. The only indication that it’s shared is an icon at the end of the channel name.
I was wondering if there is a way to bypass the initial user consent that you get when accessing the external shared channel for the first time, and instead apply a tenant wide policy that’d grant those permissions by default for everyone.
I don’t believe so. The consent is to allow details of the external user to be shared with the other members of the channel.
Just to clarify – if we have a strict conditional access for 100% MFA, and an external user’s tenant is not enforcing MFA, that invited shared channel user would not have access until they set up MFA proactively on their own tenant, correct? No failover to using our MFA (a la guest), correct?
Invited channel users must comply with the resource tenant’s security posture. If you require MFA, they must use MFA to secure credentials that will be accepted by your tenant as a valid claim.
I can’t add external users to the Shared Channel. I can to the Team it is in, but when I try “Share Channel” it brings up the usual dialog box:
Type the name of someone in your organization you want to add to this channel. You can also add people outside your organization by typing their email addresses.
All I get back is “We didn’t find any matches”
I have set up the Cross-tenant access settings in External Identities in both tenants and I am allowed to invite Guests and there is no restrictive Sensitivity Labels on the Team and no restrictions in Guest invite settings in Azure. Interestingly I CAN invite an external User using the Teams Admin Portal.
Actually no I can’t. Although it would find them and ask if I wanted to add them, when I hit reply I got: We can’t add the members that were selected.
Can you add guest users from the target tenant to the team?
If you can’t, is an Azure AD B2B Collaboration blacklist in place that includes that domain?
Is there a block on the domain for external federation with Teams? https://admin.teams.microsoft.com/company-wide-settings/external-communications
Did you find a solution to this Conrad? We’re having the same problem when trying to invite externals “We didn’t find any matches”
Did you check your federation settings?
Yes – We’ve turned on the settings for communicating with Teams users whose account aren’t managed by an org .
I’m testing this between two tenants I’ve got admin access to. I’ve managed to get this working where users from Tenant 2 can invite users from Tenant 1. Strangely though, I can’t get it to work the other way around.
The settings on both tenants are identical apart from the SharePoint Sharing settings for Tenant 1 which a bit more restrictive. Tenant 1 has the External Sharing setting to “Existing guests”.
Could this be causing the issue?
What about the settings to allow federated communications (chat) with Teams users in other organizations.
It’s under:
Teams and Skype for Business users in external organizations at https://admin.teams.microsoft.com/company-wide-settings/external-communications
When external domains are allowed, users in your organization can chat, add users to meetings, and use audio video conferencing with users in external organizations. By default, your organization can communicate with all external domains. Learn more
I’ve got that turned on with “Allow only specific external domains” and the domain I’m working with is listed in there.
Sorry for replying here. It doesn’t let me reply to your latest comment.
I’m out of ideas. You should file a support incident with Microsoft and have them check your tenant. Sometimes a new set of eyes is all that’s needed to locate a problem, and I have no access to your tenant.
I can’t add external users to the Shared Channel. I can to the Team it is in, but when I try “Share Channel” it brings up the usual dialog box: Type the name of someone in your organization you want to add to this channel. You can also add people outside your organization by typing their email addresses. all I get back is “We didn’t find any matches”
I have set up the Cross-tenant access settings in External Identities in both tenants and I am allowed to invite Guests and there is no restrictive Sensitivity Labels on the Team
Understand that guest account cannot be added into a shared channel.
What if users want to add existing guest account into a shared channel? User need to reach out IT to delete the guest account from AAD? What type of error/message user will see if they try to add existing guest account in shared channel?
What if users added an external account into a shared channel, then later want to invite the same account into a Teams group as guest account, what error/message user will see if they invite the existing external account to a Teams group? Will it automatically convert the account from external to guest? If yes, will the outsider user lose the Shared channel permission?
Members of a shared channel are added using their email address/UPN. That address points to their “real” account, so any guest account for that user in your tenant is ignored. Remember, authentication flows through the home tenant and not the host tenant (where the guest account lives). The two types of account (member and guest) work alongside each other and there’s no need to remove guest accounts to have shared channels work.
BTW, the public preview is now available, so you can test all this stuff yourself. Get hold of a development tenant https://office365itpros.com/2021/04/15/test-development-office-365-tenant-test-new-features/ and off you go…
Great review fo details for Shared Channels! Learned quite a bit.
One quick question. Can an external user download a file from a shared channel to there local machine?
Yes (by default). You can configure conditional access policies to prevent SPO downloads to untrusted workstations.
Sorry, I don’t do free consulting… Understanding risks is something you’ll need to figure out yourself. Any perceived (as opposed to actual) risks will differ from organization to organization.
@Tony
Doing research on this feature. Could you please share the potential risks involved in this feature?
Hey Guys, i have turned on Preview features enabled in when i read this article on 23th in the upgrade policies but i m still stuck without the shared channel (only standard and private) on both way trhough admin team or heaven in the Public previe Teams UI.
Can you help me ?
Thanks
M
As the article says, Microsoft will release shared channels in preview in March.
I was too excited sorry, thanks Tony 🙂
Thanks for this!
The first sentence of the last paragraph under “Using Shared Channels” needs an edit. (It repeats itself.)
“Unlike private channels, which only support Meet Now meetings, shared channels support both Meet Unlike private channels, which only support Meet Now meetings, shared channels support both Meet Now and scheduled meetings, but only for tenant users.”
Fixed.
Hi Tony,
thank you for this very clear post, as usually.
I have one question: suppose that my tenant requires MFA and that I decide to not trust MFA from other Azure AD Tenants in collaboration settings. What is the expected behaviour for the external user? It will prompt for MFA when he tries to access to the shared channel? Or when he tries to access Teams?
Thanks!
In my observations, the MFA challenge happens when the user accesses the shared channel. This is logical because it’s at that point when credentials are queried.
Hi Tony,
thank you for your post.
Do you know if it is possible to use the Planner in a shared channel?
Best Regards,
Stephan
Not yet. Microsoft needs some time to prepare all the apps which depend on Microsoft 365 Groups to work well in shared channels.
Is there any roadmap item on planner becoming available on private/shared channels? I see you (and others) have mentioned Microsoft working on this, but can’t find any roadmap item.
https://www.microsoft.com/nl-nl/microsoft-365/roadmap?ms.url=m365comroadmap&rtc=2&filters=&searchterms=planner
The wonders of a Microsoft NDA stop me saying anything more than Microsoft’s public position is that they’re working on bringing Planner to private and shared channels.
Thank you for this excellent post!
Just for the records: In order to check your tenants setup, looks like the current Teams Module is good enough:
PS C:\Users\xxx> Get-InstalledModule -Name MicrosoftTeams
Version Name Repository Description
——- —- ———- ———–
2.3.1 MicrosoftTeams PSGallery Microsoft Teams cmdlets module …
PS C:\Users\xxx> Get-CsTeamsChannelsPolicy | fl
Identity : Global
Description :
AllowOrgWideTeamCreation : True
AllowPrivateTeamDiscovery : True
AllowPrivateChannelCreation : True
AllowSharedChannelCreation : True
AllowChannelSharingToExternalUser : True
AllowUserToParticipateInExternalSharedChannel : True
That’s a pretty old version of the Teams module you have there… And the problem about using any of the 2.x.x versions is that Microsoft will decommit from these versions soon (see their release notes). You should upgrade and use the latest version, which is what I recommended in the article.